Conference DEFCON 19. Three generations of DoS-attacks (with the participation of the audience as victims). Part 1
My name is Sam Bone, I'm here to talk to you about DoS attacks, and you will help me with this. We'll talk a little about hacktivists who used such attacks, because I find them interesting. They clearly show how much damage you can do with various types of DoS attacks, while at the same time risking to go to prison.
In any case, it helps other people to sell security systems, and for me to motivate my students to learn how these attacks work and how to protect themselves from them. So today you will be my victims. Who of you brought with him a device that is not a pity to "kill"? One, two, three ... not much. Ryan has set up a wireless network to which no more than 40-50 devices can be connected, after which this network will be destroyed. I was sure that not many of those present would want their device to be “killed”. However, I believe that this attack can be used to kill every machine on DefCon. I will demonstrate the version of such an attack, which will be deadly for devices in this room, but will not affect connectivity in other rooms.
On this slide you see me, I teach hacking ethics, networking and computer security at San Francisco City College.
Here with me here are two invited. This is Matthew Prince, who is going to talk about his relationship with ALLSEC. I was very happy to meet him because we were both upset about how immoral, evil people help LulzSec.

I retweeted some of the ALLSEC tweets that pointed to instances of data theft that I thought were important, and he launched a service that they used to protect themselves from such attacks. Therefore, we will be interested to hear about this from Matthew himself.
My second guest is Ryan Carter. He built a network here and is going to use it to “kill” people who have expressed a desire to voluntarily expose themselves to a DoS attack, because through this we learn about several new vulnerabilities.

This is not a zero-day attack, I did not invent it, it has been known for many years and all because many device manufacturers do not fix their vulnerabilities. So if any of you have exotic devices, it would be interesting to subject them to this attack in order to find out how vulnerable they are.
So, here is the content of what I am going to show you. First I will talk about the history of the DoS attacks and the hackers who used it, then about the DDoS attack on the 4th, the OSI transport layer, in which thousands of attackers bring down one site, about the DoS attack on the 7th, application layer, when the hacker single-handedly brings down one or more servers and a router's local network DoS-attack, when one hacker brings down the entire network.
Last year, I told you that the version of Ipv6 will bring a lot of security problems, and that’s what happened. The sixth version of the Internet protocol is a “time warp” when a bunch of things developed in 1993 returned to our networks again, so the old hacker trick worked again. In fact, this is not a very old trick, but rather destructive, and I will show you how one hacker can kill all the machines running Windows on the same network. To do this, you need to send only a few packets per second.

Julian Assange, the head of Wikileaks, agitated everyone with information leakage by publishing about a thousand secret telegrams of the US government, and then posted a mysterious file encrypted with the AES-256 algorithm as a security on the BitTorrent network, so it cannot be decrypted without a key. Assange said that if he is put in prison or killed, he will publish this key, with which the world will be able to learn even more "terrible" secrets. However, despite the fact that Assange was detained in the UK and are preparing to deport to Sweden, the key has not yet been published.
The next slide shows the members of the Anonymous community, who are just tired of posting photos of cats on 4chan and decided to save the world using DoS. For them, it makes sense, but I think this behavior is meaningless.

In general, they began to attack everyone they hated, and started with Scientologists, so that it is very easy to hate Scientologists. Then they took on other people and eventually attacked HB Gary Federal. This guy, Aaron Barr, was supposed to be here, but three days ago he was given a court order forbidding him to participate in the DefCon discussion and tell what actually happened there.
Barra was contractually involved in computer security for government companies when Aaron announced that he was able to find people working with LulzSec and exposed them by correlating their accounts on Twitter and Facebook. Therefore, hackers decided to punish him, which turned out to be an unusually easy task.
The Anonymous community usually uses primitive hacking tools, but the more skilled part of this community has been able to join forces against HB Gary Federal. In order to bring down their website, they used SQL injection and captured an email server. Then they sent a fake letter as if on behalf of the owner of the company with a request to change the login and password and disable the firewall. It worked, after which Anonymous got into the server, took out emails from there and published them on the Internet.
These guys, who later performed as LulzSec, did what any sane person usually asks not to do, and then laughed at what they did. They published the stolen mail - it's funny, they put confidential information about the state of people's health into the network, causing them harm - it's funny again. They found a lot of real dirt in the company's correspondence and published it, because they really decided to tweak HBGary with a serious disgusting thing.

Then Anonymous decided to attack the US Chamber of Commerce, using the Drupal exploit, which is more advanced in a technical sense than the primitive attack tools that this community usually used.
Consider the attack haktivista Th3j35t3r, known under the nickname The Jester (Jester), on the site Wikileaks. This is a demonstration of a powerful attack on OSI level 7, although no one knows what exactly this attack does, it is really secret. Jester announces his attacks on Twitter, discusses them on his blog and shows live on irc.2600.net.
People who were attacked by Jester retained the packet logs, based on which we can conclude that Slowloris was used in this case - an attack with some variations. We can say that he belongs to the right wing of the same movement, the left wing of which is represented by the groups Anonymous and LulzSec. He is probably a former military man, since he tried to strike back those whose actions he regarded as a threat to the lives of American soldiers, in this case Julian Assange, and the recruitment sites of Islamic jihadists. He brought down their sites with his tools and tweeted it.

Anyone could communicate with him, and I spoke with him, he has no partners, unlike LulzSec. This is probably why he hasn’t been caught yet, and he also understands the security of military operations, which LulzSec didn’t learn.
In any case, he alone managed more than a day to disable the site Wikileaks. I talked to him in the IRC chat, and he said: “I am going to stop the attack,” and the attack immediately ceased. Then he said: “Now I will launch it again!”, And the attack resumed. This convinced me that he really controls this attack and this is his business. This slide shows the progress of the attack on Wikileaks, which he carried out alone without a botnet. The attack, which lasted just over 30 minutes, disabled the site for 1 day 3 hours 50 minutes.

After that, Jester decided to fight Anonymous, because those did not like the attacks on Wikileaks. He stated that he was going to introduce the Trojan into the Anonymus tools and capture them from the inside. Jester focused on the fight that ensued between him, Anonymous and LulzSec last year, when they started to “blast” each other with various tricks, including DoS.
Then Jester turned against the guys from the Westboro Baptist church. These guys are also very easy to dislike because of their pathological hatred of homosexuals and LBHT community.

To demonstrate their hatred, they choose a funeral and simply ask for someone to go to them in their faces. Jester brought down 4 of their sites with the help of a regular 3G phone for 2 whole months, and I have no doubt about that, because I know that I can do it myself, and my students could do it, just like any of you. Attack Slowloris runs on Windows, so it is not difficult to implement.
So, the most advanced part of LulzSec continued to hack everyone and in the end they published a phone on which you could call and order them to hack who you want. They hacked into the US Senate, FBI, NATO, and British government sites; they published the contents of the database of consulting firm Booz Allen Hamilton. It made me mad when they hacked into the Arizona Police Server, because it was a very significant blow - they published their names, password hashes and logins, emails. I was outraged when they published hashes with 50 thousand Booz Allen Hamilton passwords, half of which were cracked the next day.
The data of the highest military leadership were in free access, and anyone could use their passwords and logins. They brought down some gaming sites that I hadn’t even heard of, and then posted on lulzsecurity.com a list of their victims and gave links to data stolen from them.

Then they hacked into the PBS non-commercial television service website and posted all sorts of nonsense. Anyway, now they are caught. On June 21, 2011, Ryan Cleary, who was on the periphery of LulzSec, was arrested, and on July 19 in London, the head of this hacker organization was detained. Just a few days ago, on July 27, the Topiary hacker was arrested. So in reality, these hackers are just British teenagers who did dirty work as soon as they broke out of their own home, and their goal was to make people laugh for the sake of laughter. I wonder what makes them do this kind of thing. I am sure this is because they are just young and stupid, which is why they think that you can attack any government site for fun.
By the way, Jester and Sabu both said on Twitter that they visited here yesterday and were in the pool of this hotel, where DefCon is held. I doubt it, but who knows what risks these guys are capable of. Sabu, the main man in LulzSec, is still at large, and is supposed to be about to be captured, because all his accomplices are already arrested. As is usually the case, it is worth arresting one, and he will hand over everyone else, because they are not too strong in providing operational security.

In any case, the DoS attack on the 4th level of the OSI model is one of the simplest attacks when multiple attackers attack the same target. This is what was used to “bring down” MasterCard and Visa, but the hackers couldn’t damage Amazon in the same way, although Anonymus tried to do it.
The MasterCard attack was a protest that united many people. This method of attack, produced by the hacker tool Low Orbit Ion Canon, requires the participation of many computers, 3000 or maybe even 30,000 intruders, their exact number is not known.

They were able to disable the site of this payment system for 1 day, 13 hours and 23 minutes.

This is one of the types of attacks that Kaspersky spoke about in his May 21 interview. He was asked how many compromised machines it would take to completely sever South Africa from the Internet, and he replied that this would require hundreds of thousands of infected computers. But I know that this is not true, for this you need only one 3G mobile phone. Apparently, Kaspersky was not referring to such an attack, he was thinking about an attack on OSI level 4, where thousands of machines are aimed at destroying one common goal. For this, it is enough that many users press the F5 key repeatedly, refreshing the browser page, and thereby overload with requests a specific site. This is one of the most primitive DoS attacks.
One of the most powerful types of DoS attacks on the 7th level of the OSI model is an attack using the Slowloris software written by Robert "RSnake" Hansen a couple of years ago. There were many versions of this software, the essence of which is that one computer sends many incomplete GET requests to the web server, trying to keep the connection open as long as possible.
The server is forced to process them and, ultimately, it is simply “muffled” by all these requests. A request to retrieve a page from the server is an HTTP header that looks like 2nd or 3rd level information. This slide shows several lines, and you send only a portion of these lines to the server and never send the rest. At the same time, the server thinks that you are in some kind of unreliable network, so your packets were fragmented, and since it has the first half, it considers that the second half of the request is still going and continues to wait for it, without closing the connection.

Thus, the server "freezes" all incoming connections, and this is a very powerful attack that actually disables it from the rest of the Internet. I'll show it to you in a couple of minutes.
Slowloris "freezes" all available incoming lines, and in order to kill the Apache server, you just need to send about one packet per second.

Another tool for DoS attacks called RU-Dead-Yet is similar to Slowloris, but uses incomplete HTTP POST and sending long message fields to the server. This stops IIS, but requires thousands of packets per second.

A DoS attack using the Keep-Alive mode allows you to send 100 requests in one connection. It is not as powerful as Slowloris, but it is another effective way to completely load the server with requests.

In many attacks, Jester allegedly adheres to such principles: he acts through Tor to hide the address of the source of the attack, no one knows exactly what he is doing, and his DoS attacks are directed to the 7th level. In doing so, he uses his own tool called XerXes, whose graphical interface is similar to Linux.

One of the most important properties of DoS attacks on the 7th level is that if you can run them through the anonymizer, you will not go to jail. Low Orbit Ion Canon does not use this function, because it has to send a lot of traffic from you to the other end of the network, but if you try to launch it through Tor, you will simply be drowned in your own attack. In addition, such an attack is capable of bringing Tor down, because it acts as a flamethrower, burning everything that is located by you and the target.
The attack on the 7th level acts as a guided rocket - it simply sends a few packets that will not harm you when you get to the server but make it unavailable. Therefore, such an attack can be launched through the anonymizer. At the same time, the victim will not only be able to determine where the attack is coming from, but also will not be able to defend himself using firewall rules, because the firewall is looking for one source address, and in this case, the packets come from different addresses.
If you block all Tor output nodes, and that’s what you should do, it will prevent Tor from using the Tor network and they will look for something else, like a botnet of hacked machines. In any case, XerXes starts working through an anonymous Asian network and “knocks down” the target, after which Jester publishes another tweet called “TANGO DOWN”. For the first time this tool appeared about two years ago.
Another type of DoS attack is Link-Local DoS, which uses the new Internet Protocol IPv6. If you have a version of any modern Linux, Vista, Windows 7 or Windows XP operating system, then you enable IPv6, which is not used by default, because all domain servers, DNS servers or mail servers use IPv6, whether you like it or not . But if you follow your own rules, then disable it like any other unwanted service that you do not use, which will allow you to "kill" the attack.
If you are not so strange a person to use a static IP address, and most people do not use it, then using IPv4, your computer asks for a DHCP server through a router to give it an IP address. The server responds: “OK, use this IP here”, making sure that no one else uses this address, and that’s it. There is no more traffic between the computer and DHCP until the computer is restarted or turned off, and this can be quite a long time. A brief summary of this process: I need an IP - I get an IP.
However, the IPv6 protocol works differently - here a router participates in the distribution of addresses, which advertises itself with the appeal “I am a router! Well, drop all your business and immediately join my network! ”, After which all computers respond, get IP addresses and connect to the network. Broadband broadcasts are taking place here, although picky people will notice that this is not quite the case - in this protocol broadband broadcasts are called multicast. There is no broadband, multicast is used instead, when there is one source and several recipients. То есть роутер рассылает всем узлам один пакет, благодаря которому каждый узел подключается к сети.

В этом вроде бы нет ничего плохого. На следующем слайде показан рекламный пакет роутера, отправляемый каждому узлу сети, которым он сообщает людям, к какой именно сети они должны присоединиться.

Проблема состоит в том, что вы можете отправить множество объявлений маршрутизатора, и когда цели подключатся к сети, всё вроде бы будет в порядке, за исключением того, что Windows делает это чрезвычайно неэффективно. Поэтому позвольте мне показать вам несколько подобных атак, которые называются «флудом объявлений роутера», или RA Flood.

Для этого мне нужно установить несколько виртуальных машин, как я это делаю в классе со своими учениками. Я использую виртуальные машины для создания изолированной сети.
Итак, давайте начнем со старомодной атаки. У меня здесь есть дистрибутив Back Track 5 для Linux машин, работающий как веб-сервер, так что если я перехожу к localhost и обновляю эту страничку с картинкой кошки, всё выглядит в порядке.

Но если вы запустите эту страницу, то увидите состояние вашего сервера. Сейчас я попробую отключить все лишнее, чтобы сэкономить место на экране.

Итак, это страница состояния сервера Apache, внизу которой показано состояние текущего подключения. Мы видим, что сервер находится в ожидании одного подключения, а остальные 9 также доступны.

Этот сервер может обрабатывать запросы сотни людей, просматривающих эту веб-страницу, так что если я перейду на неё и обновлю, а затем вернусь на страницу статуса, то увижу, что теперь у нас имеется несколько активных подключений и ещё 7 доступных. Итак, давайте попробуем атаковать эту бедную машину Linux с Windows-машины. Начнем со старомодных вещей и воспользуемся инструментом Low Orbit Ion Canon, который плохие люди используют в качестве короткого пути в тюрьму.
Мне нужно вставить сюда IP-адрес, и я набираю в адресной строке http:// 192.168.198.173, надеюсь, я правильно его запомнил. Итак, наша атака идёт, а мне нужно больше места на экране. Что-то не очень получается, вот поэтому мне не нравятся виртуальные машины, хотя я вынужден их использовать. Сейчас я обновлю страницу, думаю, это сработает. Процесс идёт довольно медленно и к этому нужно привыкнуть. Вы видите, что IP-адрес наконец-то появился в окне цели нашего хакерского инструмента. С его помощью я могу выполнять различные виды атак.

К сожалению, я не вижу полосу прокрутки, так что придется перейти в полноэкранный режим. В качестве метода я использую HTTP-запрос, а теперь мне нужно добрать до кнопки «Огонь!» и произвести «выстрел» из нашей низкоорбитальной лазерной пушки. Теперь все запросы обращены к моей несчастной виртуальной машине, я обновляю страницу, и вы видите целую кучу соединений – обработано 49 запросов, свободных 0. После каждого обновления страницы количество обращений к серверу увеличивается и постепенно достигает 141.
То, что сейчас происходит – это полные соединения. Сервер осуществляет соединение, скачивает эту маленькую веб-страницу, а затем ждет тайм-аута. Итак, эта штука заполняет все возможные соединения, и веб-сервер становится недоступен. Но она делает это очень слабо, потому что каждое соединение завершается нормально, связывая сервер всего на несколько секунд.

Теперь позвольте мне вернуться к своей виртуальной машине и воспользоваться более мощным инструментом атаки — Slowloris. У меня есть Windows-версия этого эксплойта действительно небольшого размера. Теперь нам не нужно такое большое окно. Я набираю IP-адрес нашей цели в этой строке, и теперь у нас все готово для запуска атаки.

Если вернуться к нашему серверу и обновить страницу, можно увидеть, что он снова в нормальном состоянии, я на него не нападаю, поэтому у нас открыто всего одно соединение. Итак, я нажимаю на кнопку «Запустить атаку», обновляю страницу сервера, и вы видите, как строка запросов заполняется символами R – это поступающие запросы, время ожидания каждого из которых составляет по умолчанию 400 секунд. Таким образом, вам не нужно посылать слишком много таких запросов, чтобы заполнить запросами все входящие соединения и вызвать отказ от обслуживания. Вот что представляет собой атака Slowloris, атака HTTP POST очень на неё похожа, и обе эти атаки достаточны мощные и опасные.
Если я прекращу атаку Slowloris, сервер очень быстро восстановит свою работоспособность. Я не знаю, почему запросы не заняли 400 секунд, возможно, что тайминг по умолчанию в Apache на Back Track 5 отличается от того, что я о нем думаю. В любом случае, теперь, когда я показал вам, как можно убить Linux или Windows, давайте пойдем другим путем и попробуем более мощную атаку. Закроем все эти окна, чтобы продемонстрировать вам зло, которое вот-вот случится.
Итак, я перейду в консоль и попрошу показать мне конфигурацию этого компьютера. Это обычная Windows-машина, и я установил здесь статический IP-адрес IPv6 в диапазоне 2::2, она также имеет свой IP-адрес по протоколу IPv4.

На самом деле здесь пока что ничего не происходит. Я вызову окно диспетчера задач, потому что это интересный способ увидеть ущерб, который будет нанесен компьютеру этой атакой. Вы видите, что загрузка процессора равна 0%. Сейчас я попробую послать своей машине пакеты IPv6, но перед этим создам фейковый роутер под номером 6. Я использую хакерский набор утилит THC IPv6 attack suite, разработанный ван Хаузером из THC. Дальше я набираю в строке eth1 и собираюсь послать это в сеть def: cO::/64. Я нажимаю «Ввод», и роутер посылает некие пакеты, рекламирующие эту сеть.

Больше не нужно ничего ждать — все устройства в этой сети подсоединятся к моему фейковому роутеру, и теперь вы видите, что параметры компьютера изменились – теперь IP-адрес IPv6 начинается с диапазона def: cO.

То есть я добавляю роутер, который объявляет свой префикс, все к нему присоединяются и на этом игра окончена. Но если я пошлю кучу нежелательных пакетов со скоростью несколько сотен в секунду, вы увидите, что процессор компьютера зависнет под загрузкой 100% на долгое-долгое время.
(аплодисменты аудитории)

24:00 мин
Конференция DEFCON 19. Три поколения DoS-атак (с участием аудитории в качестве жертв). Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
In any case, it helps other people to sell security systems, and for me to motivate my students to learn how these attacks work and how to protect themselves from them. So today you will be my victims. Who of you brought with him a device that is not a pity to "kill"? One, two, three ... not much. Ryan has set up a wireless network to which no more than 40-50 devices can be connected, after which this network will be destroyed. I was sure that not many of those present would want their device to be “killed”. However, I believe that this attack can be used to kill every machine on DefCon. I will demonstrate the version of such an attack, which will be deadly for devices in this room, but will not affect connectivity in other rooms.
On this slide you see me, I teach hacking ethics, networking and computer security at San Francisco City College.

Here with me here are two invited. This is Matthew Prince, who is going to talk about his relationship with ALLSEC. I was very happy to meet him because we were both upset about how immoral, evil people help LulzSec.

I retweeted some of the ALLSEC tweets that pointed to instances of data theft that I thought were important, and he launched a service that they used to protect themselves from such attacks. Therefore, we will be interested to hear about this from Matthew himself.
My second guest is Ryan Carter. He built a network here and is going to use it to “kill” people who have expressed a desire to voluntarily expose themselves to a DoS attack, because through this we learn about several new vulnerabilities.

This is not a zero-day attack, I did not invent it, it has been known for many years and all because many device manufacturers do not fix their vulnerabilities. So if any of you have exotic devices, it would be interesting to subject them to this attack in order to find out how vulnerable they are.
So, here is the content of what I am going to show you. First I will talk about the history of the DoS attacks and the hackers who used it, then about the DDoS attack on the 4th, the OSI transport layer, in which thousands of attackers bring down one site, about the DoS attack on the 7th, application layer, when the hacker single-handedly brings down one or more servers and a router's local network DoS-attack, when one hacker brings down the entire network.
Last year, I told you that the version of Ipv6 will bring a lot of security problems, and that’s what happened. The sixth version of the Internet protocol is a “time warp” when a bunch of things developed in 1993 returned to our networks again, so the old hacker trick worked again. In fact, this is not a very old trick, but rather destructive, and I will show you how one hacker can kill all the machines running Windows on the same network. To do this, you need to send only a few packets per second.

Julian Assange, the head of Wikileaks, agitated everyone with information leakage by publishing about a thousand secret telegrams of the US government, and then posted a mysterious file encrypted with the AES-256 algorithm as a security on the BitTorrent network, so it cannot be decrypted without a key. Assange said that if he is put in prison or killed, he will publish this key, with which the world will be able to learn even more "terrible" secrets. However, despite the fact that Assange was detained in the UK and are preparing to deport to Sweden, the key has not yet been published.
The next slide shows the members of the Anonymous community, who are just tired of posting photos of cats on 4chan and decided to save the world using DoS. For them, it makes sense, but I think this behavior is meaningless.

In general, they began to attack everyone they hated, and started with Scientologists, so that it is very easy to hate Scientologists. Then they took on other people and eventually attacked HB Gary Federal. This guy, Aaron Barr, was supposed to be here, but three days ago he was given a court order forbidding him to participate in the DefCon discussion and tell what actually happened there.
Barra was contractually involved in computer security for government companies when Aaron announced that he was able to find people working with LulzSec and exposed them by correlating their accounts on Twitter and Facebook. Therefore, hackers decided to punish him, which turned out to be an unusually easy task.
The Anonymous community usually uses primitive hacking tools, but the more skilled part of this community has been able to join forces against HB Gary Federal. In order to bring down their website, they used SQL injection and captured an email server. Then they sent a fake letter as if on behalf of the owner of the company with a request to change the login and password and disable the firewall. It worked, after which Anonymous got into the server, took out emails from there and published them on the Internet.
These guys, who later performed as LulzSec, did what any sane person usually asks not to do, and then laughed at what they did. They published the stolen mail - it's funny, they put confidential information about the state of people's health into the network, causing them harm - it's funny again. They found a lot of real dirt in the company's correspondence and published it, because they really decided to tweak HBGary with a serious disgusting thing.

Then Anonymous decided to attack the US Chamber of Commerce, using the Drupal exploit, which is more advanced in a technical sense than the primitive attack tools that this community usually used.
Consider the attack haktivista Th3j35t3r, known under the nickname The Jester (Jester), on the site Wikileaks. This is a demonstration of a powerful attack on OSI level 7, although no one knows what exactly this attack does, it is really secret. Jester announces his attacks on Twitter, discusses them on his blog and shows live on irc.2600.net.
People who were attacked by Jester retained the packet logs, based on which we can conclude that Slowloris was used in this case - an attack with some variations. We can say that he belongs to the right wing of the same movement, the left wing of which is represented by the groups Anonymous and LulzSec. He is probably a former military man, since he tried to strike back those whose actions he regarded as a threat to the lives of American soldiers, in this case Julian Assange, and the recruitment sites of Islamic jihadists. He brought down their sites with his tools and tweeted it.

Anyone could communicate with him, and I spoke with him, he has no partners, unlike LulzSec. This is probably why he hasn’t been caught yet, and he also understands the security of military operations, which LulzSec didn’t learn.
In any case, he alone managed more than a day to disable the site Wikileaks. I talked to him in the IRC chat, and he said: “I am going to stop the attack,” and the attack immediately ceased. Then he said: “Now I will launch it again!”, And the attack resumed. This convinced me that he really controls this attack and this is his business. This slide shows the progress of the attack on Wikileaks, which he carried out alone without a botnet. The attack, which lasted just over 30 minutes, disabled the site for 1 day 3 hours 50 minutes.

After that, Jester decided to fight Anonymous, because those did not like the attacks on Wikileaks. He stated that he was going to introduce the Trojan into the Anonymus tools and capture them from the inside. Jester focused on the fight that ensued between him, Anonymous and LulzSec last year, when they started to “blast” each other with various tricks, including DoS.
Then Jester turned against the guys from the Westboro Baptist church. These guys are also very easy to dislike because of their pathological hatred of homosexuals and LBHT community.

To demonstrate their hatred, they choose a funeral and simply ask for someone to go to them in their faces. Jester brought down 4 of their sites with the help of a regular 3G phone for 2 whole months, and I have no doubt about that, because I know that I can do it myself, and my students could do it, just like any of you. Attack Slowloris runs on Windows, so it is not difficult to implement.
So, the most advanced part of LulzSec continued to hack everyone and in the end they published a phone on which you could call and order them to hack who you want. They hacked into the US Senate, FBI, NATO, and British government sites; they published the contents of the database of consulting firm Booz Allen Hamilton. It made me mad when they hacked into the Arizona Police Server, because it was a very significant blow - they published their names, password hashes and logins, emails. I was outraged when they published hashes with 50 thousand Booz Allen Hamilton passwords, half of which were cracked the next day.
The data of the highest military leadership were in free access, and anyone could use their passwords and logins. They brought down some gaming sites that I hadn’t even heard of, and then posted on lulzsecurity.com a list of their victims and gave links to data stolen from them.

Then they hacked into the PBS non-commercial television service website and posted all sorts of nonsense. Anyway, now they are caught. On June 21, 2011, Ryan Cleary, who was on the periphery of LulzSec, was arrested, and on July 19 in London, the head of this hacker organization was detained. Just a few days ago, on July 27, the Topiary hacker was arrested. So in reality, these hackers are just British teenagers who did dirty work as soon as they broke out of their own home, and their goal was to make people laugh for the sake of laughter. I wonder what makes them do this kind of thing. I am sure this is because they are just young and stupid, which is why they think that you can attack any government site for fun.
By the way, Jester and Sabu both said on Twitter that they visited here yesterday and were in the pool of this hotel, where DefCon is held. I doubt it, but who knows what risks these guys are capable of. Sabu, the main man in LulzSec, is still at large, and is supposed to be about to be captured, because all his accomplices are already arrested. As is usually the case, it is worth arresting one, and he will hand over everyone else, because they are not too strong in providing operational security.

In any case, the DoS attack on the 4th level of the OSI model is one of the simplest attacks when multiple attackers attack the same target. This is what was used to “bring down” MasterCard and Visa, but the hackers couldn’t damage Amazon in the same way, although Anonymus tried to do it.
The MasterCard attack was a protest that united many people. This method of attack, produced by the hacker tool Low Orbit Ion Canon, requires the participation of many computers, 3000 or maybe even 30,000 intruders, their exact number is not known.

They were able to disable the site of this payment system for 1 day, 13 hours and 23 minutes.

This is one of the types of attacks that Kaspersky spoke about in his May 21 interview. He was asked how many compromised machines it would take to completely sever South Africa from the Internet, and he replied that this would require hundreds of thousands of infected computers. But I know that this is not true, for this you need only one 3G mobile phone. Apparently, Kaspersky was not referring to such an attack, he was thinking about an attack on OSI level 4, where thousands of machines are aimed at destroying one common goal. For this, it is enough that many users press the F5 key repeatedly, refreshing the browser page, and thereby overload with requests a specific site. This is one of the most primitive DoS attacks.
One of the most powerful types of DoS attacks on the 7th level of the OSI model is an attack using the Slowloris software written by Robert "RSnake" Hansen a couple of years ago. There were many versions of this software, the essence of which is that one computer sends many incomplete GET requests to the web server, trying to keep the connection open as long as possible.
The server is forced to process them and, ultimately, it is simply “muffled” by all these requests. A request to retrieve a page from the server is an HTTP header that looks like 2nd or 3rd level information. This slide shows several lines, and you send only a portion of these lines to the server and never send the rest. At the same time, the server thinks that you are in some kind of unreliable network, so your packets were fragmented, and since it has the first half, it considers that the second half of the request is still going and continues to wait for it, without closing the connection.

Thus, the server "freezes" all incoming connections, and this is a very powerful attack that actually disables it from the rest of the Internet. I'll show it to you in a couple of minutes.
Slowloris "freezes" all available incoming lines, and in order to kill the Apache server, you just need to send about one packet per second.

Another tool for DoS attacks called RU-Dead-Yet is similar to Slowloris, but uses incomplete HTTP POST and sending long message fields to the server. This stops IIS, but requires thousands of packets per second.

A DoS attack using the Keep-Alive mode allows you to send 100 requests in one connection. It is not as powerful as Slowloris, but it is another effective way to completely load the server with requests.

In many attacks, Jester allegedly adheres to such principles: he acts through Tor to hide the address of the source of the attack, no one knows exactly what he is doing, and his DoS attacks are directed to the 7th level. In doing so, he uses his own tool called XerXes, whose graphical interface is similar to Linux.

One of the most important properties of DoS attacks on the 7th level is that if you can run them through the anonymizer, you will not go to jail. Low Orbit Ion Canon does not use this function, because it has to send a lot of traffic from you to the other end of the network, but if you try to launch it through Tor, you will simply be drowned in your own attack. In addition, such an attack is capable of bringing Tor down, because it acts as a flamethrower, burning everything that is located by you and the target.
The attack on the 7th level acts as a guided rocket - it simply sends a few packets that will not harm you when you get to the server but make it unavailable. Therefore, such an attack can be launched through the anonymizer. At the same time, the victim will not only be able to determine where the attack is coming from, but also will not be able to defend himself using firewall rules, because the firewall is looking for one source address, and in this case, the packets come from different addresses.
If you block all Tor output nodes, and that’s what you should do, it will prevent Tor from using the Tor network and they will look for something else, like a botnet of hacked machines. In any case, XerXes starts working through an anonymous Asian network and “knocks down” the target, after which Jester publishes another tweet called “TANGO DOWN”. For the first time this tool appeared about two years ago.
Another type of DoS attack is Link-Local DoS, which uses the new Internet Protocol IPv6. If you have a version of any modern Linux, Vista, Windows 7 or Windows XP operating system, then you enable IPv6, which is not used by default, because all domain servers, DNS servers or mail servers use IPv6, whether you like it or not . But if you follow your own rules, then disable it like any other unwanted service that you do not use, which will allow you to "kill" the attack.

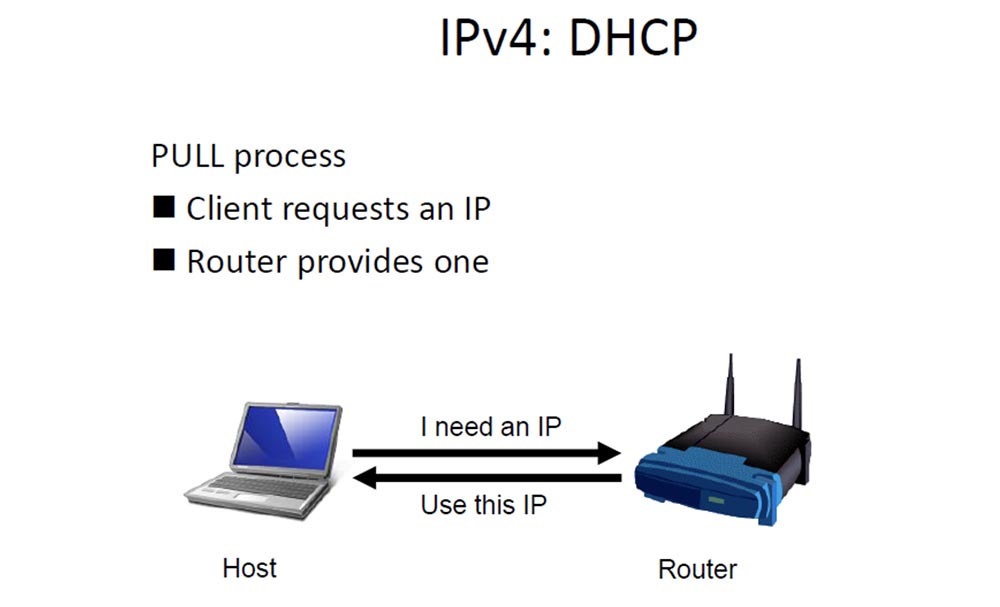
If you are not so strange a person to use a static IP address, and most people do not use it, then using IPv4, your computer asks for a DHCP server through a router to give it an IP address. The server responds: “OK, use this IP here”, making sure that no one else uses this address, and that’s it. There is no more traffic between the computer and DHCP until the computer is restarted or turned off, and this can be quite a long time. A brief summary of this process: I need an IP - I get an IP.
However, the IPv6 protocol works differently - here a router participates in the distribution of addresses, which advertises itself with the appeal “I am a router! Well, drop all your business and immediately join my network! ”, After which all computers respond, get IP addresses and connect to the network. Broadband broadcasts are taking place here, although picky people will notice that this is not quite the case - in this protocol broadband broadcasts are called multicast. There is no broadband, multicast is used instead, when there is one source and several recipients. То есть роутер рассылает всем узлам один пакет, благодаря которому каждый узел подключается к сети.

В этом вроде бы нет ничего плохого. На следующем слайде показан рекламный пакет роутера, отправляемый каждому узлу сети, которым он сообщает людям, к какой именно сети они должны присоединиться.

Проблема состоит в том, что вы можете отправить множество объявлений маршрутизатора, и когда цели подключатся к сети, всё вроде бы будет в порядке, за исключением того, что Windows делает это чрезвычайно неэффективно. Поэтому позвольте мне показать вам несколько подобных атак, которые называются «флудом объявлений роутера», или RA Flood.

Для этого мне нужно установить несколько виртуальных машин, как я это делаю в классе со своими учениками. Я использую виртуальные машины для создания изолированной сети.
Итак, давайте начнем со старомодной атаки. У меня здесь есть дистрибутив Back Track 5 для Linux машин, работающий как веб-сервер, так что если я перехожу к localhost и обновляю эту страничку с картинкой кошки, всё выглядит в порядке.

Но если вы запустите эту страницу, то увидите состояние вашего сервера. Сейчас я попробую отключить все лишнее, чтобы сэкономить место на экране.

Итак, это страница состояния сервера Apache, внизу которой показано состояние текущего подключения. Мы видим, что сервер находится в ожидании одного подключения, а остальные 9 также доступны.

Этот сервер может обрабатывать запросы сотни людей, просматривающих эту веб-страницу, так что если я перейду на неё и обновлю, а затем вернусь на страницу статуса, то увижу, что теперь у нас имеется несколько активных подключений и ещё 7 доступных. Итак, давайте попробуем атаковать эту бедную машину Linux с Windows-машины. Начнем со старомодных вещей и воспользуемся инструментом Low Orbit Ion Canon, который плохие люди используют в качестве короткого пути в тюрьму.
Мне нужно вставить сюда IP-адрес, и я набираю в адресной строке http:// 192.168.198.173, надеюсь, я правильно его запомнил. Итак, наша атака идёт, а мне нужно больше места на экране. Что-то не очень получается, вот поэтому мне не нравятся виртуальные машины, хотя я вынужден их использовать. Сейчас я обновлю страницу, думаю, это сработает. Процесс идёт довольно медленно и к этому нужно привыкнуть. Вы видите, что IP-адрес наконец-то появился в окне цели нашего хакерского инструмента. С его помощью я могу выполнять различные виды атак.

К сожалению, я не вижу полосу прокрутки, так что придется перейти в полноэкранный режим. В качестве метода я использую HTTP-запрос, а теперь мне нужно добрать до кнопки «Огонь!» и произвести «выстрел» из нашей низкоорбитальной лазерной пушки. Теперь все запросы обращены к моей несчастной виртуальной машине, я обновляю страницу, и вы видите целую кучу соединений – обработано 49 запросов, свободных 0. После каждого обновления страницы количество обращений к серверу увеличивается и постепенно достигает 141.
То, что сейчас происходит – это полные соединения. Сервер осуществляет соединение, скачивает эту маленькую веб-страницу, а затем ждет тайм-аута. Итак, эта штука заполняет все возможные соединения, и веб-сервер становится недоступен. Но она делает это очень слабо, потому что каждое соединение завершается нормально, связывая сервер всего на несколько секунд.

Теперь позвольте мне вернуться к своей виртуальной машине и воспользоваться более мощным инструментом атаки — Slowloris. У меня есть Windows-версия этого эксплойта действительно небольшого размера. Теперь нам не нужно такое большое окно. Я набираю IP-адрес нашей цели в этой строке, и теперь у нас все готово для запуска атаки.

Если вернуться к нашему серверу и обновить страницу, можно увидеть, что он снова в нормальном состоянии, я на него не нападаю, поэтому у нас открыто всего одно соединение. Итак, я нажимаю на кнопку «Запустить атаку», обновляю страницу сервера, и вы видите, как строка запросов заполняется символами R – это поступающие запросы, время ожидания каждого из которых составляет по умолчанию 400 секунд. Таким образом, вам не нужно посылать слишком много таких запросов, чтобы заполнить запросами все входящие соединения и вызвать отказ от обслуживания. Вот что представляет собой атака Slowloris, атака HTTP POST очень на неё похожа, и обе эти атаки достаточны мощные и опасные.
Если я прекращу атаку Slowloris, сервер очень быстро восстановит свою работоспособность. Я не знаю, почему запросы не заняли 400 секунд, возможно, что тайминг по умолчанию в Apache на Back Track 5 отличается от того, что я о нем думаю. В любом случае, теперь, когда я показал вам, как можно убить Linux или Windows, давайте пойдем другим путем и попробуем более мощную атаку. Закроем все эти окна, чтобы продемонстрировать вам зло, которое вот-вот случится.
Итак, я перейду в консоль и попрошу показать мне конфигурацию этого компьютера. Это обычная Windows-машина, и я установил здесь статический IP-адрес IPv6 в диапазоне 2::2, она также имеет свой IP-адрес по протоколу IPv4.

На самом деле здесь пока что ничего не происходит. Я вызову окно диспетчера задач, потому что это интересный способ увидеть ущерб, который будет нанесен компьютеру этой атакой. Вы видите, что загрузка процессора равна 0%. Сейчас я попробую послать своей машине пакеты IPv6, но перед этим создам фейковый роутер под номером 6. Я использую хакерский набор утилит THC IPv6 attack suite, разработанный ван Хаузером из THC. Дальше я набираю в строке eth1 и собираюсь послать это в сеть def: cO::/64. Я нажимаю «Ввод», и роутер посылает некие пакеты, рекламирующие эту сеть.

Больше не нужно ничего ждать — все устройства в этой сети подсоединятся к моему фейковому роутеру, и теперь вы видите, что параметры компьютера изменились – теперь IP-адрес IPv6 начинается с диапазона def: cO.

То есть я добавляю роутер, который объявляет свой префикс, все к нему присоединяются и на этом игра окончена. Но если я пошлю кучу нежелательных пакетов со скоростью несколько сотен в секунду, вы увидите, что процессор компьютера зависнет под загрузкой 100% на долгое-долгое время.
(аплодисменты аудитории)

24:00 мин
Конференция DEFCON 19. Три поколения DoS-атак (с участием аудитории в качестве жертв). Part 2
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/440794/