Users report the loss of bitcoins as a result of the ingenious hacking of Electrum wallets
Hacker stole bitcoins for $ 750,000 in a week
The hacker (or hacker grouping) earned more than 200 bitcoins (approximately $ 750,000 at the end of 2018) using an ingenious attack on the infrastructure of the Electrum wallet.
As a result of the attack, legitimate applications for working with the Electrum wallet showed messages on users' computers urging them to download a malicious update for the program from an unauthorized GitHub repository.
The attack began on December 21 and seemed to stop after the GitHub administrators closed the hacker's repository. The administration of the Electrum wallet is waiting for a replay of the attack using a new repository on GitHub or links to another server for download.
This is due to the fact that the vulnerability on which the attack is based remains uncorrected, although the administration of Electrum is taking steps to weaken its usefulness to the attacker. The attack is as follows:
- The attacker adds dozens of malicious servers to the Electrum wallet network.
- The user of the legitimate wallet Electrum initiates the transfer of bitcoins.
- If the transaction contacts one of the fake servers, they return an error that invites the user to download the application update for the wallet from the malicious site (the GitHub repository).
- The user follows the link and downloads the update .
- When a user opens a bogus application, it requests a two-factor authentication code. This is a danger signal, since these codes are requested only before sending funds, and not at the start of the wallet.
- The substitute wallet uses the code to steal the user's funds and transfer them to the attacker's Bitcoin address .
The problem is that Electrum servers allow you to send a request to a pop-up window in the user's wallet containing arbitrary text. The first attacks were more effective and deceived more users than subsequent ones. This happened because the Electrum wallet showed text in the Rich Text Format, which is why the pop-up windows looked genuine and provided users with a link that could be simply clicked.
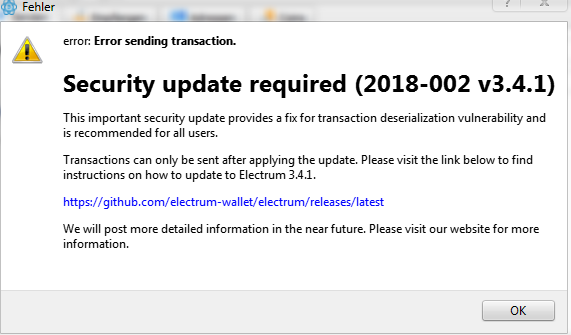
Upon receiving the attack message, the Electrum team silently updated the application so that these messages were not displayed as RTF.
“We have not announced publicly about this attack until now, because after the release of version 3.3.2 the attacks stopped,” said SomberNight, one of the members of the Electrum development team. "But now the attacks have begun again."
Not all users who received errors in the new form, they seemed suspicious. Some were more worried than worried. They manually copied the link from the text in a pop-up window to the browser, and then downloaded and installed a fake update wallet.
The attack stopped when the GitHub administration deleted the repository where the malicious wallet version was located.
As already mentioned, a wave of new attacks is expected, perhaps with a new link. But the problem in the form of malicious servers running on the attacker remains relevant.
Developers are currently considering the possibility of replacing sending error messages to servers by sending error codes that Electrum's wallet will decrypt on the client side, showing pre-defined messages.
SomberNight says that Electrum developers have currently detected at least 33 malicious servers added to their network, and there should be about 40-50 in all. It is unclear what they are going to do with these servers.
Source: https://habr.com/ru/post/436726/