Spyware Cases (Part 1)
My first article on this resource was devoted to a moment from the history of cryptography: the world of secrecy carries away, attracts, it is full of secrets and riddles that open only with the passage of time; ciphers, cryptomachines and interweaving of destinies, events, incidents around the “secrecy” stamp.

There are various forms of espionage. When countries spy on each other, the intelligence officer is usually located and works in the embassy of a hostile country, protected by diplomatic immunity. But sometimes an intelligence officer is introduced into the territory of the enemy under a fictitious name with a fictitious legend, alone or even with his family, such espionage is illegal.
In fact, the collection of information from the enemy is rarely performed by the intelligence officer himself, but rather there is some agent who has access to the necessary information. In this situation, the intelligence officer becomes just a “processor” (case management officer) of the information received from the agents. Potential agents are people whose motive is one of or a combination (sometimes all together) of such factors as Ego, Ideology, Compromise (acronym MICE: Money, Ideology, Compromise and Ego), according to one from theories of motivation for spies).

Following the chronological order, consider the history of cryptography through the prism of known events, individuals and equipment.

Chief Ensign of the Navy, John Anthony Walker (July 28, 1937 - August 28, 2014), working in the US Navy as a specialist in public relations, began to spy on the side of the Soviet Union.
Over 17 years of working with the Soviets, he was able to pass on thousands of secret documents to them, which compromised US encryption machines, such as KL-7, KL-47 and KW-7. As a result, this allowed the USSR to decipher at least a million confidential documents. John was issued a Minox C camera so that he could photograph secret documentation and key material.

Minox-C is a sub-miniature camera (for a film measuring 8 x 11 mm), it was the successor to Minox B, it was developed in Germany. For many years, Minox miniature cameras were famous in the world of spyware, right up to the 90s when the Cold War ended. Minox-C was in production from 1969 to 1978, replaced by an even more miniature Minox LX.
At first glance, Minox C is similar in design to Minox B. However, there were a few significant differences. The Minox B selenium photoexponometer was replaced with a sulphide-cadmium photoresistor present on the right front of the camera (small square).

In addition, the camera was already with an electronic shutter, rather than mechanical. To perform the function close / open, a battery was required, it was installed in the compartment to the right of the light sensor. As a result, the camera dimensions were significantly larger than the Minox B.
In the closed state, the dimensions of the camera were 120 x 27 x 15 mm, which is 2 cm longer than the Minox B. These dimensions gave the Minox C the title of the largest subminiature camera Minox had ever created. Nevertheless, it had advantages over Minox B. For example, when opening and closing the camera, the film moved only when the photo was actually taken, while in Minox B the film moved each time it was closed. The Minox C lens had an aperture with a fixed f / 3.5 value and a focusing distance of 20 cm to infinity. Since 1969, and ending in 1978, 173,594 pieces of equipment were produced.
On the left was a disk for selecting the sensitivity of a film with a scale according to DIN (from 6 DIN to 27 DIN). The disk in the center served for manual adjustment of the shutter speed (1/15 and 1/1000 seconds). The Minox C had an electronic shutter that was connected to the light meter on the left. Setting the shutter switch to position A (automatically) allowed the exposure meter to control the exposure time, I mean shutter speed.

In order to avoid blurring during movement caused by slow shutter speeds, the camera was equipped with a “speed control” device. In the automatic exposure mode (A), when the shutter speed is lower than 1/30 second, the LED (slow speed indicator) lights up.

On the right on the camera was a dial with a dial for setting the distance (focusing). Because Minox C was a spy thing and had to fit in a fist, it had a macro lens that focused well on objects as close as possible to 20 cm. Like Minox B, the viewfinder and lens were located a few centimeters from each other.

The process of replacing the film cartridge looked pretty simple. At first it was necessary to push the camera in the usual way, as if to take a picture, after pulling out a few more until you can see the indentation, use your thumb to press down on the indentation, which in turn would unlock the camera. After opening the lid of the camera body and open the film cassette.

If there was a film, the camera had to be turned upside down until the film cartridge fell out. A new film was taken from the protective container and placed in the chamber. The camera is closed.

Accessories:



Returning to Walker. In 1955, he began to serve in the US Navy, motivated by such a factor as "Money", successfully recruited a spy for the USSR in the winter of 1967. For 17 years, until his retirement in 1983, John passed information to the Soviets with keys, encryption materials for KL-47, KW-7, and others. The remuneration for the service was several thousand dollars a month. Later, he got involved with the help of Jerry Whitworth (a fleet officer), from 1973 together with him, later in 1984 by his elder brother Arthur and his son Michael, served for the "good" of the USSR. It all ended in a foolish way, the Walker couple fell out on the ground of alcohol abuse and violence and went their separate ways. Walker did not pay alimony to his wife, and Barbara filed a lawsuit against him, and at the same time handed over his underground activities to the authorities. Walker decided to cooperate with the authorities, made a deal and admitted his guilt. Suffering from diabetes and throat cancer, John Walker died in prison on August 28, 2014. By the way, the materials provided by John Walker and his espionage group allowed the USSR to build an analogue of the KL-7 .

On March 7, 1983, Richard Osborne, who had just been appointed first secretary of the US embassy in Moscow, was caught by the Russian secret service of the KGB on the hot - while operating a sophisticated RS-804 radar satellite in one of the parks of Moscow.
During the Cold War, the RS-804 was used by American operatives in many countries that were considered hostile to the United States, such as Cuba, East Germany (DDR), Poland, and the Soviet Union (USSR). However, the problem with the USSR was that Moscow was at the very end of the MARISAT satellite coverage area. In June 1981, tests showed that RS-804 cannot be reliably used from Moscow. Kits have been returned to the USA.
The RS-804 kit was upgraded by experts from the CIA, two years later it was returned to the Moscow station for testing. By the end of 1982, the Russian secret service of the KGB began to notice the interception of signals to the US MARISAT satellites, which, as expected, came from parks and forests in the USSR.
Meanwhile, Richard Osborne, a 40-year-old man, was a diplomat at the US embassy since August 1982 and lived in Moscow with his wife and two daughters for 6 and 8 years. He was appointed First Secretary in the Ministry of Economy.
March 7, 1983 Osborne was going to test an improved device, while walking in the park with his family. He went to an open place in Victory Park on Poklonnaya Hill and installed a device hidden inside his portfolio, so that he could “see” the satellite. Then Osborne began the transfer.
Understandably, he was unaware that the KGB was spying on him and his family, the Osborns came under suspicion earlier, and as soon as the KGB received confirmation that signals were actually being sent from his portfolio, he was arrested. Roughly speaking, Richard was caught hot. A complex RS-804 satellite communications transmitter, hidden under a double bottom, was found in his portfolio. The device was tuned to 311.15 MHz in the UHF band: satellite communication channel MARISAT.
In the Osborne briefcase, notes written on special water-soluble paper were found. For the KGB, this was the latest proof that Osborne was indeed a spy, not a diplomat. After his arrest, Osborne (who had diplomatic immunity) was released and declared persona non grata for "actions incompatible with diplomatic status." Then he was sent outside the Soviet Union.
The sophisticated miniature radio RS-804 was thoroughly researched and photographed by the KGB, code-named PHOBOS or FOBOS, and the information was transmitted to friendly services in countries such as Cuba, Poland and the GDR. Later, the KGB seized several more such devices in Afghanistan in 1988.
RS-804 was a modular design, thanks to which it was possible to use the radio receiver or its modules in various configurations and hide without problems. The width of the “thickest” module was 19 mm, which was ideal for covering the device inside a briefcase or in a piece of furniture. Some parts were used with a similar CDS-501 radio receiver.
Radio CDS-501

1. Transceiver RT-804
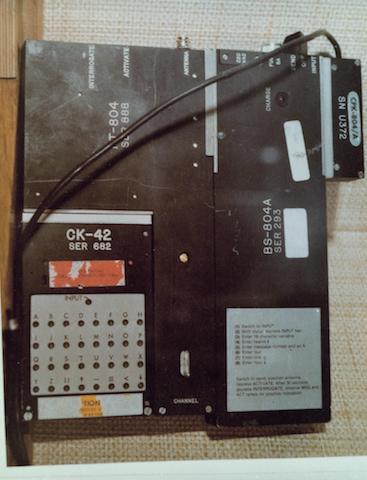
L-shaped transceiver, 100 x 188 mm in size. It had two connectors for connecting to other modules: one for connecting the CK-42 encryption device (2), the second for connecting to a battery / power supply / charger. In addition, the top has a connector for the antenna.
The transmitter worked in the microwave range of 300 MHz, the RF amplifier of the transmitter had 10 W of output power. It was suitable for use with US satellites MARISAT and FLTSATCOM. The device, which was intercepted by the KGB, was tuned to 311.15 MHz; ascending line of a MARISAT satellite earth station. It is known that the following frequencies FLTSATCOM (satellite communications fleet) were used by the CIA for data transmission, all in narrowband FM / data:
2. Encryption device CK-42
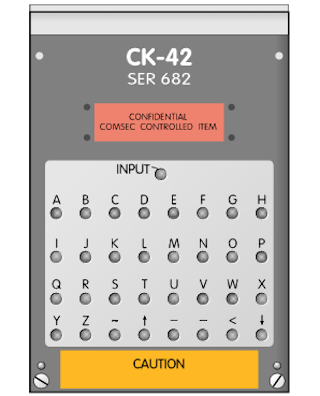
The crypto module or encryption device was the smallest part of the set. Its dimensions were 100 x 68 x 18 mm, and weight - only 160 grams. He connected to the L-shaped transceiver, easily disconnected, which made it possible to load data from the outside. CK-42 is designated as “Confidential COMSEC Controlled Item”.
CK-42 stored in the internal memory messages up to 1579 characters in length, encrypted with an encryption key of 19 characters, this key was provided on a separate sheet. Most likely, a new key was used for each message.
Messages were entered using a small keyboard, 32 buttons arranged in 4 lines, 8 columns, plus a separate INPUT button at the top. Due to the small size of the device, it was necessary to use a stylus to enter data. At maximum load, the broadcast took place in 20 seconds.
The encryption algorithm that is used by CK-42 is currently unknown. This crypto module was used as part of the CDS-501, a CIA device for communicating with agents at close range.
3. Power supply BS-804A
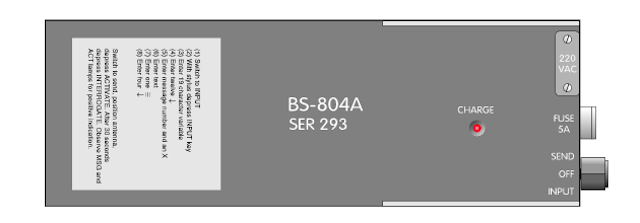
The power supply was the largest part of the system, 69 x 180 mm. This included a set of NiCd batteries, as well as an AC power supply unit (PSU), which was also used as a charger. The system could operate either on batteries or on AC power.
The power supply was connected to the transceiver through the connector in the upper left corner. There was a MODE selector: a three-position rotary switch that could be set to SEND, OFF, or INPUT. In the upper right corner was a jack for the remote control. The power supply shown in the figure has been configured for 220 V AC, indicated by a small tag on the top edge.
On top of the power supply, there was a small CHARGE lamp that turned on when connected to AC power (NiCd batteries were charging). Instructions for use - as proof of ease of use of the device.
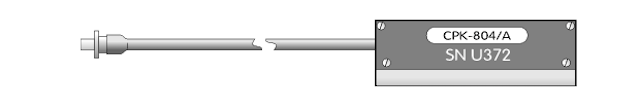
4. Remote control CPK-804 / A
A small remote control device was connected to the socket in the upper right corner of the power supply. With it, an external (wired) activation switch was connected to the device.
Antenna
Antenna with circular polarization is the longest and thinnest component of the device. Its dimensions are 310 x 310 mm.
The ICF-2001D was a portable LW, MW, SW and FM receiver, the best short-wave receiver that was ever created by the famous Japanese company Sony (1980). Although it was a commercially available product, he managed to play an important role in international espionage.

Sony ICF-2001D
The dimensions of the ICF-2001D are 29 x 16 x 5 cm; the device was powered with two AA batteries and three D-type batteries. From above - the telescopic antenna, in front - the digital indicator. The ICF-2001 could also be powered by a 4.5 V DC external adapter (or batteries). As an alternative, you could use a 12-volt adapter, which allowed you to use the radio in the car. There were three basic versions of this device, besides at least five models for different countries with different frequency and voltage standards. The device fully covered the LW and MW bands in AM, as well as VHF in FM (87-108 MHz). But the actual “target” of this radio receiver was the broadcasting band HF. Radios such as the Sony ICF-2001D and Grundig Satellit 2000 were very popular in the 1980s, allowing you to listen to international broadcasts.
Due to its rather compact size, high sensitivity and battery power, the ICF-2001D was used as a tool for Eastern European spies working in Western European countries during the Cold War. Often, agencies like the KGB, the GRU and the Stasi gave money to their Western spies to buy such a receiver in local stores.
With the help of the receiver, the spies listened to East European stations operating in the short wave range. Hidden in numbers, secret messages and instructions for the spy were decrypted using the One-Time Pad. Immediately after deciphering the messages, he was destroyed - the mission was considered accomplished. Messages were sent back to the spy center by courier, through "dead mailboxes" (caches intended for secret message forwarding agents).
A vivid example of the use of ICF-2001D in international espionage is a series of cases against US citizens from 2001 to 2009. In the homes of subjects spying on the US for Cuba, the FBI discovered Sony ICF-2010 (the US version of ICF-2001D).
The first case is the case against Ana Belen Montes (February 28, 1957), who worked in the United States Military Intelligence (DIA) and held the post of senior Cuban analyst. From 1985 until her arrest in 2001, she spied on Cuba’s side, having managed to transfer a lot of documentation and confidential military information to Cubans.
Before the arrest, on September 21, 2001, the FBI, during a search of Ana's apartment, found evidence of using the One-Time Pade (OTP) on a laptop. A Sony receiver was found that served to receive One-Time Pade (OTP) messages from Cuban stations tuned to 7887 kHz. Ana received a clear instruction from the Cuban Intelligence Service (CuIS) to destroy the data on the laptop after use - but did not have time to do it. As a result, the FBI managed to get an OTP message.
The author of The Art of Spying, Keith Melton, who studies the history of intelligence throughout the world, wrote that she used Sony ICF-2010 (equivalent to ICF-2001D in the USA). In a detailed 2010 document, researcher Dirk Rymanants explained how the FBI managed to crack the unbreakable OTP cipher due to the shortcomings of Cuban procedures. By pleading guilty of espionage, Montes was sentenced in October 2002 to 25 years in prison without the possibility of parole.
The United States was the main external facility for the Cuban Intelligence Service (CuIS). It is therefore not surprising that the CuIS personnel and agents recruited and controlled by CuIS in the United States were important targets for the FBI’s counter-intelligence efforts. In recent years, the FBI has disclosed several important operations. The link in these cases was precisely the fact that the agents received their operational reports. And why, despite the use of Cuban's unbreakable cryptographic system, the FBI was able to decipher some of these operational messages, and subsequently provide it as evidence at the trial.
Mistakes in the CuIS messaging procedure were what contributed to the prosecution, arrest, and conviction of clandestine agents.
So, Ana Belen Montes (and a couple more agents) was charged by the federal prosecutor, her case was: “Montes communicated with the Cuban Intelligence Agency with encrypted messages and received her instructions from Cuba, using the shortwave range for transmission”.
Although a common method was used to receive prompt reports and instructions from CuIS agents, it was not the reason that led to investigations, surveillance and, ultimately, the arrest of spies. It was errors during operations that played a decisive role in these cases. Thus, the cryptographic system, which is considered perfectly safe, acted as an “accuser” and provided evidence of espionage. The spies themselves were not at all stupid people, rather even educated intellectuals. So how did this perfect system work and what led to its failure?
The usual method used by CuIS to communicate with its agents in the United States was to transmit encrypted messages using powerful shortwave transmitters located in Cuba. Messages consisted of a series of numbers dictated by voice or using Morse code.

Senior Cuban analyst Ana Belen Montes (February 28, 1957) worked for 16 years at the United States Intelligence Agency (DIA) when she was arrested in 2001 on suspicion of spying for Cubans. In her stuff, the FBI found a Sony ICF-2001D receiver, a Toshiba laptop, and evidence of the use of OTP ciphers. Ana Belen Montes studied at the University of Virginia, received a diploma in international relations, and graduated from the Johns Hopkins University with a master's degree. In 1985, she began working at the Department of Justice in Washington. Her frank opinion and statements about US policy regarding Latin American countries attracted the attention of Cuban officials. Shortly after, Montes was recruited by CuIS. In 1985, Montes applied for a position at the Intelligence Agency (DIA). For many years she was a leading analyst on Cuban issues, had access to classified information.
In 1996, one of the employees told the security service that, in his opinion, Montes could be linked to Cuban intelligence. The case did not go further "denunciation", however, four years later, the FBI began searching for a Cuban agent in Washington, the same official contacted the FBI and ... an investigation began.
In the same year, Ana received instructions from CuIS to purchase a laptop, with her she received computer diskettes for decrypting radio messages and newsletters from CuIS. A shortwave radio was used to listen to messages broadcast on the Cuban Atencion station. The transmitted number of numbers was decrypted on her computer into readable text using floppy disks from CuIS. Each radio message consisted of 150 groups, five digits each, it was a typical Atencion format.
Montes also received a floppy disk and to encrypt messages received, secret information. She saved the encrypted messages on other diskettes, and then transferred them herself (or through someone) to her "conductor". She was instructed to use the “WIPE” program (secure file deletion) every time she decrypted or encrypted something on her laptop. For organizing meetings on “floppy disk sharing,” she called a pager using phone cards (specific pager codes were used to transmit a particular message).
The FBI was able to gather enough evidence against Ana. During the search of the apartment Montes was found a laptop, and his hard drive - copied. During the analysis, a copy of the hard disk was able to recover much of the deleted information. The FBI found fragments of instructions on how to receive encrypted messages. It became clear that Montes received the messages and decrypted them on her computer.
But what went wrong? The use of a computer by the agent for communications is the first major mistake made by CuIS. No computer is 100% protected, because information is often stored in temporary files or swap. Data remains on the hard disk, even after deletion. Although the instruction from CuIS required the use of the WIPE program, Ana did not seem to run the program all the time or the program did not work correctly at some point. Nevertheless, it is impossible to call this an agent’s error, rather, it’s a CuIS procedural error. Providing the highest level of precaution, rather than relying on strict adherence to agent safety procedures, was a direct task of CuIS. Moreover, using a computer for espionage and clandestine purposes is already a bad idea. And even if the agent completely “cleans up” his computer, he may forget to completely delete the information on a diskette or flash drive.
Дальнейший анализ показал вторую ошибку CuIS. Жесткий диск содержал данные, состоящие из 150 групп с 5 цифрами в каждой. В архивах ФБР уже хранились перехваченные сообщения идентичные по структуре, потому не составило труда определить, что данная информация поступала с кубинской станции «Atencion».
Непонятен оставался тот факт, почему CuIS отдали предпочтение «программному обеспечению» взамен самой надежной системе ручного шифрования. «Ручной» процесс обработки данных на протяжении многих лет доказывал преимущества one-time pad — легкость и безопасность уничтожения (например, сжигание) доказательств, без следов. С цифровыми носителями процесс обстоял гораздо сложнее. Да и процесс ручного дешифрования очень прост в освоении и применении. Чтобы расшифровать сообщение, состоящее из 150 групп, потребовалось бы не более 30-40 минут.
Случай с Аной Белен ясно показывает, как вы можете превратить совершенно безопасную схему шифрования с помощью «карандаша и бумаги» в небезопасное компьютерное приложение. Разумеется, кубинская разведка не совсем осознавала тот факт, что переход с ручного на программное шифрование требует решения многих новых проблем для обеспечения полной безопасности метода. Это яркий пример неумелого соединения нерушимого метода и небезопасного его применения на ПК.
В 1 части статьи были использованы такие источники Crypto Museum , Рэм Красильников «Призраки в смокингах. Лубянка против американских дипломатов-шпионов.», Андрей Троицкий «Знак шпиона».
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4 RAM).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?

There are various forms of espionage. When countries spy on each other, the intelligence officer is usually located and works in the embassy of a hostile country, protected by diplomatic immunity. But sometimes an intelligence officer is introduced into the territory of the enemy under a fictitious name with a fictitious legend, alone or even with his family, such espionage is illegal.
In fact, the collection of information from the enemy is rarely performed by the intelligence officer himself, but rather there is some agent who has access to the necessary information. In this situation, the intelligence officer becomes just a “processor” (case management officer) of the information received from the agents. Potential agents are people whose motive is one of or a combination (sometimes all together) of such factors as Ego, Ideology, Compromise (acronym MICE: Money, Ideology, Compromise and Ego), according to one from theories of motivation for spies).

Following the chronological order, consider the history of cryptography through the prism of known events, individuals and equipment.
John Walker / John Walker 1967-1985

Chief Ensign of the Navy, John Anthony Walker (July 28, 1937 - August 28, 2014), working in the US Navy as a specialist in public relations, began to spy on the side of the Soviet Union.
Over 17 years of working with the Soviets, he was able to pass on thousands of secret documents to them, which compromised US encryption machines, such as KL-7, KL-47 and KW-7. As a result, this allowed the USSR to decipher at least a million confidential documents. John was issued a Minox C camera so that he could photograph secret documentation and key material.

Minox-C is a sub-miniature camera (for a film measuring 8 x 11 mm), it was the successor to Minox B, it was developed in Germany. For many years, Minox miniature cameras were famous in the world of spyware, right up to the 90s when the Cold War ended. Minox-C was in production from 1969 to 1978, replaced by an even more miniature Minox LX.
The camera was 8 centimeters in length, 2.8 in width and only 1.5 centimeters thick and easily fit in the palm of your hand. He had a four-lens lens that allowed focusing at close range. The Minox camera was great for photographing documents, letters, book pages, and envelopes, but it was difficult to use without being noticed by others. The shutter clicked loudly, the camera had to be held with both hands, and she needed good lighting - not the best conditions for spy photos
At first glance, Minox C is similar in design to Minox B. However, there were a few significant differences. The Minox B selenium photoexponometer was replaced with a sulphide-cadmium photoresistor present on the right front of the camera (small square).

In addition, the camera was already with an electronic shutter, rather than mechanical. To perform the function close / open, a battery was required, it was installed in the compartment to the right of the light sensor. As a result, the camera dimensions were significantly larger than the Minox B.
In the closed state, the dimensions of the camera were 120 x 27 x 15 mm, which is 2 cm longer than the Minox B. These dimensions gave the Minox C the title of the largest subminiature camera Minox had ever created. Nevertheless, it had advantages over Minox B. For example, when opening and closing the camera, the film moved only when the photo was actually taken, while in Minox B the film moved each time it was closed. The Minox C lens had an aperture with a fixed f / 3.5 value and a focusing distance of 20 cm to infinity. Since 1969, and ending in 1978, 173,594 pieces of equipment were produced.
On the left was a disk for selecting the sensitivity of a film with a scale according to DIN (from 6 DIN to 27 DIN). The disk in the center served for manual adjustment of the shutter speed (1/15 and 1/1000 seconds). The Minox C had an electronic shutter that was connected to the light meter on the left. Setting the shutter switch to position A (automatically) allowed the exposure meter to control the exposure time, I mean shutter speed.

In order to avoid blurring during movement caused by slow shutter speeds, the camera was equipped with a “speed control” device. In the automatic exposure mode (A), when the shutter speed is lower than 1/30 second, the LED (slow speed indicator) lights up.

On the right on the camera was a dial with a dial for setting the distance (focusing). Because Minox C was a spy thing and had to fit in a fist, it had a macro lens that focused well on objects as close as possible to 20 cm. Like Minox B, the viewfinder and lens were located a few centimeters from each other.

The process of replacing the film cartridge looked pretty simple. At first it was necessary to push the camera in the usual way, as if to take a picture, after pulling out a few more until you can see the indentation, use your thumb to press down on the indentation, which in turn would unlock the camera. After opening the lid of the camera body and open the film cassette.

If there was a film, the camera had to be turned upside down until the film cartridge fell out. A new film was taken from the protective container and placed in the chamber. The camera is closed.

Accessories:



Returning to Walker. In 1955, he began to serve in the US Navy, motivated by such a factor as "Money", successfully recruited a spy for the USSR in the winter of 1967. For 17 years, until his retirement in 1983, John passed information to the Soviets with keys, encryption materials for KL-47, KW-7, and others. The remuneration for the service was several thousand dollars a month. Later, he got involved with the help of Jerry Whitworth (a fleet officer), from 1973 together with him, later in 1984 by his elder brother Arthur and his son Michael, served for the "good" of the USSR. It all ended in a foolish way, the Walker couple fell out on the ground of alcohol abuse and violence and went their separate ways. Walker did not pay alimony to his wife, and Barbara filed a lawsuit against him, and at the same time handed over his underground activities to the authorities. Walker decided to cooperate with the authorities, made a deal and admitted his guilt. Suffering from diabetes and throat cancer, John Walker died in prison on August 28, 2014. By the way, the materials provided by John Walker and his espionage group allowed the USSR to build an analogue of the KL-7 .
Richard Osborne / Richard Osborne 1982-1983

On March 7, 1983, Richard Osborne, who had just been appointed first secretary of the US embassy in Moscow, was caught by the Russian secret service of the KGB on the hot - while operating a sophisticated RS-804 radar satellite in one of the parks of Moscow.

During the Cold War, the RS-804 was used by American operatives in many countries that were considered hostile to the United States, such as Cuba, East Germany (DDR), Poland, and the Soviet Union (USSR). However, the problem with the USSR was that Moscow was at the very end of the MARISAT satellite coverage area. In June 1981, tests showed that RS-804 cannot be reliably used from Moscow. Kits have been returned to the USA.
The RS-804 kit was upgraded by experts from the CIA, two years later it was returned to the Moscow station for testing. By the end of 1982, the Russian secret service of the KGB began to notice the interception of signals to the US MARISAT satellites, which, as expected, came from parks and forests in the USSR.
Meanwhile, Richard Osborne, a 40-year-old man, was a diplomat at the US embassy since August 1982 and lived in Moscow with his wife and two daughters for 6 and 8 years. He was appointed First Secretary in the Ministry of Economy.
March 7, 1983 Osborne was going to test an improved device, while walking in the park with his family. He went to an open place in Victory Park on Poklonnaya Hill and installed a device hidden inside his portfolio, so that he could “see” the satellite. Then Osborne began the transfer.
Understandably, he was unaware that the KGB was spying on him and his family, the Osborns came under suspicion earlier, and as soon as the KGB received confirmation that signals were actually being sent from his portfolio, he was arrested. Roughly speaking, Richard was caught hot. A complex RS-804 satellite communications transmitter, hidden under a double bottom, was found in his portfolio. The device was tuned to 311.15 MHz in the UHF band: satellite communication channel MARISAT.
In the Osborne briefcase, notes written on special water-soluble paper were found. For the KGB, this was the latest proof that Osborne was indeed a spy, not a diplomat. After his arrest, Osborne (who had diplomatic immunity) was released and declared persona non grata for "actions incompatible with diplomatic status." Then he was sent outside the Soviet Union.
In the late autumn of 1982, Soviet counterintelligence among thousands of radio signals revealed coded transmissions in speed mode, which came from the Moscow region to the Marisat-3 satellite. In early 1983, such radio signals were repeated twice. This CIA station continued to insistently check the conditions for the passage of radio signals from Moscow. The fourth conspiracy radio broadcast, which was conducted by the first secretary of the American embassy, Richard Osborne of Filevsky Park in Moscow, was fatal for the Central Intelligence Agency. It did not help either that the station intended to present his trip to the park as a family walk, or that the radio kit was hidden in a shopping bag.
The sophisticated miniature radio RS-804 was thoroughly researched and photographed by the KGB, code-named PHOBOS or FOBOS, and the information was transmitted to friendly services in countries such as Cuba, Poland and the GDR. Later, the KGB seized several more such devices in Afghanistan in 1988.
RS-804 was a modular design, thanks to which it was possible to use the radio receiver or its modules in various configurations and hide without problems. The width of the “thickest” module was 19 mm, which was ideal for covering the device inside a briefcase or in a piece of furniture. Some parts were used with a similar CDS-501 radio receiver.

Radio CDS-501
CDS-501 Radio Modules

1. Transceiver RT-804
L-shaped transceiver, 100 x 188 mm in size. It had two connectors for connecting to other modules: one for connecting the CK-42 encryption device (2), the second for connecting to a battery / power supply / charger. In addition, the top has a connector for the antenna.
The transmitter worked in the microwave range of 300 MHz, the RF amplifier of the transmitter had 10 W of output power. It was suitable for use with US satellites MARISAT and FLTSATCOM. The device, which was intercepted by the KGB, was tuned to 311.15 MHz; ascending line of a MARISAT satellite earth station. It is known that the following frequencies FLTSATCOM (satellite communications fleet) were used by the CIA for data transmission, all in narrowband FM / data:
- 243,000 - 244,000 MHz
- 251,000 - 269,000 MHz
- 292.000 - 317.000 MHz
2. Encryption device CK-42

The crypto module or encryption device was the smallest part of the set. Its dimensions were 100 x 68 x 18 mm, and weight - only 160 grams. He connected to the L-shaped transceiver, easily disconnected, which made it possible to load data from the outside. CK-42 is designated as “Confidential COMSEC Controlled Item”.
CK-42 stored in the internal memory messages up to 1579 characters in length, encrypted with an encryption key of 19 characters, this key was provided on a separate sheet. Most likely, a new key was used for each message.
Messages were entered using a small keyboard, 32 buttons arranged in 4 lines, 8 columns, plus a separate INPUT button at the top. Due to the small size of the device, it was necessary to use a stylus to enter data. At maximum load, the broadcast took place in 20 seconds.
The encryption algorithm that is used by CK-42 is currently unknown. This crypto module was used as part of the CDS-501, a CIA device for communicating with agents at close range.
One of the technological innovations was the miniature electronic device SCRAC, the first of a large family. An early version of the device under the name “Buster” was given to Dmitry Polyakov, the general of the Soviet military intelligence (GRU), who himself offered his services in New York and received the code name “Cylinder” from the FBI. The CIA hoped that the new device would make it easier for Polyakov to communicate with them and prevent the KGB from seeing. It was a portable communication system consisting of two portable base stations, each the size of a shoebox, and an agent for the agent that could be hidden in a pocket. Using a tiny keyboard measuring 4 square centimeters, the agent had to encrypt the text first, and then enter this digital message. As soon as the data was uploaded - a thousand and a half characters were placed in Buster - the agent should be within a radius of 300 meters from the base station and press the send button. The base station was portable, it could be left near a window or in a car, the agent only needed to be told where it was located approximately.
3. Power supply BS-804A

The power supply was the largest part of the system, 69 x 180 mm. This included a set of NiCd batteries, as well as an AC power supply unit (PSU), which was also used as a charger. The system could operate either on batteries or on AC power.
The power supply was connected to the transceiver through the connector in the upper left corner. There was a MODE selector: a three-position rotary switch that could be set to SEND, OFF, or INPUT. In the upper right corner was a jack for the remote control. The power supply shown in the figure has been configured for 220 V AC, indicated by a small tag on the top edge.
On top of the power supply, there was a small CHARGE lamp that turned on when connected to AC power (NiCd batteries were charging). Instructions for use - as proof of ease of use of the device.
4. Remote control CPK-804 / A
A small remote control device was connected to the socket in the upper right corner of the power supply. With it, an external (wired) activation switch was connected to the device.
Antenna

Antenna with circular polarization is the longest and thinnest component of the device. Its dimensions are 310 x 310 mm.
ICF-2001D
The ICF-2001D was a portable LW, MW, SW and FM receiver, the best short-wave receiver that was ever created by the famous Japanese company Sony (1980). Although it was a commercially available product, he managed to play an important role in international espionage.

Sony ICF-2001D
The dimensions of the ICF-2001D are 29 x 16 x 5 cm; the device was powered with two AA batteries and three D-type batteries. From above - the telescopic antenna, in front - the digital indicator. The ICF-2001 could also be powered by a 4.5 V DC external adapter (or batteries). As an alternative, you could use a 12-volt adapter, which allowed you to use the radio in the car. There were three basic versions of this device, besides at least five models for different countries with different frequency and voltage standards. The device fully covered the LW and MW bands in AM, as well as VHF in FM (87-108 MHz). But the actual “target” of this radio receiver was the broadcasting band HF. Radios such as the Sony ICF-2001D and Grundig Satellit 2000 were very popular in the 1980s, allowing you to listen to international broadcasts.
Due to its rather compact size, high sensitivity and battery power, the ICF-2001D was used as a tool for Eastern European spies working in Western European countries during the Cold War. Often, agencies like the KGB, the GRU and the Stasi gave money to their Western spies to buy such a receiver in local stores.
With the help of the receiver, the spies listened to East European stations operating in the short wave range. Hidden in numbers, secret messages and instructions for the spy were decrypted using the One-Time Pad. Immediately after deciphering the messages, he was destroyed - the mission was considered accomplished. Messages were sent back to the spy center by courier, through "dead mailboxes" (caches intended for secret message forwarding agents).
A vivid example of the use of ICF-2001D in international espionage is a series of cases against US citizens from 2001 to 2009. In the homes of subjects spying on the US for Cuba, the FBI discovered Sony ICF-2010 (the US version of ICF-2001D).
The first case is the case against Ana Belen Montes (February 28, 1957), who worked in the United States Military Intelligence (DIA) and held the post of senior Cuban analyst. From 1985 until her arrest in 2001, she spied on Cuba’s side, having managed to transfer a lot of documentation and confidential military information to Cubans.
Before the arrest, on September 21, 2001, the FBI, during a search of Ana's apartment, found evidence of using the One-Time Pade (OTP) on a laptop. A Sony receiver was found that served to receive One-Time Pade (OTP) messages from Cuban stations tuned to 7887 kHz. Ana received a clear instruction from the Cuban Intelligence Service (CuIS) to destroy the data on the laptop after use - but did not have time to do it. As a result, the FBI managed to get an OTP message.
The author of The Art of Spying, Keith Melton, who studies the history of intelligence throughout the world, wrote that she used Sony ICF-2010 (equivalent to ICF-2001D in the USA). In a detailed 2010 document, researcher Dirk Rymanants explained how the FBI managed to crack the unbreakable OTP cipher due to the shortcomings of Cuban procedures. By pleading guilty of espionage, Montes was sentenced in October 2002 to 25 years in prison without the possibility of parole.
Failure of communications, which allowed to crack the perfect system of the Cuban spy agency
The United States was the main external facility for the Cuban Intelligence Service (CuIS). It is therefore not surprising that the CuIS personnel and agents recruited and controlled by CuIS in the United States were important targets for the FBI’s counter-intelligence efforts. In recent years, the FBI has disclosed several important operations. The link in these cases was precisely the fact that the agents received their operational reports. And why, despite the use of Cuban's unbreakable cryptographic system, the FBI was able to decipher some of these operational messages, and subsequently provide it as evidence at the trial.
Mistakes in the CuIS messaging procedure were what contributed to the prosecution, arrest, and conviction of clandestine agents.
So, Ana Belen Montes (and a couple more agents) was charged by the federal prosecutor, her case was: “Montes communicated with the Cuban Intelligence Agency with encrypted messages and received her instructions from Cuba, using the shortwave range for transmission”.
Although a common method was used to receive prompt reports and instructions from CuIS agents, it was not the reason that led to investigations, surveillance and, ultimately, the arrest of spies. It was errors during operations that played a decisive role in these cases. Thus, the cryptographic system, which is considered perfectly safe, acted as an “accuser” and provided evidence of espionage. The spies themselves were not at all stupid people, rather even educated intellectuals. So how did this perfect system work and what led to its failure?
The usual method used by CuIS to communicate with its agents in the United States was to transmit encrypted messages using powerful shortwave transmitters located in Cuba. Messages consisted of a series of numbers dictated by voice or using Morse code.
Ana Montes / Ana Belén Montes 1985-2001

Senior Cuban analyst Ana Belen Montes (February 28, 1957) worked for 16 years at the United States Intelligence Agency (DIA) when she was arrested in 2001 on suspicion of spying for Cubans. In her stuff, the FBI found a Sony ICF-2001D receiver, a Toshiba laptop, and evidence of the use of OTP ciphers. Ana Belen Montes studied at the University of Virginia, received a diploma in international relations, and graduated from the Johns Hopkins University with a master's degree. In 1985, she began working at the Department of Justice in Washington. Her frank opinion and statements about US policy regarding Latin American countries attracted the attention of Cuban officials. Shortly after, Montes was recruited by CuIS. In 1985, Montes applied for a position at the Intelligence Agency (DIA). For many years she was a leading analyst on Cuban issues, had access to classified information.
In 1996, one of the employees told the security service that, in his opinion, Montes could be linked to Cuban intelligence. The case did not go further "denunciation", however, four years later, the FBI began searching for a Cuban agent in Washington, the same official contacted the FBI and ... an investigation began.
In the same year, Ana received instructions from CuIS to purchase a laptop, with her she received computer diskettes for decrypting radio messages and newsletters from CuIS. A shortwave radio was used to listen to messages broadcast on the Cuban Atencion station. The transmitted number of numbers was decrypted on her computer into readable text using floppy disks from CuIS. Each radio message consisted of 150 groups, five digits each, it was a typical Atencion format.
Montes also received a floppy disk and to encrypt messages received, secret information. She saved the encrypted messages on other diskettes, and then transferred them herself (or through someone) to her "conductor". She was instructed to use the “WIPE” program (secure file deletion) every time she decrypted or encrypted something on her laptop. For organizing meetings on “floppy disk sharing,” she called a pager using phone cards (specific pager codes were used to transmit a particular message).
The FBI was able to gather enough evidence against Ana. During the search of the apartment Montes was found a laptop, and his hard drive - copied. During the analysis, a copy of the hard disk was able to recover much of the deleted information. The FBI found fragments of instructions on how to receive encrypted messages. It became clear that Montes received the messages and decrypted them on her computer.
Convenience and speed vs safety.
But what went wrong? The use of a computer by the agent for communications is the first major mistake made by CuIS. No computer is 100% protected, because information is often stored in temporary files or swap. Data remains on the hard disk, even after deletion. Although the instruction from CuIS required the use of the WIPE program, Ana did not seem to run the program all the time or the program did not work correctly at some point. Nevertheless, it is impossible to call this an agent’s error, rather, it’s a CuIS procedural error. Providing the highest level of precaution, rather than relying on strict adherence to agent safety procedures, was a direct task of CuIS. Moreover, using a computer for espionage and clandestine purposes is already a bad idea. And even if the agent completely “cleans up” his computer, he may forget to completely delete the information on a diskette or flash drive.
Дальнейший анализ показал вторую ошибку CuIS. Жесткий диск содержал данные, состоящие из 150 групп с 5 цифрами в каждой. В архивах ФБР уже хранились перехваченные сообщения идентичные по структуре, потому не составило труда определить, что данная информация поступала с кубинской станции «Atencion».
Непонятен оставался тот факт, почему CuIS отдали предпочтение «программному обеспечению» взамен самой надежной системе ручного шифрования. «Ручной» процесс обработки данных на протяжении многих лет доказывал преимущества one-time pad — легкость и безопасность уничтожения (например, сжигание) доказательств, без следов. С цифровыми носителями процесс обстоял гораздо сложнее. Да и процесс ручного дешифрования очень прост в освоении и применении. Чтобы расшифровать сообщение, состоящее из 150 групп, потребовалось бы не более 30-40 минут.
Случай с Аной Белен ясно показывает, как вы можете превратить совершенно безопасную схему шифрования с помощью «карандаша и бумаги» в небезопасное компьютерное приложение. Разумеется, кубинская разведка не совсем осознавала тот факт, что переход с ручного на программное шифрование требует решения многих новых проблем для обеспечения полной безопасности метода. Это яркий пример неумелого соединения нерушимого метода и небезопасного его применения на ПК.
В 1 части статьи были использованы такие источники Crypto Museum , Рэм Красильников «Призраки в смокингах. Лубянка против американских дипломатов-шпионов.», Андрей Троицкий «Знак шпиона».
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4 RAM).
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/410329/