802.1x, EX2200, NPS and all-all-all ...
The idea of using 802.1x as a means to combat unauthorized access to the network is not new. Each of us must have come across a courier from the delivery service, who has a patchcord from the sleeve of his signature jacket, and you can already see how he, noticing a free RJ-45 outlet, rushes to her and…
However, if in the general concept of using and configuring 802.1x with authorization via RADIUS is beaten and simple, in this case there was an incident, the solution of which I propose below.
Given:
A separate FineGrainedPasswordPolicy has been created for departments or security groups containing these devices in order to be able to set passwords that do not meet security standards.
Original config for 802.1x on EX2200:
All workstations are logged in without any problems, but any of the above riffraffs is not. Wireshark persistently showed that NPS sends an Access-Reject with EAP code 4, which, as is well known in narrow circles, means Failure.
Informative, however, as always ...
The protocol used by supplicant for mac-radius authentication, the default is EAP-MD5.
There are more options for PEAP and PAP.
PEAP is not available for EX2200.
We try to configure PAP. In plain text, of course, I didn’t really want to, but, for not having the best, we drive in the cherished team
and (drum roll) - Syntax error - Juniper helpfully informs us.
During fights, threats with a soldering iron and other repressive measures, the Juniper site suggested that this option is available only for firmware from the 15.1 release.
It would seem, here it is, the solution. But no, the same Juniper not only recommends, but also in every possible way protects customers from such lewdness as firmware 15.1 on EX2200. Grit, utilization of the CPU and RAM is above the norm, therefore 12.3 is the ceiling of the JunOS version for the lucky owners of EX2200.
OK, we will deal with the protocol that sends the switch data to the NPS.
So it turned out that by default he sends them to eap-md5, which one? - correctly, disabled in Windows Server, starting already with the 2008 release - they say, non-securized. Several queries to Google give the desired result - a reg-file that includes the protocol we need.
However, the NPS persistently responds to requests from printers and other Access-Rejects .
He took out cigarettes, remembered that he had thrown, hid ...
Google, who in the world ... But no, this is from another opera ...
Ok Google? 802.1x MAC authentication with NPS RADIUS
After a few pages of Google, on the forum ubnt found the desired. It is necessary to include several parameters for credentials of devices, then recreate passwords and - voila - Miracle. Moreover, it turned out even better than expected. Eap-md5, of course, is not God's message, but still better than plain text.
The resulting config, settings and screenshots of the policy under the spoiler.
Total:
List of tips, guides and resources:
Juniper recommendations for software version on EX2200
Juniper EAP-PAP support for MAC RADIUS Authentication
UBNT community, which gave the last kick in the right direction
However, if in the general concept of using and configuring 802.1x with authorization via RADIUS is beaten and simple, in this case there was an incident, the solution of which I propose below.
Given:
- Access switch - EX2200, JunOS 12.3R2.
- RADIUS server based on NPS Windows Server 2012R2.
- A diverse zoo of devices of the form - TVs, AppleTV, printers and other small network animals, unable as normal and adequate members of the network to authenticate with certificates or PEAP. For each of the devices in Active Directory, its own account in the corresponding OU with sAMAccountName = MAC (in lower case, without division signs), password = sAMAccountName.
A separate FineGrainedPasswordPolicy has been created for departments or security groups containing these devices in order to be able to set passwords that do not meet security standards.
Original config for 802.1x on EX2200:
//set actual interfaces set interfaces interface-range ACCESS_PORTS member "ge-0/0/[0-40]" // Config interface range as L2 ports set interfaces interface-range ACCESS_PORTS unit 0 family ethernet-switching set protocols dot1x authenticator authentication-profile-name dynamicvlan set protocols dot1x authenticator radius-options use-vlan-id set protocols dot1x authenticator interface ACCESS_PORTS supplicant single set protocols dot1x authenticator interface ACCESS_PORTS transmit-period 10 set protocols dot1x authenticator interface ACCESS_PORTS retries 0 set protocols dot1x authenticator interface ACCESS_PORTS mac-radius set protocols dot1x authenticator interface ACCESS_PORTS supplicant-timeout 10 //set actual reject-vlan and fail-vlan set protocols dot1x authenticator interface ACCESS_PORTS server-reject-vlan default set protocols dot1x authenticator interface ACCESS_PORTS server-fail vlan-name default set protocols dot1x authenticator interface ACCESS_PORTS guest-vlan default //set actual password set access radius-server 172.17.xx secret "xxx" set access profile dynamicvlan authentication-order radius set access profile dynamicvlan radius authentication-server 172.17.xx All workstations are logged in without any problems, but any of the above riffraffs is not. Wireshark persistently showed that NPS sends an Access-Reject with EAP code 4, which, as is well known in narrow circles, means Failure.
Informative, however, as always ...
The protocol used by supplicant for mac-radius authentication, the default is EAP-MD5.
There are more options for PEAP and PAP.
PEAP is not available for EX2200.
We try to configure PAP. In plain text, of course, I didn’t really want to, but, for not having the best, we drive in the cherished team
set protocols dot1x authenticator interface ACCESS_PORTS mac-radius authentication-protocol pap and (drum roll) - Syntax error - Juniper helpfully informs us.
During fights, threats with a soldering iron and other repressive measures, the Juniper site suggested that this option is available only for firmware from the 15.1 release.
It would seem, here it is, the solution. But no, the same Juniper not only recommends, but also in every possible way protects customers from such lewdness as firmware 15.1 on EX2200. Grit, utilization of the CPU and RAM is above the norm, therefore 12.3 is the ceiling of the JunOS version for the lucky owners of EX2200.
OK, we will deal with the protocol that sends the switch data to the NPS.
So it turned out that by default he sends them to eap-md5, which one? - correctly, disabled in Windows Server, starting already with the 2008 release - they say, non-securized. Several queries to Google give the desired result - a reg-file that includes the protocol we need.
However, the NPS persistently responds to requests from printers and other Access-Rejects .
He took out cigarettes, remembered that he had thrown, hid ...
Google, who in the world ... But no, this is from another opera ...
Ok Google? 802.1x MAC authentication with NPS RADIUS
After a few pages of Google, on the forum ubnt found the desired. It is necessary to include several parameters for credentials of devices, then recreate passwords and - voila - Miracle. Moreover, it turned out even better than expected. Eap-md5, of course, is not God's message, but still better than plain text.
The resulting config, settings and screenshots of the policy under the spoiler.
EX2200 configuration, NPS policy
The magic reg-file that includes support for EAP-MD5 in Windows Server 2012 R2
After making changes to the registry, you must restart the NPS service.
The script that exposes the necessary settings for accounts of devices:
In fact, it sets the parameters equivalent to the screenshot. But one thing is to put down for a couple of devices, and quite another when you have more than twenty of them. Also, the script resets the password for the device account, which is necessary after enabling reversible encryption.

NPS policy settings:
Windows Registry Editor Version 5.00 [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\RasMan\PPP\EAP\4] "RolesSupported"=dword:0000000a "FriendlyName"="MD5-Challenge" "Path"=hex(2):25,00,53,00,79,00,73,00,74,00,65,00,6d,00,52,00,6f,00,6f,00,74,\ 00,25,00,5c,00,53,00,79,00,73,00,74,00,65,00,6d,00,33,00,32,00,5c,00,52,00,\ 61,00,73,00,63,00,68,00,61,00,70,00,2e,00,64,00,6c,00,6c,00,00,00 "InvokeUsernameDialog"=dword:00000001 "InvokePasswordDialog"=dword:00000001 After making changes to the registry, you must restart the NPS service.
Stop-Service IAS Start-Service IAS The script that exposes the necessary settings for accounts of devices:
$devices=Get-ADUser -SearchBase "ou=802.1x-groups,ou=devices_groups,dc=company,dc=local" -Filter * foreach ($device in $devices) { set-aduser -Identity $device.name -UserPrincipalName ($device.name+"@company.local") -PasswordNeverExpires $true -AllowReversiblePasswordEncryption $true -CannotChangePassword $true Set-ADAccountPassword -Identity $device.name -NewPassword (ConvertTo-SecureString -AsPlainText $device.name -force) } In fact, it sets the parameters equivalent to the screenshot. But one thing is to put down for a couple of devices, and quite another when you have more than twenty of them. Also, the script resets the password for the device account, which is necessary after enabling reversible encryption.

NPS policy settings:
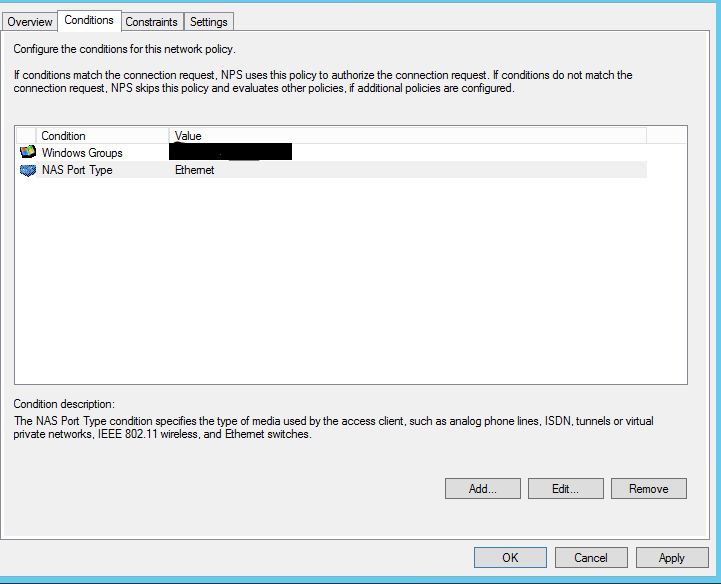
- Specify the group with the device and the type of port.
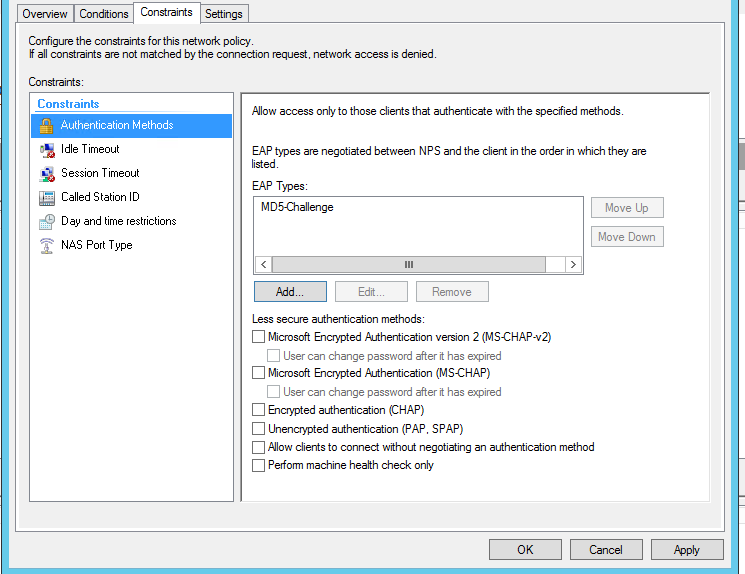
- After manipulating the registry, our coveted MD5-Challenge appears in the list of available protocols. His and choose.
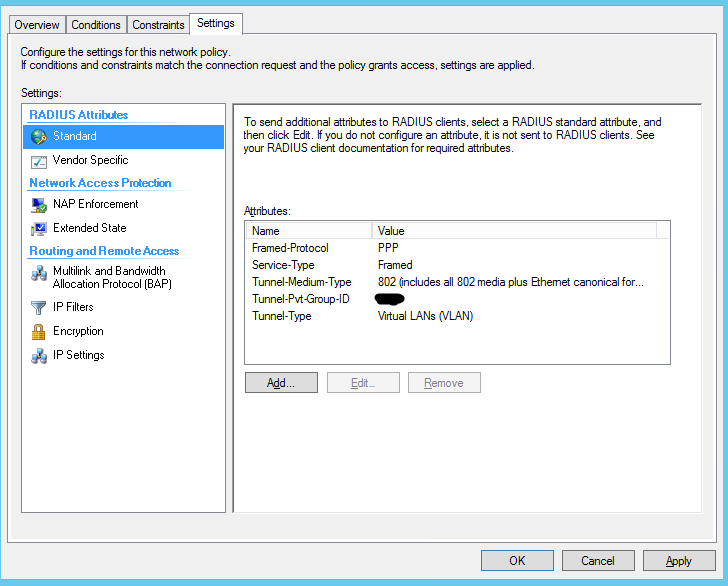
- The remaining settings are set based on the requirements of the logical implementation. No different from the standard RADIUS + 802.1x configuration.
Total:
- Network devices, such as TVs, Apple TV, printers are authenticated to 802.1x and group membership.
- Passwords are not transmitted in the clear, but somehow it is encrypted.
List of tips, guides and resources:
Juniper recommendations for software version on EX2200
Juniper EAP-PAP support for MAC RADIUS Authentication
UBNT community, which gave the last kick in the right direction
Source: https://habr.com/ru/post/437408/