ACS my LCD - security on two bolts
I hasten to warn readers: This article is written only for information, and in no case does not call for any unlawful action. The author is not responsible for any illegal actions committed by people using the information from this article.
Greetings reader. Today I want to talk about security access control systems (ACS) in general and the example of my LCD. The main vulnerabilities will be considered, and a successful attempt to copy keys will be made. All manipulations will be mostly hardware.
In my residential complex installed intercom system Sinthesi S2, as well as access system yard / porch / floor production of Urmet Group. That was how cool the street panel looked.

until one day it looked like this:
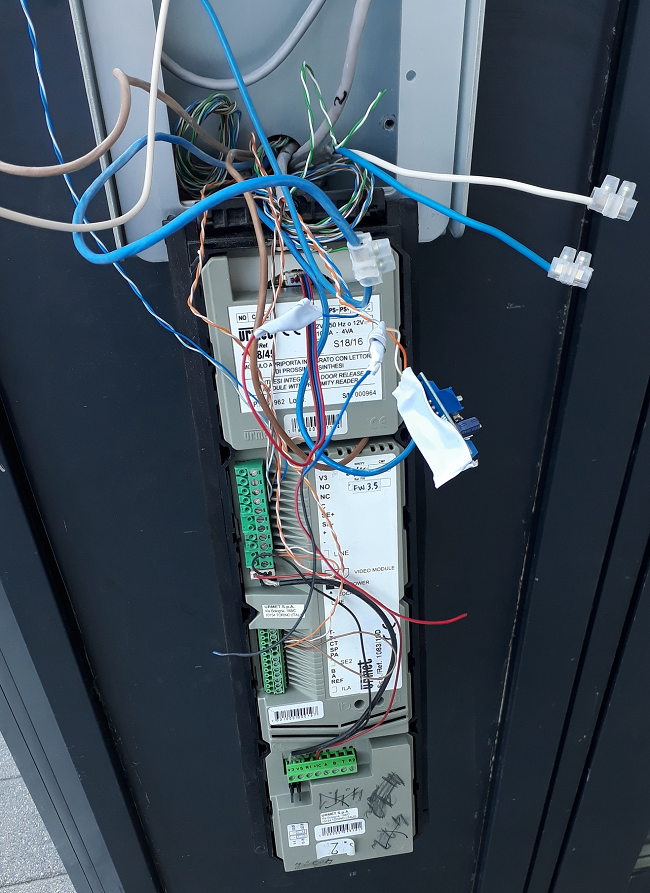
She hung for a couple of days, and then moved to a dumpster nearby. It contained only a reader and a keypad. Because one of the areas in my company is the development of HF readers, I could not resist and decided to study this RFID reader in more detail. From the documentation, I found only a huge catalog from which it was possible to conclude that this is FD-020-017 - 13.56 MHz reader with a Wiegand26 interface. Inside there was a sandwich from reader boards ( MFRC531 ) and MK with BLE ( CC2541 ) glued with hot glue to the case, which was clearly not designed for this board.

The MK board is flooded with a soft compound apparently to protect the radio part from moisture. Having twirled the fee, I put it off.
Until recently, I was not interested in the work of the system, since it was partially started (only access locks worked, but they had an access code, which I knew and did not use the key). After the system was fully started and the access codes were canceled, I began to study it in more detail. It began one of the nights when I returned home and found that the tambour door was already working and the wife was already sleeping. I had only pocket-sized items with me, but as it turned out this was quite enough to bypass all the elite security (as Urmet assures).

All I needed was to unscrew the 2 carving screws holding the panel frame with the car key, remove the 2 blocks and close the relay channel using the same key that goes to the lock of the vestibule door. Everything…
After this incident, when I watch another Hollywood film (“Passengers” (2016) at KDPV) and see how the super secret doors are opened by removing the code panel and sticking a pin into the board (always with sparks and a spectacular opening of the door), I see real situation.
In my memory, most of the access control systems I have seen have access to the lock directly from the code panel, and this is precisely the main vulnerability. All security is provided by several bolts holding this panel, and on faith that this system is reliable. But at the same time, it is possible to significantly increase the entry threshold (let's call it protection from a person with a screwdriver) by using locks with brains that are controlled by the interface - even the simplest. This measure will dramatically reduce the likelihood of spontaneous penetration.
ACS LCD as a whole, its work, the reaction to other keys, as well as a way to add keys:

First of all, I copied Block0 (the one that contains the UID and the Manufacturer information) to the Mifare Zero disc and checked that it was not enough - the key fob did not work. The reader did not even respond to the presentation of such a clone. It became clear that you need to look for the key from sectors 8 and 12. After reading all the available trinkets, I saw that only one of them locked 12 block, in the rest it is zero, therefore it is obvious that the magic is contained in block 8.
It's time to get a gift reader and consider it more closely. So we have FD-020-017 - 13.56 MHz, Wiegand26 interface. The MFRC531 and CC2541 are connected by a 10-pin comb. And he earned great money on the table - without the rest of the system. I reacted to the keys in the same way as the other readers. First, let's see what comes out:
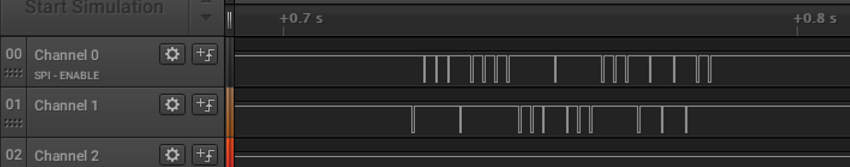
Silence until the presentation of a valid key fob. After reading the interface leaves the message in full accordance with Wiegand26 . So I decoded the package my key sends. Using a multimeter, I restored the pinout, it turned out that the chips communicate via SPI. We connect the analyzer,
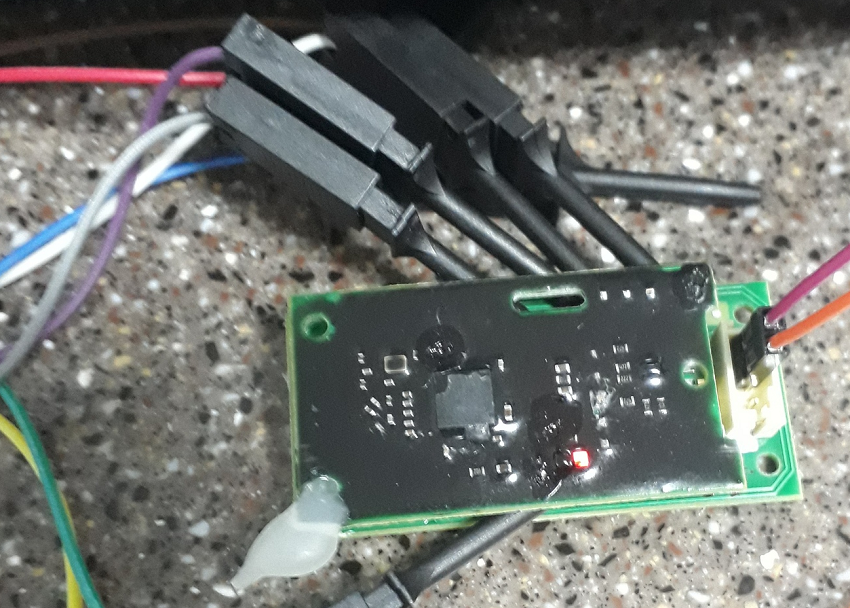
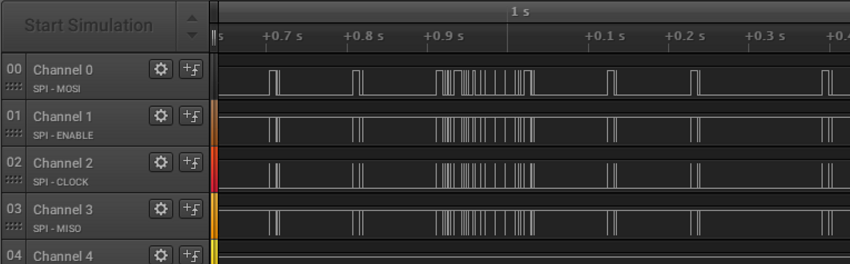
bring a valid key chain and watch the exchange on SPI:
Next, I began to look at the documentation on the MFRC531 microchip and almost gave up seeing that it has a special EEPROM for storing keys. I found the commands to load the key:

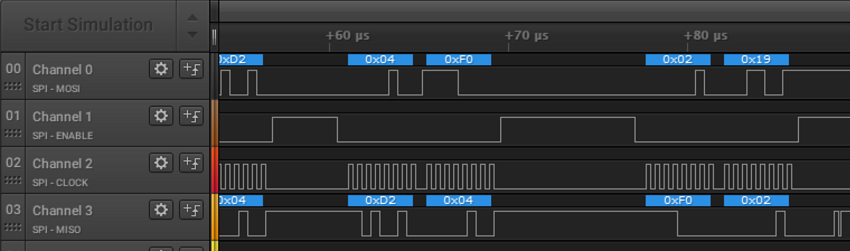
The command 0x0B loads from the EEPROM, the command 0x19 from the FIFO, which in turn receives the key via SPI. It would seem that if I load the key from the EEPROM, then I have no chance to reverse this way, but to my surprise, the 0x0B command is not exchanged, but there is a 0x19 command
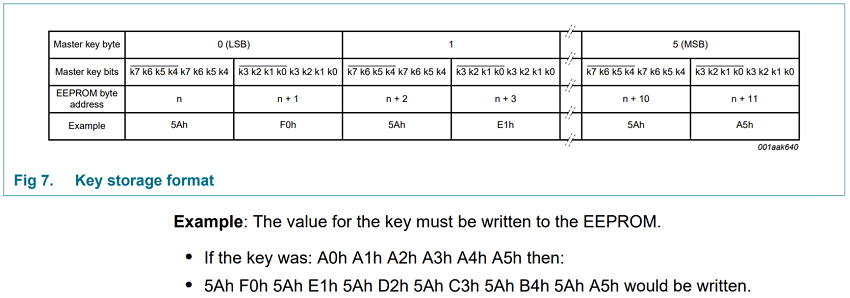
It remains only to collect the key according to the format
And add to the key list.
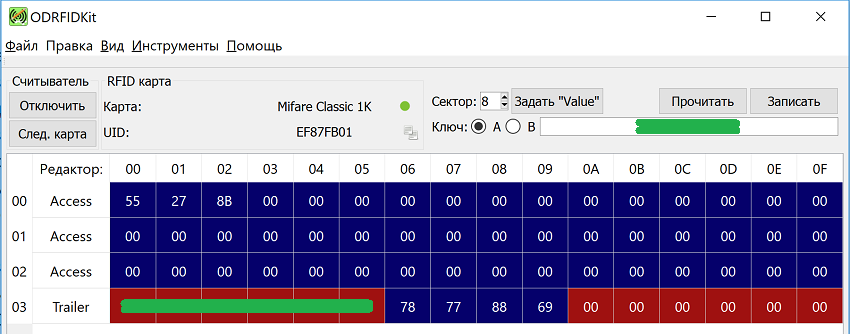
Bingo!!! It turned out that block 8 starts with 3 non-zero bytes, which just go to Wiegand with matching key and reader keys. This data has nothing to do with the UID - most likely it is just a sequence number when issued to the Criminal Code. My trinkets had 3 numbers in a row + one very different. Record blanks was successful, I combined the key from the LCD with the key from the office, which works on UID.
For a successful hacking system, I need to thank the programmer from the Urmet Group, who frankly flipped while writing software for the reader, because if you have hardware that can eliminate such a hacking method (generally simple enough), you cannot call it anything.
Most people working with RFID technology know that the Crypto-1 encryption algorithm used in Mifare (Classic) cards has been cracked long ago and it was possible to get the key from the unit in a “cleaner” way, but I went head-on.
In our own projects we use programmable readers with one time password dictionaries for encryption. This allows you to protect against cloning if the original card is attached to the reader before the clone, otherwise it will allow to detect the fact of duplication (the original card will stop working).

Greetings reader. Today I want to talk about security access control systems (ACS) in general and the example of my LCD. The main vulnerabilities will be considered, and a successful attempt to copy keys will be made. All manipulations will be mostly hardware.
In my residential complex installed intercom system Sinthesi S2, as well as access system yard / porch / floor production of Urmet Group. That was how cool the street panel looked.

until one day it looked like this:

She hung for a couple of days, and then moved to a dumpster nearby. It contained only a reader and a keypad. Because one of the areas in my company is the development of HF readers, I could not resist and decided to study this RFID reader in more detail. From the documentation, I found only a huge catalog from which it was possible to conclude that this is FD-020-017 - 13.56 MHz reader with a Wiegand26 interface. Inside there was a sandwich from reader boards ( MFRC531 ) and MK with BLE ( CC2541 ) glued with hot glue to the case, which was clearly not designed for this board.

The MK board is flooded with a soft compound apparently to protect the radio part from moisture. Having twirled the fee, I put it off.
Until recently, I was not interested in the work of the system, since it was partially started (only access locks worked, but they had an access code, which I knew and did not use the key). After the system was fully started and the access codes were canceled, I began to study it in more detail. It began one of the nights when I returned home and found that the tambour door was already working and the wife was already sleeping. I had only pocket-sized items with me, but as it turned out this was quite enough to bypass all the elite security (as Urmet assures).

All I needed was to unscrew the 2 carving screws holding the panel frame with the car key, remove the 2 blocks and close the relay channel using the same key that goes to the lock of the vestibule door. Everything…
After this incident, when I watch another Hollywood film (“Passengers” (2016) at KDPV) and see how the super secret doors are opened by removing the code panel and sticking a pin into the board (always with sparks and a spectacular opening of the door), I see real situation.
In my memory, most of the access control systems I have seen have access to the lock directly from the code panel, and this is precisely the main vulnerability. All security is provided by several bolts holding this panel, and on faith that this system is reliable. But at the same time, it is possible to significantly increase the entry threshold (let's call it protection from a person with a screwdriver) by using locks with brains that are controlled by the interface - even the simplest. This measure will dramatically reduce the likelihood of spontaneous penetration.
Initial data
ACS LCD as a whole, its work, the reaction to other keys, as well as a way to add keys:
- One free key is given to the apartment, each following - 300r, is registered in the personal account of the ACS. You can only buy from the Criminal Code. In the chat LCD wrote that market copiers could not make a duplicate - it means the system is steeper than just reading the UID.
- When you present any other mifare card, the reader does not even give signs that he sees it.
- When you bring the key to another entrance / floor, the reader peaks in reading, but nothing happens.
- When reading the contents of the key fob 8 and 12, the blocks are hidden and have an access key different from Mifare well-known keys. So the secret is somewhere there.

Beginning of work
First of all, I copied Block0 (the one that contains the UID and the Manufacturer information) to the Mifare Zero disc and checked that it was not enough - the key fob did not work. The reader did not even respond to the presentation of such a clone. It became clear that you need to look for the key from sectors 8 and 12. After reading all the available trinkets, I saw that only one of them locked 12 block, in the rest it is zero, therefore it is obvious that the magic is contained in block 8.
It's time to get a gift reader and consider it more closely. So we have FD-020-017 - 13.56 MHz, Wiegand26 interface. The MFRC531 and CC2541 are connected by a 10-pin comb. And he earned great money on the table - without the rest of the system. I reacted to the keys in the same way as the other readers. First, let's see what comes out:

Silence until the presentation of a valid key fob. After reading the interface leaves the message in full accordance with Wiegand26 . So I decoded the package my key sends. Using a multimeter, I restored the pinout, it turned out that the chips communicate via SPI. We connect the analyzer,

bring a valid key chain and watch the exchange on SPI:

Next, I began to look at the documentation on the MFRC531 microchip and almost gave up seeing that it has a special EEPROM for storing keys. I found the commands to load the key:

The command 0x0B loads from the EEPROM, the command 0x19 from the FIFO, which in turn receives the key via SPI. It would seem that if I load the key from the EEPROM, then I have no chance to reverse this way, but to my surprise, the 0x0B command is not exchanged, but there is a 0x19 command

It remains only to collect the key according to the format

And add to the key list.

Bingo!!! It turned out that block 8 starts with 3 non-zero bytes, which just go to Wiegand with matching key and reader keys. This data has nothing to do with the UID - most likely it is just a sequence number when issued to the Criminal Code. My trinkets had 3 numbers in a row + one very different. Record blanks was successful, I combined the key from the LCD with the key from the office, which works on UID.
Conclusion
For a successful hacking system, I need to thank the programmer from the Urmet Group, who frankly flipped while writing software for the reader, because if you have hardware that can eliminate such a hacking method (generally simple enough), you cannot call it anything.
Most people working with RFID technology know that the Crypto-1 encryption algorithm used in Mifare (Classic) cards has been cracked long ago and it was possible to get the key from the unit in a “cleaner” way, but I went head-on.
In our own projects we use programmable readers with one time password dictionaries for encryption. This allows you to protect against cloning if the original card is attached to the reader before the clone, otherwise it will allow to detect the fact of duplication (the original card will stop working).
Source: https://habr.com/ru/post/439278/