Safe Internet Day: what threats to pay attention to in 2019

February 5th was the World Day for Safe Internet . The holiday was created to promote the development of a more secure Web. A good reason to remember useful tools for work that will help not only information security specialists. First of all, you need to take care of the most vulnerable element of the security system - your end users.
We will talk about not quite typical problems and several undeservedly little-known applications that make the network as secure as possible. And we also focus on potential threats - it will be useful for system administrators to know in terms of advanced training.
Antidote measures
A source
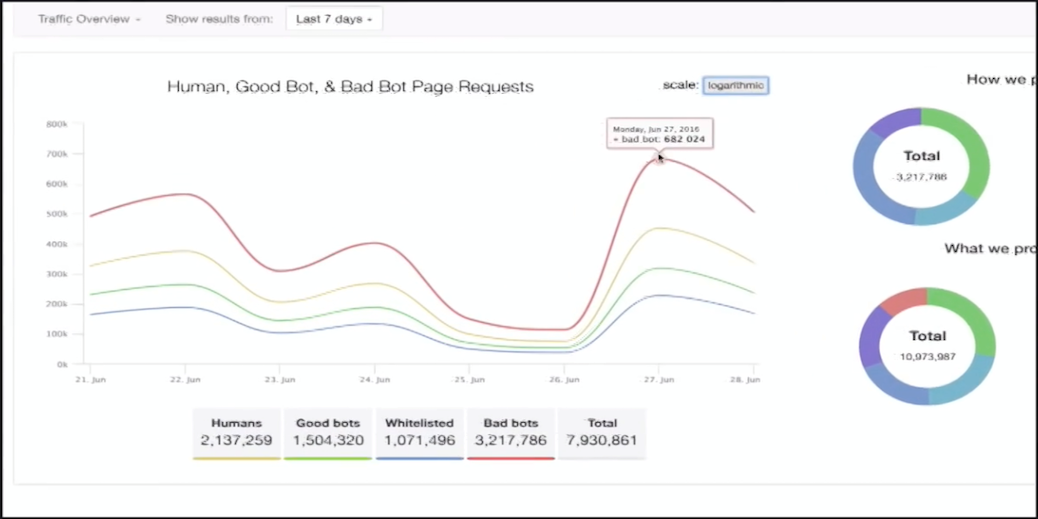
In 2018, 42.2% of all traffic on the network was generated by bots , and 21.8% were made up of markedly malicious bots. About 82.7% of malicious bot traffic originated from data centers. 74% of bots turned out to be “moderately complex or complex”, able to evade detection or at least attempt to do so.
In addition, at least twice a month attacks aimed at intercepting accounts are carried out against all sites on the Internet. By the way, in the same study it is indicated that the most active preventive measures against bots are used in Russia. There is no doubt that in 2019 attacks will increase both in quantitative terms and in complexity.
Distil Networks is an interesting platform for detecting bots and eliminating the consequences of their activities. It offers multiple tools to protect websites and APIs from web scraping (data extraction), data leakage, account hijacking, transaction fraud, unauthorized scanning of vulnerabilities, spam, digital advertising fraud and DoS attacks.
The company uses several technologies for analyzing user behavior: mouse movements and scrolling patterns in combination with longitudinal analysis data and individual identification - more than 40 parameters for each visitor.
If, as a result of the check, the visitor is identified as a bot, he will receive a corresponding mark and will be determined by the system, even if he disconnects the connection and tries to reconnect from random IP addresses or through anonymous proxies.
The tool lets you know how bots and botnets access your web pages, and reports on the success or failure of your anti-anti measures, such as CAPTCHA.
The company received the highest rating in an independent rating, which assessed the possibility of detecting attacks, responding to them, the interface, threat research, reporting and analysis, feedback and other parameters.
File sharing tools

A source
There are a huge number of file sharing applications in the world - Dropbox, SugarSync, Syncplicity, Box, Citrix ShareFile, Microsoft OneDrive, Google Drive, Egnyte, Oxygen Cloud, and so on. All these solutions help to work effectively with content, share files, synchronize all types of documents on all user devices, support the execution of document-oriented tasks and the needs of work processes of small and large businesses. However, not all solutions are secure.
The most significant case occurred in 2012, when hackers managed to seize the passwords of Dropbox employees. As a result, a file with users' email addresses was stolen - the company immediately recognized the leak, but hid its scale. Four years later, it turned out that the leak was more serious: they published a dump containing more than 68 million Dropbox user accounts: email addresses and hashed passwords.
Against this background, the demand for secure corporate collaboration applications has grown. Among the most secure SaaS solutions for sharing content and collaboration are Box, Huddle, ShareFile, Syncplicity and Intralinks VIA. However, you can only trust them to a certain extent - most often companies provide closed systems for external auditing, and it is impossible to judge the presence of vulnerabilities until the first news of a burglary appears.
In all presented systems, files are encrypted, and owners receive a flexible system for distributing access rights. In Intralinks VIA and some similar solutions, the administrator at any time can find out which users and which documents were viewed, as well as delete the files that were saved on external media and all their copies. This opportunity is worth paying attention to. Perhaps it is even more useful than access to unlimited storage for each account.
Single point of traffic analysis
A source
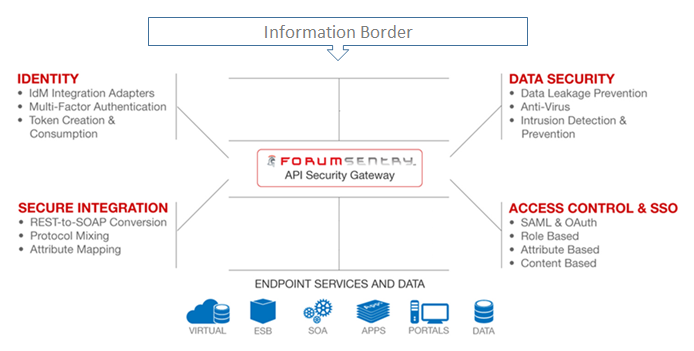
In modern enterprise systems, APIs that may not be sufficiently protected are the main channel for business transactions. The security of even simple API requests is endangered by use in various environments — with local, cloud or hybrid access. Access fragmentation becomes a problem for many APIs that work with sensitive data.
The best solution to this problem is to use the API gateway. In the usual form, any gateway, as a rule, is placed on the perimeter of the network and performs the functions of a firewall, streaming antivirus, antibot and IPS, preventing data leakage and ensuring control of employee access to corporate resources. Although it should be noted that API developers often put functionality and uptime above security.
The API gateway works like a server, which is the only entry point to the system. It provides an API adapted for each client, but it may have other responsibilities, such as authentication, monitoring, load balancing, caching, querying and managing them, as well as handling static responses.
A good example of using the API gateway was demonstrated in Netflix. At first, the company tried to provide a universal API for its streaming services. However, she quickly discovered that it was not working properly due to the variety of devices and their unique features. Today, Netflix uses an API gateway that provides an API interface adapted for each device.
A bad example is Panera Bread. In 2017, it turned out that due to an error in the API, the company was to blame for the leakage of 37 million customer records. The leaked data contained the names, dates of birth, postal addresses and the last four digits of the credit card numbers. It's funny that eight months after finding the error, the problem was not solved .
The Forum Sentry API Security Gateway (not to be confused with the Sentry Error Monitor) provides “no-code” APIs to integrate legacy and modern systems, connect cloud and mobile technologies, and securely distribute business applications and services across the organization.
Forum Sentry supports several authentication and authorization methods, including Basic Auth and OAuth 2.0, imports SOAP API and converts it to REST. In addition, thanks to the protection of APIs and the application of security policies in these connections, the service can also protect the underlying network.
Payment Protection
A source
In retail, there is a security standard for payment cards PCI DSS (Payment Card Industry Data Security Standard). It regulates the activities of organizations that work with credit cards of major payment systems, including Visa, MasterCard, American Express, Discover and JCB. PCI DSS consists of 12 core requirements that are broken down into more than 200 sub-requirements.
The standard has a whole section on how to develop software that works with PCI DSS. Moreover, all provisions of the standard are checked by an authorized auditor with QSA (Qualified Security Assessor) status. He has the right to talk with the employee of the payment gateway, study the settings of the system components, take screenshots and just see "how it works."
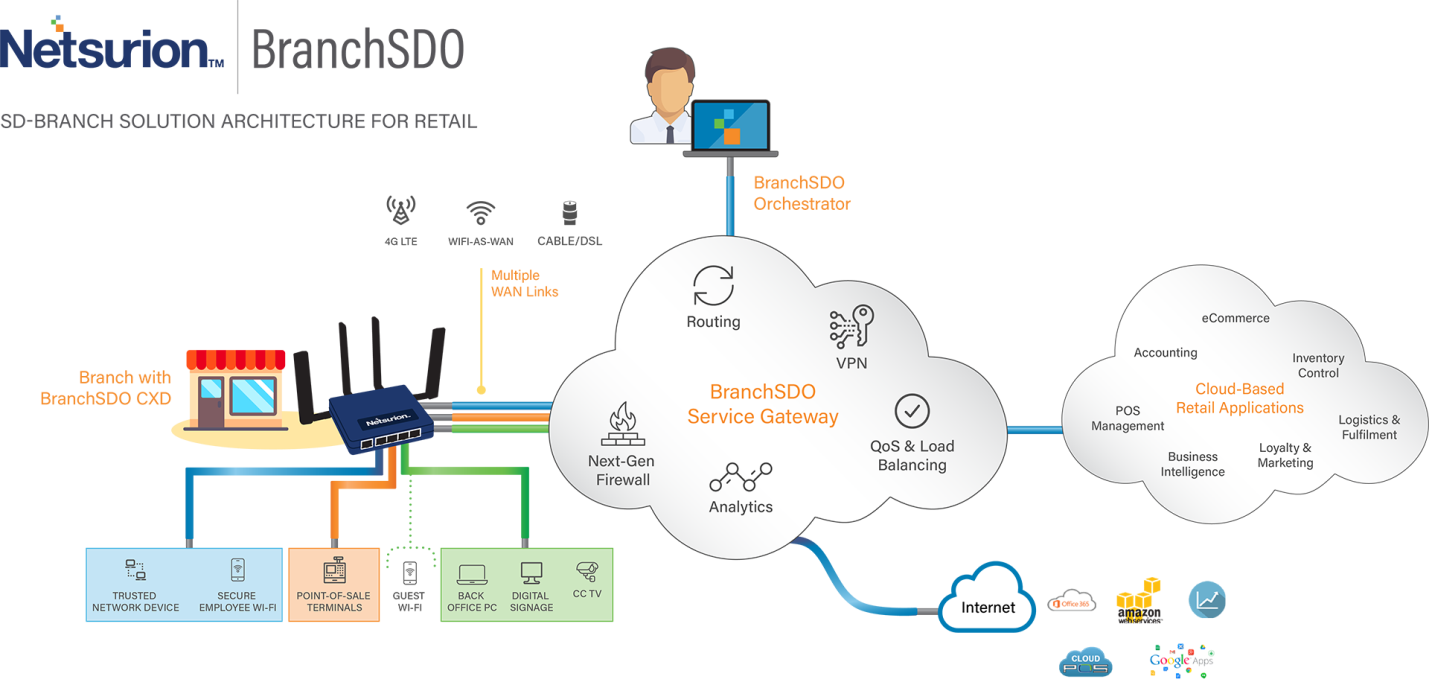
All these requirements are a serious problem for companies that need to process, store and transfer credit card information in a secure environment. If you have a network of hundreds of stores, then it is difficult to organize simultaneous monitoring of security at all points taking into account all the existing requirements. To accomplish this task, you can use the services of several services. Consider their work on the example of Netsurion Managed PCI.
Netsurion provides comprehensive security solutions for the central office and all branches of any distribution network. In this scheme outside the main office, outlets often do not have enough funds to deploy solutions of this level. Netsurion can be installed on a network of any size, from a huge franchise to an IP shop, without additional support costs.
Netsurion Managed PCI uses remote configuration for its cloud-controlled firewalls in each store, and alerts the administrator if any suspicious traffic occurs. What is important: the system can control the volume of all traffic on bank cards. The fall (as well as growth) of the volume often indicates a problem with the payment system.
The service can also detect and block unauthorized devices attempting to connect to the network. When a customer’s credit card information enters the network, Netsurion helps ensure that it is transferred only to authorized locations.
VPN

A source
A lot of things have been said about VPN, but we will stop at a little-known side.
As more and more employees “go to work” from coworking, libraries, cafes, subways, hotels and other dubious places :), a tool is needed for remote access, making it easy to connect from any environment.
Multiprotocol solutions to this problem are dizzying: L2TP / IPsec, OpenConnect, OpenSSH, OpenVPN, Shadowsocks, sslh, Stunnel, Tor bridge, WireGuard. Their main disadvantage is that these tools may not always be convenient for end users.
We came across a service that combines simplicity (as usual, fits into one button), scalability and security (with a certain degree of trust, since the code is closed). NCP engineering specializes in corporate VPN services and offers encrypted data transmission with additional biometric protection (for example, fingerprint or face recognition).
NCP detects exactly what prevents the employer from connecting to the VPN gateway. If the network environment blocks communication, for example, the firewall allows only HTTPS traffic, the NCP VPN client automatically uses HTTPS emulation mode outside the VPN tunnel. This allows the VPN client to establish an encrypted tunnel to the VPN gateway on the corporate network via the HTTPS port, while fulfilling all the requirements of the security policy.
NCP Secure Enterprise VPN Server supports multi-protocol tunneling, which makes it possible to choose a VPN technology depending on the obstacles the user’s environment network repairs. At the same time, the system allows servicing from 1 to 10 000 users simultaneously - it can be not only people, but also devices of the industrial Internet of things - for secure processing of all incoming traffic and monitoring the infrastructure.
As usual, welcome comments - add data on the subject of safe Internet. We talked mainly about the environment in which employees of small and medium-sized businesses work, but we will be happy if you share any of your favorite tools for ensuring corporate security.
Without SMS

The existing mobile infrastructure is outdated in terms of security. On Habré they wrote a lot about intercepting SMS , hacking mobile communications . Intercepting incoming SMS does not make any special problems - it can be done at a considerable distance from the victim, even if the user doesn’t release the phone.
The problem is that many use the phone number as the main “digital passport”. This video from the company Positive Technologies demonstrates how easy it is to crack a bitcoin wallet by intercepting sms.
Every network today is at risk of being hacked due to the ability to set an IMSI trap, improper hardware configuration, SS7 architectural flaws. All these obvious and potential vulnerabilities cannot be fixed today. Probably, telecom operators should perform regular network checks, properly set up equipment, monitor traffic continuously, but users have no way to monitor these actions.
SMS messages have never been designed for security. There are several specific steps you can take to stop using them. For example, put the Authy application for two-factor authentication. In addition, the application can create backup copies of the database, encrypt data and backup copies in the cloud, and synchronize on multiple devices.
So far it is difficult to completely abandon SMS when delivering secret codes for logging, password recovery and similar tasks, because this is a fairly simple and accessible "transport" for users. But increasingly there is a transition to push-notifications and offline code generators.
Source: https://habr.com/ru/post/439174/