Own research, what can open source tell us?
Inspired by the Group-IB article on a large-scale hacker attack on banks and enterprises on behalf of state institutions, I decided to find out a little more about RTM.
The goal is not only to find those involved in this attack, but also to show how accessible such an investigation is when there are good tools and some technical background.
Source data from EditorGIB post :
- September 11, 2018 - the beginning of the mass malware distribution
“... In total, from September to early December, hackers sent 11,073 letters from 2,900 different e-mail addresses forged by government agencies. Found about 900 different domains associated with the addresses of the senders.
- The content of the letters provides information:
“... as the subject of the letter, it is indicated“ Sending on Thursday ”,“ Service Note ”,“ Payment August-September ”,“ Copies of documents ”, etc.)”.
- Information about malicious code - "Trojan RTM".
- Network identifiers: namecha.in domain and IP addresses: 188.165.200.156, 185.190.82.182, 5.135.183.146, 151.80.147.153, 109.69.8.34.
- According to Group-IB analyst findings:
“To obtain the C & C server’s IP address, the site is called namecha.in.
Let us verify that they know the services of hybrid-analysis.com, virustotal.com about namecha.in. For the investigation I will use the product called Lampyre - positioning itself as the “Data analysis tool for everyone”, according to my impressions, the product is the result of the i2 composition, Maltego and apparently the developers were inspired by Palantir.
Execution of Hybridanalysis search queries, and Virustotal search gives the following result:
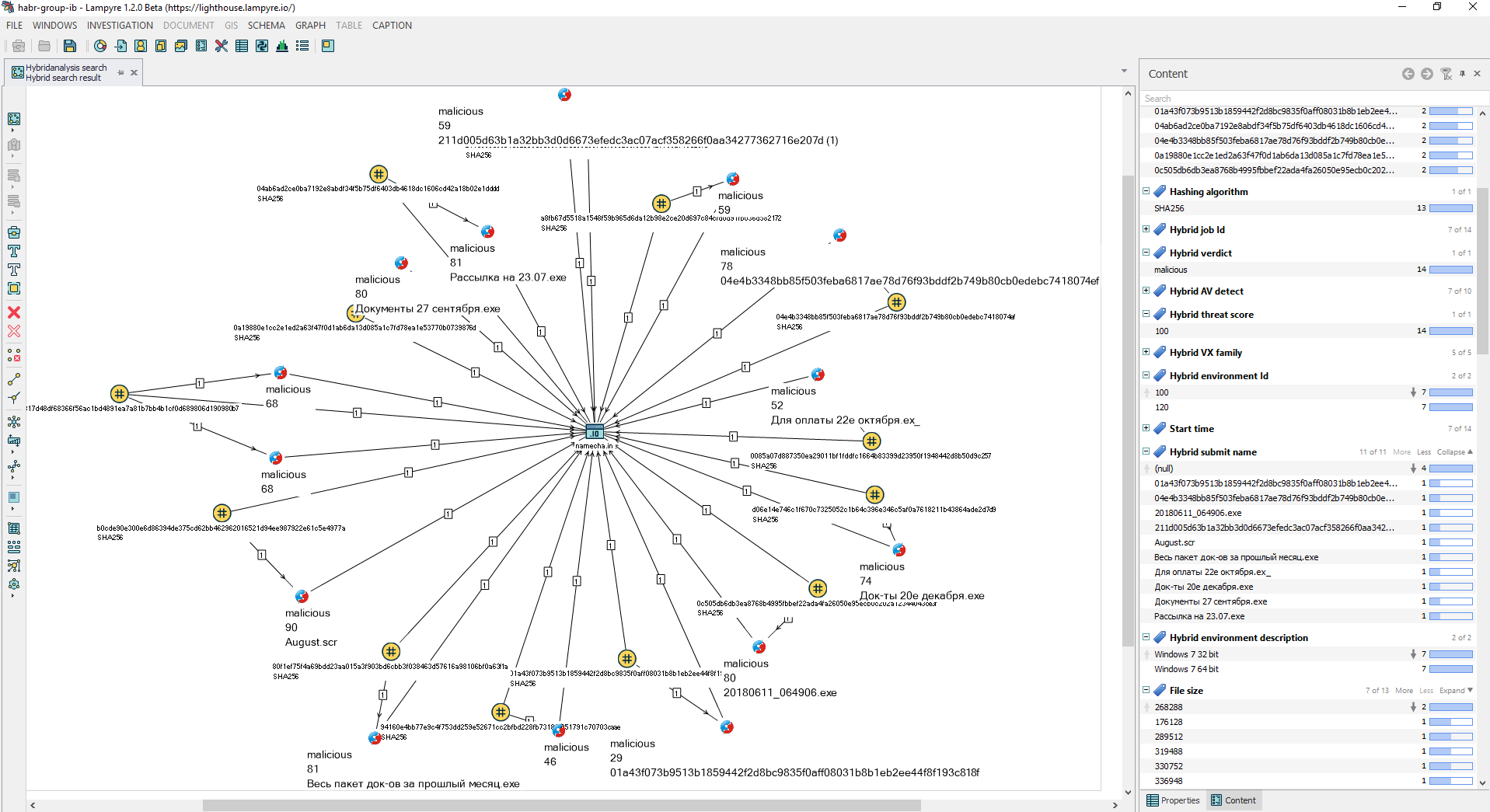
It can be seen that the names of files that were once sent for verification to the Hybrid-analysis service are similar to the names from the Group-IB analyst report.
Let's execute 2 queries of Hybridanalysis report by hash with input data report ids, and hashes from the result of the previous report. The results of the requests will be sent to the circuit with the original graph and we will clear the graph from objects that are not yet necessary. The result is:
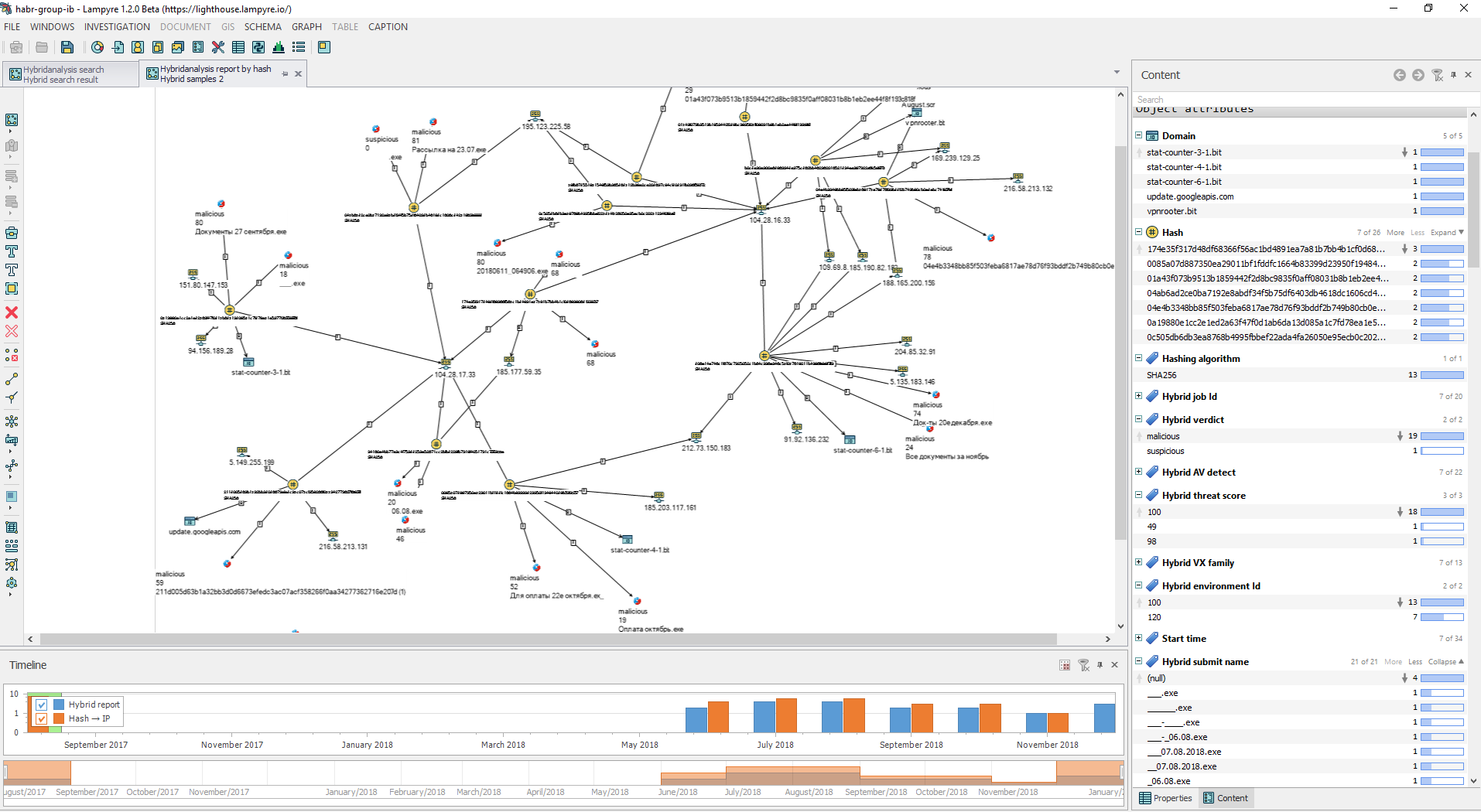
You can see that the events on the graph have the earliest date in August 2017, then failure, and the resumption of infrastructure use since the beginning of the summer of 2018.
Visualize the result from the query to Virustotal
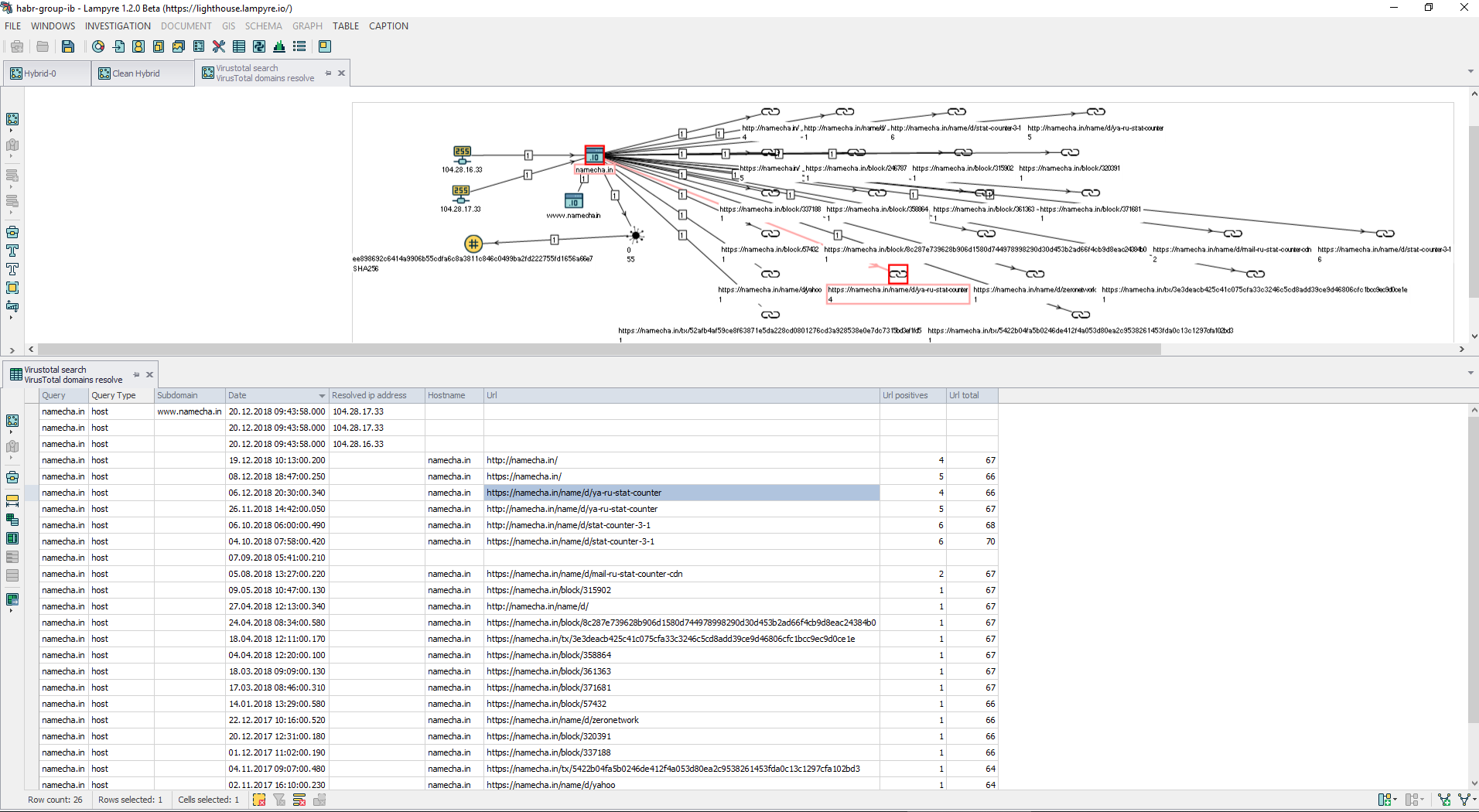

Let's summarize the intermediate results for the objects and results:
- Hybrid-analysis:
- 4 domains: stat-counter-3-1.bit, stat-counter-4-1.bit, stat-counter-6-1.bit, vpnrooter.bit;
- 19 ip-addresses: 151.80.147.153, 94.156.189.28, 185.177.59.35, 185.203.117.161, 88.221.214.41, 195.123.225.58, 5.135.183.146, 91.92.136.232, 212.73.150.183, 204.85.32.91, 169.239.129.25, 216.58 .213.132, 109.69.8.34, 185.190.82.182, 188.165.200.156, 216.58.213.131, 5.149.255.199, 104.28.17.33, 104.28.16.33
- Virsutotal:
So, there are questions:
- What a domain zone * .bit;
- What are the urls to namecha.in and what are the answers.
You can see that the domain name stat-counter-3-1.bit from the Hybrid-analysis data is similar to url namecha.in/name/d/stat-counter-3-1 from Virustotal .
Initially, I had no idea about namecha.in, however, in general, it turned out: there is a Namecoin project, another use of blockchain technologies.
Namecoin is a Bitcoin-based storage system for arbitrary name-value combinations, the most well-known application of which is the alternative root DNS server system.Resource Namecha.in is an alternative namecoin block explorer.
That is, the information on the namecha.in/name/d/mail-ru-stat-counter-cdn will return information of the following content (abbreviated):
| Status | Active |
| Expires after block | 461917 (30918 blocks to go) |
| Last update | 2018-11-16 10:35:22 (block 425917) |
| Registered since | 2018-06-13 19:44:47 (block 402893) |
| Current value | {"Ip": ["185.203.117.161"]} |
Operations
| Date / time | Operation | Value |
|---|---|---|
| 2018-11-16 10:35:22 | OP_NAME_UPDATE | {"Ip": ["185.203.117.161"]} |
| 2018-07-30 14:05:46 | OP_NAME_UPDATE | {"Ip": ["195.123.226.143"]} |
| 2018-07-18 11:35:27 | OP_NAME_UPDATE | {"Ip": ["185.82.219.79"]} |
| 2018-06-13 19:44:47 | OP_NAME_FIRSTUPDATE | {"Ip": ["195.123.217.232"]} |
As you can see, information is returned on the ip-addresses of the specified domain name (mail-ru-stat-counter-cdn.bit), including with a retrospective.
By the way, it is possible to check the resolution of a domain name in the bit zone via nslookup from the server 91.217.137.44 (taken from bitname.ru ).
Using the search on namecha.in, we managed to find the following domains in the * .bit zone, which by the type of generation and creation, quite possibly have a related origin:
- namecha.in/name/d/ya-ru-stat-counter , ya-ru-stat-counter.bit;
- namecha.in/name/d/ya-ru-stat-counter-cdn , ya-ru-stat-counter-cdn.bit;
- namecha.in/name/d/stat-counter-3-1 , stat-counter-3-1.bit;
- namecha.in/name/d/stat-counter-3-2 , stat-counter-3-2.bit;
- namecha.in/name/d/stat-counter-4-1 , stat-counter-4-1.bit;
- namecha.in/name/d/stat-counter-4-2 , stat-counter-4-2.bit;
- namecha.in/name/d/stat-counter-6-1 , stat-counter-6-1.bit;
- namecha.in/name/d/stat-counter-6-2 , stat-counter-6-2.bit;
- namecha.in/name/d/mail-ru-stat , mail-ru-stat.bit;
- namecha.in/name/d/mail-ru-stat-cdn , mail-ru-stat-cdn.bit;
- namecha.in/name/d/mail-ru-stat-counter , mail-ru-stat-counter.bit;
- namecha.in/name/d/mail-ru-stat-counter-cdn , mail-en-stat-counter-cdn.bit
Therefore, using queries to namecha.in, I collected all the information on the listed domains in the * .bit zone, saved the information in a csv file with the fields Datetime, IP, URL, Domain, imported into Lampyre and created a template for the graph.
Urls hint at involvement in well-known companies, but then there are questions:
- their structural identity - I believe that if different people actually invented them, then their structure would be different.
- The IP addresses to which these entries are resolved have no relation to these two companies, but belong to foreign hosts. Both companies have their own data centers outside of the Russian Federation and it is unlikely that they would have started hosting any services. But even if they had become, they would most likely have added reverse DNS entries to these addresses.
- It seems that these urls invented in order to disguise themselves under the well-known, Russian services.
In the form of a graph it looks like this (vertices with url are removed from the graph)
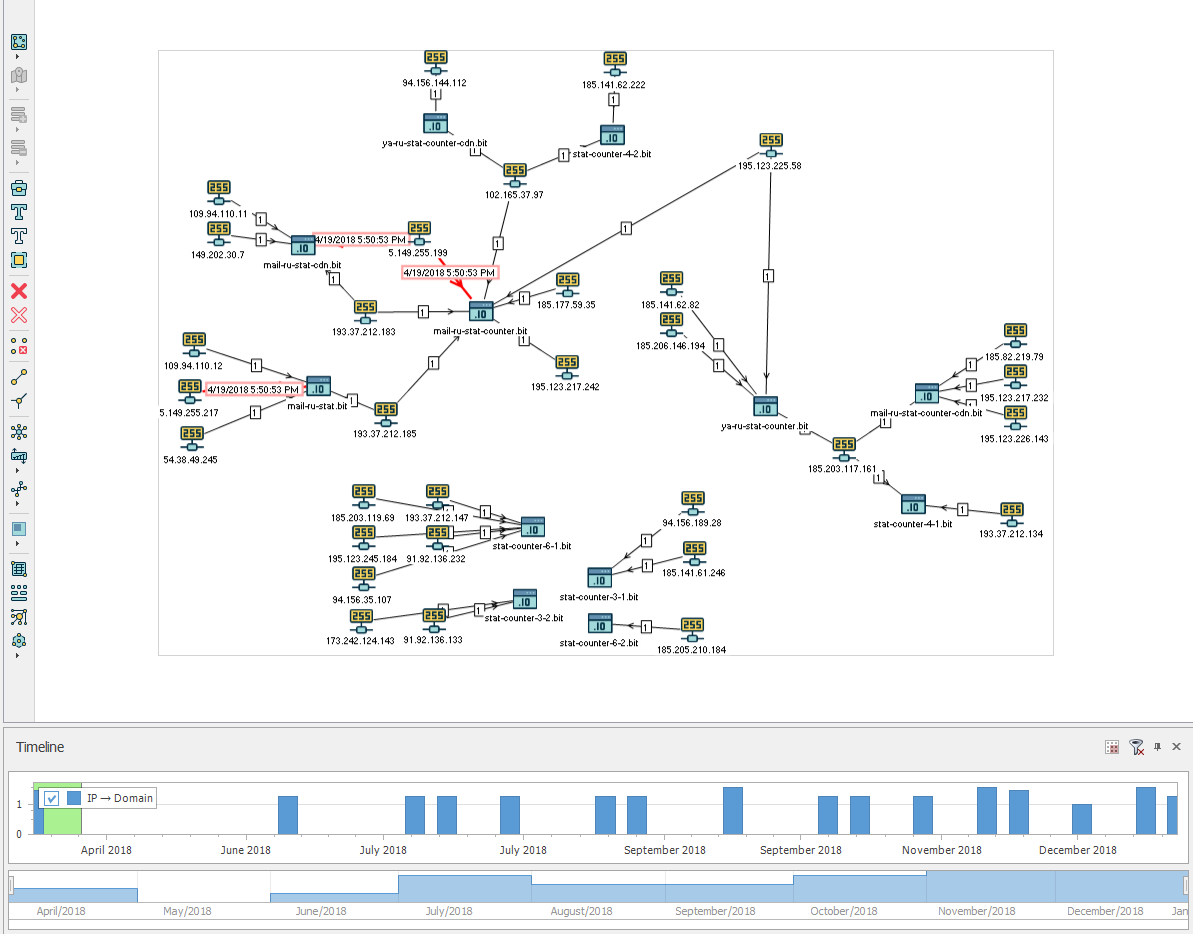
According to the graph, you can see that the infrastructure of the * .bit domains was prepared from April 2018 and continues to be used up to the present. The “randomness” of domains and ip-addresses, it seems to me, is excluded.
So, starting from the very beginning of the fact that the RTM Trojan has addressed the namecha.in, the investigation has come to some kind of stable infrastructure - networks from ip-addresses, which definitely can be part of the campaign to spread malicious software.
Total IP addresses detected: from Hybrid-analysis - 19, from the scheme with namecha.in and * .bit domains - 31.
Only 44 unique IP addresses:
102.165.37.97, 104.28.16.33, 104.28.17.33, 109.69.8.34, 109.94.110.11, 109.94.110.12, 149.202.30.7, 151.80.147.153, 169.239.129.25, 173.242.124.143, 185.141.61.246, 185.141.62.222, 185.141. 62.82, 185.177.59.35, 185.190.82.182, 185.203.117.161, 185.203.119.69, 185.205.210.184, 185.206.146.194, 185.82.219.79, 188.165.200.156, 193.37.212.134, 193.37.212.147, 193.37.200.156, 193.37.212.134, 193.37.212.147, 193.37.200.156, 193.37.212.134, 193.37.212.147, 193.37.200.156, 193.37.212.134, 193.37.219.147, 193-377.1.156, 193.37.212.134, 193.37.212.147, 193-7.320.156, 193.37.212.134, 193.37.212. 195.123.217.232, 195.123.217.242, 195.123.225.58, 195.123.226.143, 195.123.245.184, 204.85.32.91, 212.73.150.183, 216.58.213.131, 216.58.213.132, 5.135.183.146, 5.149.255.199, 5.1.5.55.223.231.231.131, 216.58.213.132, 5.135.183.146, 5.149.255. 49.245, 88.221.214.41, 91.92.136.133, 91.92.136.232, 94.156.144.112, 94.156.189.28, 94.156.35.107
And now, back to the analyst's article from Group-IB, to the input data in our study:
“Next,“ RTM ”tries to establish a connection with the“ C & C ”server (the following addresses were found: 188.165.200.156, 185.190.82.182, 5.135.183.146, 151.80.147.153, 109.69.8.34). To obtain the C & C server’s IP address, the site is called “namecha.in”.All of these 5 IP addresses were detected by us as a result of the first request to Hybrid-analysis with the namecha.in argument, and it would be possible to deal only with them, but I continued further in order to try to find other IP addresses. As a result, 44 IP addresses are available for analysis and research on the subject of interconnections.
There is already an understanding that the well-known 5 IP addresses should be somehow connected for some signs, it is possible that the network (on the graph) will have an obvious connection with the other 39 addresses, or they will all form an interesting structure.
Again Russian hackers?
Obviously, the targets of the attacks were Russian enterprises, and the files were called in Russian, and the sending was carried out from various e-mail addresses forged by state institutions. Will there be any more signs of a Russian trace? What else can you find at the IP addresses found above?
Let's check the IP addresses belonging to countries and get the following result: United States, Bulgaria, France, Austria, Canada, Czechia, Netherlands, Poland, South Africa, Spain.
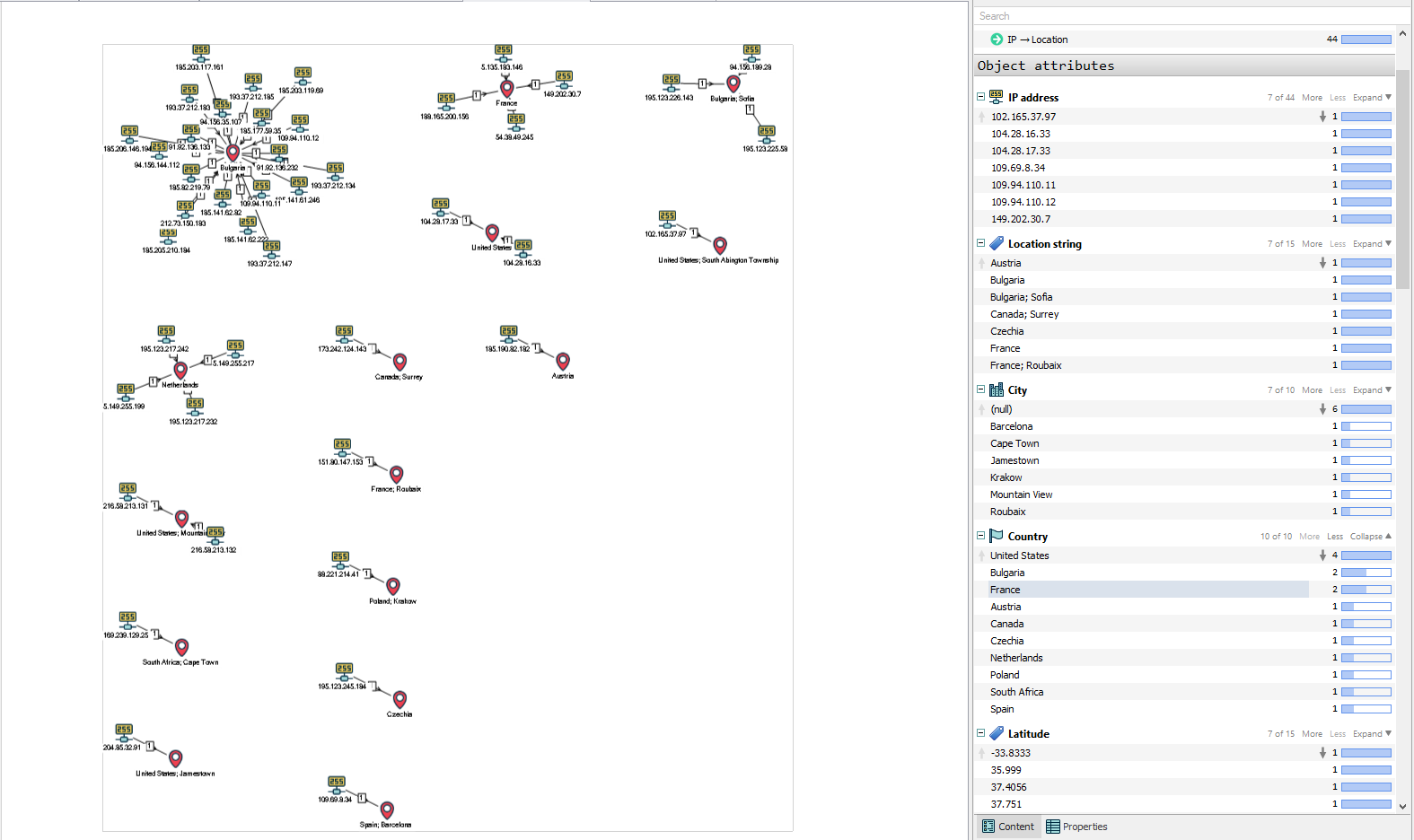

Check if there are Tor nodes among the 44 IP addresses found, and there will be no such verification.
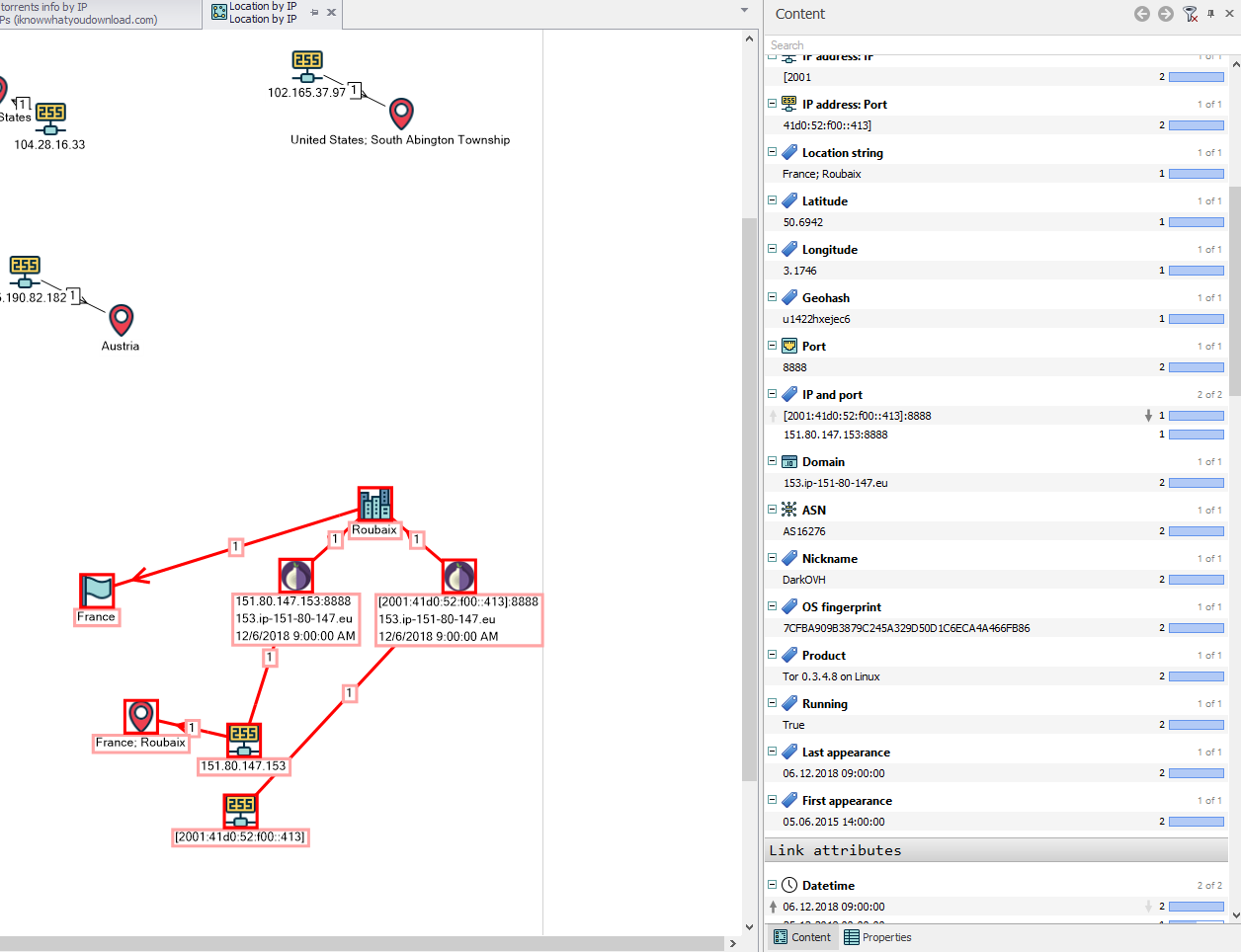
Note that IP 151.80.147.153 — since 2015, a regular TOR network node, nickname: DarkOVH, email: julles.reneau@post.com — this IP follows the Group-IB analyst report and Hybrid-analysis reports.
Check whether they were downloading (handing out) torrents from these IP addresses.
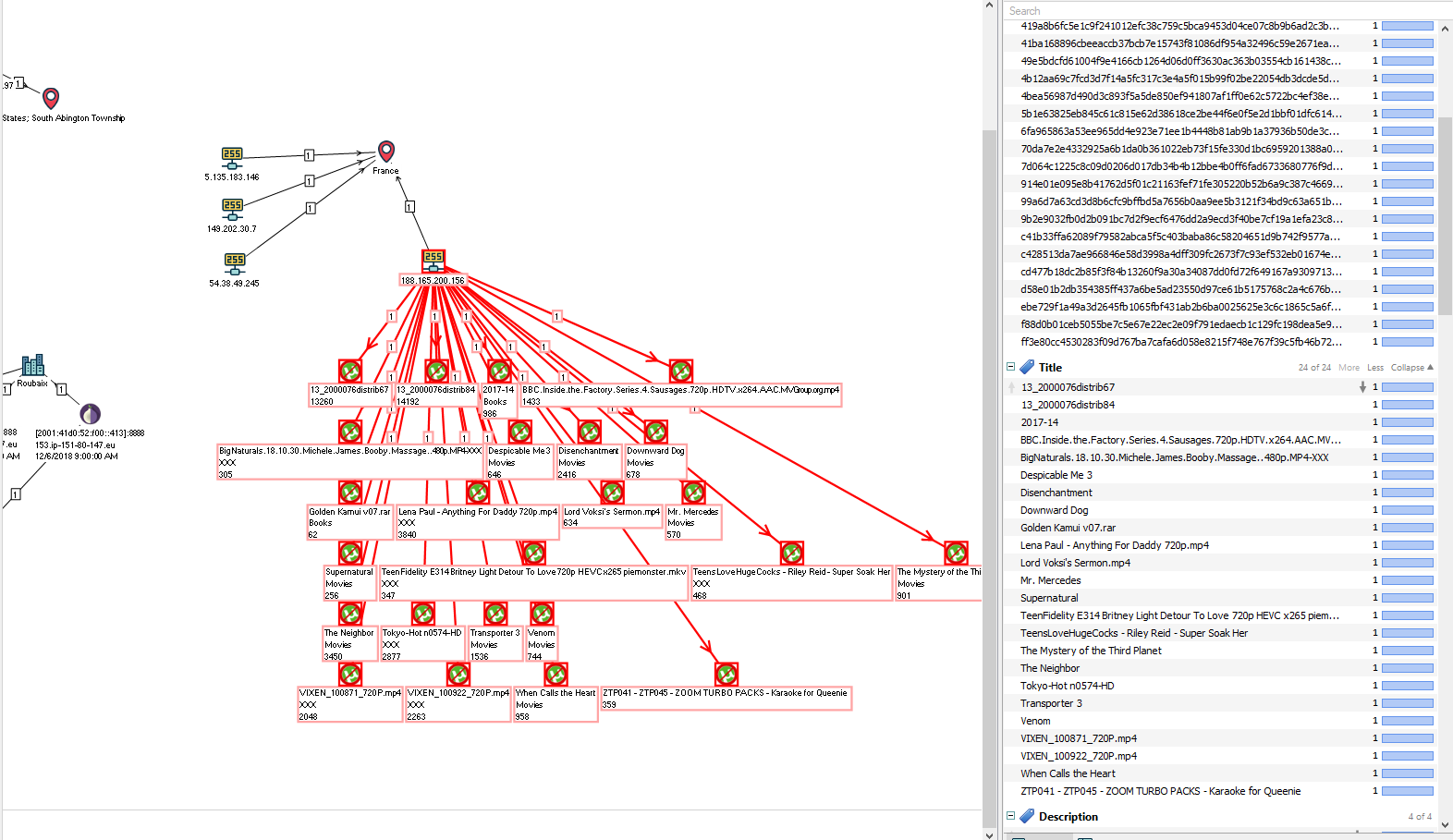
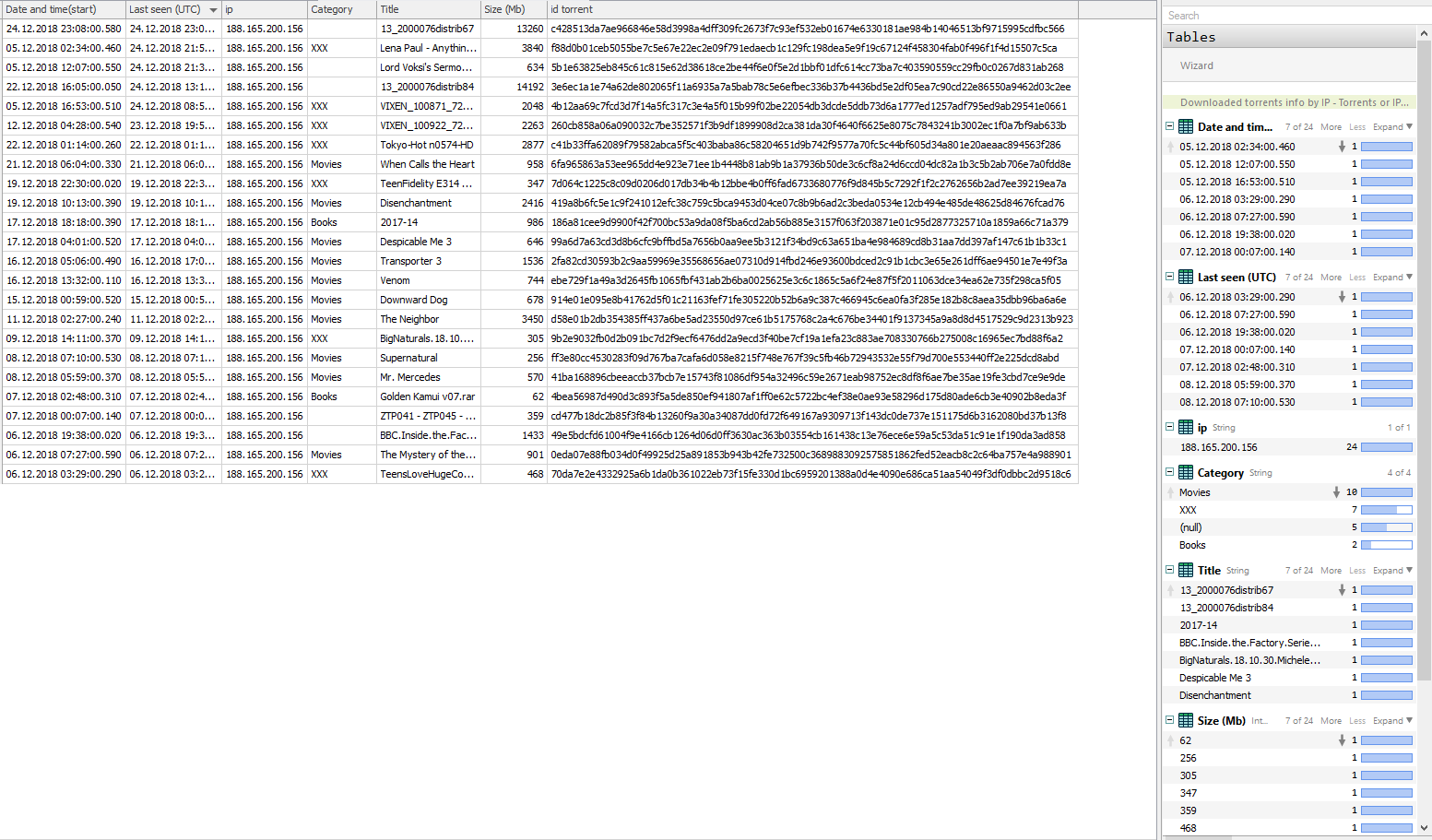
But now, for my part, there will be a small trick - since the article was prepared in two approaches, I already reasonably assume that 188.165.200.156 can be used by someone speaking Russian, but now from the screenshot and table it is not at all obvious. Earlier, in the first approach to writing an article, the result of the search for torrents contained, among others, the following information:
30.11.2018 14:36:00 30.11.2018 14:36:00 188.165.200.156 Пастырь (сезон 1) Preacher (2016).WEB-DL.720p.LostFilm 1976 cd46d4168ee44f31fbefce4303e24cbbda2d2cafe8283fa30363bc6148455d1ac1130edad0c9237934c05bf6c2d857c7 That is, the user (s) behind this IP address understand Russian speech? And yes, 188.165.200.156 is also one of 5 interesting addresses.
So, in order to confirm the assumption within the framework of the current visual investigation that, for IP 188.165.200.156 someone is “sitting” very similar to the “Russian comrade”, we single out the following line:
17.12.2018 18:18:00 17.12.2018 18:18:00 188.165.200.156 Books 2017-14 986 186a81cee9d9900f42f700bc53a9da08f5ba6cd2ab56b885e3157f063f203871e01c95d2877325710a1859a66c71a379 For the torrent id, send the request Downloaded torrents info by ID and get the answer who and with what ip downloaded the torrent with the given id. The result is as follows:
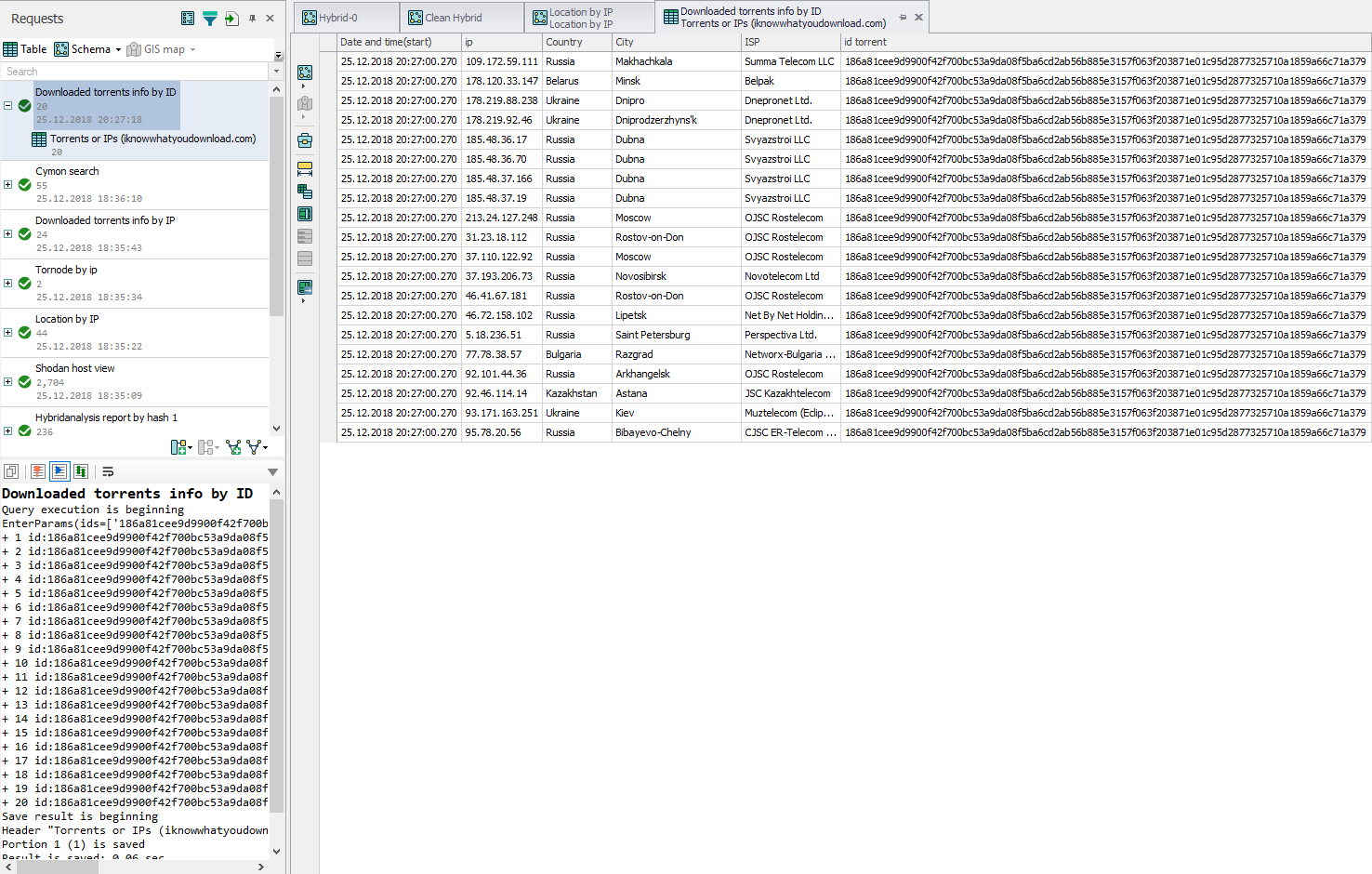
According to the table, those who download and distribute such a torrent are all Russian-speaking comrades. Moreover, Lampyre does not hide the fact that it uses the result of the iknowwhatyoudownload.com service, and in principle, anyone can see the content of the torrent by following the link - many book files in Russian.
The final scheme and a strange resource
Combining the queries from those presented in Lampyre and the visualization methods (laying the graph, removing unnecessary vertices, grouping the vertices, changing the visual properties of the vertices and edges of the graph), such a scheme was built.
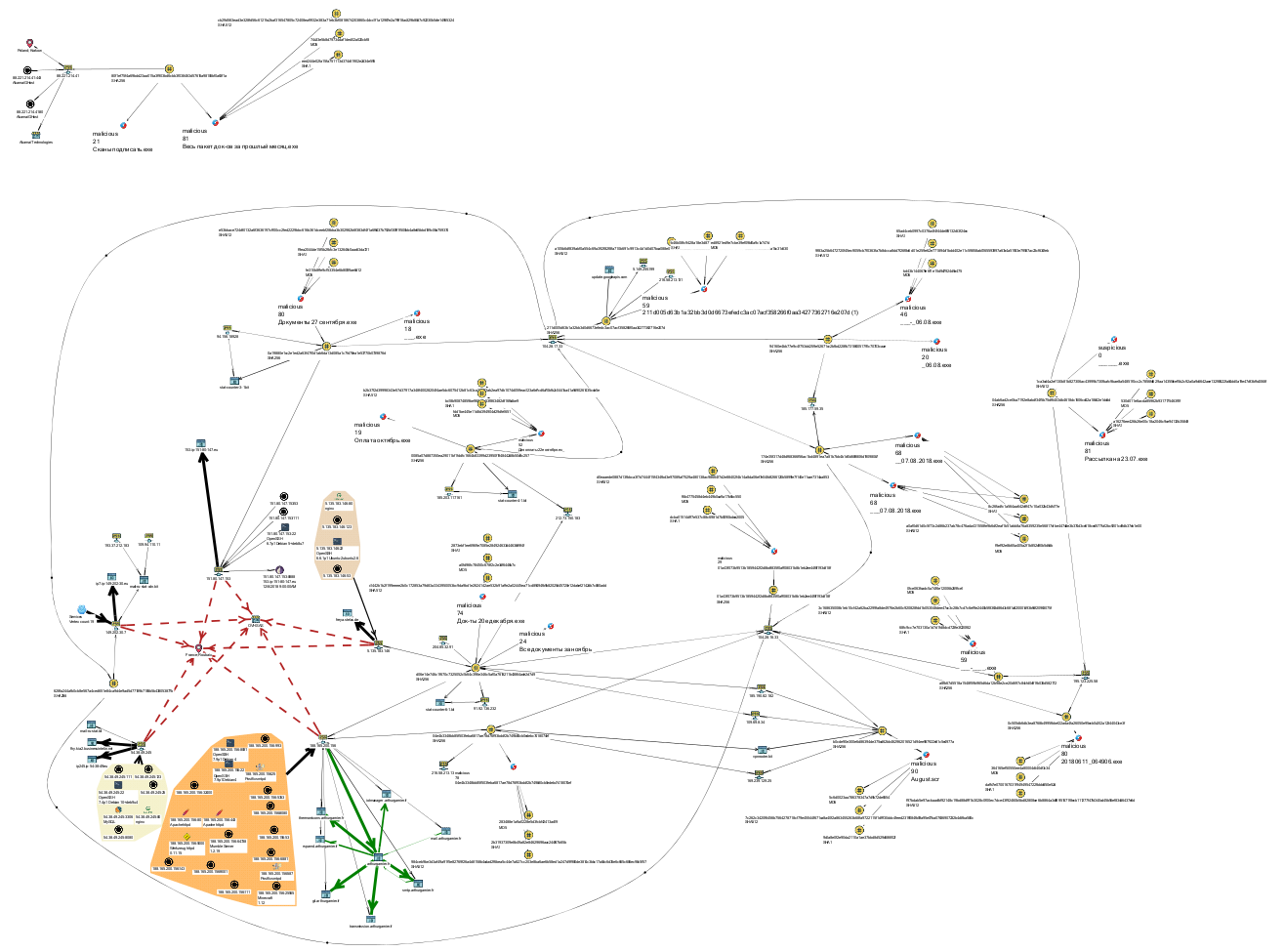
In the process, various difficulties arose, and, according to some input data, Hybrid-analysis showed a lack of information, and the Virustotal service returned a single data slice from Lampyre upon request, while searching from the interface at www.virustotal.com/#/home/upload provided another data set, through the search from the interface from the address www.virustotal.com/gui/home/upload - the most complete data. Several links on the final chart - made up by Lampyre in the manual mode for creating edges.
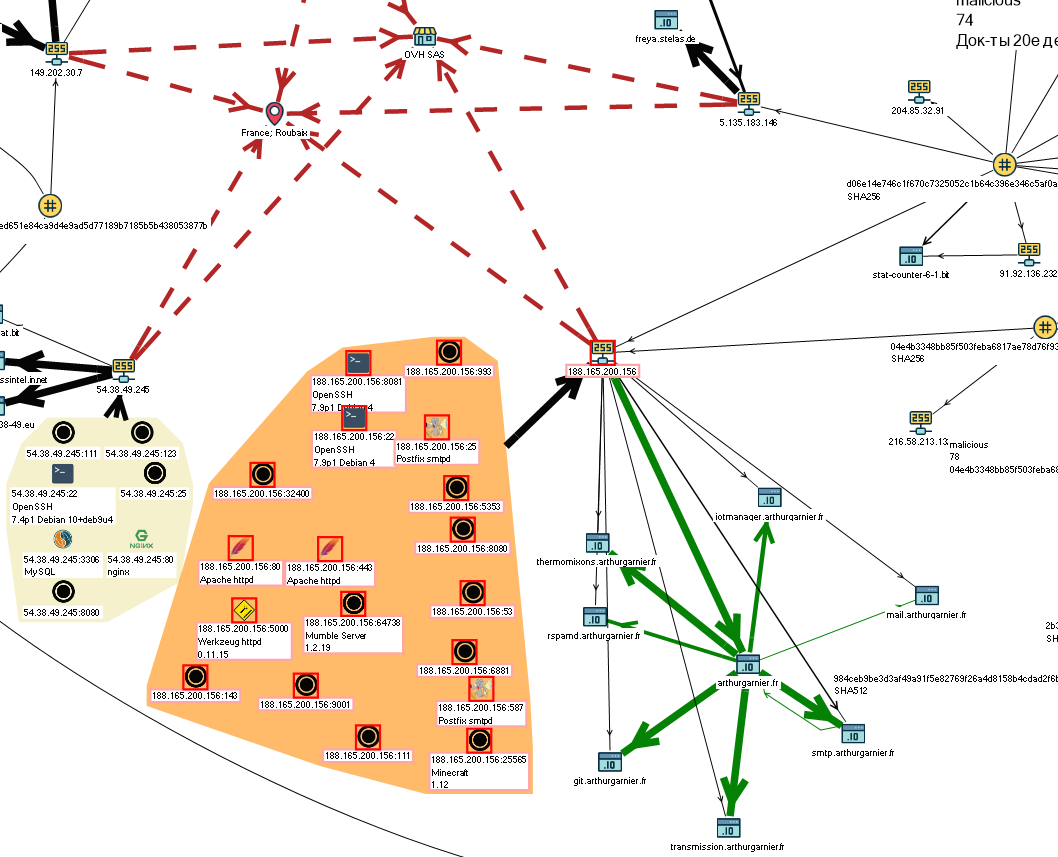
In my opinion, the diagram rather clearly shows the interrelation of ip-addresses, names and hash values of malicious files. The area on the column from ip-addresses is highlighted: 151.80.147.153, 188.165.200.156, 5.135.183.146, 54.38.49.245, 149.202.30.7,
IP addresses set by analysts GIB - 151.80.147.153, 188.165.200.156, 5.135.183.146, 185.190.82.182, 109.69.8.34
As can be seen from the diagram, the IP addresses presented in the GIB report - 185.190.82.182, 109.69.8.34 are associated with the hash: b0cde90e300e6d86394de375cd62bb462962016521d94ee987922e61c5e4977a, which in turn is associated with the Hybrid report object —r.r. of the year.
The next event, associated with malicious activity, starts from June 2018 and is increasing until the end of 2018.

In a good way, further investigation could be continued, having on hand the access control logs, registration, payment, and so on, to the IP addresses of the OVH provider. But alas, there is no such data, and the investigation could be completed, but ...
During the investigation, looking at the content of the web pages of resources did not leave the head of the French resource arthurgarnier.fr

It is worth noting that he did not get out of his head, because Russian torrents were being downloaded (handed out) from him.
The resource allegedly belongs to the French engineer “Arthur Garnier”, even his resume is indicated on the resource - arthurgarnier.fr/CV_A_Garnier.pdf . From which you can learn: github.com/ArthurGarnier , www.linkedin.com/in/arthur-garnier-13326880 . Moreover, according to the summary, it was compiled at the end of 2017; it rarely writes to github.com. The profile of www.linkedin.com states that from October 2017 to the present, Arthur is working as an engineer at Groupe SII. And it seems to be nothing, but, but the same thing ... on the page, among other things, the address of Arthur’s twitter account is specified. Twitter.com/Dark_Arthur

and then when you go to your account
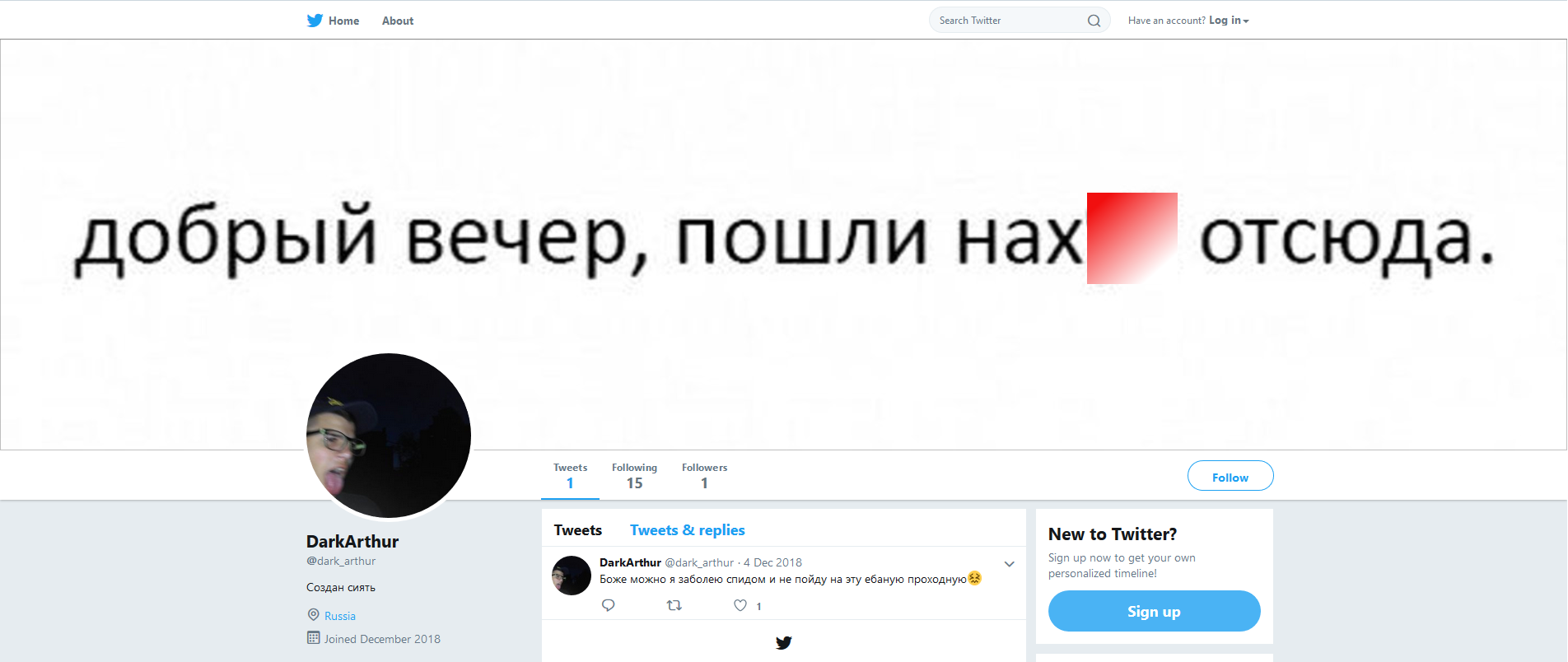
Who is behind this profile, why the Russian-speaking Twitter account is listed on Arthur’s website, and not the supposedly real, later found, account: twitter.com/UpsiloN1X - remains a question.
In conclusion, it is possible to say, of course, the initially stated goal is not achieved, but the results of such a study, as well as the process of knowledge itself, turned out to be very fascinating.
There are questions about the account on Twitter, the list of IP addresses, why so much information about the "Russian trace". I think it would be possible to continue an independent investigation by turning to the true Arthur, if he still manages his server (if the server is his own).
Source: https://habr.com/ru/post/436740/