The new attack of the Shade encoder is aimed at Russian business users.
In January 2019, we recorded a sharp increase in the number of detections of malicious JavaScript email attachments (in 2018, this attack vector was minimally used). In the "New Year's release" you can select a distribution in Russian, intended for the distribution of the Shade encoder (aka Troldesh), which is detected by ESET products as Win32 / Filecoder.Shade.
It seems that this attack continues the spam campaign to distribute the Shade encoder, discovered in October 2018 .

According to our telemetry, the October campaign was at a constant pace until the second half of December 2018. This was followed by a break at Christmas, and then in mid-January 2019, the campaign’s activity doubled (see chart below). Falls on the chart, corresponding to weekends, suggest that attackers prefer corporate email addresses.

Figure 1. Detection of malicious JavaScript attachments distributing Win32 / Filecoder.Shade since October 2018
As mentioned earlier, the campaign illustrates the trend that we have seen since the beginning of 2019, the return of malicious JavaScript attachments as an attack vector. The dynamics are displayed on the chart below.

Figure 2. Detection of malicious javascript distributed in email attachments since 2018. Attachments are detected by ESET as JS / Danger.ScriptAttachment
It is worth noting that the campaign for the dissemination of the Shade encoder is most active in Russia, accounting for 52% of the total number of malicious attachments detected by JavaScript. Other victims include Ukraine, France, Germany, and Japan, as shown below.

Figure 3. The number of malicious JavaScript attachments detected distributing Win32 / Filecoder.Shade. Data from January 1 to January 24, 2019
According to our analysis, a typical attack of the January campaign begins with the victim receiving a letter in Russian with a ZIP file info.zip or inf.zip as an attachment.
Letters are disguised as official requests of legitimate Russian companies. We saw the newsletter on behalf of Binbank (merged with Otkritie Bank since 2019) and the Magnit retail chain. The text in the image below.

Figure 4. Sample spam mailing used in the January campaign
The ZIP file contains a JavaScript file called “Info.js”. After extracting and running the file, it downloads a malicious loader detected by ESET products as Win32 / Injector. The loader decrypts and launches the final payload - the Shade encoder.
The malicious loader is downloaded from the URL of compromised legitimate WordPress sites, where it disguises itself as an image. To compromise WordPress pages, attackers use a massive, automated brute force attack using bots. Our telemetry captures hundreds of URLs that host the malicious loader, all addresses end with the ssj.jpg line.
The loader is signed with an invalid digital signature, which is allegedly issued by Comodo. The Signer information field value and time stamp are unique for each sample.

Figure 5. Counterfeit digital signature used by the malicious loader
In addition, the bootloader is trying to disguise itself, posing as a legitimate system process Client Server Runtime Process (csrss.exe). It copies itself to C: \ ProgramData \ Windows \ csrss.ex, where Windows is a hidden folder created by the bootloader; usually in ProgramData this folder is not.
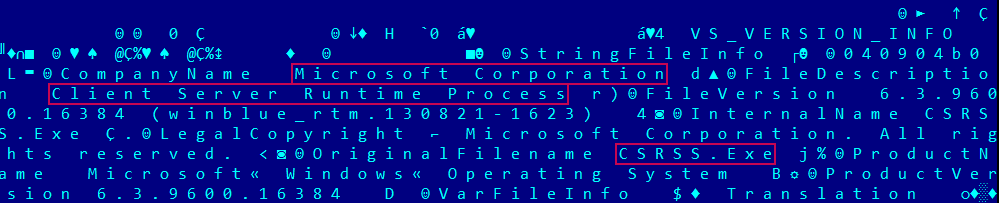
Figure 6. Malicious software that is a system process and uses version information copied from a legitimate Windows Server 2012 R2 binary file
The final payload is the Shade (Troldesh) encoder. It was first discovered in the wild at the end of 2014, and has since been repeatedly updated. Shade encrypts a wide range of files on local drives. In the new campaign, he adds the extension .crypted000007 to the encrypted files.
The victim receives payment instructions in Russian and English in the TXT file stored on the infected computer. The text is the same as in the last campaign in October 2018.
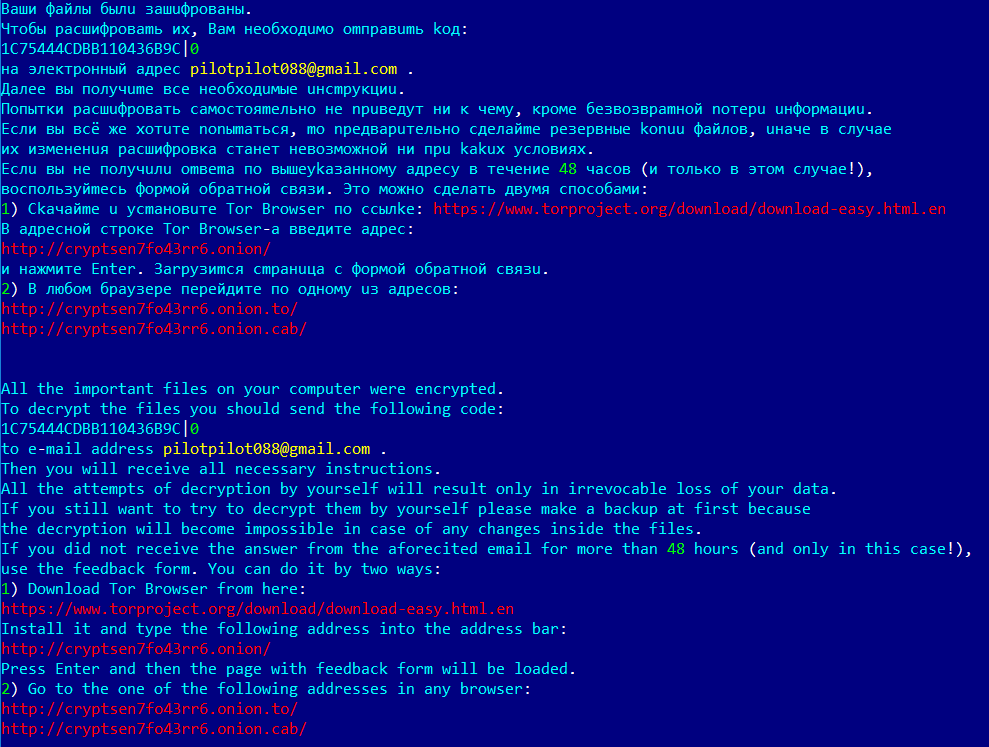
Figure 7. Shade buyout requirements, January 2019
Examples of hashes of malicious ZIP attachments
ESET Detection: JS / Danger.ScriptAttachment
Examples of JavaScript hash loaders
ESET Detection: Win32 / Injector
Examples of Shade encoder hashes
ESET Detection: Win32 / Filecoder.Shade
Character string in URLs where Shade is coded
It seems that this attack continues the spam campaign to distribute the Shade encoder, discovered in October 2018 .

New Campaign Shade
According to our telemetry, the October campaign was at a constant pace until the second half of December 2018. This was followed by a break at Christmas, and then in mid-January 2019, the campaign’s activity doubled (see chart below). Falls on the chart, corresponding to weekends, suggest that attackers prefer corporate email addresses.

Figure 1. Detection of malicious JavaScript attachments distributing Win32 / Filecoder.Shade since October 2018
As mentioned earlier, the campaign illustrates the trend that we have seen since the beginning of 2019, the return of malicious JavaScript attachments as an attack vector. The dynamics are displayed on the chart below.

Figure 2. Detection of malicious javascript distributed in email attachments since 2018. Attachments are detected by ESET as JS / Danger.ScriptAttachment
It is worth noting that the campaign for the dissemination of the Shade encoder is most active in Russia, accounting for 52% of the total number of malicious attachments detected by JavaScript. Other victims include Ukraine, France, Germany, and Japan, as shown below.

Figure 3. The number of malicious JavaScript attachments detected distributing Win32 / Filecoder.Shade. Data from January 1 to January 24, 2019
According to our analysis, a typical attack of the January campaign begins with the victim receiving a letter in Russian with a ZIP file info.zip or inf.zip as an attachment.
Letters are disguised as official requests of legitimate Russian companies. We saw the newsletter on behalf of Binbank (merged with Otkritie Bank since 2019) and the Magnit retail chain. The text in the image below.

Figure 4. Sample spam mailing used in the January campaign
The ZIP file contains a JavaScript file called “Info.js”. After extracting and running the file, it downloads a malicious loader detected by ESET products as Win32 / Injector. The loader decrypts and launches the final payload - the Shade encoder.
The malicious loader is downloaded from the URL of compromised legitimate WordPress sites, where it disguises itself as an image. To compromise WordPress pages, attackers use a massive, automated brute force attack using bots. Our telemetry captures hundreds of URLs that host the malicious loader, all addresses end with the ssj.jpg line.
The loader is signed with an invalid digital signature, which is allegedly issued by Comodo. The Signer information field value and time stamp are unique for each sample.

Figure 5. Counterfeit digital signature used by the malicious loader
In addition, the bootloader is trying to disguise itself, posing as a legitimate system process Client Server Runtime Process (csrss.exe). It copies itself to C: \ ProgramData \ Windows \ csrss.ex, where Windows is a hidden folder created by the bootloader; usually in ProgramData this folder is not.

Figure 6. Malicious software that is a system process and uses version information copied from a legitimate Windows Server 2012 R2 binary file
Shade Encoder
The final payload is the Shade (Troldesh) encoder. It was first discovered in the wild at the end of 2014, and has since been repeatedly updated. Shade encrypts a wide range of files on local drives. In the new campaign, he adds the extension .crypted000007 to the encrypted files.
The victim receives payment instructions in Russian and English in the TXT file stored on the infected computer. The text is the same as in the last campaign in October 2018.

Figure 7. Shade buyout requirements, January 2019
Indicators of compromise
Examples of hashes of malicious ZIP attachments
0A76B1761EFB5AE9B70AF7850EFB77C740C26F82
D072C6C25FEDB2DDF5582FA705255834D9BC9955
80FDB89B5293C4426AD4D6C32CDC7E5AE32E969A
5DD83A36DDA8C12AE77F8F65A1BEA804A1DF8E8B
6EA6A1F6CA1B0573C139239C41B8820AED24F6AC
43FD3999FB78C1C3ED9DE4BD41BCF206B74D2C76ESET Detection: JS / Danger.ScriptAttachment
Examples of JavaScript hash loaders
37A70B19934A71DC3E44201A451C89E8FF485009
08C8649E0B7ED2F393A3A9E3ECED89581E0F9C9E
E6A7DAF3B1348AB376A6840FF12F36A137D74202
1F1D2EEC68BBEC77AFAE4631419E900C30E09C2F
CC4BD14B5C6085CFF623A6244E0CAEE2F0EBAF8CESET Detection: Win32 / Injector
Examples of Shade encoder hashes
FEB458152108F81B3525B9AED2F6EB0F22AF0866
7AB40CD49B54427C607327FFF7AD879F926F685F
441CFA1600E771AA8A78482963EBF278C297F81A
9023B108989B61223C9DC23A8FB1EF7CD82EA66B
D8418DF846E93DA657312ACD64A671887E8D0FA7ESET Detection: Win32 / Filecoder.Shade
Character string in URLs where Shade is coded
hxxp://[redacted]/ssj.jpgSource: https://habr.com/ru/post/437982/