Repeated decentralization of the web. This time forever
In recent years, the web has become highly centralized. To regain freedom and control over the digital aspects of our lives, we need to understand how we got to this state and how to get back on the right path. This article tells the story of the decentralization of the web and the role of Tim Berners-Lee in the ongoing struggle for free and open Internet. Problems and solutions are not purely technical in nature, but rather fit into a larger socio-economic puzzle. We all have to do it together. Let's take the Internet back to this forever, and use the full potential of the web, as envisioned by its creator.
The inventor may suggest the purpose and fate of his creation, but in the end it is people who decide how to use it. John Pemberton was going to treat morphine addicts when he started brewing a potion, now known as Coca-Cola, and the Play-Doh toy plasticine was originally created as a means of cleaning walls. Alfred Nobel instituted annual awards to avoid being remembered as the inventor of dynamite.
It is noteworthy that Tim Berners-Lee never intended to control his own invention: his former employer CERN released the World Wide Web software for public use, and the network itself is designed to be decentralized so that no one has the power and right to silence other people. Such unprecedented openness led to large-scale free innovation and limitless creativity, giving voice to more than half of the world's population. She revolutionized communications, education, and business. However, the consequence of this freedom is also the fact that everyone can create things that are contrary to the spirit of the Internet, such as illegal materials and - ironically, platforms - whose main purpose is centralization .
The concept of centralization is not a problem in itself: there are good reasons for the centralized unification of people or things. But the problem arises when we are deprived of choice, misleading - we are forced to think that there is only one door to the space that we actually collectively own. Some time ago it seemed inconceivable that the fundamentally open Internet would become the basis for private services, where we pay with our personal data for some of the freedoms that are actually ours. However, today the majority of users with daily interaction are locked within the boundaries of several influential social media. These giants collect information from all over the world and accumulate this wealth in their closed space, where they are both the boss and the judge.
Since the change happened so suddenly, you may need to remember that not so long ago the web landscape looked quite different. In 2008, Iranian blogger Hosein Derakhshan was sentenced to 20 years in prison for posting on a blog. He and many others could express their critical opinion, because they had the Web as an open platform - they did not ask anyone for permission to publish. It is important to note that the hyperlink mechanism on the Internet allows blogs to link to each other, again without requiring permission in any way. This allows you to create a decentralized value network between equal people, where readers retain active and conscious control over their actions. When Derakhshan was released in 2014, he returned to a completely different Network : instead of readers with an active position, he saw passive viewers, who seemed to watch TV. Of course, web technologies have advanced, but the main foundations of the Network have degraded: in just six years, people began to use the Internet in a completely different way.
Of course, social media is not our enemy: thanks to them, the barrier to publishing short texts and photos by anyone has been reduced. Nevertheless, they work within the framework of the “winner takes all” strategy: each of the players tends to dominate, not to interact with each other, like the rest of the Internet. Unlike blogs, we usually cannot interact with publications on one network from within another: we need to move either people or data. The known problem of “fenced gardens” in social media has deteriorated significantly since 2008. Some of the “gardens” have grown to enormous size, but the walls have remained.
The main problem is that access to the dominant networks necessarily means giving up control over personal data: we can enter, but pay with our digital property. This personal data is then used to influence us imperceptibly through personalized advertising of brands, products, and even political programs. In addition, once inside, people usually form small communities — an effect that social networking algorithms specifically aim at maximizing involvement at the expense of diversity. As a result, the filter bubble isolates us in separate echo cameras, although the web and social networks have always wanted to bring people together .
Not surprisingly, this situation is reflected in the three global tasks that Tim Berners-Lee formulated in 2017:
Obviously, it is undesirable to solve these problems centrally through some kind of commission or committee. This again creates a point of failure, which - even with the best of intentions - is always vulnerable to abuse. Ultimately, the main problem is not in specific social networks, but in the hyper-centralization of data and people, that is, the authorities. We need control, but the power should belong to all people - as the right to own personal data and content created.
It becomes clear that the main obstacles are not technological ; therefore, Tim Berners-Lee calls for “gathering scientists, business, technology, government, civil society, and the arts world to fight Internet threats.” At the same time, the technological mission is entrusted to scientists and engineers: to prove that decentralized networks with personal data can globally scale and be as convenient for people as centralized platforms.
Therefore, let us begin with the technical issues of decentralization, emphasizing the role of Tim Berners-Lee in the ongoing struggle to maintain an open and decentralized Network. After a historical excursion, we will focus on what changes decentralization requires, and consider what a healthy ecosystem looks like. As a concrete implementation, we study the Solid project. In conclusion, we discuss unresolved issues and prospects for the future.
Social networks were not always the cause of centralization — and, most likely, at some point in the future, the problem will become different. The target is constantly moving: every time we begin to see a threat, it is replaced by an even larger one. Understanding these threats allows you to better understand the various aspects of decentralization.
At the time of the invention of the WWW, decentralized systems already existed in the world, including the Internet. E-mail has become an even more decentralized service than the traditional postal service, which imitated, since different mail servers directly exchanged messages. Long-forgotten protocols, such as the Network News Transfer Protocol (NNTP), have decentralized the sharing of news and articles. In short, decentralization is not a crazy idea, but rather the spirit of that time.
Therefore, from the very beginning of the design of the new hypertext system in 1989, Tim Berners-Lee took for granted that the system would be decentralized, unlike the documentation systems of the time. The main force of the web has become universality - independence from hardware and software. Decentralization was such an obvious property that it was not even mentioned. This is reflected in the original article with the announcement of the WWW , which emphasizes universal support in all operating systems, but the term “decentralization” is not mentioned at all.
The only centralized component in the network architecture is the Domain Name System (DNS). In those days, there were relatively few domains, and the owners did not change, so the problem was not so acute. Currently, millions of domain names often pass from hand to hand, thereby breaking existing links, possibly in malicious ways. By manipulating the DNS, governments can block or modify access to existing sites. Tim Berners-Lee says: now it is clear that it was better to immediately implement a distributed DNS system. Except for this, the Internet had all the components to flourish as a decentralized system.
The browser war in the 90s was the first wave of centralization, where companies were trying to gain a monopoly position and become the only software provider to access the Web. The principle of universality of web design required readability on any platform, so nothing interfered with the work of several browsers at the same time - except that they sought to dominate the market, and not to mutually beneficial coexistence. Netscape and Microsoft Internet Explorer browsers tried to entice users by introducing new features, and the share of Internet Explorer on desktops at some point exceeded 90%.
Although competition through innovation is beautiful in itself, but because of new features, browsers have become incompatible with each other and, therefore, have begun to directly threaten the universality of the Internet. Sites like “Best viewed in Internet Explorer” have appeared on the websites, as the developers could not guarantee consistent work on all platforms. If someone did not want or could not install a specific browser, then he risked losing access to such sites altogether. As a result, the IE monopoly influenced the choice of people in relation to the browser and the OS. The power on the Internet was concentrated in the hands of one company, which slowed down innovation.
The World Wide Web Consortium (W3C) was founded by Tim Berners-Lee to ensure interoperability between browsers. For this, recommendations are issued that determine the proper operation of web technologies. Although the W3C is administratively centralized, the adoption of standards represents feedback from a distributed network of participants through a consensus-based process. In the early 2000s, the problem was that Internet Explorer at critical moments deviated from the recommendations of the W3C, forcing developers to follow either actual standards or their incorrect implementation in the most popular browser.
Fortunately, the pressure from Firefox and Safari during the second war of browsers ultimately forced Microsoft to change course and focus on standards . Since 2010, no browser has owned more than 2/3 of the global market, so now compatibility is in the interests of both browser developers and web developers. Balkanization of the network due to the centralized development of the browser has largely been avoided.
Microsoft's short victory was unimportant, because the battle for centralization shifted to other areas. While each browser sought to become the default application, search engines competed to become the main entry point to the Web. Soon it did not matter what your browser is; the important thing was who gave you the search instructions. In the end, free browser development does not bring direct income, while companies are happy to pay for first place in the search.
Among the search engines immediately appeared several competitors, such as AltaVista and Lycos, but just a couple of years, Google became the leader. The centralization of the search meant that one company began to influence too much what content was available to people by changing the search results for certain conditions. Even assuming the best intentions and ignoring paid advertising, the presence of a single algorithm that makes decisions for a large number of people affects the information field. After all, there is no one objective way to determine the "best" web pages on any topic. Attempts were made to manipulate this algorithm externally, first through deceptive keywords, and then using advanced SEO techniques to improve the ranking of sites in various (sometimes questionable) ways.
With the advent of search engines, the first time monetization of user data began. Search queries of a person allow you to create a detailed profile of interests in your personal and professional life. Search engines may know more about certain aspects of a person’s life than his close friends. This profile helps you find personalized advertisements and search results, encouraging you to visit sites and buy things that you otherwise might not have bought. Although personalization is useful for many, the problem is lack of choice and control. We focus on large search engines that have accumulated the largest amount of data and show a more relevant issue. However, these search engines do not provide options - most of them accept only our personal data as payment. In addition, we don’t know how our data influences search results, let alone to control them. The growth of personalization has led to the emergence of the first filter bubbles , within which we are more likely to show results similar to those we pressed earlier.
While Google’s hegemony continues, social networks have found a more powerful way to collect and monetize our data. The social networking revolution in the 2000s prompted people to go online, leading them to various platforms for sharing text on blogs, bookmarks, photos, videos and more. After a few years, social media companies created centralized platforms to take on many of the functions that were previously distributed among several providers. In exchange for their services, these platforms store our personal data and request the right to use it. Each works in its own "fenced garden".
Like search engines, social networks give the user a linear list of content, ranked by factors and algorithms that we can minimally influence. Unlike the search, here the tape is generated without any search queries from our side - like a TV without a remote control.
The tape was carefully personalized on the basis of the data that we deliberately left on the social network, in combination with traces from the history of page views, collected without our explicit consent using trackers on third-party sites. In his lecture in 2018, Tim Berners-Lee noted that political television had long ago banned political advertising because of fears that such a direct means of influence unduly affects the masses. According to this logic, one should be much more wary of the highly personalized political advertising that modern social networks allow. Even if a person refrains from explicitly expressing very personal preferences, these preferences are reliably determined from seemingly insignificant fragments of other data . Data mining reveals a person’s sexual orientation, ethnicity, religious and political views. Subsequently, the information is used for targeted exposure.
As in previous battles for centralization, people feel pressured to join a large network. Refusal to join means to fall out of the circle of virtual communication of friends and relatives. Often for grandparents, the easiest way to see the latest photos of grandchildren is to create a Facebook or Instagram account.
That is how the digital memory of the modern generation is largely concentrated in one place, often beyond the control of the users themselves. The centralization of online activity has become so extreme forms that some Facebook users are no longer aware of the possibility of access to the Internet . Unfortunately, this paradox has become a reality in many countries where, at the initiative of Internet.org, [a “charitable” organization that Facebook founded - approx. Lane.] provides a strictly limited version of the Internet, which is a glaring violation of network neutrality.
Meanwhile, another battle unfolded in the background, this time for becoming our identity provider. More and more sites are replacing their own authentication systems with a service from large providers such as Google or Facebook. It is convenient for people with an account to log in using the Facebook button. On the rest, additional pressure is created to join the network. In both cases, these buttons are another way to track online activity. This centralization deprives us of anonymity, that is, the freedom to hide data that we consider personal.
In all the listed battles for centralization, the refrain is one theme: lack of choice. Lack of choice of browser and operating system, point of entry to the Internet, the location of storage of our personal data. Decentralization is, first of all, the creation of favorable conditions for selection by abandoning the unique place of data storage, artificially tied to the service. These two systems should be separated from each other and give the user a choice. Just as we are free to choose any combination of gadgets, operating systems and browsers to access the Internet, we must be able to interact with sites and other people without obligations with respect to one or another social platform.
The return of control over our personal data, according to Tim Berners-Lee, is accomplished by separating the storage of data from other services . This means that people can store their data where they want, at the same time using any services. To store your texts, photos and videos, we can choose any provider - or just store them on our own computer. Any third-party service with our permission will use this data, regardless of the storage location. The data repository can, although not required, provide the most important user authentication service.
This logic creates the concept of a personal data pod module , in which we store all the created information. As shown in the figure below, this can be understood literally: even the seemingly trivial part of the data, like the likes put, is stored in a private module. Although this degree of decentralization may seem extreme, remember that even supposedly trivial likes reveal deeply personal information , so it makes sense to put them under control. In addition, if a person does not depend on someone else's permission to publish data in his own module, he can put likes and comments wherever he wants, without fear of censorship and punishment.
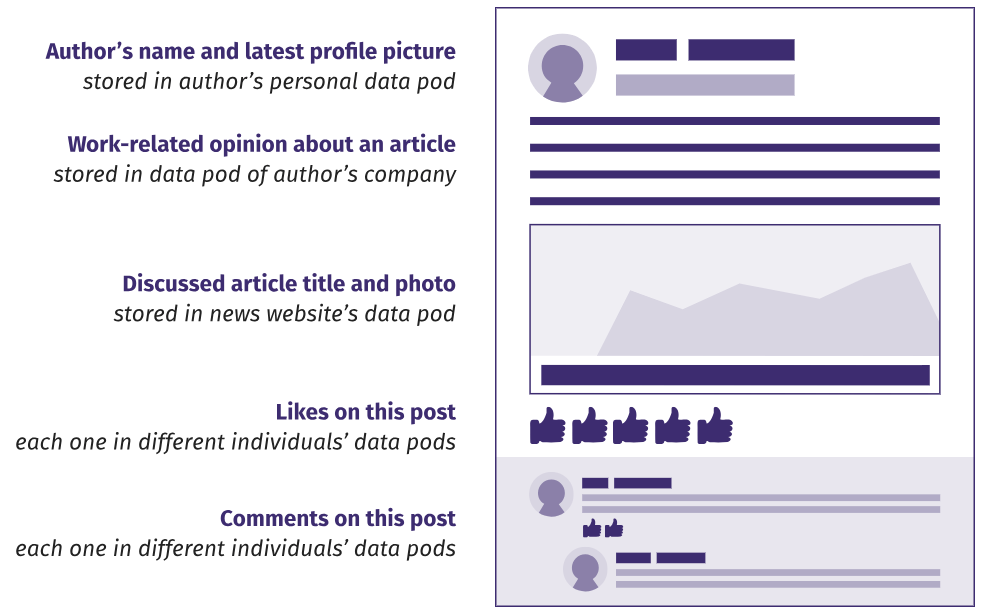
In a decentralized network, each piece of data is stored in a location chosen by the author.
This full ownership of the data provides very detailed access control: users can selectively grant friends or applications permissions to read or write certain fragments. For example, they decide whether to publish their photo and full name, who will see the likes and comments, which applications will edit the photos and posts. You can change or revoke permission at any time. Several data modules are allowed for various purposes: for example, a module for personal and family photos, a module with rules for storing professional data for work, a university module with training materials and assessments. After creating the module, the person decides what data to store.
Choosing a place to store your own data, we prevent unauthorized access and operation. We are no longer required to pay with our data for the services of Internet companies. Moreover, we can protect the most sensitive parts of the data, keeping them with us, limiting access only to those people and services that really need it, and only for a certain time.
When people themselves store their data, it will become impossible to cash in on them. These economic changes can be accelerated with legislation like the GDPR and explaining the danger of centralization to the population, given the recent scandals with leaks of private information like the stories of Equifax and Facebook. Therefore, new business models are needed.
Decentralization requires avoiding isolated applications. As shown in the figure below, current web applications combine data and service. Because of this connection, our LinkedIn contacts cannot comment on our Facebook photos, and an invitation to an event on Facebook cannot be shown on the Doodle calendar. On the other hand, distributed applications act as views on top of our and other data modules. Having received a special permission, the social tape application can take from the module the photos uploaded there by the photo gallery application. Events from the personal calendar with the status “visible to all” are added to the same tape. Friends can access individual pieces of our data through any application they want to use.

Now, centralized web applications act as repositories that do not communicate with each other. Distributed applications work as general views (view) on top of personal data modules.
Since the choice of data and service provider is no longer dependent on data storage, separate data and service markets arise. The figure below shows that centralized applications are now competing for ownership of data. Thus, people cannot easily switch to a more convenient application, and data transfer is technically challenging, if possible at all. In addition, new potentially more convenient applications are experiencing problems with entering the market because they do not yet have enough data. With decentralized applications, people choose a service provider and storage location separately, and companies independently compete in both markets. At both levels, competition is based solely on the quality of services, the ratio of functions to cost.
This independence means that we can freely switch between providers of data and services, without requiring our friends to make the same choice. This destroys the walls between the "gardens" because the services interact freely with each other. Providers of data and services can develop independently, providing a faster and more creative cycle of innovation. Anyone can enter any market and attract customers if his service is better than others without requiring control over user data.
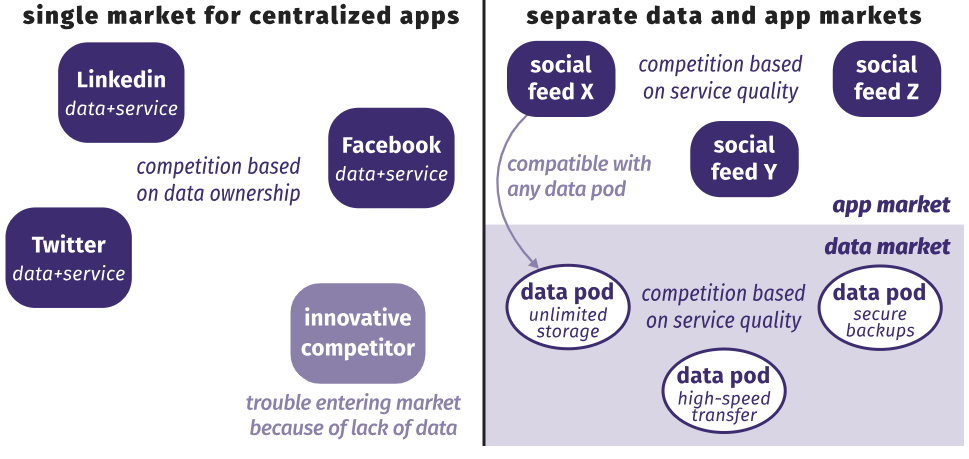
Centralized applications compete in the same market for owning our data. In a distributed network, data and service providers compete in different markets.
To implement this concept, Tim Berners-Lee launched the Solid project . It includes specifications for interoperability, server, client, and application implementations , as well as the developer community . Next, we discuss some of the unique features of Solid.
The goal of Solid is the empowerment of people through personal data management as an analogue of corporate Personal Data Management systems. A Solid server or data module is the web equivalent of a hard disk where we store arbitrary documents, and Solid applications are similar to programs for a personal computer, only opening documents from Solid servers on the Internet. Unlike real hard drives, Solid servers are usually open to the world, so they need detailed access control options. They set who can view or edit which documents. Tim Berners-Lee himself set an example, using Solid in his personal and professional life for several years.
Чтобы это работало в сетевом масштабе, данные в разных модулях должны быть связаны ссылками, как гипертекстовые документы. Для этого Solid использует формат Linked Data : каждый фрагмент данных можно связать с любым другим. Например, комментарий в модуле одного пользователя прикрепляется к фотографии в модуле другого, при этом оба пользователя остаются владельцами своих данных. В момент выполнения Solid-приложения данные интегрируются из нескольких источников и объединяются в единое целое.
Модули обеспечивают и децентрализованную аутентификацию. Человек выбирает так называемый WebID — уникальный веб-адрес для идентификации. Этот адрес указывает на общий профиль, и пользователь заходит в любой модуль со своим собственным WebID без необходимости отдельной аутентификации на каждом сайте или использования централизованной платформы.
Одним из важнейших аспектов Solid является то, что он обеспечивает платформу для чтения-записи, каким и являлось первоначальное предназначение WWW . Хотя «запись» всегда была технически возможна, в том смысле, что любой мог запустить собственный сайт, но революции Веб 2.0 и социальных сетей должны были значительно упростить процесс. Успех этих платформах частично обязан их интерактивности: теперь каждый способен создавать и публиковать контент в любое время, особенно через мобильные устройства.
Solid должен так же легко публиковать контент. Разница в том, что мы публикуем в собственные модули данных, а не в приложение. При этом гарантируется свобода самовыражения без риска цензуры. Для обеспечения максимальной совместимости связанные данные должны храниться с использованием технологий Семантического веба , которые увязывают фрагменты данных с их значением. Таким образом, приложения понимают (фрагменты) данных друг друга, не договариваясь о формате.
Нужен также механизм информирования, когда объекты в модулях создаются или изменяются — особенно если речь о комментариях. Это обеспечивает технология Linked Data Notifications : небольшие автоматические сообщения, как email, которые различные модули данных отправляют друг другу. Объединив эти технологии, Solid реализует концепцию Read-Write Linked Data, гарантирую каждому участие в Вебе Данных.
Трансформируя владение данными и роль приложений в распределённой экосистеме, Solid нарушит многие централизованные процессы в интернете. Теперь можно исключить посредников, контролирующих эти процессы, что стимулирует инновации во многих областях.
Первая очевидная цель — социальные отношения между людьми. Благодаря Solid появляется простой и конфиденциальный способ обмена мультимедийными файлами с друзьями, коллегами и родственниками. Другие примеры — совместная работа над различными документами с чётким контролем доступа: организация встреч и мероприятий — опять же с полным владением данными, выбором приложения и хранилища, синхронизацией между приложениями и т. д.
Кроме того, технологически Solid способен произвести революцию в целых отраслях, таких как научные публикации. Текущий процесс предполагает, что автор загружает рукопись на централизованную платформу, где её оценивает закрытая группа рецензентов. После одобрения рукопись публикуется в виде статьи, а затем становится доступной для общественности, возможно, за отдельную плату. Этот довольно длительный процесс. Широкое научное сообщество может прочитать статью только в самом конце, если её примут. Процесс ещё и непрозрачный, поскольку от общественности скрыты ценные детали: рецензии и правка статей. Как правило, обратная связь возможна только через аналогичный медленный процесс. Вместо этого распределённое приложение для публикации статей, такое как dokieli , позволяет исследователям самостоятельно публиковать рукописи в собственном модуле Solid. Комментарии коллег хранятся в их собственных модулях, гарантируя свободу выражения любому, кто хочет принять участие. Все результаты остаются открыты для комментариев даже после публикации в вебе.
Повторная децентрализация веба в соответствии с концепцией Solid поможет одолеть три проблемы, которые сформулировал Тим Бернерс-Ли . Мы можем вернуть контроль над личными данными, храня их в собственных модулях. Дезинформация блокируется, потому что свободный выбор приложений позволяет контролировать свою ленту новостей — а любая информация прослеживается до самого источника. Политическая реклама становится более прозрачной, поскольку каждый решает, кому и какие открыть фрагменты данных. Более того, разделение рынков данных и услуг позволяет рассмотреть другие варианты, вообще без рекламы. Хотя Solid не в полной мере решает все проблемы, но владение данными и свобода выбора — это главное.
Впрочем, за свободу всегда нужно платить: победа личных прав и свободы слова одновременно способствует незаконной активности, потому что распределённые сети затрудняют контроль за информацией. Конечно, это сложный вопрос, поскольку в некоторых странах объявляют незаконными высказывания, которые вполне законны в другом месте. Интригующий пример — возросшая популярность децентрализованной социальной сети Mastodon в Японии : когда Twitter начал удалять изображения, сомнительные по американским нормам, японские пользователи начали публиковать их на платформах с меньшей цензурой.
Нам придётся принять этот компромисс между свободой и контролем. В отсутствие общепризнанных норм централизованная фильтрация запрещённого контента никогда не будет адекватным решением.
Это подводит нас к другому аспекту децентрализации, а именно к противоречию между свободой и универсальностью. Парадокс свободы гласит, что человек может стать свободным, только если подчинится определённым правилам. Проще говоря, мы свободны взять велосипед и ехать куда угодно — если только держимся правой стороны дороги (в нескольких странах левой). Не соблюдая это правило, мы никуда не доедем без аварий. Поскольку универсальность всегда была главной задачей веба , распределённые сообщества должны согласовать некоторые базовые рамки децентрализации. Как и с универсальностью браузеров, консорциум W3C играет важную роль в создании стандартов для взаимодействия модулей данных и приложений. К счастью, не нужно согласовывать все детали. Формат Linked Data позволяет заключать многоуровневые соглашения, в которых несколько правил распространяются на многих участников, а дополнительные правила согласовываются меньшими группами по мере необходимости.
Важно отметить, что Solid не создаётся для борьбы с конкретными компаниями, такими как Google, Facebook или Twitter. Проект бросает вызов централизации в целом, поскольку многие проблемы этих компаний вызваны централизацией и бизнес-моделью владения данными. Мы подошли к тому, что компании обладают таким объёмом данных, что уже не могут предсказать долгосрочные последствия такой централизации . Поэтому неразумно и дальше в качестве предлога полагаться на «информированное согласие» , поскольку ни один человек не в силах понять, к чему в конечном итоге приведёт отказ от контроля над малыми или большими фрагментами его данных. Таким образом, хранение своих данных в надёжном месте со свободой выбора и детализированной моделью разрешений — единственный безопасный вариант.
Никто из нас не мечтает о Сети без крупных игроков. Совсем наоборот: Тим Бернерс-Ли настаивает, что Сеть всегда должна масштабироваться от очень маленьких к очень большим участникам. Проблема в том, что в настоящее время очень большие участники пытаются подавить остальных, что ставит под угрозу свободы, которыми мы пользовались в течение многих лет. Как указывалось выше, децентрализация — это прежде всего свобода выбора: у людей должна быть возможность свободно вступать в большие или малые сообщества. И хотя перед нами стоит несколько технических проблем, в том числе гарантия аналогичного удобства и скорости работы, как у централизованных платформ, Solid представляет собой первое жизнеспособное техническое решение. Теперь мы должны закрепить прогресс в социально-экономической реальности, чтобы полностью децентрализовать веб. Только когда нам удастся вернуть контроль и свободу выбора для самых ценных цифровых активов, мы сможем по-настоящему сказать: это Сеть для всех .
Power to the people
The inventor may suggest the purpose and fate of his creation, but in the end it is people who decide how to use it. John Pemberton was going to treat morphine addicts when he started brewing a potion, now known as Coca-Cola, and the Play-Doh toy plasticine was originally created as a means of cleaning walls. Alfred Nobel instituted annual awards to avoid being remembered as the inventor of dynamite.
It is noteworthy that Tim Berners-Lee never intended to control his own invention: his former employer CERN released the World Wide Web software for public use, and the network itself is designed to be decentralized so that no one has the power and right to silence other people. Such unprecedented openness led to large-scale free innovation and limitless creativity, giving voice to more than half of the world's population. She revolutionized communications, education, and business. However, the consequence of this freedom is also the fact that everyone can create things that are contrary to the spirit of the Internet, such as illegal materials and - ironically, platforms - whose main purpose is centralization .
The concept of centralization is not a problem in itself: there are good reasons for the centralized unification of people or things. But the problem arises when we are deprived of choice, misleading - we are forced to think that there is only one door to the space that we actually collectively own. Some time ago it seemed inconceivable that the fundamentally open Internet would become the basis for private services, where we pay with our personal data for some of the freedoms that are actually ours. However, today the majority of users with daily interaction are locked within the boundaries of several influential social media. These giants collect information from all over the world and accumulate this wealth in their closed space, where they are both the boss and the judge.
Since the change happened so suddenly, you may need to remember that not so long ago the web landscape looked quite different. In 2008, Iranian blogger Hosein Derakhshan was sentenced to 20 years in prison for posting on a blog. He and many others could express their critical opinion, because they had the Web as an open platform - they did not ask anyone for permission to publish. It is important to note that the hyperlink mechanism on the Internet allows blogs to link to each other, again without requiring permission in any way. This allows you to create a decentralized value network between equal people, where readers retain active and conscious control over their actions. When Derakhshan was released in 2014, he returned to a completely different Network : instead of readers with an active position, he saw passive viewers, who seemed to watch TV. Of course, web technologies have advanced, but the main foundations of the Network have degraded: in just six years, people began to use the Internet in a completely different way.
Of course, social media is not our enemy: thanks to them, the barrier to publishing short texts and photos by anyone has been reduced. Nevertheless, they work within the framework of the “winner takes all” strategy: each of the players tends to dominate, not to interact with each other, like the rest of the Internet. Unlike blogs, we usually cannot interact with publications on one network from within another: we need to move either people or data. The known problem of “fenced gardens” in social media has deteriorated significantly since 2008. Some of the “gardens” have grown to enormous size, but the walls have remained.
The main problem is that access to the dominant networks necessarily means giving up control over personal data: we can enter, but pay with our digital property. This personal data is then used to influence us imperceptibly through personalized advertising of brands, products, and even political programs. In addition, once inside, people usually form small communities — an effect that social networking algorithms specifically aim at maximizing involvement at the expense of diversity. As a result, the filter bubble isolates us in separate echo cameras, although the web and social networks have always wanted to bring people together .
Not surprisingly, this situation is reflected in the three global tasks that Tim Berners-Lee formulated in 2017:
- regain control of our personal data;
- prevent the spread of misinformation;
- ensure transparency of political advertising.
Obviously, it is undesirable to solve these problems centrally through some kind of commission or committee. This again creates a point of failure, which - even with the best of intentions - is always vulnerable to abuse. Ultimately, the main problem is not in specific social networks, but in the hyper-centralization of data and people, that is, the authorities. We need control, but the power should belong to all people - as the right to own personal data and content created.
It becomes clear that the main obstacles are not technological ; therefore, Tim Berners-Lee calls for “gathering scientists, business, technology, government, civil society, and the arts world to fight Internet threats.” At the same time, the technological mission is entrusted to scientists and engineers: to prove that decentralized networks with personal data can globally scale and be as convenient for people as centralized platforms.
Therefore, let us begin with the technical issues of decentralization, emphasizing the role of Tim Berners-Lee in the ongoing struggle to maintain an open and decentralized Network. After a historical excursion, we will focus on what changes decentralization requires, and consider what a healthy ecosystem looks like. As a concrete implementation, we study the Solid project. In conclusion, we discuss unresolved issues and prospects for the future.
A brief history of (de) web centralization
Social networks were not always the cause of centralization — and, most likely, at some point in the future, the problem will become different. The target is constantly moving: every time we begin to see a threat, it is replaced by an even larger one. Understanding these threats allows you to better understand the various aspects of decentralization.
Decentralization as an unspoken assumption
At the time of the invention of the WWW, decentralized systems already existed in the world, including the Internet. E-mail has become an even more decentralized service than the traditional postal service, which imitated, since different mail servers directly exchanged messages. Long-forgotten protocols, such as the Network News Transfer Protocol (NNTP), have decentralized the sharing of news and articles. In short, decentralization is not a crazy idea, but rather the spirit of that time.
Therefore, from the very beginning of the design of the new hypertext system in 1989, Tim Berners-Lee took for granted that the system would be decentralized, unlike the documentation systems of the time. The main force of the web has become universality - independence from hardware and software. Decentralization was such an obvious property that it was not even mentioned. This is reflected in the original article with the announcement of the WWW , which emphasizes universal support in all operating systems, but the term “decentralization” is not mentioned at all.
The only centralized component in the network architecture is the Domain Name System (DNS). In those days, there were relatively few domains, and the owners did not change, so the problem was not so acute. Currently, millions of domain names often pass from hand to hand, thereby breaking existing links, possibly in malicious ways. By manipulating the DNS, governments can block or modify access to existing sites. Tim Berners-Lee says: now it is clear that it was better to immediately implement a distributed DNS system. Except for this, the Internet had all the components to flourish as a decentralized system.
Battle for desktops
The browser war in the 90s was the first wave of centralization, where companies were trying to gain a monopoly position and become the only software provider to access the Web. The principle of universality of web design required readability on any platform, so nothing interfered with the work of several browsers at the same time - except that they sought to dominate the market, and not to mutually beneficial coexistence. Netscape and Microsoft Internet Explorer browsers tried to entice users by introducing new features, and the share of Internet Explorer on desktops at some point exceeded 90%.
Although competition through innovation is beautiful in itself, but because of new features, browsers have become incompatible with each other and, therefore, have begun to directly threaten the universality of the Internet. Sites like “Best viewed in Internet Explorer” have appeared on the websites, as the developers could not guarantee consistent work on all platforms. If someone did not want or could not install a specific browser, then he risked losing access to such sites altogether. As a result, the IE monopoly influenced the choice of people in relation to the browser and the OS. The power on the Internet was concentrated in the hands of one company, which slowed down innovation.
The World Wide Web Consortium (W3C) was founded by Tim Berners-Lee to ensure interoperability between browsers. For this, recommendations are issued that determine the proper operation of web technologies. Although the W3C is administratively centralized, the adoption of standards represents feedback from a distributed network of participants through a consensus-based process. In the early 2000s, the problem was that Internet Explorer at critical moments deviated from the recommendations of the W3C, forcing developers to follow either actual standards or their incorrect implementation in the most popular browser.
Fortunately, the pressure from Firefox and Safari during the second war of browsers ultimately forced Microsoft to change course and focus on standards . Since 2010, no browser has owned more than 2/3 of the global market, so now compatibility is in the interests of both browser developers and web developers. Balkanization of the network due to the centralized development of the browser has largely been avoided.
Battle of the search engines
Microsoft's short victory was unimportant, because the battle for centralization shifted to other areas. While each browser sought to become the default application, search engines competed to become the main entry point to the Web. Soon it did not matter what your browser is; the important thing was who gave you the search instructions. In the end, free browser development does not bring direct income, while companies are happy to pay for first place in the search.
Among the search engines immediately appeared several competitors, such as AltaVista and Lycos, but just a couple of years, Google became the leader. The centralization of the search meant that one company began to influence too much what content was available to people by changing the search results for certain conditions. Even assuming the best intentions and ignoring paid advertising, the presence of a single algorithm that makes decisions for a large number of people affects the information field. After all, there is no one objective way to determine the "best" web pages on any topic. Attempts were made to manipulate this algorithm externally, first through deceptive keywords, and then using advanced SEO techniques to improve the ranking of sites in various (sometimes questionable) ways.
With the advent of search engines, the first time monetization of user data began. Search queries of a person allow you to create a detailed profile of interests in your personal and professional life. Search engines may know more about certain aspects of a person’s life than his close friends. This profile helps you find personalized advertisements and search results, encouraging you to visit sites and buy things that you otherwise might not have bought. Although personalization is useful for many, the problem is lack of choice and control. We focus on large search engines that have accumulated the largest amount of data and show a more relevant issue. However, these search engines do not provide options - most of them accept only our personal data as payment. In addition, we don’t know how our data influences search results, let alone to control them. The growth of personalization has led to the emergence of the first filter bubbles , within which we are more likely to show results similar to those we pressed earlier.
Battle for our personal data and identity
While Google’s hegemony continues, social networks have found a more powerful way to collect and monetize our data. The social networking revolution in the 2000s prompted people to go online, leading them to various platforms for sharing text on blogs, bookmarks, photos, videos and more. After a few years, social media companies created centralized platforms to take on many of the functions that were previously distributed among several providers. In exchange for their services, these platforms store our personal data and request the right to use it. Each works in its own "fenced garden".
Like search engines, social networks give the user a linear list of content, ranked by factors and algorithms that we can minimally influence. Unlike the search, here the tape is generated without any search queries from our side - like a TV without a remote control.
The tape was carefully personalized on the basis of the data that we deliberately left on the social network, in combination with traces from the history of page views, collected without our explicit consent using trackers on third-party sites. In his lecture in 2018, Tim Berners-Lee noted that political television had long ago banned political advertising because of fears that such a direct means of influence unduly affects the masses. According to this logic, one should be much more wary of the highly personalized political advertising that modern social networks allow. Even if a person refrains from explicitly expressing very personal preferences, these preferences are reliably determined from seemingly insignificant fragments of other data . Data mining reveals a person’s sexual orientation, ethnicity, religious and political views. Subsequently, the information is used for targeted exposure.
As in previous battles for centralization, people feel pressured to join a large network. Refusal to join means to fall out of the circle of virtual communication of friends and relatives. Often for grandparents, the easiest way to see the latest photos of grandchildren is to create a Facebook or Instagram account.
That is how the digital memory of the modern generation is largely concentrated in one place, often beyond the control of the users themselves. The centralization of online activity has become so extreme forms that some Facebook users are no longer aware of the possibility of access to the Internet . Unfortunately, this paradox has become a reality in many countries where, at the initiative of Internet.org, [a “charitable” organization that Facebook founded - approx. Lane.] provides a strictly limited version of the Internet, which is a glaring violation of network neutrality.
Meanwhile, another battle unfolded in the background, this time for becoming our identity provider. More and more sites are replacing their own authentication systems with a service from large providers such as Google or Facebook. It is convenient for people with an account to log in using the Facebook button. On the rest, additional pressure is created to join the network. In both cases, these buttons are another way to track online activity. This centralization deprives us of anonymity, that is, the freedom to hide data that we consider personal.
Separation of data and services
In all the listed battles for centralization, the refrain is one theme: lack of choice. Lack of choice of browser and operating system, point of entry to the Internet, the location of storage of our personal data. Decentralization is, first of all, the creation of favorable conditions for selection by abandoning the unique place of data storage, artificially tied to the service. These two systems should be separated from each other and give the user a choice. Just as we are free to choose any combination of gadgets, operating systems and browsers to access the Internet, we must be able to interact with sites and other people without obligations with respect to one or another social platform.
The return of control over our personal data, according to Tim Berners-Lee, is accomplished by separating the storage of data from other services . This means that people can store their data where they want, at the same time using any services. To store your texts, photos and videos, we can choose any provider - or just store them on our own computer. Any third-party service with our permission will use this data, regardless of the storage location. The data repository can, although not required, provide the most important user authentication service.
This logic creates the concept of a personal data pod module , in which we store all the created information. As shown in the figure below, this can be understood literally: even the seemingly trivial part of the data, like the likes put, is stored in a private module. Although this degree of decentralization may seem extreme, remember that even supposedly trivial likes reveal deeply personal information , so it makes sense to put them under control. In addition, if a person does not depend on someone else's permission to publish data in his own module, he can put likes and comments wherever he wants, without fear of censorship and punishment.

In a decentralized network, each piece of data is stored in a location chosen by the author.
This full ownership of the data provides very detailed access control: users can selectively grant friends or applications permissions to read or write certain fragments. For example, they decide whether to publish their photo and full name, who will see the likes and comments, which applications will edit the photos and posts. You can change or revoke permission at any time. Several data modules are allowed for various purposes: for example, a module for personal and family photos, a module with rules for storing professional data for work, a university module with training materials and assessments. After creating the module, the person decides what data to store.
Choosing a place to store your own data, we prevent unauthorized access and operation. We are no longer required to pay with our data for the services of Internet companies. Moreover, we can protect the most sensitive parts of the data, keeping them with us, limiting access only to those people and services that really need it, and only for a certain time.
Independent innovation after sharing data and services
When people themselves store their data, it will become impossible to cash in on them. These economic changes can be accelerated with legislation like the GDPR and explaining the danger of centralization to the population, given the recent scandals with leaks of private information like the stories of Equifax and Facebook. Therefore, new business models are needed.
Decentralization requires avoiding isolated applications. As shown in the figure below, current web applications combine data and service. Because of this connection, our LinkedIn contacts cannot comment on our Facebook photos, and an invitation to an event on Facebook cannot be shown on the Doodle calendar. On the other hand, distributed applications act as views on top of our and other data modules. Having received a special permission, the social tape application can take from the module the photos uploaded there by the photo gallery application. Events from the personal calendar with the status “visible to all” are added to the same tape. Friends can access individual pieces of our data through any application they want to use.

Now, centralized web applications act as repositories that do not communicate with each other. Distributed applications work as general views (view) on top of personal data modules.
Since the choice of data and service provider is no longer dependent on data storage, separate data and service markets arise. The figure below shows that centralized applications are now competing for ownership of data. Thus, people cannot easily switch to a more convenient application, and data transfer is technically challenging, if possible at all. In addition, new potentially more convenient applications are experiencing problems with entering the market because they do not yet have enough data. With decentralized applications, people choose a service provider and storage location separately, and companies independently compete in both markets. At both levels, competition is based solely on the quality of services, the ratio of functions to cost.
This independence means that we can freely switch between providers of data and services, without requiring our friends to make the same choice. This destroys the walls between the "gardens" because the services interact freely with each other. Providers of data and services can develop independently, providing a faster and more creative cycle of innovation. Anyone can enter any market and attract customers if his service is better than others without requiring control over user data.

Centralized applications compete in the same market for owning our data. In a distributed network, data and service providers compete in different markets.
Solid project
To implement this concept, Tim Berners-Lee launched the Solid project . It includes specifications for interoperability, server, client, and application implementations , as well as the developer community . Next, we discuss some of the unique features of Solid.
Linking and integration of personal data
The goal of Solid is the empowerment of people through personal data management as an analogue of corporate Personal Data Management systems. A Solid server or data module is the web equivalent of a hard disk where we store arbitrary documents, and Solid applications are similar to programs for a personal computer, only opening documents from Solid servers on the Internet. Unlike real hard drives, Solid servers are usually open to the world, so they need detailed access control options. They set who can view or edit which documents. Tim Berners-Lee himself set an example, using Solid in his personal and professional life for several years.
Чтобы это работало в сетевом масштабе, данные в разных модулях должны быть связаны ссылками, как гипертекстовые документы. Для этого Solid использует формат Linked Data : каждый фрагмент данных можно связать с любым другим. Например, комментарий в модуле одного пользователя прикрепляется к фотографии в модуле другого, при этом оба пользователя остаются владельцами своих данных. В момент выполнения Solid-приложения данные интегрируются из нескольких источников и объединяются в единое целое.
Модули обеспечивают и децентрализованную аутентификацию. Человек выбирает так называемый WebID — уникальный веб-адрес для идентификации. Этот адрес указывает на общий профиль, и пользователь заходит в любой модуль со своим собственным WebID без необходимости отдельной аутентификации на каждом сайте или использования централизованной платформы.
Веб для чтения-записи
Одним из важнейших аспектов Solid является то, что он обеспечивает платформу для чтения-записи, каким и являлось первоначальное предназначение WWW . Хотя «запись» всегда была технически возможна, в том смысле, что любой мог запустить собственный сайт, но революции Веб 2.0 и социальных сетей должны были значительно упростить процесс. Успех этих платформах частично обязан их интерактивности: теперь каждый способен создавать и публиковать контент в любое время, особенно через мобильные устройства.
Solid должен так же легко публиковать контент. Разница в том, что мы публикуем в собственные модули данных, а не в приложение. При этом гарантируется свобода самовыражения без риска цензуры. Для обеспечения максимальной совместимости связанные данные должны храниться с использованием технологий Семантического веба , которые увязывают фрагменты данных с их значением. Таким образом, приложения понимают (фрагменты) данных друг друга, не договариваясь о формате.
Нужен также механизм информирования, когда объекты в модулях создаются или изменяются — особенно если речь о комментариях. Это обеспечивает технология Linked Data Notifications : небольшие автоматические сообщения, как email, которые различные модули данных отправляют друг другу. Объединив эти технологии, Solid реализует концепцию Read-Write Linked Data, гарантирую каждому участие в Вебе Данных.
Революционный потенциал
Трансформируя владение данными и роль приложений в распределённой экосистеме, Solid нарушит многие централизованные процессы в интернете. Теперь можно исключить посредников, контролирующих эти процессы, что стимулирует инновации во многих областях.
Первая очевидная цель — социальные отношения между людьми. Благодаря Solid появляется простой и конфиденциальный способ обмена мультимедийными файлами с друзьями, коллегами и родственниками. Другие примеры — совместная работа над различными документами с чётким контролем доступа: организация встреч и мероприятий — опять же с полным владением данными, выбором приложения и хранилища, синхронизацией между приложениями и т. д.
Кроме того, технологически Solid способен произвести революцию в целых отраслях, таких как научные публикации. Текущий процесс предполагает, что автор загружает рукопись на централизованную платформу, где её оценивает закрытая группа рецензентов. После одобрения рукопись публикуется в виде статьи, а затем становится доступной для общественности, возможно, за отдельную плату. Этот довольно длительный процесс. Широкое научное сообщество может прочитать статью только в самом конце, если её примут. Процесс ещё и непрозрачный, поскольку от общественности скрыты ценные детали: рецензии и правка статей. Как правило, обратная связь возможна только через аналогичный медленный процесс. Вместо этого распределённое приложение для публикации статей, такое как dokieli , позволяет исследователям самостоятельно публиковать рукописи в собственном модуле Solid. Комментарии коллег хранятся в их собственных модулях, гарантируя свободу выражения любому, кто хочет принять участие. Все результаты остаются открыты для комментариев даже после публикации в вебе.
Децентрализованная Cеть для всех
Повторная децентрализация веба в соответствии с концепцией Solid поможет одолеть три проблемы, которые сформулировал Тим Бернерс-Ли . Мы можем вернуть контроль над личными данными, храня их в собственных модулях. Дезинформация блокируется, потому что свободный выбор приложений позволяет контролировать свою ленту новостей — а любая информация прослеживается до самого источника. Политическая реклама становится более прозрачной, поскольку каждый решает, кому и какие открыть фрагменты данных. Более того, разделение рынков данных и услуг позволяет рассмотреть другие варианты, вообще без рекламы. Хотя Solid не в полной мере решает все проблемы, но владение данными и свобода выбора — это главное.
Впрочем, за свободу всегда нужно платить: победа личных прав и свободы слова одновременно способствует незаконной активности, потому что распределённые сети затрудняют контроль за информацией. Конечно, это сложный вопрос, поскольку в некоторых странах объявляют незаконными высказывания, которые вполне законны в другом месте. Интригующий пример — возросшая популярность децентрализованной социальной сети Mastodon в Японии : когда Twitter начал удалять изображения, сомнительные по американским нормам, японские пользователи начали публиковать их на платформах с меньшей цензурой.
Нам придётся принять этот компромисс между свободой и контролем. В отсутствие общепризнанных норм централизованная фильтрация запрещённого контента никогда не будет адекватным решением.
Это подводит нас к другому аспекту децентрализации, а именно к противоречию между свободой и универсальностью. Парадокс свободы гласит, что человек может стать свободным, только если подчинится определённым правилам. Проще говоря, мы свободны взять велосипед и ехать куда угодно — если только держимся правой стороны дороги (в нескольких странах левой). Не соблюдая это правило, мы никуда не доедем без аварий. Поскольку универсальность всегда была главной задачей веба , распределённые сообщества должны согласовать некоторые базовые рамки децентрализации. Как и с универсальностью браузеров, консорциум W3C играет важную роль в создании стандартов для взаимодействия модулей данных и приложений. К счастью, не нужно согласовывать все детали. Формат Linked Data позволяет заключать многоуровневые соглашения, в которых несколько правил распространяются на многих участников, а дополнительные правила согласовываются меньшими группами по мере необходимости.
Важно отметить, что Solid не создаётся для борьбы с конкретными компаниями, такими как Google, Facebook или Twitter. Проект бросает вызов централизации в целом, поскольку многие проблемы этих компаний вызваны централизацией и бизнес-моделью владения данными. Мы подошли к тому, что компании обладают таким объёмом данных, что уже не могут предсказать долгосрочные последствия такой централизации . Поэтому неразумно и дальше в качестве предлога полагаться на «информированное согласие» , поскольку ни один человек не в силах понять, к чему в конечном итоге приведёт отказ от контроля над малыми или большими фрагментами его данных. Таким образом, хранение своих данных в надёжном месте со свободой выбора и детализированной моделью разрешений — единственный безопасный вариант.
Никто из нас не мечтает о Сети без крупных игроков. Совсем наоборот: Тим Бернерс-Ли настаивает, что Сеть всегда должна масштабироваться от очень маленьких к очень большим участникам. Проблема в том, что в настоящее время очень большие участники пытаются подавить остальных, что ставит под угрозу свободы, которыми мы пользовались в течение многих лет. Как указывалось выше, децентрализация — это прежде всего свобода выбора: у людей должна быть возможность свободно вступать в большие или малые сообщества. И хотя перед нами стоит несколько технических проблем, в том числе гарантия аналогичного удобства и скорости работы, как у централизованных платформ, Solid представляет собой первое жизнеспособное техническое решение. Теперь мы должны закрепить прогресс в социально-экономической реальности, чтобы полностью децентрализовать веб. Только когда нам удастся вернуть контроль и свободу выбора для самых ценных цифровых активов, мы сможем по-настоящему сказать: это Сеть для всех .
Source: https://habr.com/ru/post/436326/