Benefits of analyzing level 7 applications in firewalls. Part 1. Basics
The new generation of firewalls is more convenient and safer, thanks to the new architecture of the engine and the new ideology of managing network flows.
Why did this article appear?
Repeatedly I came to security colleagues who use the firewall of a new generation and saw that they continue to write rules for port numbers. On my proposal to write by the name of the application, I heard, “What if it doesn’t work?”. If you are also “scared” or do not understand why writing rules on applications, from this article is for you.
PART 1. Firewall Basics
CONTENT
IntroductionDefinitions
Firewall
L3 firewall
L4 firewall
L7 firewall
UTM
Ngfw
Examples
Proxy server
What is a USER-ID
Stateful Inspection Misconceptions: L4 vs L7 State
Misconceptions about Stateful Inspection: The number of sessions L4 vs L7
Misconceptions about Stateful Inspection: L4 vs L7 Cluster
Part 2. The impact of L7 Firewall on security
Introduction
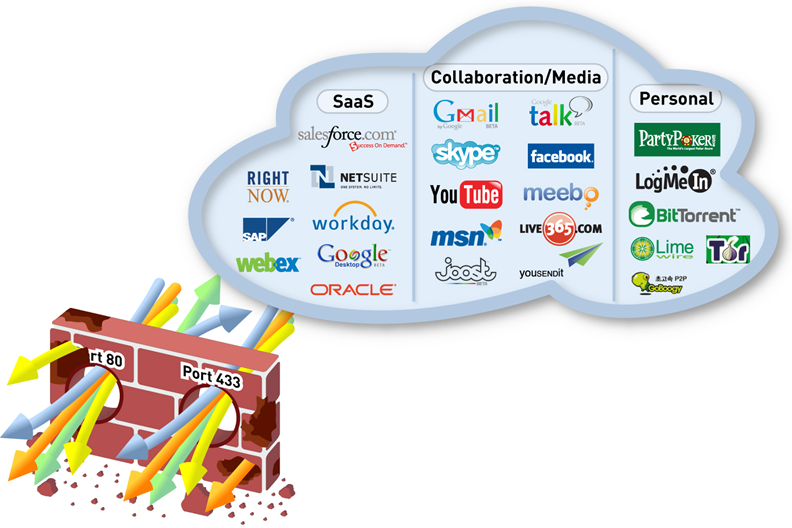
Skype, TOR, Ultrasurf, TCP-over-DNS and several hundreds more applications and tunnels quietly pass through statefull inspection firewall and HTTP proxies. Many defenses open connections, but do not check what goes inside them. I propose to understand how to control the connection of applications in a new generation of firewall, where the rules are written by application names, which corresponds to the 7th level of the OSI ISO model. These firewalls are called Next Generation Firewall, a new generation firewall, or simply NGFW.
The firewall administrator needs not only to allow the connection, but also to ensure that what you want goes within the allowed connection, including checks on the files being transferred. This is called secure application resolution .There are several important differences in the work with traffic, which you understand only when you switch to the actual use of the rules, where the criterion is the ISO 7 application model level 7 application:
- An IT administrator sees that NGFW visualizes network traffic, that is, shows the contents of the packet data field, user names and which application is running and which files are being transmitted.
- IT security sees that NGFW provides secure application resolution, since deeper analysis of the data in the package allows you to see viruses, connect sending unknown files to the sandbox, check the file type, keywords for DLP, check the URL category, check what goes inside SSL and SSH, compare with the world-famous indicators of compromise, enable the DNS filter and other modern techniques.
To understand the reasons for this, compare the L4 and L7 firewall logs.
A) Compare the log entry in the L4 firewall , which parses only the header of the transport (fourth) layer of the OSI ISO model - in this case TCP:Yes, there is information about the source and the recipient, you can guess by the port number 443, that inside, with a high degree of probability (as the British say) SSL connection. I personally cannot see any incident in this record. And you?
B) Compare the L7 firewall log entry for the same TCP connection, where the content transmitted in the TCP / IP data field is also parsed:Here you can see that Ivanov from the marketing department has uploaded a file on “Slideshare” marked “not for distribution”. This is an example of a real incident where an employee posted confidential company development plans for the year on the Internet. This information was obtained in the L7 firewall based on the analysis of the same connection as above in the L4 firewall and immediately the information becomes sufficient to understand that there was an incident. And this is a completely different approach to traffic analysis. But I will immediately warn you that such a deep analysis imposes a serious load on the processor and the operational memory of the device.
It is sometimes felt that the level of log detail in NGFW is similar to the level of detail in SIEM systems that collect information bit by bit from different sources. That is why NGFW is one of the best sources of information for SIEM.
Definitions
It is necessary to highlight the terms with which we will continue to operate. I have no purpose in detail to give all the definitions.

The OSI ISO seven-tier model is a model of interaction between network devices, which states that there are 7 consecutive levels of interaction abstraction: the first is physical, the next channel, network, the fourth is transport, then session, views, and the seventh level is applications (see picture above ).
Each network device operates at its own abstraction level: web server and browser - at the application level (level 7 or L7 for short), routers - communicate with each other on the link (2) and network level (3), when they send frames and packets to each other .
Firewalls are also network devices and, depending on their type, can also be switches and routers and even be a “virtual cable” in terms of network topology, but these network devices have an additional burden: they must analyze the contents of the packets.
And the depth of network packet analysis may vary. Whether they analyze level 4 or level 7 is an important difference.
Firewall
Firewall (ITU) Network Firewall is a network device that divides a network into segments with different security policies and controls these policies. For example, the segment of the Internet - there you can anything. And a segment of your data center - there you can work only with a dedicated list of employees on allowed applications. Within a single VMware host, there may be several virtual networks with virtual machines and different access policies.
The firewall security policy contains the rules that the device program code triggers, analyzing every frame and packet that arrives and outgoing from the firewall. The firewall rules specify test criteria (qualifiers) according to which the decision is made to pass or block traffic. Examples of qualifiers in the rules are: address, port, application, user, zone. Firewall sequentially, rule by rule, top down the list scans the criteria and if the incoming traffic meets all the criteria of the rule (logical operation “And” between the criteria), then the specified action is taken: block or skip. The action is performed both for the first packet and for all subsequent packets of one TCP / IP connection.
There are different types and implementations of the firewall. We consider the classification according to the degree of depth of traffic analysis used: L3, L4 and L7.
L3 firewall
L3 firewall is a firewall that passes traffic through itself and analyzes only IP protocol headers, that is, the address from where and where the traffic is going. These firewalls are called packet filters . The rules are called “access list” or access-list (ACL) and this functionality currently works in almost any router and operating system. Such an analysis does not require a serious load on the processors and memory of the firewall.
L4 firewall
L4 firewall is a firewall that passes traffic through itself and checks protocol headers 4 levels: TCP, UDP, ICMP, that is, the main test criteria for passing traffic are IP addresses and TCP / UDP ports or ICMP services.
Also, the concept of stateful inspection appears in the L4 firewall when every passing request is remembered and the status of the request is stored in order to allow the necessary response connections. That is, the concept of a connection initiator appears, which is logical in networks built on client-server technology. Such a firewall spends memory for storing data about each connection, that is, there is a limit on the maximum number of stored simultaneous sessions in memory. In the L4 firewall, it is no longer necessary to write a response rule for the reverse connection, as is required in the L3 firewall, because based on the connection state, the firewall automatically allows reverse connections. That is, L4 firewall is more convenient than a packet filter.
Modern L4 firewalls store not only TCP, UDP, and ICMP status, but also track the interaction of some L7 applications. For example, the state of FTP, HTTP, SIP, and other applications, which already depends on the specific implementation of the firewall. You need to ask the manufacturer of the L4 firewall the question: what specific applications does the stateful inspection firewall engine support?

L7 firewall
The L7 firewall is a firewall that passes IP network traffic through itself and checks both Layer 4 and the data segment of each IP packet, that is, L7 understands application-level traffic, down to which files are transmitted and in which direction. As more data is analyzed, there are more criteria for checking in the L7 firewall rules: username, application, URL category, software status on the user's computer.
The load on the L7 firewall is much higher, because its processor must constantly analyze the megabytes of the data field that the application transmits, while the L4 firewall checks only a few bytes of the IP packet header with source and destination addresses and ports. The buffer size for storing the state of each L7 application is much more required, since more data is transmitted to L7 than just the TCP / IP header. Due to the increased buffer size when using application analysis, the number of simultaneous in-memory sessions of the L7 firewall is less than the L4 firewall with the same amount of memory. Since the L7 firewall sees from the content that the application goes over the network, the port number does not have any special meaning and the rules can be written by the name of the L7 application. In addition, modern applications generate many connections and all of these connections are part of the same application. This type of firewall allows you to regain control of modern dynamic applications running on any port, for example, teamviewer, bittorent, tor, about which the L4 firewall knows nothing. That is, the L7 firewall in modern realities is needed if the network needs security.
If, after reading this article, you continue to use the L4 firewall, it means that you do not care about security.
UTM

UTM is a network device within which several different protection components are installed that sequentially analyze the traffic passing through the device. The core of UTM is L4 firewall, attack prevention system (IPS), antivirus, analysis of URL categories in HTTP and HTTPS. Often, UTMs still implement VPN gateway functions. All of these components are typically controlled from several different control systems. The traffic inside the UTM passes sequentially through the filtering modules and the output is pure traffic, which is allowed by the security policies of each module. UTM can be used as a platform for other functions: virus protection, IPS, DDoS, QoS, DLP, DNS filter, Threat Intelligence compromise indicators database, phishing protection, and so on (depending on the manufacturer).
The parable about the person who ordered seven hats from one skin was written, including for UTM buyers: the more functions you want to include after the purchase, the more burden the UTM processor will bear to analyze the same traffic volume. More functions - less device speed.
The idea of UTM - to load one processor with as many functions as possible became an evolutionary deadlock, because the number of functions grew and the processors could not withstand all this load. Today, despite the stated good features, no one includes all the functionality in UTM to eliminate traffic delays.
The goal of UTM is to implement as many functions as possible on one server in order to make the device cheaper for the user.Now UTM manufacturers have begun to put Level 7 application analysis engines to say that they are NGFW, which confuses the consumer. However, this is easily recognized when looking at the security policy: the rules are still based on the criteria for checking the L4 fields. And for filtering L7 applications, a separate settings section is used, that is, the L7 application is not a qualifier, as it should be in the L7 firewall. Recognizing the L7 application and using the L7 application as a security policy criterion are “two big differences.”
Ngfw
NGFW is the network device within which the L7 firewall is implemented. Since the main qualifier becomes the name of the L7 application, the rules are written according to the new criteria. Dynamic mapping of IP addresses to network users always works in NGFW, so the user name also becomes a qualifier (criterion). NGFW includes SSL / TLS and SSH decryption functions for recognizing applications and attacks inside them, IPS, antivirus, URL filtering.
The term NGFW was first coined by the marketing of Palo Alto Networks. But it gradually got accustomed to the market and all the UTM manufacturers now also call themselves NGFW. Indeed, NGFW also performs several functions at the same time, why then is NGFW not UTM? The difference is important to know. It is that in NGFW, application security features (IPS, antivirus, URL filtering) are hardware accelerated. There are specialized hardware chips: IPS checks for attacks on its chip, anti-virus signature on its own, decryption of SSL on its own, and so on. Separation of functions for different processors makes it possible to run protective functions in parallel and not wait for the previous function to finish, as in UTM. For example, in hardware firewalls of Palo Alto Networks, up to 60 are installed.
Cavium’s dedicated processors accelerate security, networking and management functions. It is important that NGFW contain a single software interface for managing all functions simultaneously.
The idea of NGFW, in contrast to UTM, is to implement each function on a separate processor that is specialized for the required functionality.In the same way once the computer makers went, who carried out the functions of mathematics and graphics into separate mathematical and graphic coprocessors. Therefore, in NGFW there are separate processors for recognizing L7 applications, for decrypting SSL / SSH, for checking antivirus signatures, checking IPS signatures, and so on. This allows you to enable all functions at the same time, without degradation and delay of traffic in the device during the scan. Why no one buys computers without graphic accelerators, and firewalls without acceleration buy? Because acceleration is not necessary at low speeds, but when traffic analysis speeds go beyond 1-5 Gigabits, it is no longer possible to implement all security features without acceleration.
The goal of the NGFW device is to enable companies to operate safely without slowing down traffic. This allows you to constantly check that applications deliver the required content to the company, and the parallel operation of the protection engines with one traffic stream ensures the specified performance with all the security features enabled and also the minimum traffic delay.
Examples
L7 Policy Example at Palo Alto Networks NGFWWhy might a URL category be required as a qualifier? For example, you can still allow some employees to visit malicious sites with a browser, but block their downloading of files.
Palo Alto Networks policy example using Host Information Profile checks and category URLs.This policy also includes checking for the presence of the TRAPS host protection in the HIP Profile column, which will prevent you from entering the site with malicious code and exploits without protection installed on your computer. Traps is an agent for protection against malicious code and exploits.
Blocking of downloading files is performed in the settings of the Profile column, where the profile of blocking the transfer of all files for any application is applied. This is what its setup looks like:

Proxy server
A proxy server is a device that terminates the traffic of an application on itself, checks this traffic using various methods and sends this traffic further. Most commonly used in proxy networks for HTTP and HTTPS protocols. Since UTM and NGFW analyze HTTP and HTTPS streams transparently, without requiring explicitly specifying proxy server settings for clients, HTTP proxies are gradually disappearing from companies.

What is a USER-ID
In NGFW, a user identification mechanism was invented. The algorithm either runs inside or runs on an external agent. I will call this the USER-ID mechanism. The USER-ID creates and maintains a lookup table for the user's name and current IP address. It also happens that there is a value and a port for this user in the table if the users work through VDI (that is, the users go from the same address and can be distinguished only by ports).
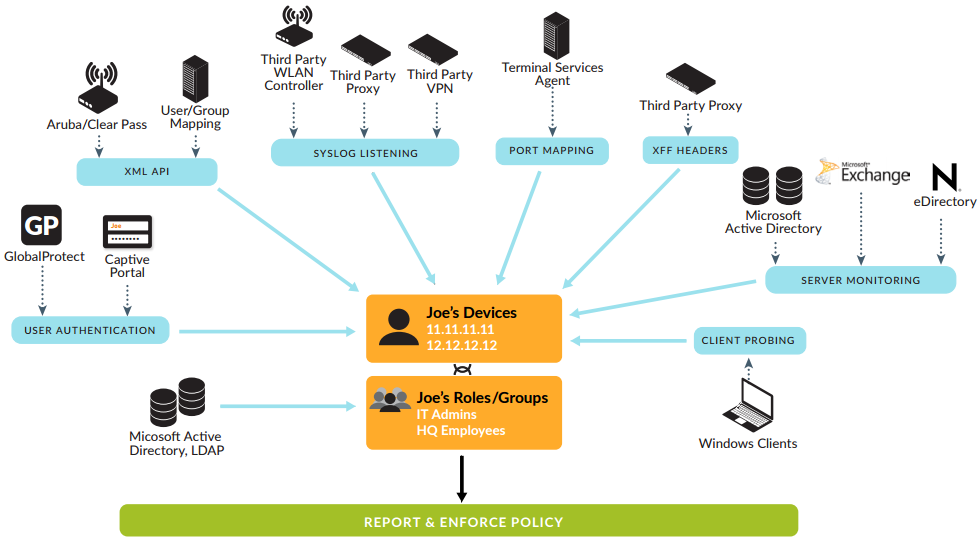
List the USER-ID mechanisms in Palo Alto Networks.
- Server monitoring : User-ID agent reads Exchange Servers events, domain controllers or Novell eDirectory servers
- Client probing : User-ID agent polls Windows clients via WMI
- Terminal services agent : TS agent distributes different TCP / UDP port ranges to different users for working with Windows / Citrix Terminal Servers
- Syslog messages parsing: User-ID agent reads syslog authentication messages from various systems, wireless controllers, 802.1x devices, Apple Open Directory servers, proxy servers, VPN gateways, Cisco ISE
- Authentication through the GlobalProtect client: login and password on VPN +, you can add MFA
- Authentication via Captive Portal : Web traffic is authenticated by NTLM or AAA web form (Captive Portal is used in the Moscow metro and cafes. NTLM allows you to make authentication transparent)
- XML API : entry and exit information is transmitted by the User-ID agent by special commands via the REST API firewall
- X-Forwarded-For : proxy server fill in this field in the HTTP request to make it clear who is hiding behind the proxy
Reading logs from Active Directory controllers is the most frequently used feature in USER-IDs. The USER-ID agent periodically reads messages from AD logs, where it is recorded which user logged in from which IP address, it is from them that the USER-ID knows what address the user is storing inside NGFW, for example, for Windows 2008/2012, these messages:
- 4768 - Authentication Ticket Granted
- 4769 - Service Ticket Granted
- 4770 - Ticket Granted Renewed
- 4264 - Logon Success
To read the logs, the USER-ID agent needs access with Even Log Reader permissions.
Misconceptions about Stateful Inspection
I must devote a separate chapter to this saint to every network engineer and safety technician. It is necessary to emphasize and supplement important things that are often missed on courses on firewalls. If you have already studied the basics of stateful inspection, then most likely you have several misconceptions.
There is one misconception that I sometimes see from colleagues. Attention! Stateful inspection is not only about TCP, UDP, or ICMP connection status! It is also about the state of other more complex protocols and applications: FTP, SIP, RPC, SMTP, SMB and so on!
Example.That is, in any modern L4 firewall there is a component that spies on the L7 level. And there is not one such protocol: there are still HTTP, RPC, and others ... And such Layer 7 protocol analyzers are called Application Layer Gateway (ALG).
FTP is an application level protocol. And it has a PORT command that can assign a new TCP connection. Any firewall that positions itself as a stateful inspection firewall should monitor the FTP commands and see the PORT command and allow the connection to the port and the address requested there. And that's not all: the firewall also has to replace the parameters of the PORT command and insert the correct address if the FTP server is running for NAT.
Example.That is, already in the L4 firewall there are the beginnings of the analysis of level 7 protocols. L4 firewalls differ in the amount of ALG implemented. When you compare ordinary L4 firewalls, then a fair question to the manufacturer’s system engineer will be: how many protocols and applications does your Stateful Inspection engine support? As a rule, no one answers.
The most "beloved" of networkers and security guards at the same time is ALG for SIP, with which many who set up SIP ALG on the L4 firewall are full of problems, and often end with its shutdown.
It turns out that the L7 firewall is also a stateful inspection firewall, but which analyzes and stores the status of ALL applications, and not just selectively, like the L4 firewall.
The second misconception is made by the firewall manufacturers themselves. Take any datasheet, where the manufacturer writes such a parameter as “number of simultaneous sessions”. The question to the manufacturer is the following: what particular protocols and applications were the sessions measured and was at least stateful for TCP included, let alone were there checks for the L7 level?
We know that every protocol or application has a state that the firewall remembers. And to store this state, you need to allocate a buffer in the device memory. In fact, the parameter “number of simultaneous sessions” means how many buffers for storing states can be stored in the device memory. You need to understand that for L4 firewall most often measure this parameter for bare TCP or even UDP. That is, for TCP, a buffer is needed, in which only the IP and port of the connection can fit. However, in the test for L7 applications, for example, HTTP, this buffer will be much larger, because storing, for example, GET request parameters inside HTTP requires more memory. And the memory is not rubber. Accordingly, if the manufacturer writes such a parameter as “the number of simultaneous sessions”, then he should write:
- was it just a switch / router mode test, with stateful inspection turned off,
- was it L4 mode, where he remembered only TCP / IP headers,
- Whether any L7 level application was taken for the test.
Correctly measure the L7 firewall on the number of simultaneous HTTP sessions, on packets of different lengths: 64Kb, 44Kb, 16Kb, 1.5Kb. It is clear that if some manufacturer made all measurements on UDP 1518 bytes, then most likely this device will not work on your network, since it will not work to force your users to send only 1518 byte UDP packets, and even more so to make them respond HTTP server packages. It is necessary to say to such a manufacturer that the performance of the L7 firewall must be measured at least on the traffic with the HTTP protocol. From well-known companies that conduct such tests in public: NSS Labs.
Firewall manufacturers themselves conduct custom tests in their laboratories, which can order their traffic profile, for example: 30% of HTTPS traffic, 10% of SMB traffic, 10% of FTP traffic, and so on.
Example.
After checking the IXIA device on a traffic generator from one of the UTM manufacturers:
- in L4 firewall mode - 4,000,000 simultaneous sessions,
- in L7 firewall mode - 200,000 simultaneous sessions.
This is an indication that the buffers for L7 sessions in the device’s memory are smaller due to their large size.
And, by the way, it will also be with the overall performance of the device: with the application content checks turned off, the firewall works 10 times faster than with those turned on. You can only use header analysis 4 to speed up the device, but there is no security anymore.
The third important point is the work in the cluster.All firewalls should work in a cluster, because if a single firewall stops working, then its task is to "breastfeed" and block all traffic - such is the theory of building protection based on firewalls. As long as a “broken” firewall blocks traffic, the next firewall should take over the task of passing legitimate traffic. And what about the connections that went through the first? Most likely, the first firewall transmitted the status of all connections to the second, but whether it transmitted to the neighbor only the status of IP headers or the full status of all L7 level applications: there were some SSL connections that were decrypted and IPS and anti-virus worked on them - they collected packets in the buffer to check the contents. And here it turns out that L4 and L7 firewall are also different: transmitting the L4 state is not the same,that pass the state of L7. This is also important to understand.
There is another misconception that the L7 firewall can work in clusters of more than two devices - this is incorrect, since the amount of L7 data transferred grows exponentially with each new node in the cluster and the data processing of even two neighbors exceeds the cost of processing the data of its own device. That is why clusters of more than two devices work only by exchanging L4 headers, and when switching clusters, all application analysis and protection functions are restarted.
Therefore, you need to competently compare the L4 and L7 firewall, as well as when you compare whether a car and a tank suits you in a war. L7 firewall to increase the security of your network does more complex work, much more work goes on its processors and it needs more memory to store the state of your applications! All this needs to be done for safety.
Part 2. The impact of L7 Firewall on security
Source: https://habr.com/ru/post/436392/





