Analysis of the available data of the January attack, in which virtual threats had to really respond

In past years, centralized attacks were carried out using IP telephony, now a new round, but using email. Let us analyze the available electronic data on this attack.
Updated information on 02/01/2019.

Problem:
2017: “The anonymity of the call is ensured by the fact that an attacker, using IP-telephony, can substitute any number of the caller, including the numbers of real uncomplicated subscribers from anywhere in the world. This IP telephony feature makes it difficult for security officials to work. Connecting the voice gateway of IP-telephony to the networks of telecom operators often happens illegally, with the substitution of the caller's number, IP-addresses and other identifiers ”
2019: According to the press services of the administrations and from the staff of medical institutions and schools in different regions and cities, they received emails with threats and demands to perform certain actions.
Law enforcement agencies together with the executive authorities began to act in accordance with their powers, which meant checking each message.
Institutions that were listed in the text of the letters, began to hold emergency events.
None of the facts on the received threats were confirmed, the work of the institutions was resumed in full.
Initial data:
Let's try to abstract from the situation as a whole and go through the points from some published in the public domain emails, photos of which are presented below.

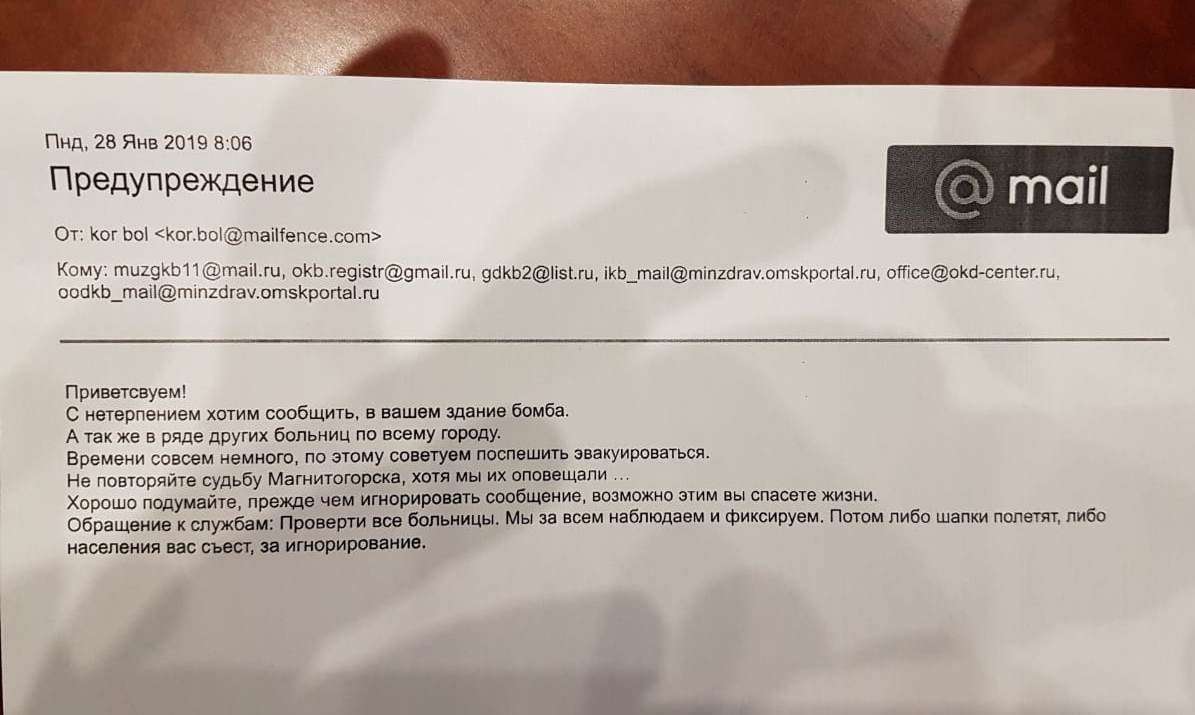

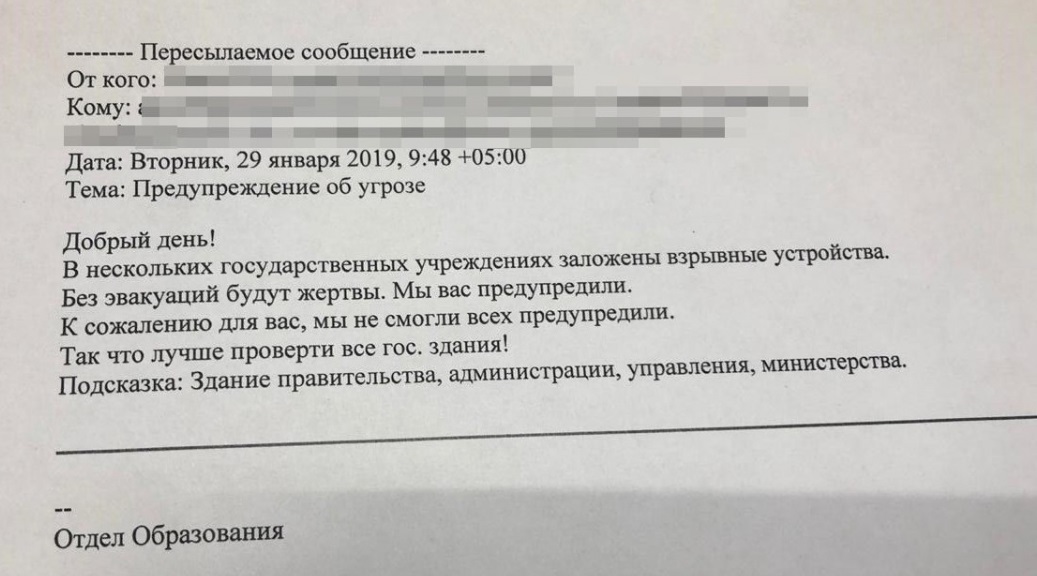


Data on the information on the "official headers" in the letters there.






Data on the information on the "official headers" in the letters there.
Data analysis:
All emails were sent using the free mailfence mail com service, which positions itself as a “secure and confidential email service.”
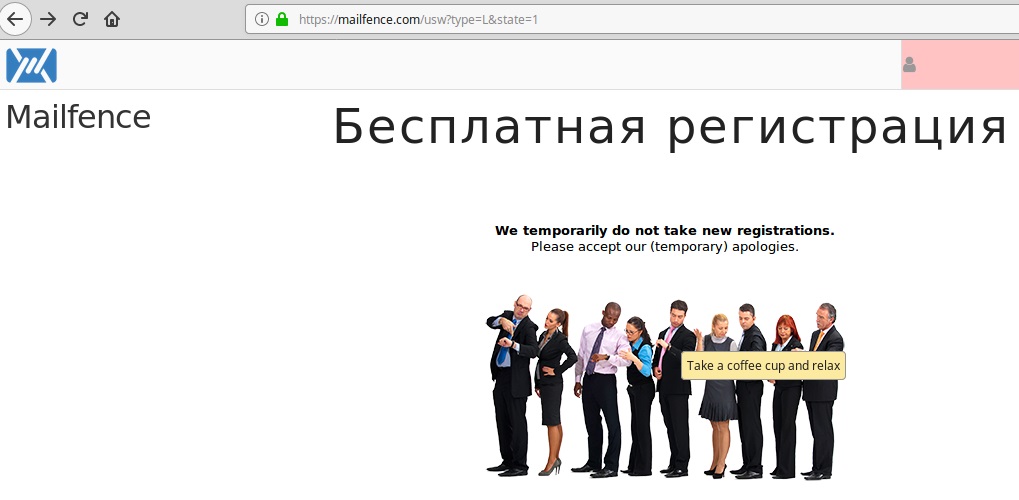
At the moment, some providers in the Russian Federation have restricted access to this service.
We will try to enter this service and register. We get the following failure:
Using the VPN plugin, you can go a little further and register:
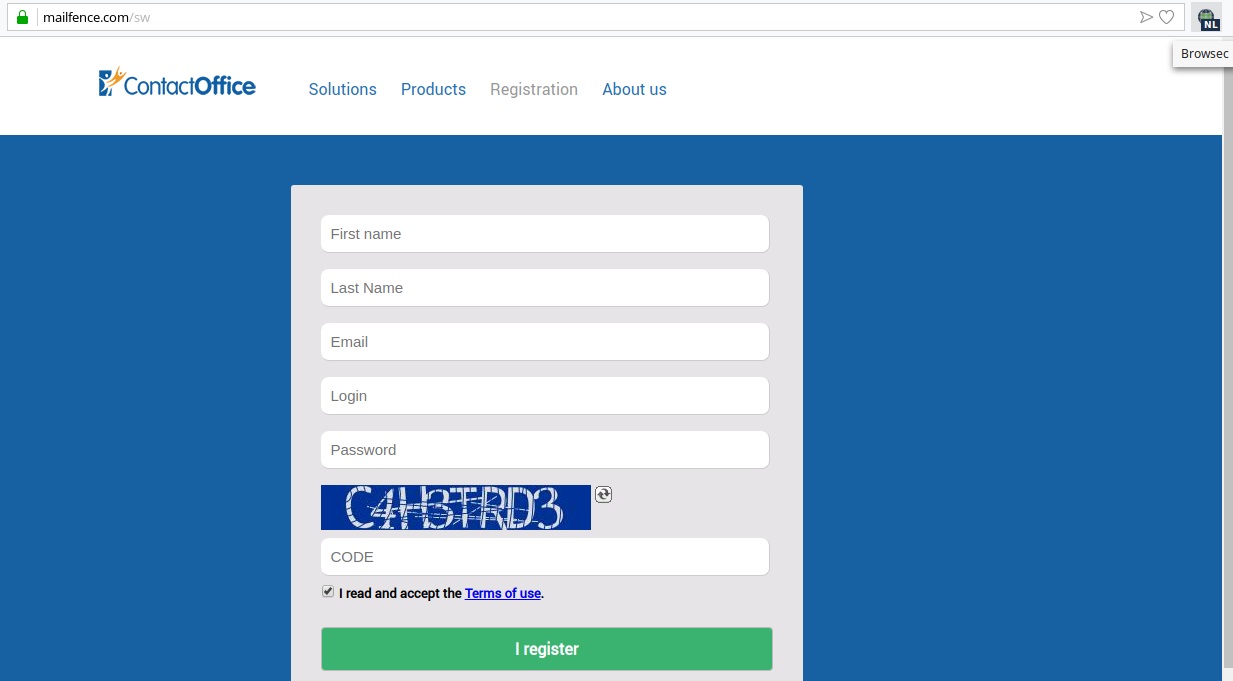
However, here we have this choice of possible email addresses.

Thus, there is a suspicion that the email addresses that were used in the attack were created quite a long time ago on this system, when there was such an opportunity to choose another domain name earlier. This means that the attack was not spontaneous, and the addresses were created earlier by some pool.
And why do we need to create a mailbox in this service?
When registering, you must specify your working email address, which will send a link to confirm registration with the service.
Next, we check how the password reset process takes place in this service .
Enter your username and / or your e-mail address:
Enter after the username or email (in the test case we have mail.ru) and we get:
To reset your password, an e-mail was sent to:
sin***@***mail.ru
Thus, we can find out the first three characters of the user name and the last 5 characters of the second-level mail domain. (thanks michaelkl for the comment! )
Moreover, when requesting a password reset, you can specify a username or email.
And according to the addresses from the sent e-mails, when requesting a password reset, you can specify only e-mail.

putin.fsb2@mailfence.com
To reset your password, an e-mail was sent to:
kul***@***utoo.email
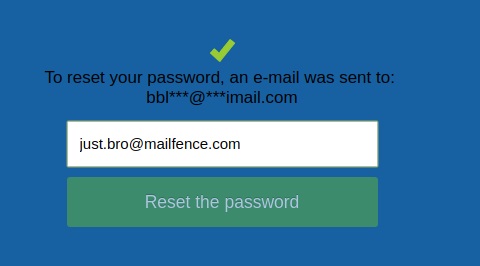
just.bro@mailfence.com
To reset your password, an e-mail was sent to:
bbl***@***imail.com
A single thread leads to gmail.com:

kor.bol@mailfence.com
to reset your password, an e-mail was sent to:
vov***@***gmail.com
Here you can search for the full address, but for a long time:
This address, by the way, is out of the entire list by the fact that it has a connection with gmail.com.
Another address is there:
kiano.lok@mailfence.com
To reset your password, an e-mail was sent to:
put***@***gmail.com
There is a suspicion that this is an imitator, as an option, which also contributed to the wave of mailings, but with mercenary goals in order to commit its malicious intent in place of events (theft, data deletion, when no one is near, etc.).
Further, if somewhere in the address there are numbers, then by slightly changing or removing them, we can also check these addresses:
putin.fsb@mailfence.com
To reset your password, an e-mail was sent to:
poc***@***cloud.info
putin.fsb1@mailfence.com
o reset your password, an e-mail was sent to:
joo***@***email.com
putin.fsb3@mailfence.com
To reset your password, an e-mail was sent to:
bud***@***email.com
putin.fsb4@mailfence.com
To reset your password, an e-mail was sent to:
bep***@***itnow.com
Thus, you can still expect to receive letters from these email addresses.
And here, nevertheless, for the registration in the mailfence dot com, the service temp-mail dot org was used,

As a result, two different mail services were used in eight email addresses.
Addition: new letters also come from the free mail mail dot bg mail server.
jekson.lo1@mailfence.com
o reset your password, an e-mail was sent to:
pet***@***mail.bg
Data from MosIgra:
habr.com/ru/company/mosigra/blog/439036
laki.kak@mailfence.com
To reset your password, an e-mail was sent to:
ale***@***mail.uk
How the victims were chosen for the attack, judging by the mailing lists, it is clear that the addresses were copied from the websites of state institutions or “driven in” manually, because these data are publicly available.
The range of simultaneous recipients in the letters (2-6-10) is small, so that the mail servers do not restrict the distribution and the letters do not fall into the "Spam" folder.
Excerpts from the service headers:
Received: from wilbur.contactoffice.com (wilbur.contactoffice.com [212.3.242.68])
(Client certificate not present)
Return-Path: putin.fsb3@mailfence.com
domain of mailfence.com designates 212.3.242.68 as permitted sender,
rule = [ip4: 212.3.242.64/26]) smtp.mail=putin.fsb3@mailfence.com; dkim = pass
DKIM-Signature: v = 1; a = rsa-sha256; c = relaxed / simple; d = mailfence.com;
X-Priority: 3
Reply-To: Putin FSB <putin.fsb3@mailfence.com>
From: Putin FSB <putin.fsb3@mailfence.com>
X-Mailer: ContactOffice Mail
X-ContactOffice-Account: com: 188677102
Received: from mxfront13g.mail.yandex.net ([127.0.0.1])
by mxfront13g.mail.yandex.net with LMTP id a6sJli0I
for <info@mosigra.ru>; Tue, Feb 5 2019 11:00:14 +0300
Received: from wilbur.contactoffice.com (wilbur.contactoffice.com [212.3.242.68])
by mxfront13g.mail.yandex.net (nwsmtp / Yandex) with ESMTPS id jttuF4mQRo-0DAa1MBL;
Tue 05 Feb 2019 11:00:13 +0300
(using TLSv1.2 with cipher ECDHE-RSA-AES128-GCM-SHA256 (128/128 bits))
(Client certificate not present)
Return-Path: laki.kak@mailfence.com
X-Yandex-Front: mxfront13g.mail.yandex.net
X-Yandex-TimeMark: 1549353613
Authentication-Results: mxfront13g.mail.yandex.net; spf = pass (mxfront13g.mail.yandex.net: domain authorized Sender, rule = [ip4: 212.3.242.64/26]) smtp.mail=laki.kak@mailfence.com; dkim = pass header.i=@mailfence.com
X-Yandex-Spam: 2
X-Yandex-Fwd: MzM4MDAwNDcyNDYzOTM2Mzg1OSwyMTg3Njc1NDQ5ODIwMzIwNzMz
Received: from ichabod.co-bxl (ichabod.co-bxl [10.2.0.36])
by wilbur.contactoffice.com (Postfix) with ESMTP id 16350329D;
Tue Feb 5, 2019 09:00:13 +0100 (CET)
DKIM-Signature: v = 1; a = rsa-sha256; c = relaxed / simple; d = mailfence.com;
s = 20160819-nLV10XS2; t = 1549353613;
bh = gADFkQslj8dDCkx + Y9OhJNmeT7fosViIkpUDPPk1UO8 =;
h = Date: To: Subject: Reply-To: From: From;
b = Th6eWs74xYE35Y5pouZD / 9vbA / oJZ6jyrtzWrMs3XilthYjL3DnwVm1SiysHGHr4J
6ROHYI / HMAnLOJfv + JsKC574UzsmjU1yhikwYLakMPTWKiqcR6knC4mXkfWFm / fXHU
LPod1MeMeNlD1rqEXnkr8wJk4GX / s6DzCUVxC5qzcv6ChEwa5DJOvIg0mxMxP9UfMr
LaPBQIGOiELGYfFOWi8XwGW1BDFfKXCgE0vxYYo8lqgXuXN720BHTv + CksccUdo44v
KyDZEQYqM7J3JhjL8GCiaWxfLBbEkLqYCHnRUEGyKbC2pqT23c2TaafXXW7g5raN63
WyVocjjQbTDpA ==
Date: Tue, Feb 5 2019 09:00:10 +0100 (CET)
Message-ID: <790975597.619629.1549353610731@ichabod.co-bxl>
MIME-Version: 1.0
Content-Type: text / plain; charset = utf-8
Content-Transfer-Encoding: base64
To: info@torrogrill.ru, kapitoly_adm@cosmik.ru, kashirskaya.enkatc@enka.com,
6112158@re-reserved.ru, info@mosigra.ru, info@toy.ru,
filion@minisolife.ru, 6412027@re-reserved.ru, info@modi.ru,
office@melonfashion.ru
Subject: =? Utf-8? B? 0L7RgtCy0LXRgiDQvdCwINC30LDQv9GA0L7RgQ ==? =
X-Priority: 3
Reply-To: laki kak <laki.kak@mailfence.com>
From: laki kak <laki.kak@mailfence.com>
X-Mailer: ContactOffice Mail
X-ContactOffice-Account: com: 190697286
X-Yandex-Forward: c4503a689c840ee5c1704413e6045827
(Client certificate not present)
Return-Path: putin.fsb3@mailfence.com
domain of mailfence.com designates 212.3.242.68 as permitted sender,
rule = [ip4: 212.3.242.64/26]) smtp.mail=putin.fsb3@mailfence.com; dkim = pass
DKIM-Signature: v = 1; a = rsa-sha256; c = relaxed / simple; d = mailfence.com;
X-Priority: 3
Reply-To: Putin FSB <putin.fsb3@mailfence.com>
From: Putin FSB <putin.fsb3@mailfence.com>
X-Mailer: ContactOffice Mail
X-ContactOffice-Account: com: 188677102
Received: from mxfront13g.mail.yandex.net ([127.0.0.1])
by mxfront13g.mail.yandex.net with LMTP id a6sJli0I
for <info@mosigra.ru>; Tue, Feb 5 2019 11:00:14 +0300
Received: from wilbur.contactoffice.com (wilbur.contactoffice.com [212.3.242.68])
by mxfront13g.mail.yandex.net (nwsmtp / Yandex) with ESMTPS id jttuF4mQRo-0DAa1MBL;
Tue 05 Feb 2019 11:00:13 +0300
(using TLSv1.2 with cipher ECDHE-RSA-AES128-GCM-SHA256 (128/128 bits))
(Client certificate not present)
Return-Path: laki.kak@mailfence.com
X-Yandex-Front: mxfront13g.mail.yandex.net
X-Yandex-TimeMark: 1549353613
Authentication-Results: mxfront13g.mail.yandex.net; spf = pass (mxfront13g.mail.yandex.net: domain authorized Sender, rule = [ip4: 212.3.242.64/26]) smtp.mail=laki.kak@mailfence.com; dkim = pass header.i=@mailfence.com
X-Yandex-Spam: 2
X-Yandex-Fwd: MzM4MDAwNDcyNDYzOTM2Mzg1OSwyMTg3Njc1NDQ5ODIwMzIwNzMz
Received: from ichabod.co-bxl (ichabod.co-bxl [10.2.0.36])
by wilbur.contactoffice.com (Postfix) with ESMTP id 16350329D;
Tue Feb 5, 2019 09:00:13 +0100 (CET)
DKIM-Signature: v = 1; a = rsa-sha256; c = relaxed / simple; d = mailfence.com;
s = 20160819-nLV10XS2; t = 1549353613;
bh = gADFkQslj8dDCkx + Y9OhJNmeT7fosViIkpUDPPk1UO8 =;
h = Date: To: Subject: Reply-To: From: From;
b = Th6eWs74xYE35Y5pouZD / 9vbA / oJZ6jyrtzWrMs3XilthYjL3DnwVm1SiysHGHr4J
6ROHYI / HMAnLOJfv + JsKC574UzsmjU1yhikwYLakMPTWKiqcR6knC4mXkfWFm / fXHU
LPod1MeMeNlD1rqEXnkr8wJk4GX / s6DzCUVxC5qzcv6ChEwa5DJOvIg0mxMxP9UfMr
LaPBQIGOiELGYfFOWi8XwGW1BDFfKXCgE0vxYYo8lqgXuXN720BHTv + CksccUdo44v
KyDZEQYqM7J3JhjL8GCiaWxfLBbEkLqYCHnRUEGyKbC2pqT23c2TaafXXW7g5raN63
WyVocjjQbTDpA ==
Date: Tue, Feb 5 2019 09:00:10 +0100 (CET)
Message-ID: <790975597.619629.1549353610731@ichabod.co-bxl>
MIME-Version: 1.0
Content-Type: text / plain; charset = utf-8
Content-Transfer-Encoding: base64
To: info@torrogrill.ru, kapitoly_adm@cosmik.ru, kashirskaya.enkatc@enka.com,
6112158@re-reserved.ru, info@mosigra.ru, info@toy.ru,
filion@minisolife.ru, 6412027@re-reserved.ru, info@modi.ru,
office@melonfashion.ru
Subject: =? Utf-8? B? 0L7RgtCy0LXRgiDQvdCwINC30LDQv9GA0L7RgQ ==? =
X-Priority: 3
Reply-To: laki kak <laki.kak@mailfence.com>
From: laki kak <laki.kak@mailfence.com>
X-Mailer: ContactOffice Mail
X-ContactOffice-Account: com: 190697286
X-Yandex-Forward: c4503a689c840ee5c1704413e6045827
Recommendations:
System administrators of institutions, if possible, check email more often, create a filter for emails from “mailfence dot com” in a separate folder and immediately report them, according to their job descriptions, save service headers and all data for further analysis.
Tactics:
Just the question - why so many email addresses are used in ezines?
The answer is simple - the Achilles' heel of the service used is the monetization of services and the possibility of registering through one-time mailboxes (one-time mail service).
1. So, most likely, all accounts used for mailing are now on a free plan, which includes only 500 MB emails.
If this box is “filled up” with messages with attachments and overfilled, then it will first have to be cleaned in order to make further distribution. Paid plans are already payment for services and additional opening of your bank data.
So, you can help with this by sending letters as large as possible to the addresses below.
putin.fsb@mailfence.com
putin.fsb1@mailfence.com
putin.fsb2@mailfence.com
putin.fsb3@mailfence.com
putin.fsb4@mailfence.com
just.bro@mailfence.com
kor.bol@mailfence.com
kiano.lok@mailfence.com
jekson.lo1@mailfence.com
laki.kak@mailfence.com
2. Interception of mailbox management by resetting the password and selecting a login through the one-time mail service .
Theoretically, it is possible to get access to the mailboxes listed in item 1, if it is possible to perform a large amount of actions:
- select the desired login and domain in the temp-mail org dot
- send a password reset command to the address mailfence dot com
- get an email about resetting your password in temp-mail org
- login to your mailbox account at dot com
Data for selection (where * is one or more characters (1-4 Latin letters most likely) in the user name):
Difficult situation:
password reset - putin.fsb1@mailfence.com
one-time mail service - joo*@321-email.com
one-time mail service - joo*@braun4email.com
one-time mail service - joo*@utooemail.com
password reset - putin.fsb3@mailfence.com
one-time mail service - bud*@321-email.com
one-time mail service - bud*@braun4email.com
one-time mail service - bud*@utooemail.com
There is only one domain to check:
password reset - putin.fsb2@mailfence.com
one-time mail service - kul*@utoo.email
password reset - putin.fsb4@mailfence.com
one-time mail service - bep*@4senditnow.com
password reset - just.bro@mailfence.com
one-time mail service - bbl*@heximail.com
3. Alternatively, by iterating (by pressing the “delete” button in the service) of the staffed suggested logins (4-8 characters long), find from the proposed new login that which starts with kul / bep / bbl / bud / joo .
Item 3 can be implemented using software methods.
If anyone is interested and can find access to at least one mailbox through a large brute force of data on the login in the one-time mail service and can (block) stop the mailing from it - it will be great.
We will not dwell on the linguistic and stylistic analysis of the content of the letters, although, coupled with spelling errors and some consonant syllables in the text, there is something to think about. However, it is possible that this dialectic was introduced into the text specifically for compromise.
This article is related to analytical topics, please follow the rules of the resource in the comments and not go beyond the generally accepted framework.
Source: https://habr.com/ru/post/438092/