How we monitored Black Hat Europe 2018
Half a year ago, I already wrote on Habré a note where I shared our experience in monitoring various IT and security conferences, in which Cisco is invited to work for SOC and NOC (Black Hat, Mobile World Congress, RSAC, etc.). Today I would like to share the experience of participating in the network monitoring center, which served the last European Black Hat, in which we have been helping the NOC for the second year. Together with RSA, Palo Alto, Gigamon and Rukus, we provided protection for the conference and training infrastructure. Cisco has taken on the task of monitoring and investigating DNS incidents (using Cisco Umbrella and Cisco Umbrella Investigate ), as well as automated malware analysis and Threat Intelligence using Cisco Threat Grid .

Ensuring the cybersecurity of conferences such as Black Hat is more than a difficult task, since the appearance of malicious files in traffic or attempts to access malicious domains is not something out of the ordinary. On the contrary, within the framework of various trainings, this is a completely normal event, which cannot be blocked, thereby disrupting the learning process and causing dissatisfaction with both the participants who paid their money and the instructors. The same is true for sponsors, who often demonstrate how their decisions work as part of their events, briefings and press conferences, which also requires attention and intelligibility from the NOC team.
The monitoring of the network on Black Hat was the responsibility of the RSA NetWitness solution, which was inspected, among other things, of files transmitted over various network protocols, including with various violations. For example, on the first day of one of the trainings, the download of the file table.png was recorded. NetWitness discovered that despite the extension inherent in images, the file header began with MZ, which could indicate that the file being transferred is actually executable. The file was transferred to Cisco Threat Grid for dynamic analysis.

A few minutes after downloading, the file table.png was recognized as a Trickbot Trojan.
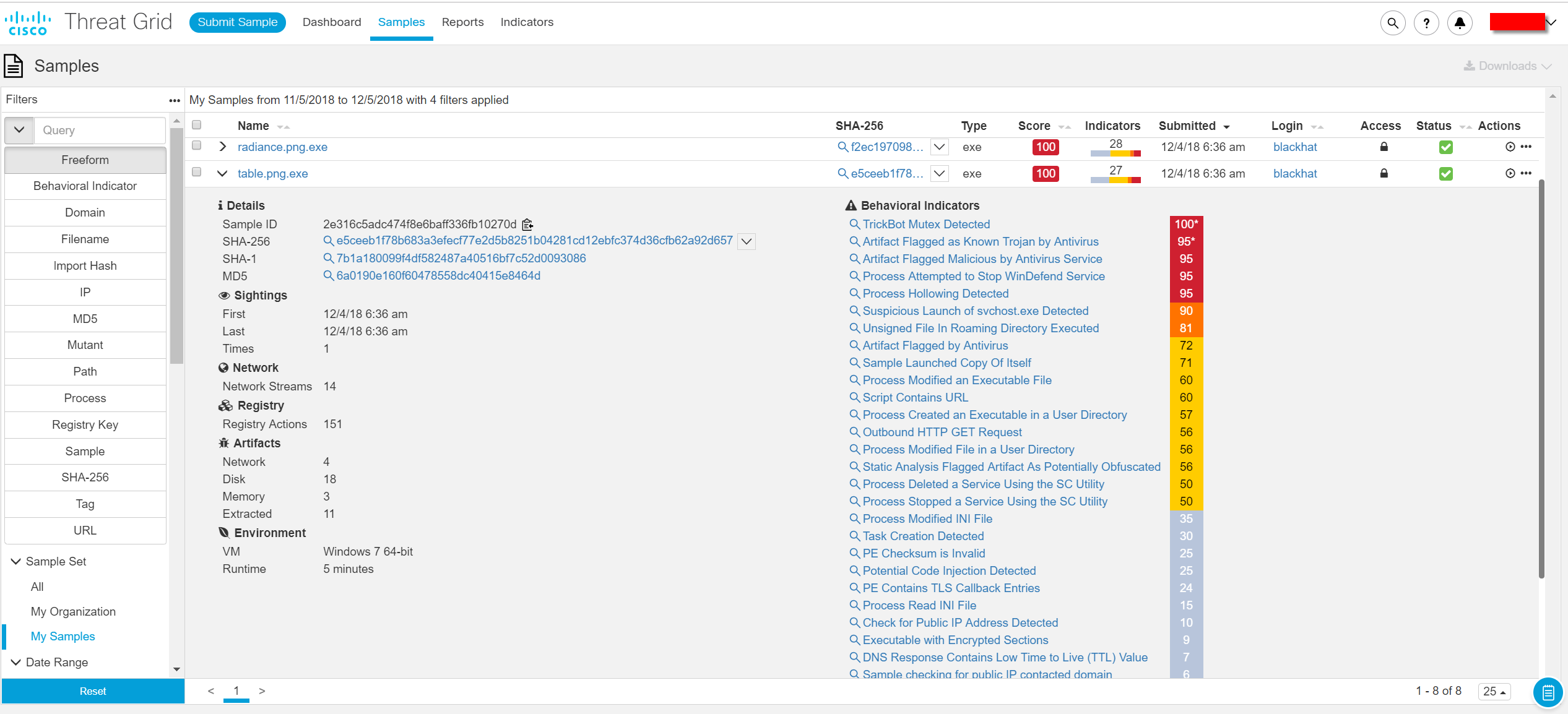
Detection occurred on a number of behavioral indicators, including the work with memory. It is enough to change just one bit in order to change the hash of the file, but it is rather difficult to rewrite the code for working with memory in order to become imperceptible to the malware analysis system. Exactly the same address space was used by Trickbot, which allowed us to make a conclusion about this malware.
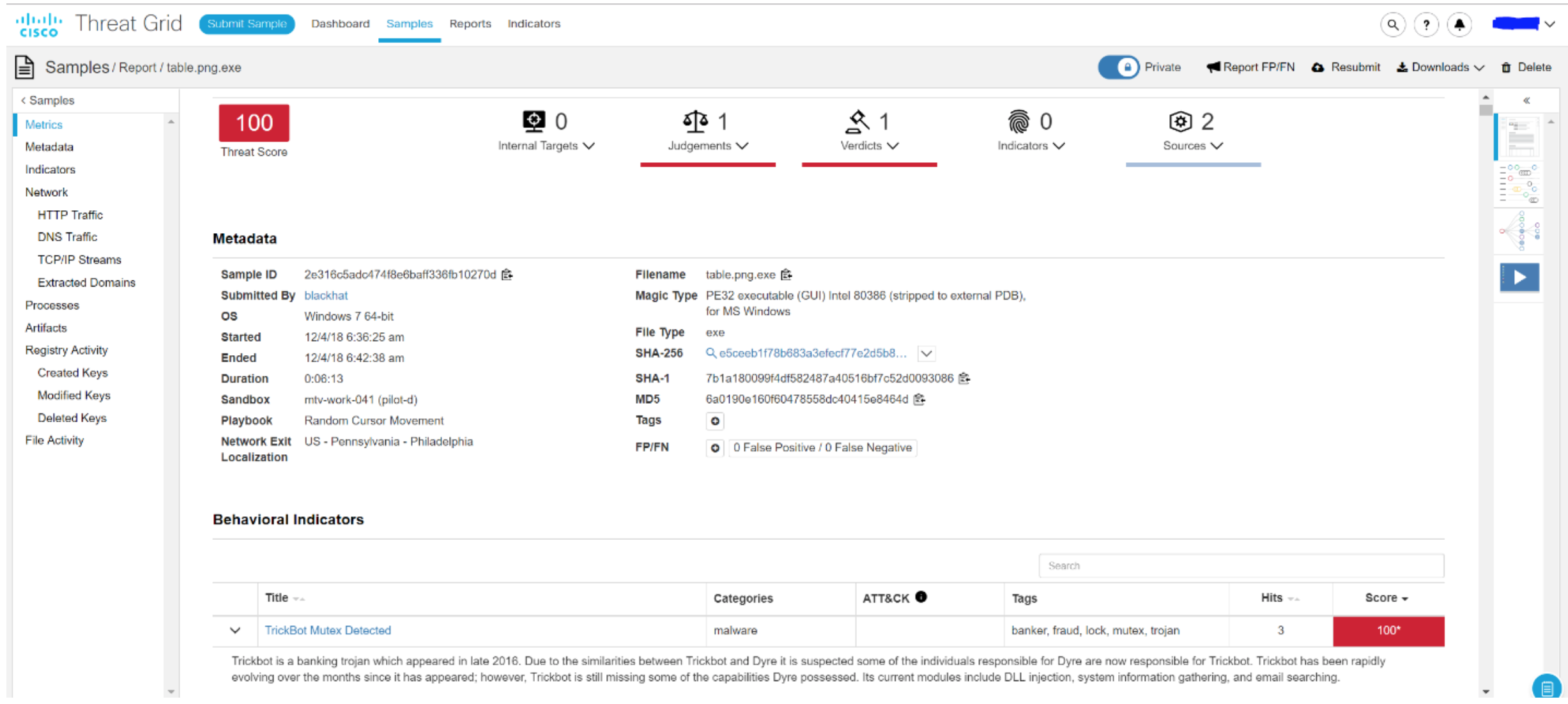
Trickbot is not a new trojan; It appeared at the end of 2016, but is still found on the Internet. The NOC team identified the MAC address of the laptop from which the Trickbot was downloaded, disguised as a .png file. We checked all the activity that was going on from this Macbook - it turned out that it took only a few minutes to try to connect to hundreds of DGA-domains, download dozens of various malicious programs, etc. In the course of the investigation, it was found out that the MacBook was used as part of one of the trainings; therefore, the NOC team did not block this activity, while making efforts so that nothing dangerous would fall outside the limits of this training on the computers of other Black Hat Europe participants.
As the function expands in our solutions, we test them in the framework of conferences where we are invited to participate in SOC / NOC. This time, on the very first day, we turned on the Intellgent Proxy feature in Cisco Umbrella, which allows you to proxy Web traffic by tracking threats, content and applications transmitted as part of a Web interaction.
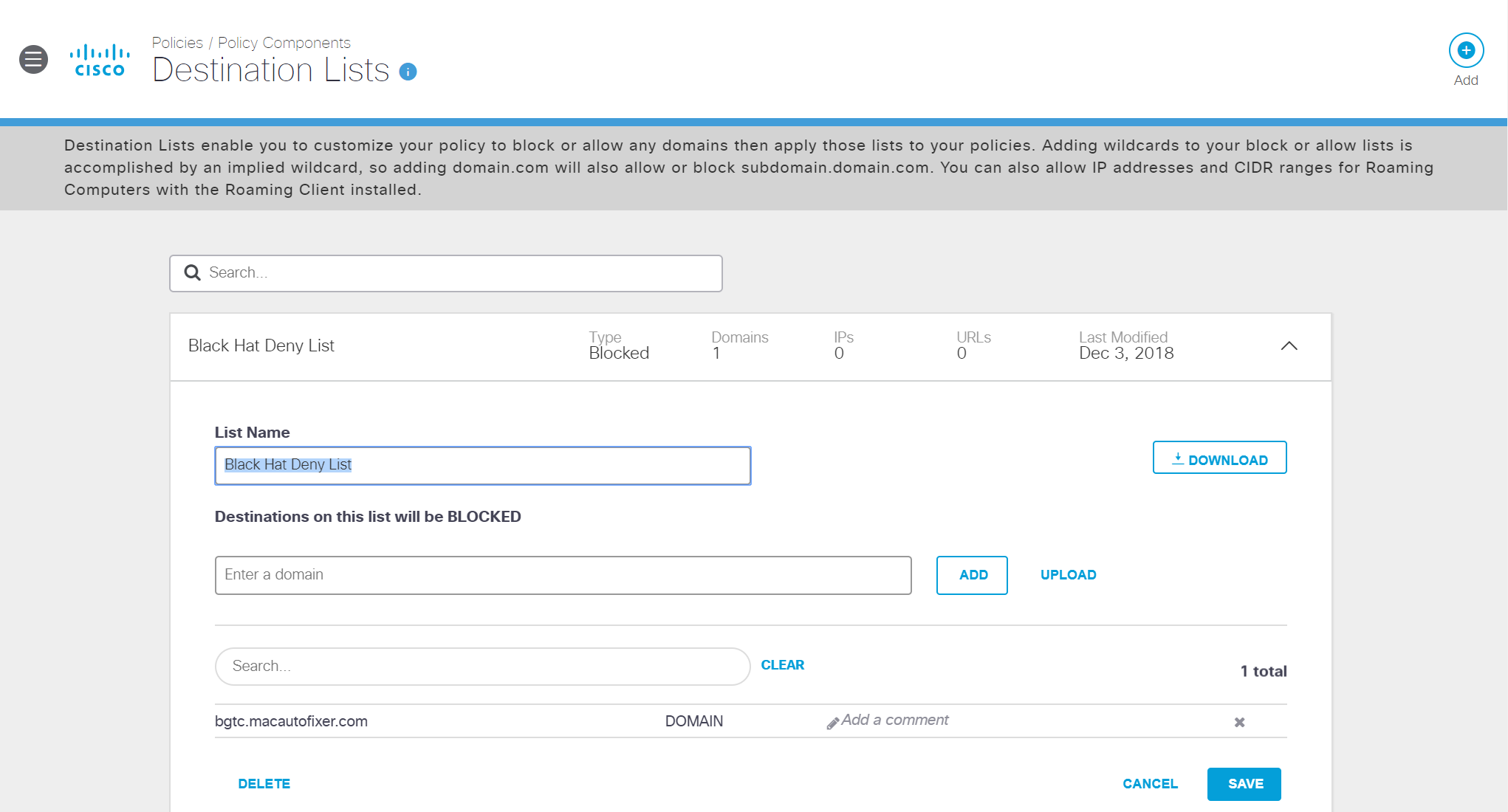
In the morning of the first day we recorded the alarm associated with access to the macautofixer.
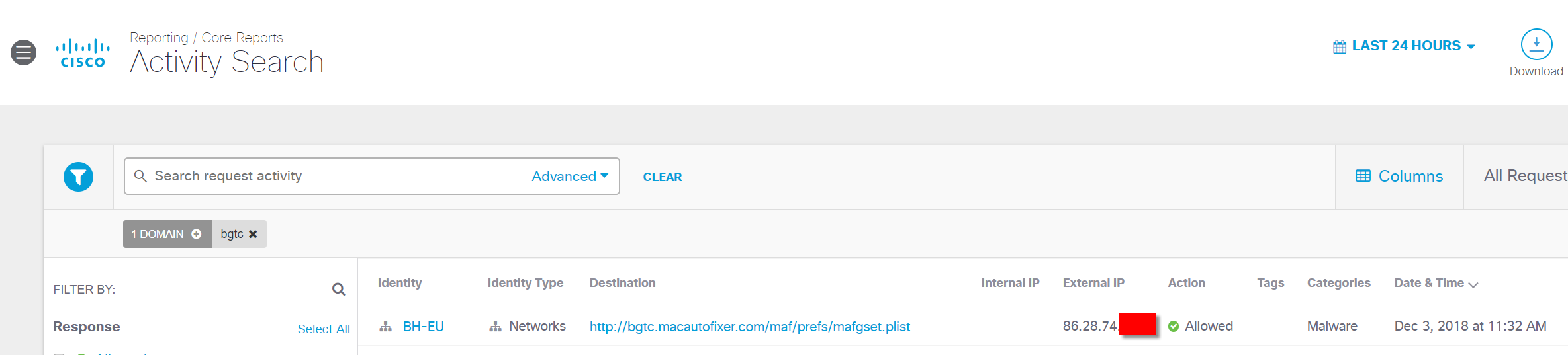
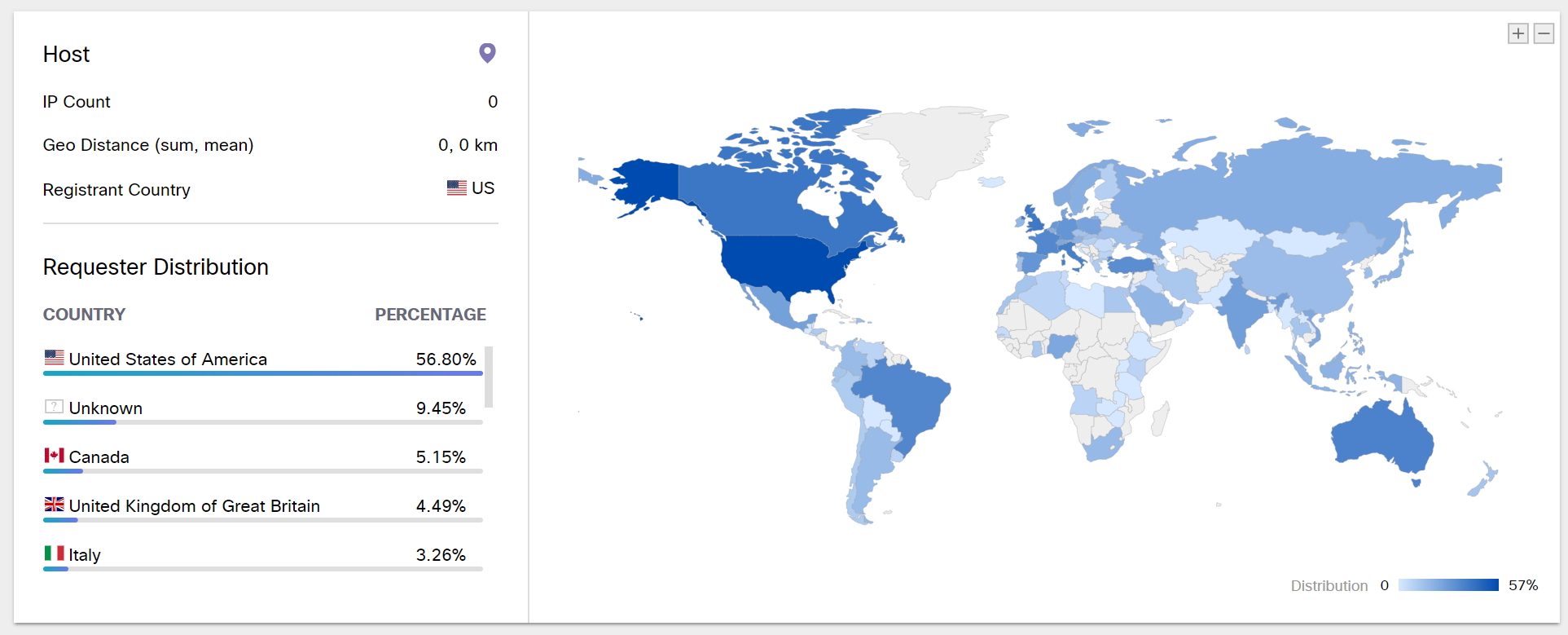
The NOC team launched an investigation, including the analysis of ITU logs, the reconstruction of network packets and the identification of the machine that initiated the request. Judging by the data of Cisco Umbrella Investigate, this is a rather popular malicious resource - about 20 thousand requests are recorded daily to it:
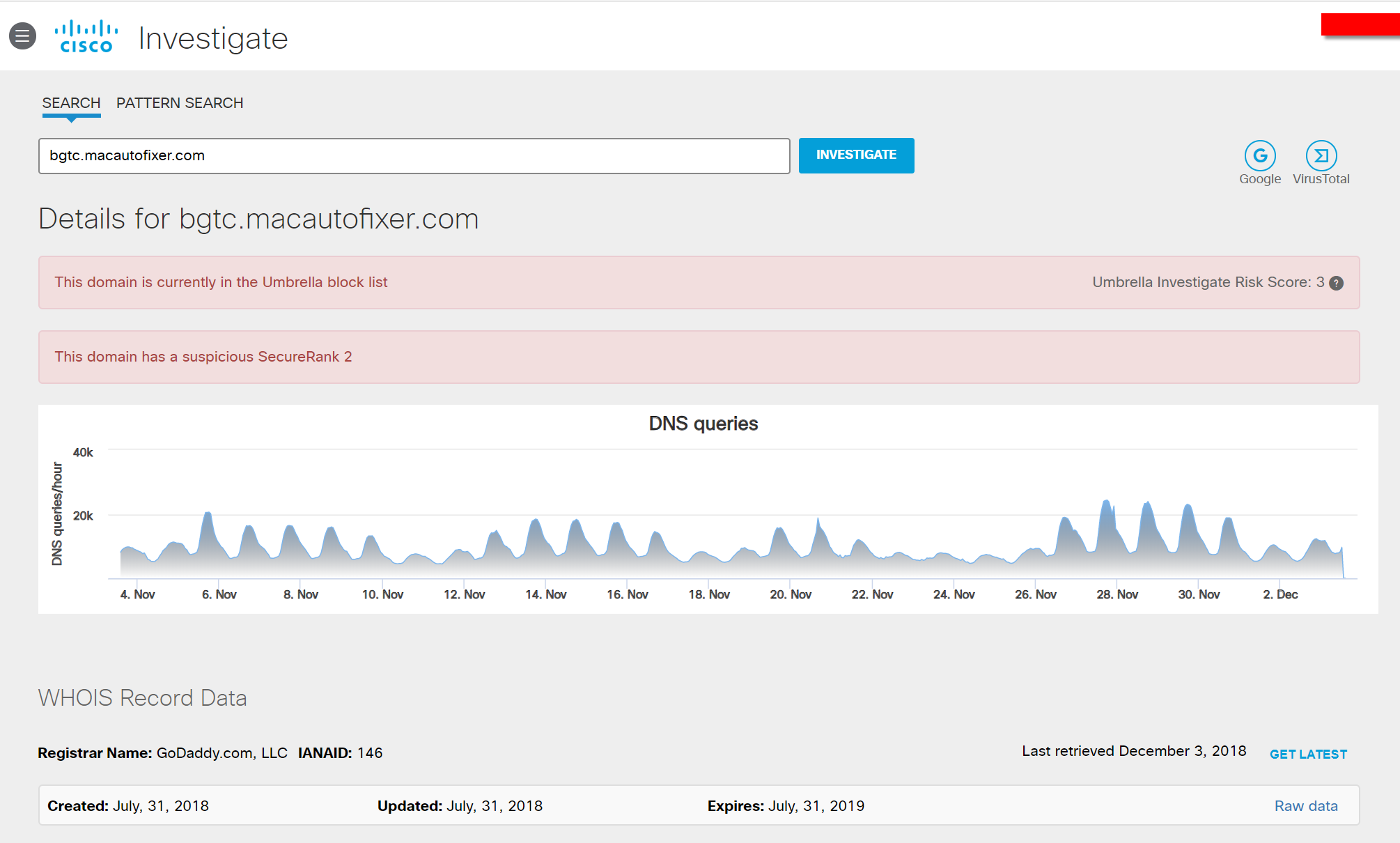
mainly from the USA:
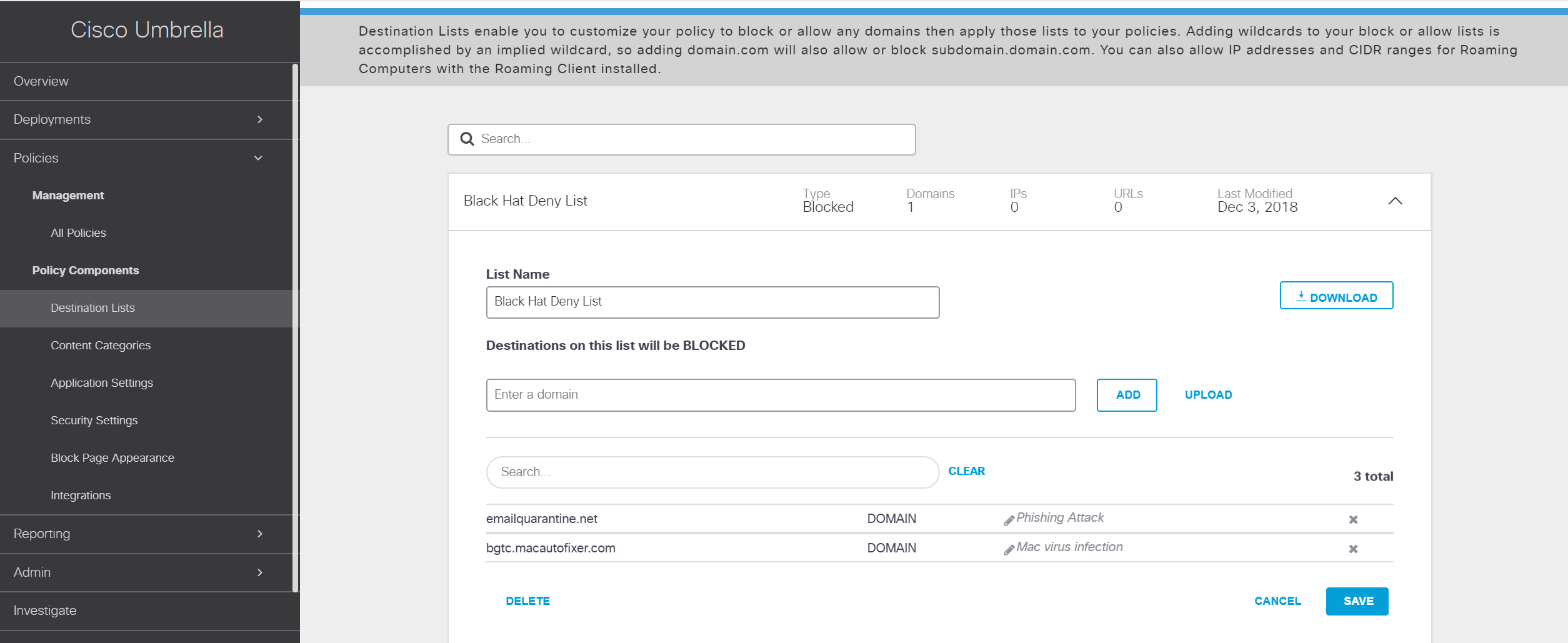
It turned out that one of the computers of the conference organizers was infected. The BlackHat policy allows access to malicious resources until it is identified that this is an external attack on Black Hat resources, as recorded in this case. The domain has been locked by Cisco Umbrella for this and all future Black Hat conferences.
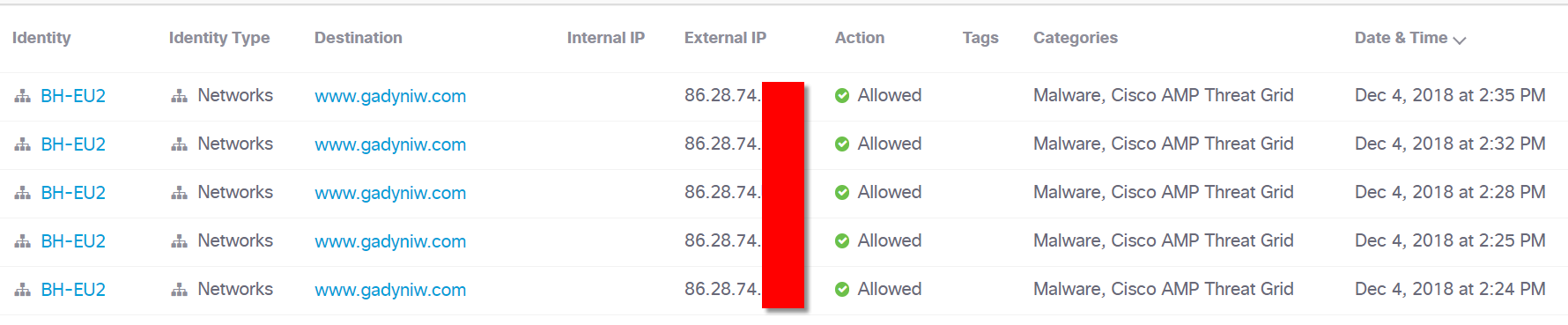
On the second day, several Wi-Fi network users were infected with the Simba malware, which was trying to connect to fairly old command servers:
Domain gadyniw [.] Com was identified by Cisco Threat Grid as malicious and blocked. The investigation revealed that this malware was used as part of one of the trainings, in which participants had unpatched computers. We advised the instructor to remind infected participants not to connect with their laptops to the public Wi-Fi segment.
In the course of Black Hat, its organizers, the UBM company, encountered a massive phishing attack via e-mail, which is still the most massive method of attacking organizations.
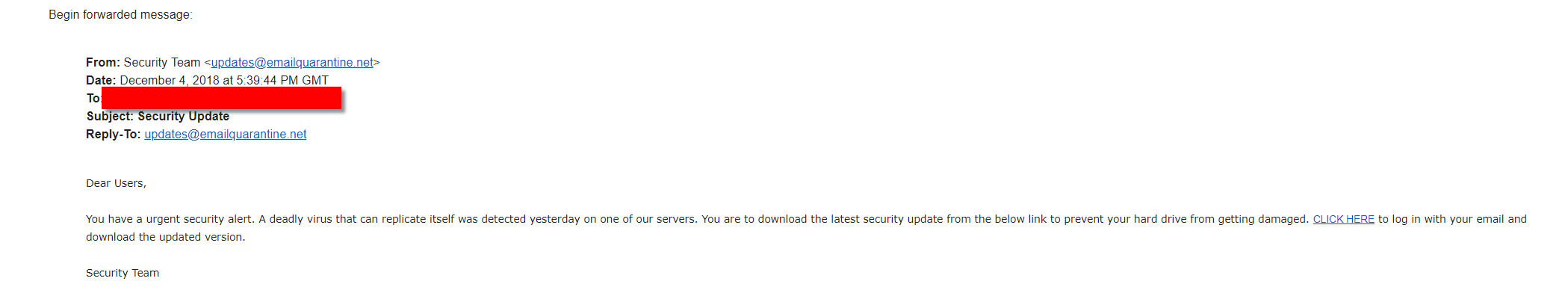
We conducted a CLICK HERE reference study using the Glovebox function in the Threat Grid, which allows you to interact with the virtual machine without the risk of infection. In two browsers, the link returned an error, as if the page needed did not exist.
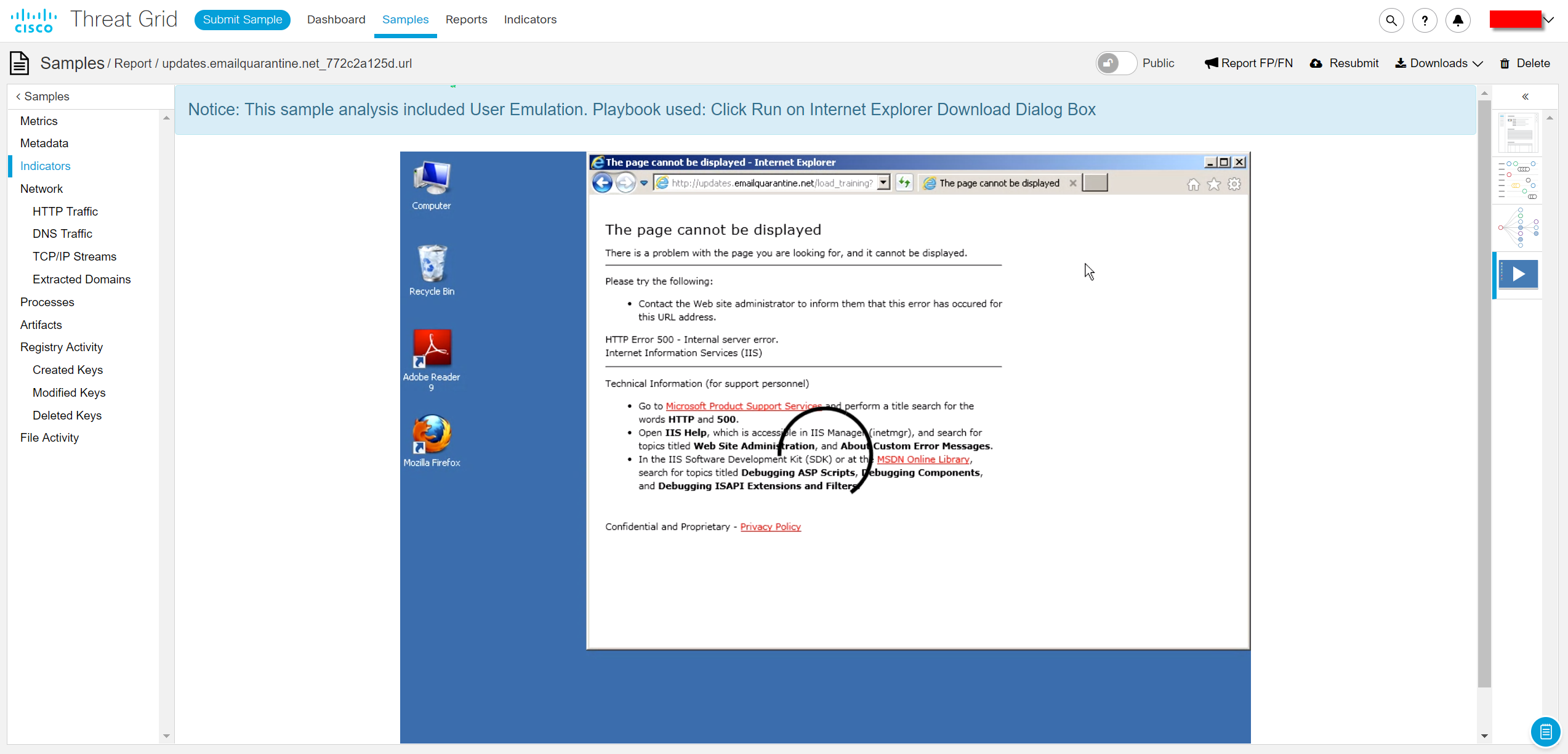
However, in the report we recorded about 100 open network connections, about 100 artifacts loaded on the disk, including JavaScript, as well as about 170 registry changes.
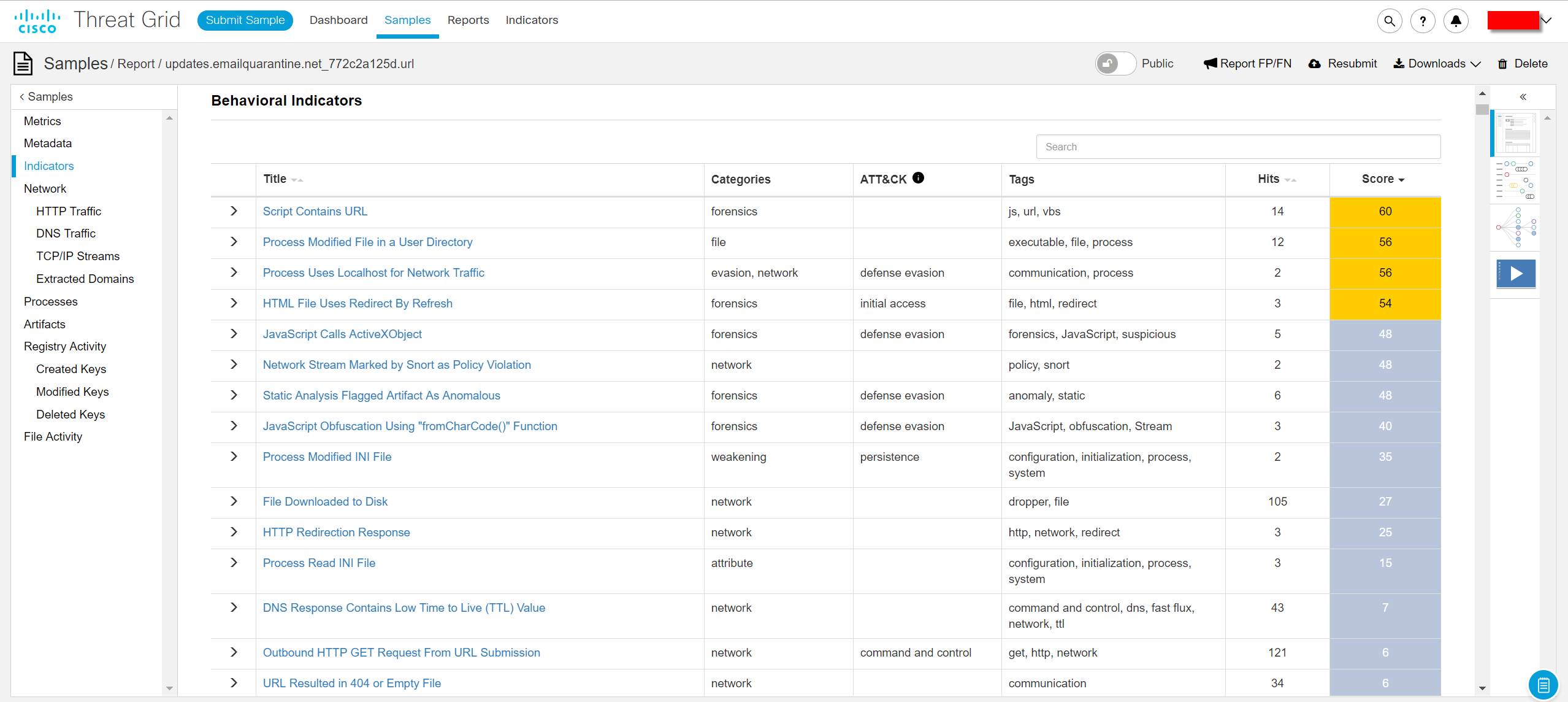
We have added this domain to the blacklist for all Black Hat conferences.
In 2017, we recorded about 5.8 million DNS requests at Black Hat Europe conferences. A year later, in 2018, we recorded 7.6 million requests, of which about 4,000 were associated with malicious activity, command servers or phishing.
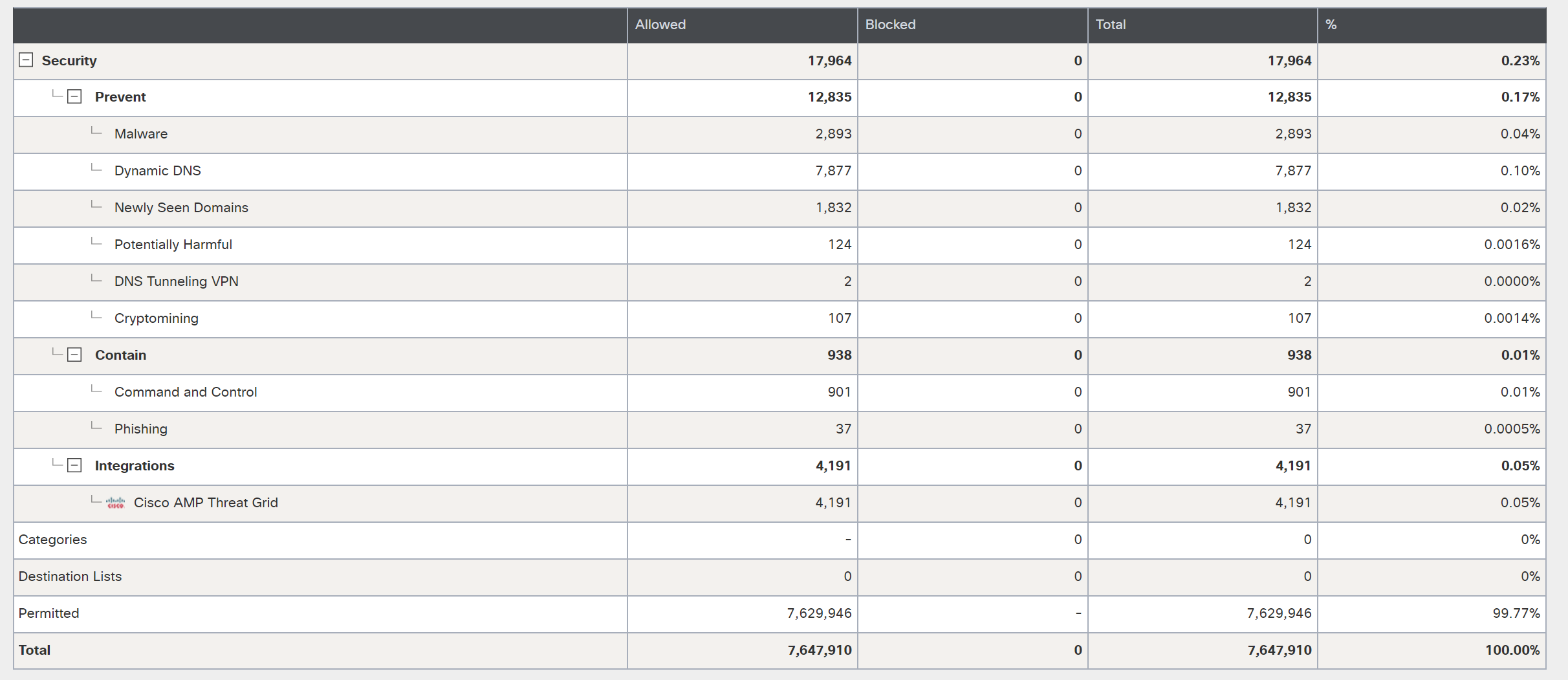
New on European Black Hat was the notification of users whose credentials for e-mail were transmitted in the clear. Fortunately, compared with previous conferences this time, only 14 users sent their mail in unprotected mode. This was the first conference at which we did not observe financial or banking documents transmitted in open form.
The NOC team also recorded a large number of references to mining resources. For the first time, we began to record such attempts a year ago in Europe, followed by a big surge on the Asian Black Hat.

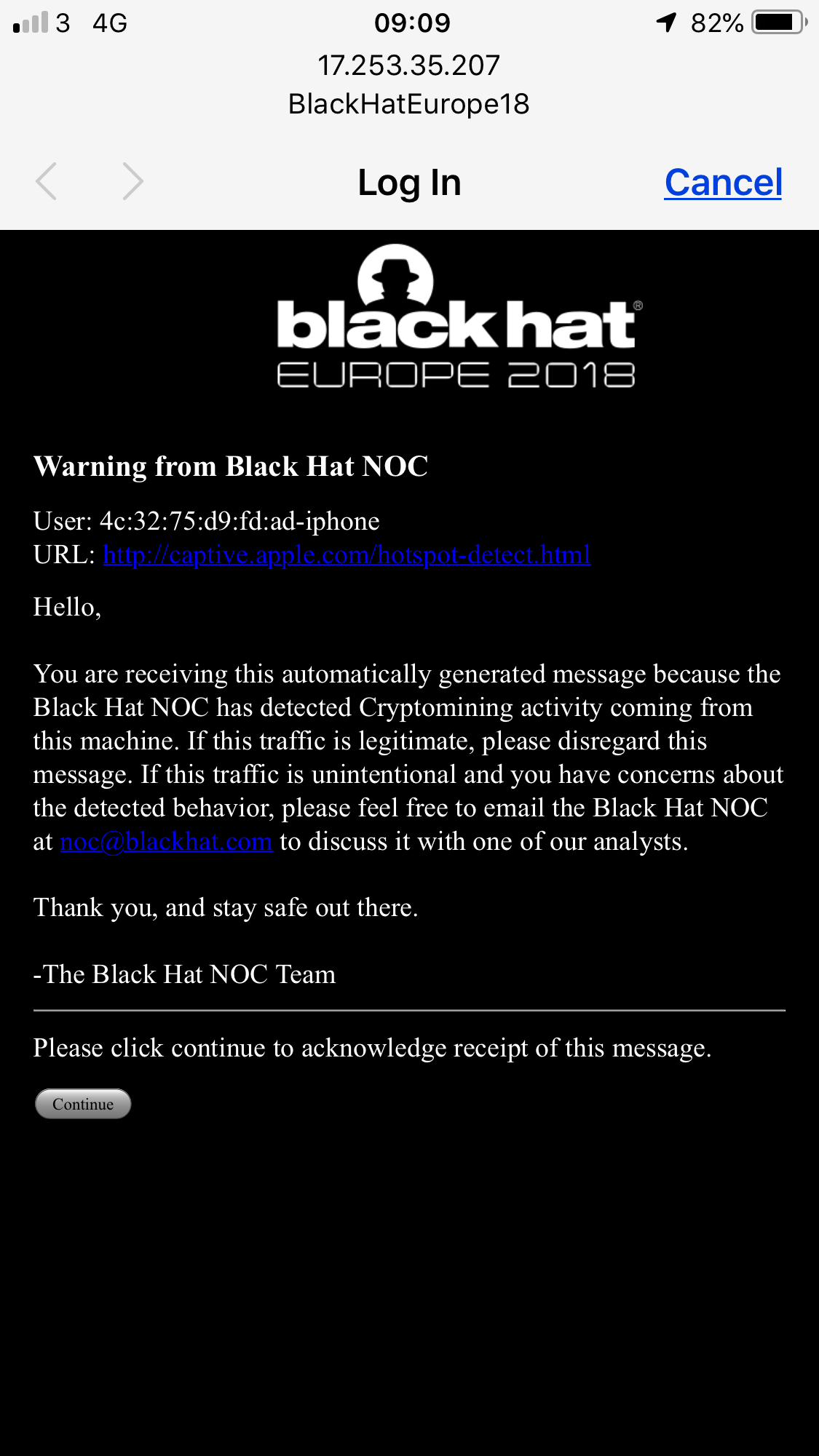
Users with cryptomines were warned by the Black Hat NOC team. If they used mining consciously, then there is no problem. If it was about infection, the users were offered help in treating the computer.
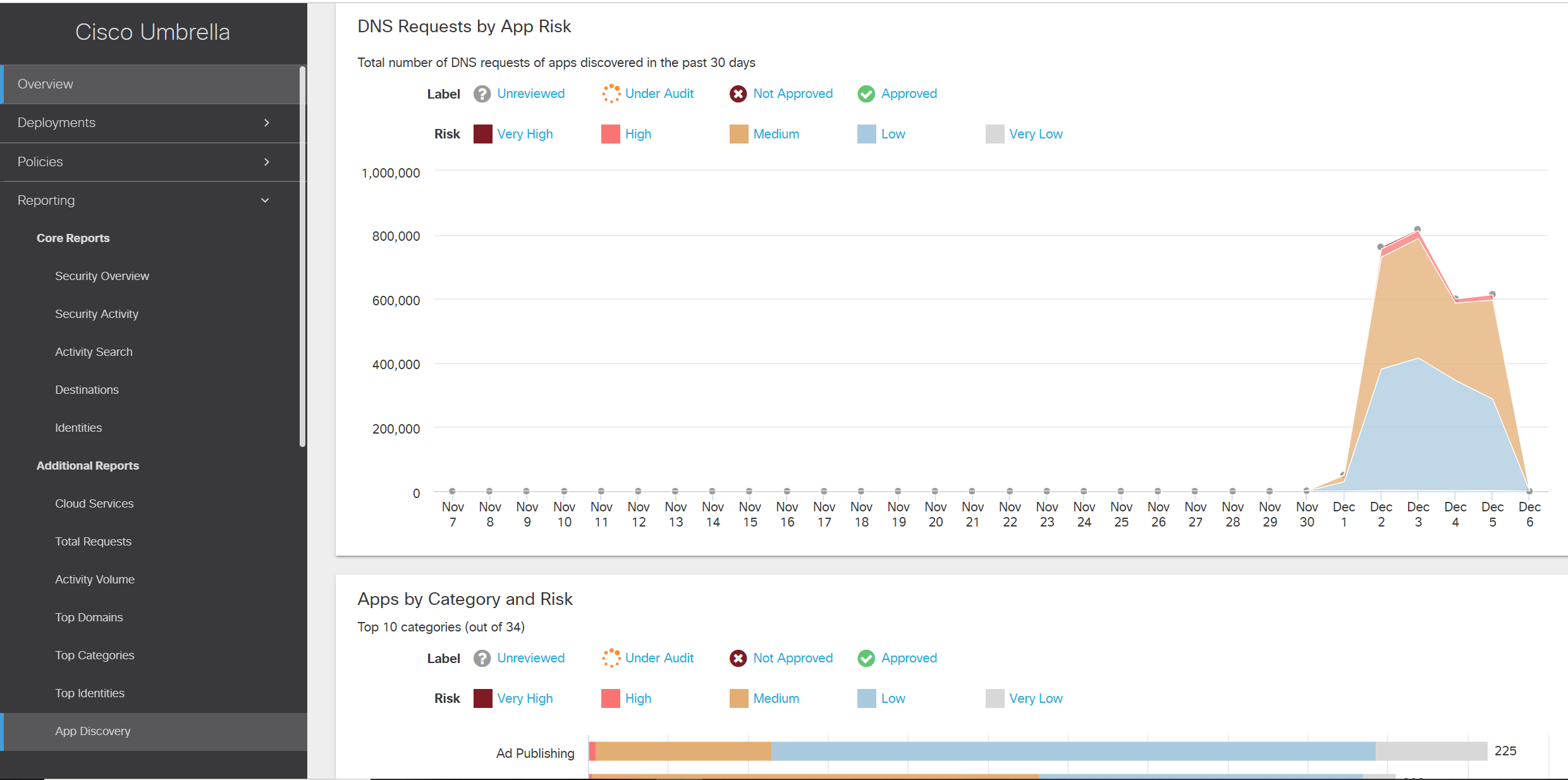
Also, the new Cisco Umbrella feature, which was tested on European Black Hat, was App Discovery, which allows you to identify the applications used (now there are more than 2000) and assess their risk to the enterprise.
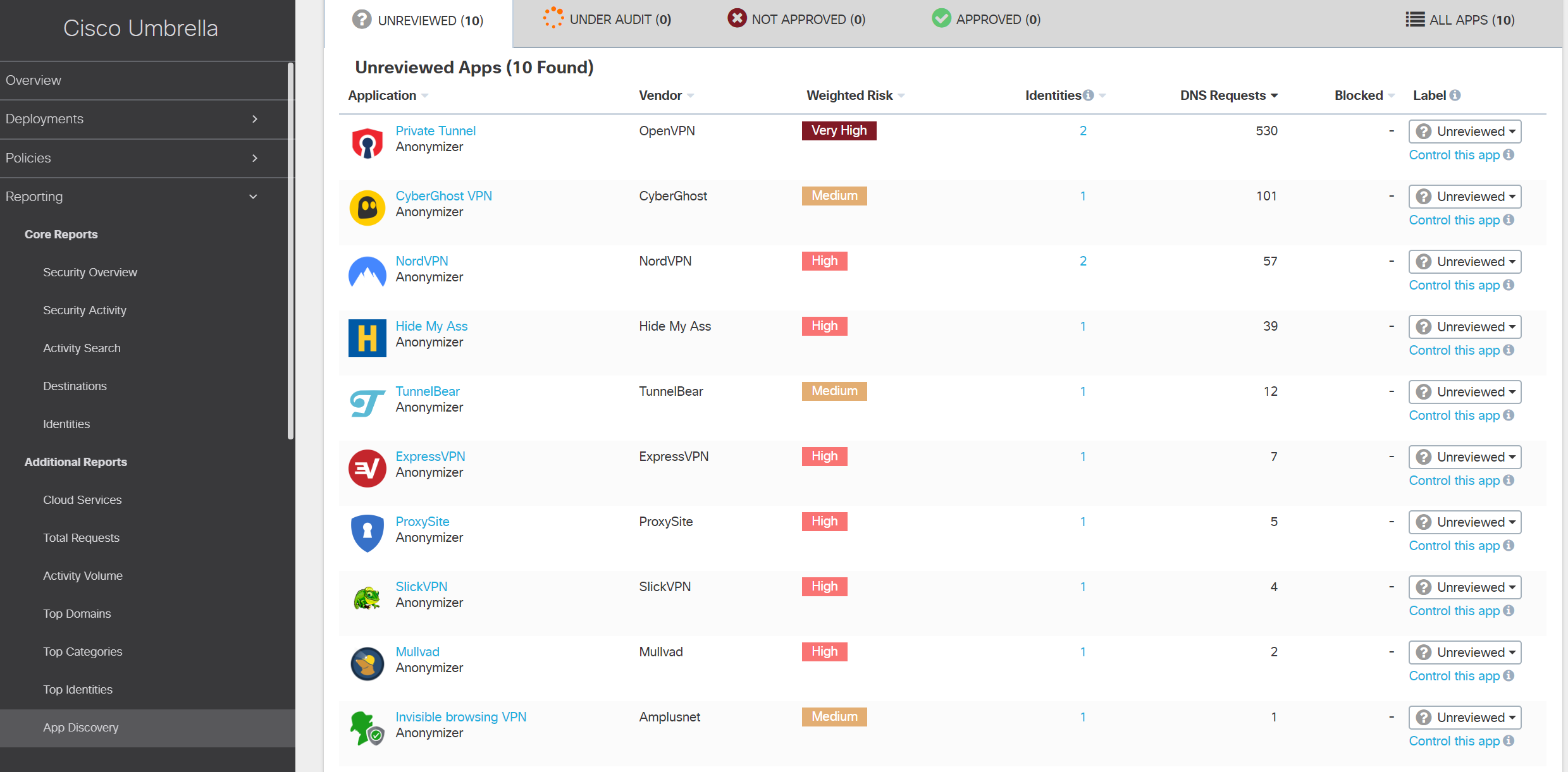
It is clear that the policy of Black Hat is different from a normal company, in which anonymizers and VPN services that may violate corporate security policies may be prohibited. At the conference on information security, the use of such applications is quite normal and, therefore, they were not blocked. But it was interesting to look at the most popular solutions of this class.
The next stop for the Cisco Security team will be the RSA conference, which will be held this March in San Francisco, where we will again be responsible for the work of RSA SOC. If suddenly you plan to visit this exhibition, then we invite you on an excursion to the security monitoring center of one of the largest world events on information security, which annually is visited by tens of thousands of people. If you are in RSAC days in San Francisco and want to visit the exhibition, but do not have a ticket for it, then Cisco will give you a promotional code for a free pass to the exhibition - X8SCISCOP.


Ensuring the cybersecurity of conferences such as Black Hat is more than a difficult task, since the appearance of malicious files in traffic or attempts to access malicious domains is not something out of the ordinary. On the contrary, within the framework of various trainings, this is a completely normal event, which cannot be blocked, thereby disrupting the learning process and causing dissatisfaction with both the participants who paid their money and the instructors. The same is true for sponsors, who often demonstrate how their decisions work as part of their events, briefings and press conferences, which also requires attention and intelligibility from the NOC team.
Obfuscated Malware
The monitoring of the network on Black Hat was the responsibility of the RSA NetWitness solution, which was inspected, among other things, of files transmitted over various network protocols, including with various violations. For example, on the first day of one of the trainings, the download of the file table.png was recorded. NetWitness discovered that despite the extension inherent in images, the file header began with MZ, which could indicate that the file being transferred is actually executable. The file was transferred to Cisco Threat Grid for dynamic analysis.

A few minutes after downloading, the file table.png was recognized as a Trickbot Trojan.

Detection occurred on a number of behavioral indicators, including the work with memory. It is enough to change just one bit in order to change the hash of the file, but it is rather difficult to rewrite the code for working with memory in order to become imperceptible to the malware analysis system. Exactly the same address space was used by Trickbot, which allowed us to make a conclusion about this malware.

Trickbot is not a new trojan; It appeared at the end of 2016, but is still found on the Internet. The NOC team identified the MAC address of the laptop from which the Trickbot was downloaded, disguised as a .png file. We checked all the activity that was going on from this Macbook - it turned out that it took only a few minutes to try to connect to hundreds of DGA-domains, download dozens of various malicious programs, etc. In the course of the investigation, it was found out that the MacBook was used as part of one of the trainings; therefore, the NOC team did not block this activity, while making efforts so that nothing dangerous would fall outside the limits of this training on the computers of other Black Hat Europe participants.
Intelligent proxy
As the function expands in our solutions, we test them in the framework of conferences where we are invited to participate in SOC / NOC. This time, on the very first day, we turned on the Intellgent Proxy feature in Cisco Umbrella, which allows you to proxy Web traffic by tracking threats, content and applications transmitted as part of a Web interaction.
In the morning of the first day we recorded the alarm associated with access to the macautofixer.

The NOC team launched an investigation, including the analysis of ITU logs, the reconstruction of network packets and the identification of the machine that initiated the request. Judging by the data of Cisco Umbrella Investigate, this is a rather popular malicious resource - about 20 thousand requests are recorded daily to it:

mainly from the USA:

It turned out that one of the computers of the conference organizers was infected. The BlackHat policy allows access to malicious resources until it is identified that this is an external attack on Black Hat resources, as recorded in this case. The domain has been locked by Cisco Umbrella for this and all future Black Hat conferences.

On the second day, several Wi-Fi network users were infected with the Simba malware, which was trying to connect to fairly old command servers:
- www [.] gadyniw [.] com / hbt.php? rewrite = login.php
- purycap [.] com / login.php
- gadyniw [.] com / hbt.php? rewrite = login.php
- ww1 [.] ysyfyj [.] com / login.php
Domain gadyniw [.] Com was identified by Cisco Threat Grid as malicious and blocked. The investigation revealed that this malware was used as part of one of the trainings, in which participants had unpatched computers. We advised the instructor to remind infected participants not to connect with their laptops to the public Wi-Fi segment.

Phishing attack
In the course of Black Hat, its organizers, the UBM company, encountered a massive phishing attack via e-mail, which is still the most massive method of attacking organizations.

We conducted a CLICK HERE reference study using the Glovebox function in the Threat Grid, which allows you to interact with the virtual machine without the risk of infection. In two browsers, the link returned an error, as if the page needed did not exist.

However, in the report we recorded about 100 open network connections, about 100 artifacts loaded on the disk, including JavaScript, as well as about 170 registry changes.

We have added this domain to the blacklist for all Black Hat conferences.

DNS activity
In 2017, we recorded about 5.8 million DNS requests at Black Hat Europe conferences. A year later, in 2018, we recorded 7.6 million requests, of which about 4,000 were associated with malicious activity, command servers or phishing.

New on European Black Hat was the notification of users whose credentials for e-mail were transmitted in the clear. Fortunately, compared with previous conferences this time, only 14 users sent their mail in unprotected mode. This was the first conference at which we did not observe financial or banking documents transmitted in open form.
The NOC team also recorded a large number of references to mining resources. For the first time, we began to record such attempts a year ago in Europe, followed by a big surge on the Asian Black Hat.

Users with cryptomines were warned by the Black Hat NOC team. If they used mining consciously, then there is no problem. If it was about infection, the users were offered help in treating the computer.

Also, the new Cisco Umbrella feature, which was tested on European Black Hat, was App Discovery, which allows you to identify the applications used (now there are more than 2000) and assess their risk to the enterprise.

It is clear that the policy of Black Hat is different from a normal company, in which anonymizers and VPN services that may violate corporate security policies may be prohibited. At the conference on information security, the use of such applications is quite normal and, therefore, they were not blocked. But it was interesting to look at the most popular solutions of this class.

The next stop for the Cisco Security team will be the RSA conference, which will be held this March in San Francisco, where we will again be responsible for the work of RSA SOC. If suddenly you plan to visit this exhibition, then we invite you on an excursion to the security monitoring center of one of the largest world events on information security, which annually is visited by tens of thousands of people. If you are in RSAC days in San Francisco and want to visit the exhibition, but do not have a ticket for it, then Cisco will give you a promotional code for a free pass to the exhibition - X8SCISCOP.

Source: https://habr.com/ru/post/436786/