[PixelKnot] 0day-vulnerability in the field of steganography

Prologue
Verbalization of the article will start with a statement from one domestic "cyberpunk", which demonstrated the "0day-vulnerability in Virtualbox".
“The reason is the disagreement with the current realities in information security, more precisely, in the direction of security research and bug bounty.I agree with the researcher.
It is considered normal to wait for a patch for vulnerabilities for six months, if only these bugs are no longer in public access.
In the area of bug bounty programs is considered normal:
- Wait more than a month until the vulnerability is verified and the decision to acquire it is announced.
- On the go, change the decision on whether the program will buy bugs for this software. Today you have learned that yes, they will buy, and in a week you come with bugs and exploits and get the answer that no, they will not.
- Do not have a clear list of applications for which the bugs will pay. Yes, it is convenient for bug bounty organizers, no, it is inconvenient for researchers.
- Not have clearly defined upper and lower price limits for vulnerabilities. There are a lot of factors affecting the price, but researchers need to see what it is worth wasting their time and what is not worth the day of work.
- Mania of greatness and marketing nonsense: give names to vulnerabilities and create websites for them; hold a thousand conferences a year; to exaggerate the importance of their work; consider yourself a "savior of the world." Go down to earth, Your Highness. "
................... MorteNoir
Subject of publication - steganography
Steganography is a way of transmitting or storing information, taking into account the fact that such a transmission is secret (Wikipedia) , in other words, steganography is hiding the presence / existence of the secret message itself without attracting too much attention.
At the end of last year, I discovered a vulnerability in the field of steganography: in the Android application “PixelKnoot”. The PixelKnoot app is the development of world saviors The Guardian Project is a popular company with a worldwide reputation in the field of paranoid mobile development . Orbot / Orweb / Orfox, etc. - the development of their hands business.
The guys from the "star team" Guardianproject described their application in the GP as
“★ INVISIBLE CHANGES: Even an experienced analyst should not be able to detect any message. Bytes image should appear undistorted. "
on of.sayte so
ATTACK RESISTANT: It is an automated tool for detecting and steganographic content in images.
This is not quite so - “marketing nonsense!”. I carried out a Stegoanalysis and found a way: to determine whether the presence of the secret message itself in the picture exists or not, encoded with PixelKnot. Time for data analysis: analysis of such picture albums, where the secret, and where it is not, goes to the "weak machine" ~ 1s / 1picture.
I contacted The Guardian Project technical support with my “thoughts” about the fact that everything is not so smooth from a technical point of view, as stated in their description of PixelKnot in GP and on of.sayte. And these guys, like politicians, love boredom: neither bug bounty programs, nor timely feedback. Received several "slow answers" asking not to disclose details of vulnerability to the public, and in the body of one of the letters such a wish from the "World's Saviors The Guardian Project " themselves: to publish the PixelKnot problem on Github-e. Hmm ... um ... these are the mental sounds.
Some controversial logic: “not to disclose a 0day vulnerability to the public, but to publish it on Github”. At the same time, “they” did not update PixelKnot for almost two years (PixelKnot v1.0.1 from 17/02/2017, the number of downloads from GP> 100k.) . Can you imagine what the gap is two years in the information security in the era of numbers? In the body of the letter there were links to open source and PD. (one of such conscientious ) . Of course, no one is going to contact you for a report or a “proposal to confirm a vulnerability / pay”. Maybe from one side it looks quite righteous, but what about the “problem”?
Like MorteNoir (if I understood his message correctly ...) , I don’t always like this policy, even though The Guardian projects are Open Source Projects. “It made me angry” not that the “Gods” were vulnerable, but the fact that they very reluctantly respond to letters ~ “rms” letter once a month.
$ Retreat
In the article I will touch upon the domestic office: Superjob. A commercial company that knows about a bug in its Android application since last fall and cannot fix it, shame IMHO).
He drew a parallel between the two companies, because in both cases a bug report (if they confirmed a vulnerability / bug) requested a ridiculous amount - $ 10. Superjob was stupid for a long time and didn’t understand where they had a problem there (although I correctly described the problem “in words” in the context of technical support letters), as soon as I suggested “filming a bug on a $ 10 video,” the company immediately gave back. Technical support immediately confirmed the problem on its side and said “thank you”, but of course I didn’t deserve any $. I do not want to pay a lot of attention to this superjob bug in this article, I’ll give answers to technical support letters
The bug has not been eliminated since last autumn in the next versions of the application ...
He drew a parallel between the two companies, because in both cases a bug report (if they confirmed a vulnerability / bug) requested a ridiculous amount - $ 10. Superjob was stupid for a long time and didn’t understand where they had a problem there (although I correctly described the problem “in words” in the context of technical support letters), as soon as I suggested “filming a bug on a $ 10 video,” the company immediately gave back. Technical support immediately confirmed the problem on its side and said “thank you”, but of course I didn’t deserve any $. I do not want to pay a lot of attention to this superjob bug in this article, I’ll give answers to technical support letters
“Hello, ne555!
Thank you for contacting Superjob.ru site support service.
Ne555, I see that the application was not updated according to my recommendation. Update it, please. Also send screenshots of the screen, how you look at the moment with the impossibility of scrolling and moving the column to add. intelligence. We will try to figure it out. "
“Hello, ne555!
Thank you for contacting Superjob.ru site support service.
ne555, thank you very much for the information! The question was passed to the developers, we will try to correct this nuance in the next versions of the application.
“Hello, ne555!
Thank you for contacting Superjob.ru site support service.
ne555, yes, we understand exactly where at the moment we have a flaw in the application and this question is still in the work of the developers. Expect to be fixed in the next versions. ”
The bug has not been eliminated since last autumn in the next versions of the application ...
For example, software for imitation - ON Veracrypt. Free software with open source, but recently the guys offered their bug bounty program (after finding a “serious error” in their code) , I don’t have questions of ethical morality (about revealing / not revealing details to the public) .
Initially and publicly, I slightly touched upon the PixelKnot steganography problem in one of my works: “Mobile Lab on Android for Penetration Testing”, of course, few people paid attention to the problem. Later I came up with, organized a contest and timed it to the problem in steganography: PixelKnot. Similarly, the metric shows low popularity, but this step more strongly aroused public interest in the problem in steganography. Now I publish the vulnerability of PixelKnot in the media on Habré, which is what the “speech” below will go about.
() day-vulnerability in PixelKnot
Using the Android application PixelKnot hid the secret message in the picture. The processed picture, like a picture, was about nothing - nothing has changed in it, and MAT / 2 did not reveal any aspects of the metadata of the processed photo.
Compared binary with the original - nothing "such", except for processing the format JPEG.
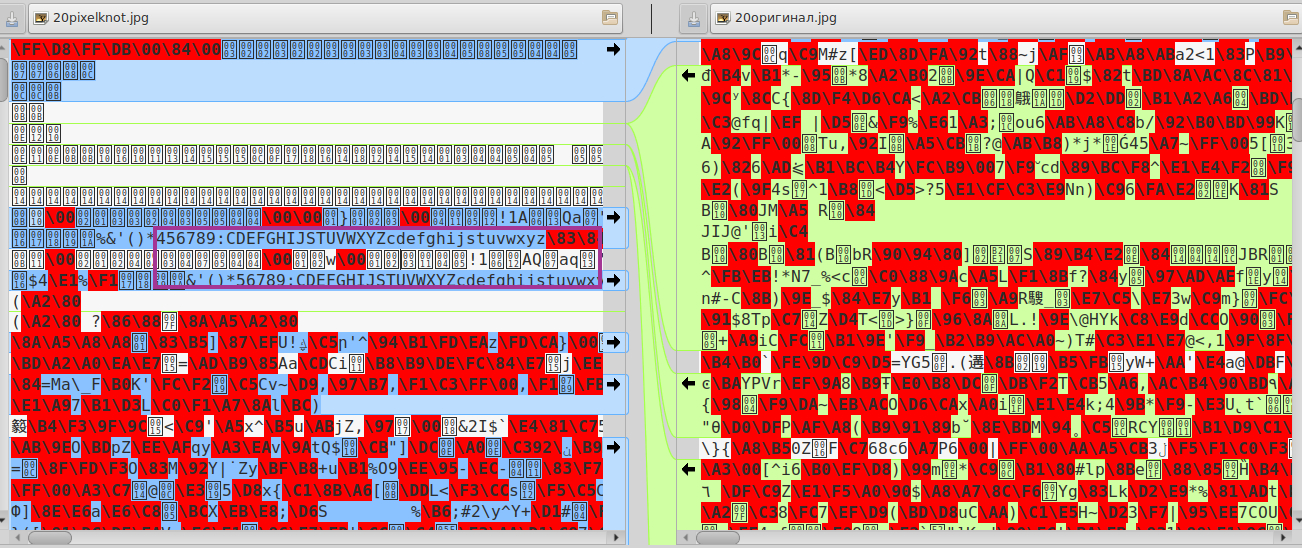
The dumped file on the PC, looked at different programs on GNU / Linux / Windows 7: GIMP / Photoshop and standard OS programs for viewing and editing images - nothing.
I missed the original photo through Steghide / Stegosuite steganography and compared all instances to binwalk (GNU / Linux) - there is a clue. The original image and the images processed in Steghide and Stegosuite were determined by the executable code, but the PixelKnot image was not (I checked a dozen more images processed in PixelKnot - none of them “passed” the binwalk, but this is not enough ...) .
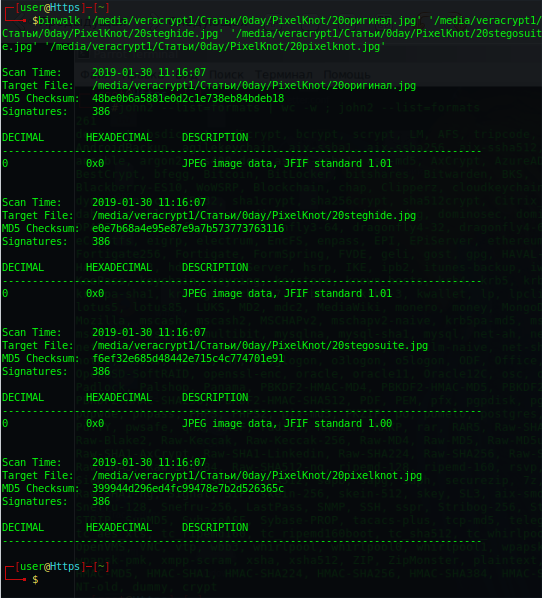
PixelKnot processed image - binwalk don't define.
I tried the bruthos attack Stegcracker - nothing (SC - brutes photos, processed only in Steghide)
Held bruthos attack Stegbreak - nothing (the tool is very ancient, brut, but does not understand the steganography of PixelKnot / Steghide / Stegosuite).
Engaged light infantry: a modified tool 15 years old - Stegdetect
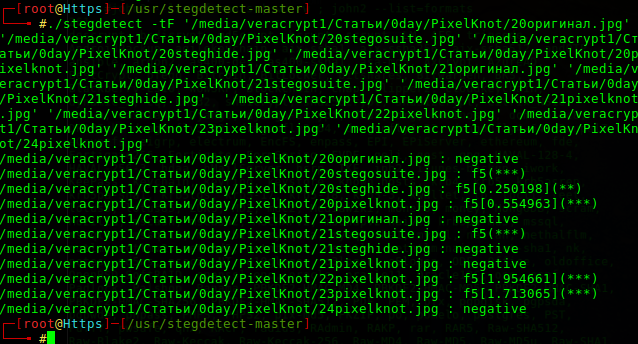
From the results of the analysis I see that out of 5 photos processed in PixelKnot, two photos successfully obfuscated the tool, and also one picture processed in Steghide slipped unnoticed.
Pull the coefficient. luminance and chrominance components of the image (since all the information about the image for the eye, including the secret, is contained either in coefficients or in components) . Empirically, something stands out: obvious artifacts in the "blue" in the picture PixelKnot , but this analysis of the photo manually, with automatic steanalysis, such as photo albums, so "famously" the necessary coefficient / cop. brightness and chromaticity to identify chaotic pixelate not pick up.
a fragment of the investigated photo, processed in PixelKnot.
Then I realized the completely random thing that came to mind: I renamed the file, discarding the image extension (.jpg / .png. PixelKnot.jpg> PixelKnot) . Opened an image file without an extension using KDE / Mate / Windows / Android with standard image viewers - nothing, but it didn’t open in Photoshop - an error! I think, here it is, found "Cibola"! But no, Photoshop is angry and does not open the photo without the extension (.jpg / ...) in ordinary photos.
He continued his steganalysis, opened the image without an extension in the GIMP, and received a similar error, as in Photoshop. But! GIMP, in contrast to Photoshop, opens ordinary pictures with a folded extension! That is, GIMP is “stuck” on images processed in PixelKnot (provided that the file processed in PixelKnot has an extension, or otherwise everything is fine / opens) .
He conducted a number of different and similar experiments / manipulations with “secret messages in pictures” in Stegosuite (GUI) and Steghide (CLI) . These "friends" did not disappoint. In a photo album, it was not always possible to calculate a picture with a secret message (not having the original) , that is, the problem of “revealing the fact of having a secret message in a picture” remained only with PixelKnot.
But how to carry out PixelKnot Steganalysis, if there are tens and hundreds of pictures with different extensions and so on (how to search for “the only one in a haystack”) ?
Swinging the found vulnerability: an effective way to stegoanalyze photos processed in PixelKnot on GNU / Linux.
1) Open Double Commander> group file renaming> select photo album> open file extension (.jpg / .png / ...) is an almost instant file operation.
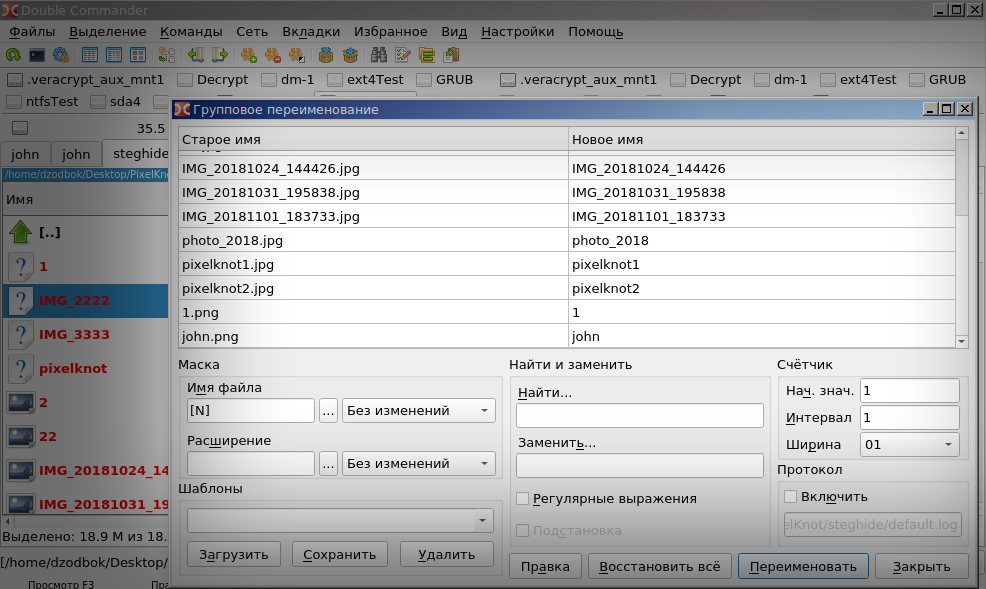
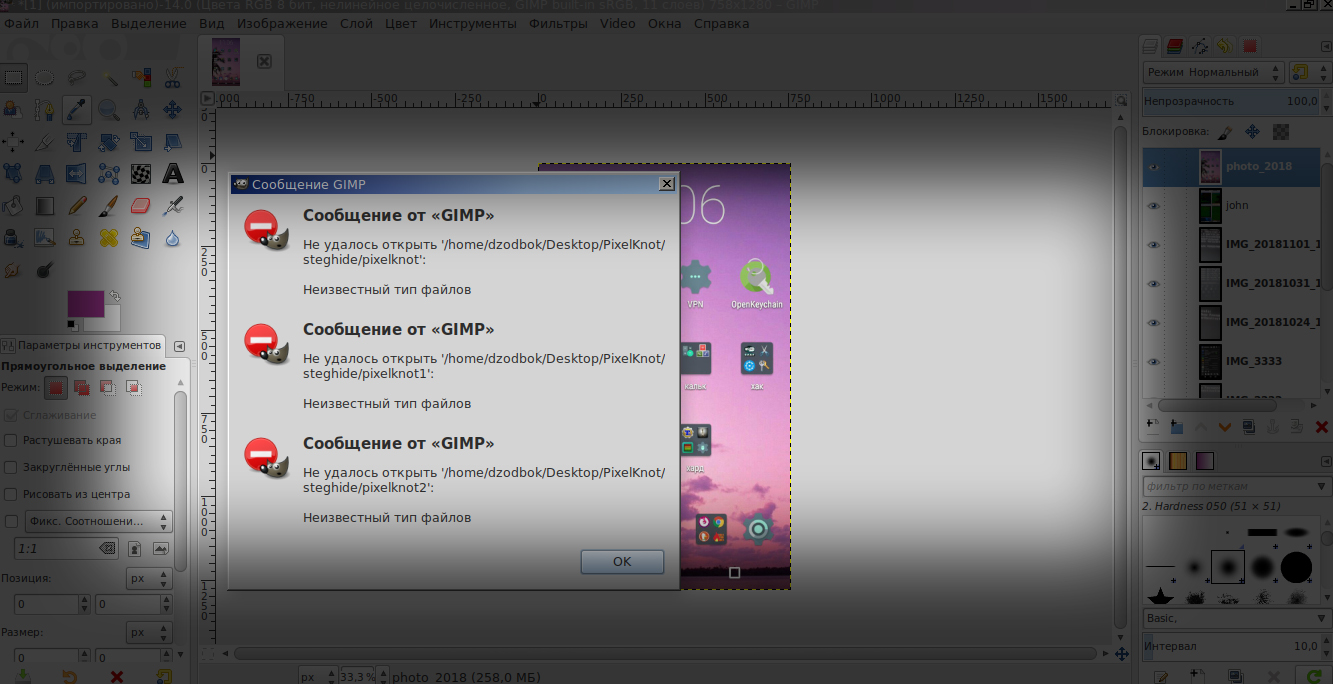
2) I open GIMP> file> open as layers> select any photo album with previously expanded photo extensions. I am waiting. If among the images you find the processed photos in PixelKnot, then the GIMP software will issue, upon completion of processing all the files, the names of all the photos that contain the presence of a secret message. On the analysis of such photos takes ~ 1s / 1 picture (this is the Intel 2x CPU of the last decade).
Epilogue
According to the F5 steganographic algorithm that uses The Guardian Project, PixelKnot hides a secret message in the body of the picture ( not in the name and not in the metadata ), for example, if the picture contains one word on a uniform background, this will not be enough to process the photo in PixelKnot. With a few words on a uniform background, PixelKnot photo processing will be successful, but it will also be visible to the naked eye.
Example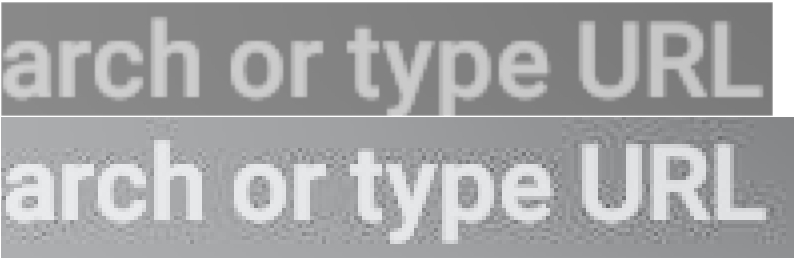

A system is considered hacked if the analyst succeeds in proving at least the presence of a hidden message (the task was completed successfully ).
I have no other technical claims to PixelKnot, on free Android firmware Resurrection Remix or LineageOS - PixelKnot software works without any failures, however, due to the demonstrated vulnerability, the PixelKnot application completely loses its meaning.
UPD, after a day.
Thursday turned out to be a crazy day for Habr: dozens of articles were published, a lot of minuses flew. Several publications were “poisoned”.
It's funny that IT made a whipping (trampled) on a good article that came out on the same day with the following distinctive title: <Definition of a “toxic personality” in IT>.
Another author showed a weakness: he deleted his article, later deleted his other work and deactivated his account on Habré (sawed out).
Toxic behavior continued until the evening. In the evening, an interesting thing happened to smooth out the consequences of the nihilism “someone” walked through all the articles (except minus ones) and added +3, but such voice manipulation was ineffective, and an hour later they served the second batch, only +2 put it to everyone. Little, the next day (in the morning), another +3 were distributed.
IMHO, do not want the "minuses" publish your articles on weekends, or publish on specialized resources.
Found in the open spaces of the network
The article will not be deleted by the author from the portal under any circumstances.
Source: https://habr.com/ru/post/438268/
