Cowrie Hanipot Attack Analysis
Statistics for 24 hours after installing a hanipot at the Digital Ocean site in Singapore
Our super class map shows unique ASNs that have been connected to our Cowrie handheld in 24 hours. Yellow corresponds to SSH connections, and red to Telnet. Such animations often impress a company's board of directors, which allows them to knock out more funding for safety and resources. Nevertheless, the map has some value, clearly demonstrating the geographical and organizational distribution of the sources of attack on our host in just 24 hours. The animation does not reflect the amount of traffic from each source.
The Pew Pew card is a cyber attack visualization , usually animated and very beautiful. This is a fashionable way to sell your product, notorious for being used by Norse Corp. The company ended badly: it turned out that beautiful animashki were their only merit, and for analysis they used fragmentary data.
For those who want to develop an attack map for a large screen in the operations center (your boss will like it), there is a leafletjs library. We combine it with the leaflet migration layer plugin, the Maxmind GeoIP service - and that's it .

Hanipot is a system that is placed on the network specifically to lure intruders. Connections to the system are usually illegal and allow an intruder to be detected using detailed logs. Logs retain not only the usual information about the connection, but also session information, revealing the attacker's technique, tactics and procedures (TTP) .
Cowrie Hanipot is designed to record SSH and Telnet connections . Such hanipots are often put on the Internet to track the tools, scripts and hosts of attackers.

Many hosts received repeated connection attempts. This is normal, since the attacking scripts are filled with the list of credentials and they try several combinations. Cowrie hanipot is configured to accept certain username and password combinations. This is configured in the user.db file .
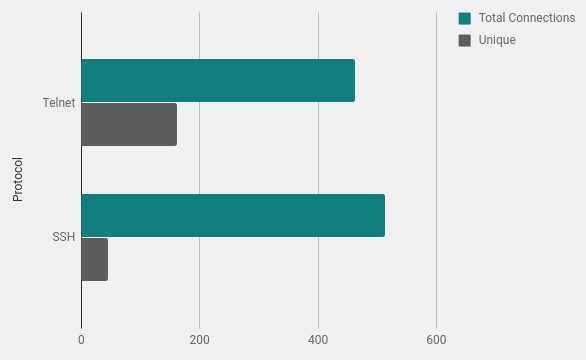
According to Maxmind's geolocation, I calculated the number of connections from each country. Brazil and China lead by a wide margin, from these countries there is often a lot of noise from scanners.

A study of the owners of network blocks (ASN) can reveal organizations with a large number of attacking hosts. Of course, and in such cases, you should always remember that many attacks come from infected hosts. It is reasonable to assume that most intruders are not so stupid as to scan the Net from a home computer.

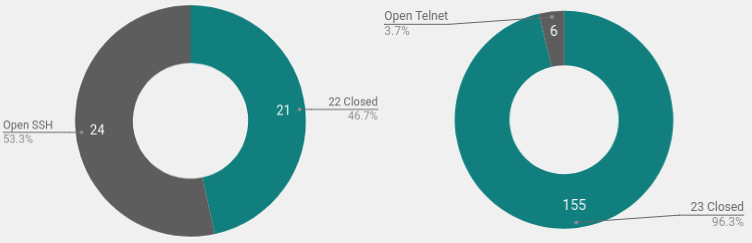
Running an IP list through the excellent Shodan API quickly identifies open port systems and what the ports are. The figure below shows the concentration of open ports by country and organization. It would be possible to identify blocks of compromised systems, but within the small sample nothing is visible, except for a large number of open ports of 500 in China .
An interesting find is a large number of systems in Brazil that do not have 22, 23 or other ports open , according to Censys and Shodan. Apparently, these are connections from end-user computers.

Censys data for ports 22 and 23 for that day showed strange. I assumed that most scans and password attacks come from bots. The script spreads through open ports, picks up passwords, and from the new system copies itself and continues to spread using the same method.
But here it can be seen that only a small number of hosts scanning telnet open port 23 to the outside. This means that the systems are either compromised in another way, or the attackers run scripts manually.
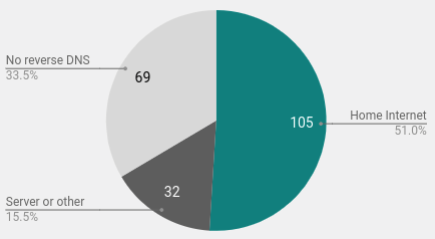
Another interesting discovery was a large number of home users in the sample. Using reverse lookup, I identified 105 connections from specific home computers. For many home connections, when you reverse DNS lookup, the host name is displayed with the words dsl, home, cable, fiber, and so on.
Recently, I wrote a short manual on how to install Cowrie hanipot on my system . As already mentioned, in our case Digital Ocean VPS was used in Singapore. For 24 hours of analysis, the cost was literally a few cents, and the time to build the system was 30 minutes.
Instead of running Cowrie on the Internet and catching all the noise, you can benefit from the hanipot on the local network. Stand by notification if requests go to certain ports. This is either an intruder within the network, or a curious employee, or a vulnerability scan.
After watching the actions of the attackers for a day, it becomes clear that it is impossible to isolate an obvious source of attacks in some organization, country, or even the operating system.
A wide distribution of sources indicates that scanning noise is constant and not associated with a particular source. Anyone who works on the Internet should make sure that his system has several levels of security . A common and effective solution for SSH is to move the service to a random high port. This does not eliminate the need for strict password protection and monitoring, but at least ensures that the logs are not clogged by constant scanning. High port connections are more likely to target attacks that might interest you.
Often, open telnet ports are on routers or other devices, so they cannot be easily moved to a high port. Information about all open ports and attack surfaces is the only way to ensure that these services are firewall-protected or disabled. If possible, you do not need to use Telnet at all, this protocol is not encrypted. If you need it without it, then carefully monitor it and use strong passwords.
Pew Pew! Let's start right away with the attack map.
Our super class map shows unique ASNs that have been connected to our Cowrie handheld in 24 hours. Yellow corresponds to SSH connections, and red to Telnet. Such animations often impress a company's board of directors, which allows them to knock out more funding for safety and resources. Nevertheless, the map has some value, clearly demonstrating the geographical and organizational distribution of the sources of attack on our host in just 24 hours. The animation does not reflect the amount of traffic from each source.
What is a Pew Pew Card?
The Pew Pew card is a cyber attack visualization , usually animated and very beautiful. This is a fashionable way to sell your product, notorious for being used by Norse Corp. The company ended badly: it turned out that beautiful animashki were their only merit, and for analysis they used fragmentary data.
Made with Leafletjs
For those who want to develop an attack map for a large screen in the operations center (your boss will like it), there is a leafletjs library. We combine it with the leaflet migration layer plugin, the Maxmind GeoIP service - and that's it .

WTF: what is Cowrie hanipot?
Hanipot is a system that is placed on the network specifically to lure intruders. Connections to the system are usually illegal and allow an intruder to be detected using detailed logs. Logs retain not only the usual information about the connection, but also session information, revealing the attacker's technique, tactics and procedures (TTP) .
Cowrie Hanipot is designed to record SSH and Telnet connections . Such hanipots are often put on the Internet to track the tools, scripts and hosts of attackers.
My message is for companies that think they are not attacking: “You are not looking well.”
- James Snook

What is in the logs?
Total number of connections
Many hosts received repeated connection attempts. This is normal, since the attacking scripts are filled with the list of credentials and they try several combinations. Cowrie hanipot is configured to accept certain username and password combinations. This is configured in the user.db file .
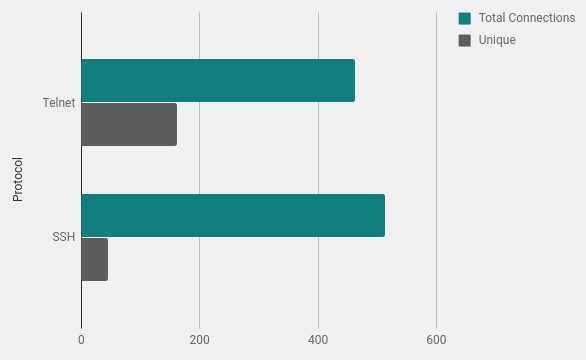
Attack geography
According to Maxmind's geolocation, I calculated the number of connections from each country. Brazil and China lead by a wide margin, from these countries there is often a lot of noise from scanners.

Network unit owner
A study of the owners of network blocks (ASN) can reveal organizations with a large number of attacking hosts. Of course, and in such cases, you should always remember that many attacks come from infected hosts. It is reasonable to assume that most intruders are not so stupid as to scan the Net from a home computer.

Open ports on attacking systems (data Shodan.io)
Running an IP list through the excellent Shodan API quickly identifies open port systems and what the ports are. The figure below shows the concentration of open ports by country and organization. It would be possible to identify blocks of compromised systems, but within the small sample nothing is visible, except for a large number of open ports of 500 in China .
An interesting find is a large number of systems in Brazil that do not have 22, 23 or other ports open , according to Censys and Shodan. Apparently, these are connections from end-user computers.

Bots? Not necessary
Censys data for ports 22 and 23 for that day showed strange. I assumed that most scans and password attacks come from bots. The script spreads through open ports, picks up passwords, and from the new system copies itself and continues to spread using the same method.
But here it can be seen that only a small number of hosts scanning telnet open port 23 to the outside. This means that the systems are either compromised in another way, or the attackers run scripts manually.

Home connections
Another interesting discovery was a large number of home users in the sample. Using reverse lookup, I identified 105 connections from specific home computers. For many home connections, when you reverse DNS lookup, the host name is displayed with the words dsl, home, cable, fiber, and so on.

Learn and explore: raise your own hanipot
Recently, I wrote a short manual on how to install Cowrie hanipot on my system . As already mentioned, in our case Digital Ocean VPS was used in Singapore. For 24 hours of analysis, the cost was literally a few cents, and the time to build the system was 30 minutes.
Instead of running Cowrie on the Internet and catching all the noise, you can benefit from the hanipot on the local network. Stand by notification if requests go to certain ports. This is either an intruder within the network, or a curious employee, or a vulnerability scan.
findings
After watching the actions of the attackers for a day, it becomes clear that it is impossible to isolate an obvious source of attacks in some organization, country, or even the operating system.
A wide distribution of sources indicates that scanning noise is constant and not associated with a particular source. Anyone who works on the Internet should make sure that his system has several levels of security . A common and effective solution for SSH is to move the service to a random high port. This does not eliminate the need for strict password protection and monitoring, but at least ensures that the logs are not clogged by constant scanning. High port connections are more likely to target attacks that might interest you.
Often, open telnet ports are on routers or other devices, so they cannot be easily moved to a high port. Information about all open ports and attack surfaces is the only way to ensure that these services are firewall-protected or disabled. If possible, you do not need to use Telnet at all, this protocol is not encrypted. If you need it without it, then carefully monitor it and use strong passwords.
Source: https://habr.com/ru/post/436076/