How did we choose the DLP system (practical experience)
Hi, Habr! Not so long ago, a rather typical situation arose - the management gave the command “ Select data protection system against leakage ”. The main selection criterion is the ability to solve a problem to prevent leaks of critical (according to management) documentation, files, and the like. As follows from the oral central manager, the journals and various analytical functional equipment are secondary. Quoting the chief, “ to catch intruders, we can also hang up video cameras, solve the problem so as not to deal with leaks, but eliminate them ”. Of course, everyone understands that 100% elimination of the risk of leaks is unrealistic, so we are talking about minimizing the risk of information leakage.

A little about the company: we are medium in size - about 300 workstations (on some work in shifts), plus for some of the employees we have remote access to virtual work environments via Citrix Desktop. As a side effect, some compliance was considered for 152 FZ and the corresponding organization for the protection of personal data.
We have no relation to the state; other branch regulatory requirements are also not affected in principle. The price of the issue and the procurement process in general is the business of the competent unit. Accordingly, the cost of the solution and the fashionable topic of import substitution did not limit us, and we could consider any development: both domestic and foreign. We (a small information security department consisting of as many as three people) did not want to fill in various questionnaires and forms from vendors and integrators, so we decided to refresh our memory with fact-checking (we already knew the DLP theme, but without much practical experience). This means using your own hands to test only those DLP systems that are either relatively easy (“without registration and SMS” and the company’s illumination before the seller) can be obtained for an independent test on their own stand, or can be viewed in the work of colleagues from other organizations. Important: Considering that further implementation and operation will be carried out on our own, we just wanted to test it ourselves on the stand, and not to watch the “properly debugged” demo versions “from the hands” and brochures to make sure that the declared functions are actually implemented and work as we need.
Systems based on monitoring applications, screen shots, keyboards, etc. they didn’t even try to watch - simply because they don’t solve the key task, no matter how their developers are positioned on the market. This refers to Stakhanovets and his clone from the Infofotch Person Monitor, StaffCop, TimeInformer, KickIdler and the like. This does not mean that these systems are bad - they just do not solve the key task “ to prevent leaks! ”Confidential data, but can be (possibly) a good tool for other tasks with passive observation.
They got acquainted with independent analytical and review materials ... they turned out to be sparse. From the readable - two publications on Habré ( one and two times ) and an already outdated and very superficial review on Anti-Malware with a separate comparison in tabular form.
We were interested in: foreign Symantec DLP, Forcepoint DLP, McAfee DLP, Sophos Endpoint Protection, Russian (or Russian) Solar Dozor, Zecurion DLP, InfoWatch Traffic Monitor, DeviceLock DLP, Information Security Circuit SearchInform, Falcongaze SecureTower.
As soon as we receive in our hands a distributive of a fresh version or an invitation to colleagues, the tests themselves of the declared functions and capabilities were carried out. As a source of additional information, publications and recordings of webinars of vendors and their partners were taken, as well as data from OBS agencies, that is, the expert opinion of colleagues with experience.
Immediately list what DLP-system failed to see.
The test results were summarized in a table of the type of function - system / compliance, it turned out quite a lot. They checked how each tested DLP performs the tasks set for a large range of data leakage channels, what other possibilities there are, how it works in principle with the system ... The test is, of course, not a full-fledged pilot, something could be missed, I apologize for it right away.
They checked simple things that directly correspond to the task: blocking the channel as such for specified users (“ this is not possible! ”); sending a shadow copy of the intercepted document to the archive; notification for IB when a ban is triggered.
Were checked:
Upon successful completion of the basic test, an additional stress test was carried out with elements of load and complications for the analytical module of the system:
As additional useful functions (in addition to verification of compliance with the primary criterion, see above), we looked at analytical capabilities, work with the archive and reporting. The function of scanning workstations (for example, how the system will find a document with passport data at the workstation) was decided to be postponed for another approach; now this task is not paramount (and critical in general).
The test bench is simple, as a server, a virtual machine with 8 GB of dedicated memory, as a guinea pig, a typical computer on i5 / 2.3 GHz / 4 Gb RAM and 32-bit Windows 10.
Well, here are some of the DLP systems that we managed to see and touch at our booth or at colleagues, and the corresponding impressions on them: McAfee DLP, Sophos Endpoint Protection, InfoWatch Traffic Monitor, DeviceLock DLP, Information Security Circuit SearchInform, Falcongaze SecureTower. To begin, I will describe general impressions, then a review of the actual test runs.
The tests got version of McAfee Data Loss Prevention 10.0.100.
At once I want to note that this is a very difficult system both in installation and configuration. To install and use it, you must first deploy McAfee ePolicy Orchestrator as your own management platform. Maybe for organizations where McAfee's ecosystem of solutions is fully implemented, it will be meaningful and convenient, but for the sake of one product ... pleasure from the category of dubious. The situation is somewhat facilitated by the fact that the user documentation is very thoughtful and describes the entire installation procedure, and the installer himself installs all the external components he needs. But for a long time ... Setting the rules is not an easy task either.
I liked: the ability to set conditional priorities for the rules, and then use these priorities as filtering events in the log. The filtering itself is very nice and convenient. The ability to give the user to send a file when banned, if it provides some kind of explanation (user-justification).
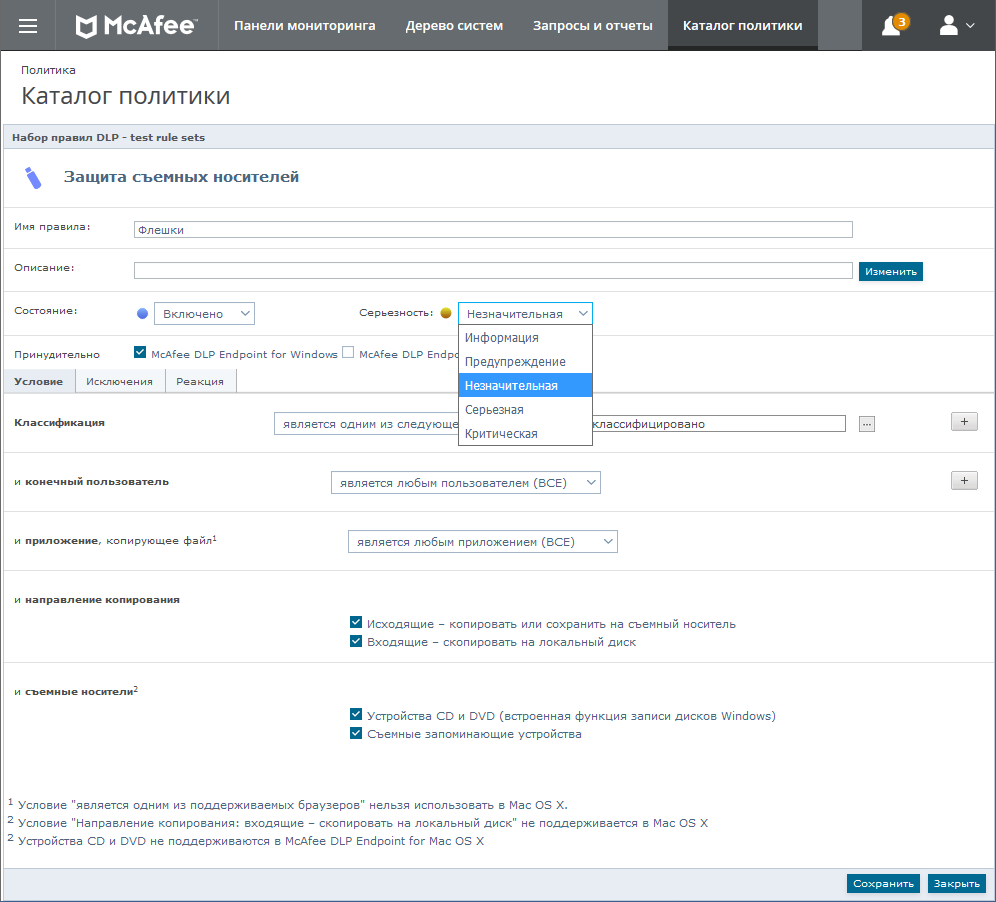
Disliked: the already mentioned need to install its own management platform, largely duplicating AD. Built-in OCR-module is absent, control of scanned documents is by. They identified a number of restrictions, such as email control only in Outlook (correspondence through The Bat! Flew past agency control), dependence on specific browser versions, and lack of control of correspondence in Skype (only files are intercepted).
Summary: At first glance, McAfee DLP seemed to us a very interesting solution, despite the shortcomings mentioned above. Grieved that the wizards for the task of the politician were gone - in the once studied old versions it was in our opinion more convenient than in the current web console. The key drawback is that almost all control is implemented through application control, and not at the protocol or driver level. Allows you to block flashing devices in a Citrix environment.
The tests took the version of Sophos Endpoint Protection 10.
The solution is complex, the foundation is antivirus. It took a long time to install. The manual does not even specify the system requirements - for them, if you please the site. Policies are set based on per computer logic :(
I liked it: as in McAfee, it is possible to let the user send the file when banned. On this, perhaps, everything.
I did not like it: there are no difficulties in circumventing device control by an agent — stop the antivirus from Sophos, then enable the device driver in the Device Manager - and voila, full access to the prohibited flash drive. Somehow difficult and dull done with the implementation and configuration of content analysis rules, which in the end have not yet been implemented in fact. Surprisingly, there are no shadow copies. Notifications in the form of email alerting and SNMP messaging must be configured from the antivirus of the same developer. The list of monitored devices is poor, mail is controlled through embedding in email clients. Access control to the sites is made just like firewall. Built-in OCR-module is absent, control of scanned documents is by. The user manual is sad - no details can be found in it. There is not even a description of what is meant by this or that built-in rule - whether it is a dictionary test, or a regular expression ...
Summary: Unsuccessful, in our opinion, solution. In fact, this is an appendix to the antivirus, and even the complete absence of the possibility of creating an evidence base for incidents. Policies are not set by users, but by machines — this is unacceptable. Well, actually, from the free supplements to the antivirus a lot was not expected, but hope dies last.
Perhaps the most promoted DLP complex on our market, which means we expected the most from it. Opportunities just to take and see - no, but the site is replete with beauty from marketers. It was difficult for the tests, but I managed to get the version of InfoWatch Traffic Monitor 6.9 Enterprise. Perhaps there is a newer version - but we don’t know about it, we didn’t find all the same marketing in kilotons. But the technical information on the site is somehow not enough. The test revealed that the documentation had the same problem - if something is unclear, it’s almost impossible to find the answer in the manual, there is no detail in general. This greatly reduces the possibility of self-exploitation.
It was pleasant: very high-quality, well-thought-out interface, with good structuredness. Convenient dashboards, where you can configure a specific query, the time of its update - and then continue to watch the whole picture. A good assortment of console widgets. It is possible to send a user request to provide access to the device straight from the agent module. Ability to specify different recipients for notifications depending on the type of event and user membership in the OU. A solid set of reports. Good opportunities to work with the archive, a large set of tools for analyzing the content of data in the archive is supported. There is a creation of screenshots from workstations.
I didn’t like it: in fact, it’s not just one product, but a bunch of Infowatch Traffic Monitor and Infowatch Device Monitor, and it works on two operating systems (Windows and Red Hat Linux), so installation and configuration for launching are complicated. There are also two management consoles. The widely advertised developer logic “checked content, only then we block, do not interfere with business processes” is actually somewhere in the bud. Content analysis for monitoring devices is simply not available - access to devices can be denied for users, there are whitelists, but they simply don’t know what is inside the document that is being written to the USB flash drive. For network channels there is about the same problem - content checking is implemented only for SMTP and HTTP. As they say, colleagues familiar with this decision for a long time, now at least there is an opportunity to block network channels - there used to be only monitoring. In fact - this feature is limited to HTTP, FTP, SMTP, plus file sharing and some instant messengers. I repeat, the possibility of blocking the transfer of data on the basis of checking their contents in, for example, instant messengers, no - only SMTP and HTTP. This is not bad, but not very consistent with the description in the brochures, and this is not enough to fully cover the leakage channels. The agent module is actually implemented as a mix of different agents.
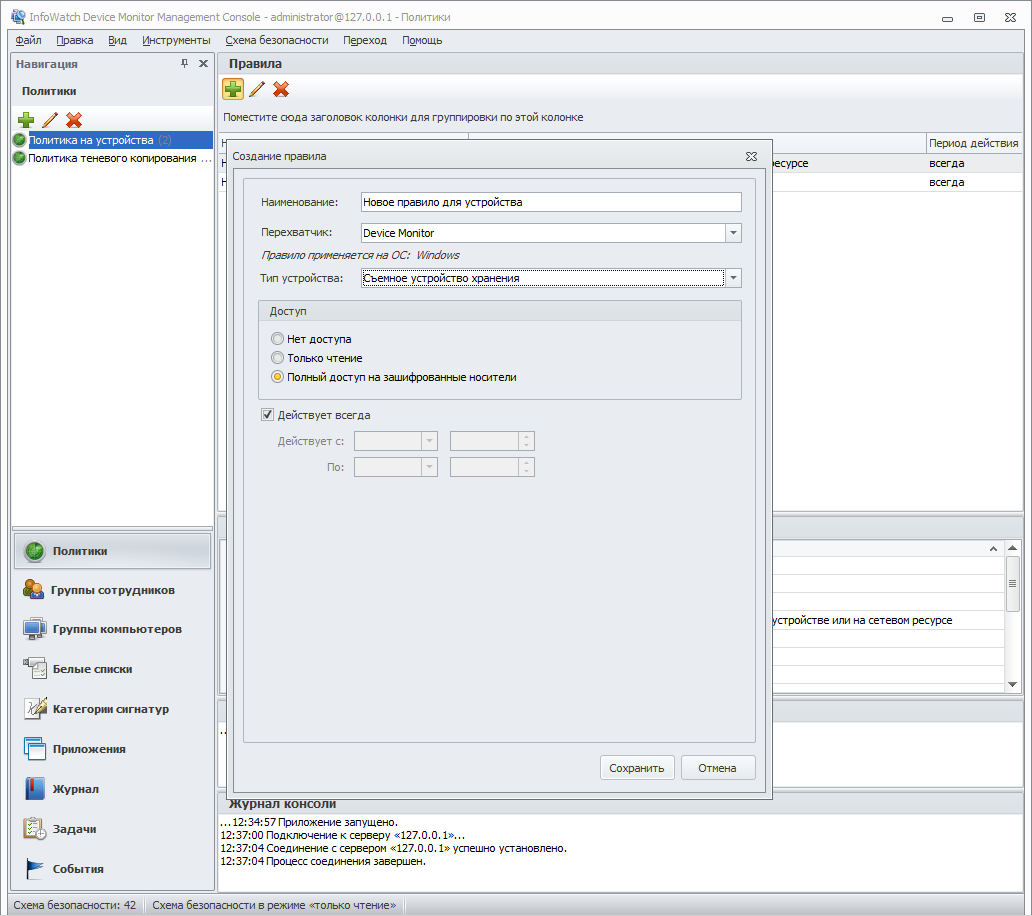
Summary: In general, the solution looks (especially looks) very well. Device control at a basic level is good, for network channels monitoring is good, and blocking is satisfactory. In terminal sessions, allows you to deny access to the forwarded disks, or provide read access only, shadow copying works (for both flash drives and forwarded disks). The lack of content verification for most of the monitored channels, especially devices, is distressing, despite the fact that logic is stated in marketing documents. Let's hope that this is a kind of roadmap, and sooner or later, developers will catch up with marketers. In the meantime - PR five, the developers of the troika with a plus. Or vice versa. How to look.
The tests were taken version 8.3 (last updated, released in December 2018), downloaded by the developer site.
A fairly highly specialized system, only protection against leaks and nothing more - no screenshots, application controls ... However, if you believe information from webinars from the developer, user control functions should appear through screenshots in the foreseeable future. Installation is easy. A lot of management options, old-school consoles, to work with them you need at least some experience of a sysadmin - then everything becomes obvious and simple. In general, the impression is very simple to operate the system.
It was pleasant: detailed elaboration in settings of controls. Not just conditionally control, for example, Skype — but separate control, events, shadow copies, alerts, content checking — and for separate Skype components — chat, files, calls ... The list of monitored devices and network channels is reasonably built, and quite large. Built-in OCR module. Content locks do work, albeit with some workload on workstations. Alerts can come almost instantly. Agents are completely independent with respect to the server part, they can live their own lives, as required. An automatic switching of modes has been done - you can safely let an employee go with a laptop, the politicians will switch themselves to other settings. Blocks and monitoring in the system are still divorced at the console level - there is no difficulty for some channels to turn on the ban for individual comrades, and for other comrades to set the settings only for monitoring. Also, the content analysis rules look independent and work both on a ban and vice versa on the resolution of transmission with the channel closed in principle.
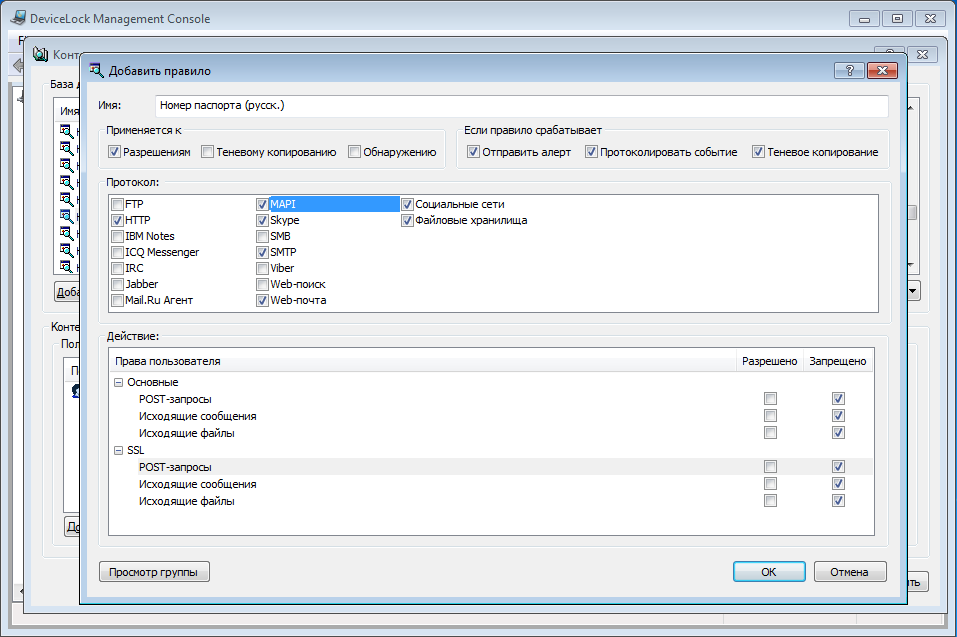
Did not like: no wizards. To set up a policy, you must immediately understand what you need to get, go to the appropriate section of the console and poke ticks, select users, etc. Пошаговый вариант создания политики напрашивается. С другой стороны — можно проверить, что реально задано в плане контроля. Поиск по архиву ограничен полнотекстовым поиском по содержимому теневых копий, поискать по шаблону документа или с помощью словарей возможности нет. Более-менее выручает развитая система фильтров, но это далеко не контентные фильтры. Неизбежная нагрузка на рабочие станции при работе контентно-зависимых правил (терминология разработчика).
Резюме:The system is easy to operate, clearly working, with a rich arsenal of features to protect against information leakage. According to the apt remark of one of the colleagues, it was made according to the principle “set up and forget” Given that all policies are set per user, to change the available operations for a user, it is enough to simply transfer him to another domain User group for which different control rules are configured, from simple controls to rules with content analysis. In terminal sessions, it allows you to set access rights for the forwarded disks (blocking or read-only), for the clipboard (everything is quite flexible depending on the direction of copying, on the type of data being transferred), shadow copying works, blocking by content when writing to the forwarded drives and when transferring data through the clipboard.
We looked at our colleagues, so the dates were very tight. At first I wanted to write “I got the XXXX version for tests”, but I could not. Just because KIB Searchinform is not a system, but acomplex lunch.a set of several almost independent systems. Up to separate consoles for different tasks - we counted as many as 5 pieces. Colleagues say, before the consoles were even more ... The key in this complex is the module EndpointController - version 5.49. The rest have their own numbering. By the way, the distribution kit is also from a handful of archives ... Accordingly, it is not easy to install such a system - you cannot do without documentation. She, in turn, is also specific - written according to the principle of “what I see, I am writing,” without explaining the logic of the work. Management looks like this - interception policies are created in one management console, indexing and index settings for viewing intercepted data a separate console, viewing audit data and shadow copying again a separate console, building reports again a separate console, and so on. And in the marketing descriptions on the site,and in the documentation the word "interception" is constantly found. In practice, this means for almost all network channels leaks only the receipt of a shadow copy. For blocking devices there is, and for Internet channels, you can disable SMTP for all users - or allow. Another option is to use message quarantine for SMTP, which is implemented on the agent. Content analysis as a basis for blocking is done very specifically: the agent sends to quarantine all emails that are already viewed on the server (manually or using a content analyzer) by the administrator and then he chooses what to send next and what to block. We imagined what it would look like in an organization where there are at least 5 more employees than ours ...In practice, this means for almost all network channels leaks only the receipt of a shadow copy. For blocking devices there is, and for Internet channels, you can disable SMTP for all users - or allow. Another option is to use message quarantine for SMTP, which is implemented on the agent. Content analysis as a basis for blocking is done very specifically: the agent sends to quarantine all emails that are already viewed on the server (manually or using a content analyzer) by the administrator and then he chooses what to send next and what to block. We imagined what it would look like in an organization where there are at least 5 more employees than ours ...In practice, this means for almost all network channels leaks only the receipt of a shadow copy. For blocking devices there is, and for Internet channels, you can disable SMTP for all users - or allow. Another option is to use message quarantine for SMTP, which is implemented on the agent. Content analysis as a basis for blocking is done very specifically: the agent sends to quarantine all emails that are already viewed on the server (manually or using a content analyzer) by the administrator and then he chooses what to send next and what to block. We imagined what it would look like in an organization where there are at least 5 more employees than ours ...Another option is to use message quarantine for SMTP, which is implemented on the agent. Content analysis as a basis for blocking is done very specifically: the agent sends to quarantine all emails that are already viewed on the server (manually or using a content analyzer) by the administrator and then he chooses what to send next and what to block. We imagined what it would look like in an organization where there are at least 5 more employees than ours ...Another option is to use message quarantine for SMTP, which is implemented on the agent. Content analysis as a basis for blocking is done very specifically: the agent sends to quarantine all emails that are already viewed on the server (manually or using a content analyzer) by the administrator and then he chooses what to send next and what to block. We imagined what it would look like in an organization where there are at least 5 more employees than ours ...We imagined what it would look like in an organization where there are at least 5 more employees than ours ...We imagined what it would look like in an organization where there are at least 5 more employees than ours ...
I liked it: the power of working with the archive is well developed. There is everything. A lot of criteria, dictionary search tools, regular expressions, fingerprints, corporate “similar search” ... There are tags for different incidents - you can mark already viewed, for example. There is a transparent encryption flash drives.
I did not like it: chaos in the logic of system control, which goes beyond the number of control consoles. No blocking for network channels. The absence of locks on the content for the entire set of "intercepted" channels.
Summary: Device locking is implemented at a decent level, for network channels - at a rudimentary level. In terminal sessions, you can set permissions for the forwarded disks (blocking, read only), shadow copying for the forwarded disks works. In general, the system is quite difficult to operate, strongly focused on investigating incidents - that is, monitoring and working with the archive. For this there is, perhaps, all that is needed. Protecting an organization from data leaks is clearly not here, unless you close devices you don’t need.
The tests got version 6.2. Two key words describing this system, if you do not go into the nuances - it is easy, convenient. Easy to install, conveniently managed, convenient to watch reports, convenient to work with the archive. Documentation is practically not required. Then the focus begins again with the word "interception", as in the CIB. Interception here is just for monitoring, that is, a shadow copy is being created, there is practically no blocking (except for HTTP, SMTP and MAPI). There are screenshots from workstations and some other functions for monitoring user activity.
Liked:friendly user interface. Everything is done for convenience. A good tool for viewing and analyzing the archive, successfully implemented a graph of links. Almost from any report you can go to the event (incident) specified there. Incidents can be assigned categories (investigated, unexplored, deferred). Monitoring Telegram and Viber'a.
Did not like: the lack of locks for network channels. The inability to lock printers and disks thrown into a terminal session. The absence of locks on the content for the entire set of "intercepted" channels. Low stability of the agent - unpredictable hangs and the appearance of dumps were noted. Unexpected console hangs even when working with the archive.
Summary: The system is very easy and convenient to install and operate, but sharpened to monitor and work with the archive. There is a feeling that the system is somewhat damp, OTC is not working.
As mentioned above, the results of the basic tests were tabulated. Parameters that can be assessed subjectively were estimated conditionally, according to the “traffic light scale” - in color.
Actually the table looks like this (clickable):
Stress tests were performed only for McAfee and DeviceLock DLP. In other cases, there was simply no point (see the table below).
At McAfee correctly worked ban archive with Excel file.
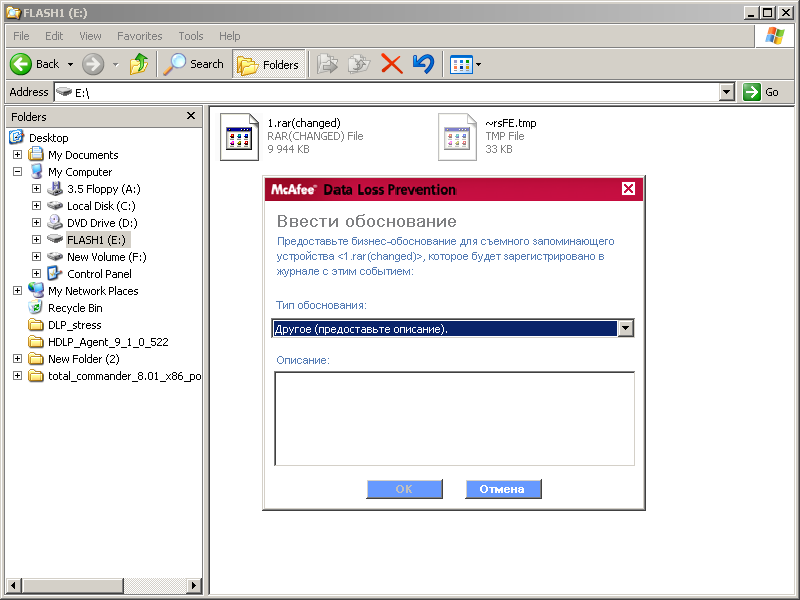
The test with the interception of the scan in McAfee did not go - there is no built-in OCR.
With checking on templates - it works only with full compliance, if the document is changed - the DLP system skips it.
At DeviceLock DLP all tests worked completely. Amended agreement, interception in Skype:

Writing to the flash drive archive with a littered Excel file:
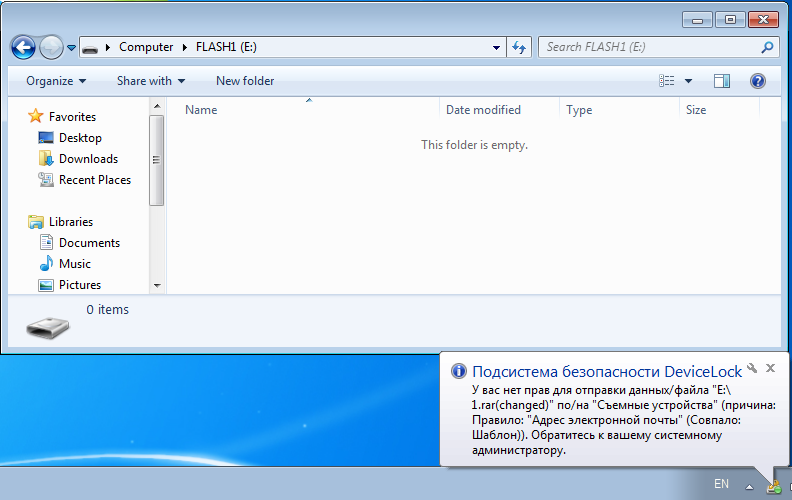
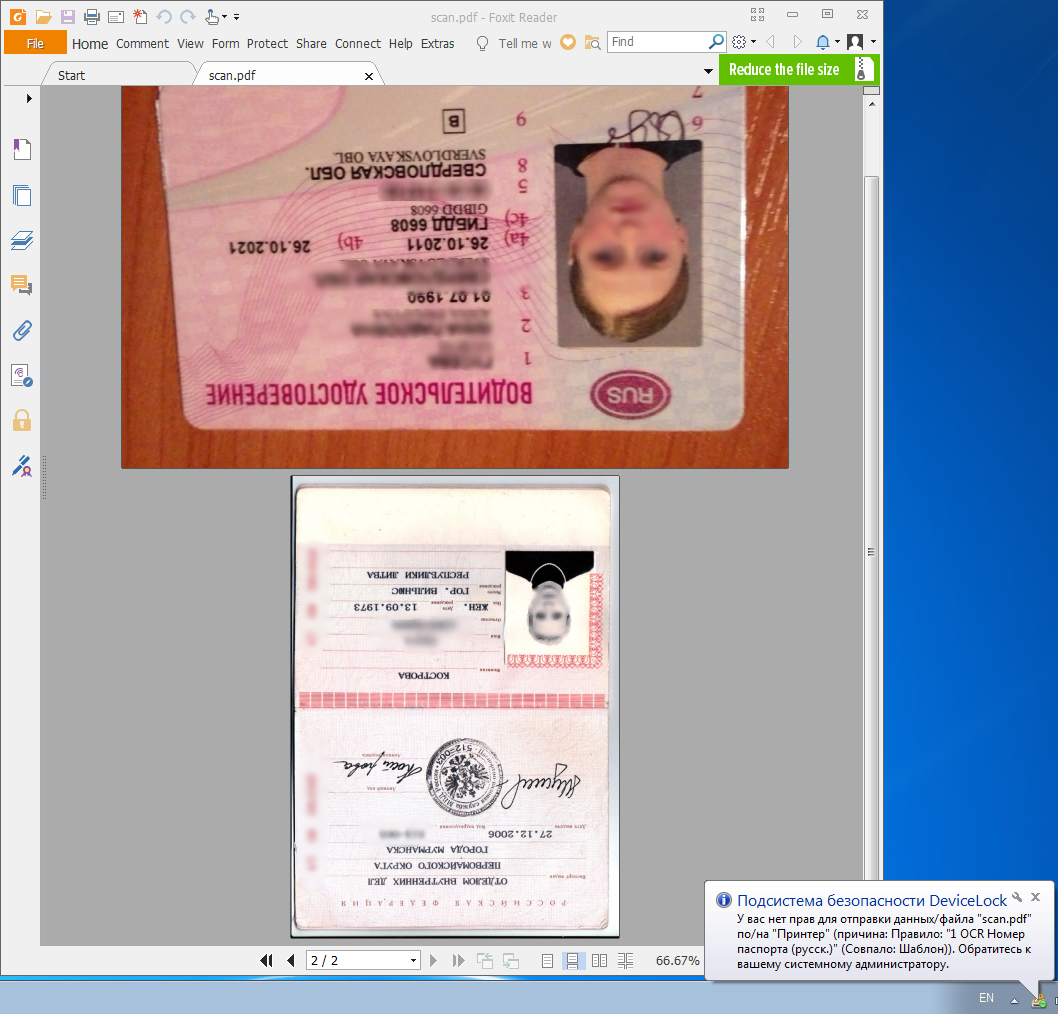
Block printing of an inverted scan of documents:
The summary results of the tests are as follows (clickable):
Anticipating the readers' question - “what was chosen in the end, because the title is“ experience of choice ”? Unfortunately, at the time of this writing, the guide with the choice has not yet been determined. We tried to fulfill our task - drove tests on a number of systems, provided test results to the management, and in the process decided to share with the Habra community.
Our opinion, I repeat, is subjective, built on personal impressions and determined by the task set, therefore our own choice will remain unpublished.
По большому счёту, поставленные задачи всегда первичны, поэтому всем, кто выбирает для решения своих задач DLP-систему, рекомендуем пройти по нашему пути и самостоятельно, отталкиваясь от поставленных задач, разобраться с возможностями предлагаемых систем. Надеемся, наши таблички будут вам полезной шпаргалкой.
Всем спасибо за внимание!

A little about the company: we are medium in size - about 300 workstations (on some work in shifts), plus for some of the employees we have remote access to virtual work environments via Citrix Desktop. As a side effect, some compliance was considered for 152 FZ and the corresponding organization for the protection of personal data.
We have no relation to the state; other branch regulatory requirements are also not affected in principle. The price of the issue and the procurement process in general is the business of the competent unit. Accordingly, the cost of the solution and the fashionable topic of import substitution did not limit us, and we could consider any development: both domestic and foreign. We (a small information security department consisting of as many as three people) did not want to fill in various questionnaires and forms from vendors and integrators, so we decided to refresh our memory with fact-checking (we already knew the DLP theme, but without much practical experience). This means using your own hands to test only those DLP systems that are either relatively easy (“without registration and SMS” and the company’s illumination before the seller) can be obtained for an independent test on their own stand, or can be viewed in the work of colleagues from other organizations. Important: Considering that further implementation and operation will be carried out on our own, we just wanted to test it ourselves on the stand, and not to watch the “properly debugged” demo versions “from the hands” and brochures to make sure that the declared functions are actually implemented and work as we need.
Systems based on monitoring applications, screen shots, keyboards, etc. they didn’t even try to watch - simply because they don’t solve the key task, no matter how their developers are positioned on the market. This refers to Stakhanovets and his clone from the Infofotch Person Monitor, StaffCop, TimeInformer, KickIdler and the like. This does not mean that these systems are bad - they just do not solve the key task “ to prevent leaks! ”Confidential data, but can be (possibly) a good tool for other tasks with passive observation.
They got acquainted with independent analytical and review materials ... they turned out to be sparse. From the readable - two publications on Habré ( one and two times ) and an already outdated and very superficial review on Anti-Malware with a separate comparison in tabular form.
We were interested in: foreign Symantec DLP, Forcepoint DLP, McAfee DLP, Sophos Endpoint Protection, Russian (or Russian) Solar Dozor, Zecurion DLP, InfoWatch Traffic Monitor, DeviceLock DLP, Information Security Circuit SearchInform, Falcongaze SecureTower.
As soon as we receive in our hands a distributive of a fresh version or an invitation to colleagues, the tests themselves of the declared functions and capabilities were carried out. As a source of additional information, publications and recordings of webinars of vendors and their partners were taken, as well as data from OBS agencies, that is, the expert opinion of colleagues with experience.
Immediately list what DLP-system failed to see.
- Solar Dozor (Solar Dozor). Well, a very heavy system. The descriptions have a strong emphasis on analytical capabilities. The developer’s website states “The modular architecture allows you to distribute the load and deploy Solar Dozor on any old hardware,” and according to the documentation you need to allocate a server with 8 cores and 32 GB of memory. And this is only to ensure the launch of the minimum configuration, plus put an additional proxy and mail server ... Apparently, our hardware is not that old :) They abandoned such resource consumers. Although rumored to be possible to run on the config 6 cores / 24 GB.
- Symantec DLP . From the first click on the site, a form opens with a bunch of questions and there is not a hint of a trial. Buy and try. Thank you, wrap back.
- Forcepoint DLP (aka
Websense ). There is also no hint of a trial on the site, but there is a form for requesting a demonstration in order to view it “from the hands of” the integrator. Again, thanks, but no. - Zecurion DLP . Again, no hint of a trial without sticking sales, or the ability to look at colleagues.
- Digital Guardian - generally impossible to get a trial.
- Another small list from the Gartner quadrant, which are too hard to get, and the “young” Russian products, which have not yet been seriously tested on the mass market.
The test results were summarized in a table of the type of function - system / compliance, it turned out quite a lot. They checked how each tested DLP performs the tasks set for a large range of data leakage channels, what other possibilities there are, how it works in principle with the system ... The test is, of course, not a full-fledged pilot, something could be missed, I apologize for it right away.
Separately, I emphasize that the opinion described in this article is subjective and is based on the personal impressions of the employees of one department following the results of a few basic tests and a general overview of the system. All conclusions are built from “fitting for themselves” and the fulfillment of the main task “to prevent leaks” is not claimed to be complete.
They checked simple things that directly correspond to the task: blocking the channel as such for specified users (“ this is not possible! ”); sending a shadow copy of the intercepted document to the archive; notification for IB when a ban is triggered.
Were checked:
- write to the USB flash drive;
- printing documents on the printer (local via USB and network);
- sending to SMTP and MAPI;
- sending to the webmail (viewed Mail.ru, Gmail, Yandex.Mail);
- sending to social networks (watched Facebook and Vkontakte);
- fill in the clouds (viewed Yandex.Disk and Dropbox);
- sending files through forms via HTTP;
- upload to FTP server;
- instant messengers: chat, file sending, voice or video chat (watched Skype, Whatsapp, Telegram);
- control in the terminal session (will it be triggered when pulling a document from the clipboard in a terminal session and when writing to a disk ejected from a remote workplace to a terminal session).
Upon successful completion of the basic test, an additional stress test was carried out with elements of load and complications for the analytical module of the system:
- A multi-level archive with a modified extension was sent through the channels to be checked, with an Ex-giant file of giant size inside, where the target text was hidden among thousands of junk text cells. Expected response to the specified words, phone numbers and email addresses of the company.
- Scanned printouts of a document on two pages, scanned by an ordinary multifunction device “upside down”, were sent through the channels to be checked. It was expected to trigger passport and driver's license numbers.
- The filled contract was sent through the channels to be checked, and the contract template was previously “fed” to the system.
As additional useful functions (in addition to verification of compliance with the primary criterion, see above), we looked at analytical capabilities, work with the archive and reporting. The function of scanning workstations (for example, how the system will find a document with passport data at the workstation) was decided to be postponed for another approach; now this task is not paramount (and critical in general).
The test bench is simple, as a server, a virtual machine with 8 GB of dedicated memory, as a guinea pig, a typical computer on i5 / 2.3 GHz / 4 Gb RAM and 32-bit Windows 10.
Well, here are some of the DLP systems that we managed to see and touch at our booth or at colleagues, and the corresponding impressions on them: McAfee DLP, Sophos Endpoint Protection, InfoWatch Traffic Monitor, DeviceLock DLP, Information Security Circuit SearchInform, Falcongaze SecureTower. To begin, I will describe general impressions, then a review of the actual test runs.
McAfee DLP
The tests got version of McAfee Data Loss Prevention 10.0.100.
At once I want to note that this is a very difficult system both in installation and configuration. To install and use it, you must first deploy McAfee ePolicy Orchestrator as your own management platform. Maybe for organizations where McAfee's ecosystem of solutions is fully implemented, it will be meaningful and convenient, but for the sake of one product ... pleasure from the category of dubious. The situation is somewhat facilitated by the fact that the user documentation is very thoughtful and describes the entire installation procedure, and the installer himself installs all the external components he needs. But for a long time ... Setting the rules is not an easy task either.
I liked: the ability to set conditional priorities for the rules, and then use these priorities as filtering events in the log. The filtering itself is very nice and convenient. The ability to give the user to send a file when banned, if it provides some kind of explanation (user-justification).
Disliked: the already mentioned need to install its own management platform, largely duplicating AD. Built-in OCR-module is absent, control of scanned documents is by. They identified a number of restrictions, such as email control only in Outlook (correspondence through The Bat! Flew past agency control), dependence on specific browser versions, and lack of control of correspondence in Skype (only files are intercepted).
Summary: At first glance, McAfee DLP seemed to us a very interesting solution, despite the shortcomings mentioned above. Grieved that the wizards for the task of the politician were gone - in the once studied old versions it was in our opinion more convenient than in the current web console. The key drawback is that almost all control is implemented through application control, and not at the protocol or driver level. Allows you to block flashing devices in a Citrix environment.
Sophos Endpoint Protection
The tests took the version of Sophos Endpoint Protection 10.
The solution is complex, the foundation is antivirus. It took a long time to install. The manual does not even specify the system requirements - for them, if you please the site. Policies are set based on per computer logic :(
I liked it: as in McAfee, it is possible to let the user send the file when banned. On this, perhaps, everything.
I did not like it: there are no difficulties in circumventing device control by an agent — stop the antivirus from Sophos, then enable the device driver in the Device Manager - and voila, full access to the prohibited flash drive. Somehow difficult and dull done with the implementation and configuration of content analysis rules, which in the end have not yet been implemented in fact. Surprisingly, there are no shadow copies. Notifications in the form of email alerting and SNMP messaging must be configured from the antivirus of the same developer. The list of monitored devices is poor, mail is controlled through embedding in email clients. Access control to the sites is made just like firewall. Built-in OCR-module is absent, control of scanned documents is by. The user manual is sad - no details can be found in it. There is not even a description of what is meant by this or that built-in rule - whether it is a dictionary test, or a regular expression ...
Summary: Unsuccessful, in our opinion, solution. In fact, this is an appendix to the antivirus, and even the complete absence of the possibility of creating an evidence base for incidents. Policies are not set by users, but by machines — this is unacceptable. Well, actually, from the free supplements to the antivirus a lot was not expected, but hope dies last.
InfoWatch Traffic Monitor
Perhaps the most promoted DLP complex on our market, which means we expected the most from it. Opportunities just to take and see - no, but the site is replete with beauty from marketers. It was difficult for the tests, but I managed to get the version of InfoWatch Traffic Monitor 6.9 Enterprise. Perhaps there is a newer version - but we don’t know about it, we didn’t find all the same marketing in kilotons. But the technical information on the site is somehow not enough. The test revealed that the documentation had the same problem - if something is unclear, it’s almost impossible to find the answer in the manual, there is no detail in general. This greatly reduces the possibility of self-exploitation.
It was pleasant: very high-quality, well-thought-out interface, with good structuredness. Convenient dashboards, where you can configure a specific query, the time of its update - and then continue to watch the whole picture. A good assortment of console widgets. It is possible to send a user request to provide access to the device straight from the agent module. Ability to specify different recipients for notifications depending on the type of event and user membership in the OU. A solid set of reports. Good opportunities to work with the archive, a large set of tools for analyzing the content of data in the archive is supported. There is a creation of screenshots from workstations.
I didn’t like it: in fact, it’s not just one product, but a bunch of Infowatch Traffic Monitor and Infowatch Device Monitor, and it works on two operating systems (Windows and Red Hat Linux), so installation and configuration for launching are complicated. There are also two management consoles. The widely advertised developer logic “checked content, only then we block, do not interfere with business processes” is actually somewhere in the bud. Content analysis for monitoring devices is simply not available - access to devices can be denied for users, there are whitelists, but they simply don’t know what is inside the document that is being written to the USB flash drive. For network channels there is about the same problem - content checking is implemented only for SMTP and HTTP. As they say, colleagues familiar with this decision for a long time, now at least there is an opportunity to block network channels - there used to be only monitoring. In fact - this feature is limited to HTTP, FTP, SMTP, plus file sharing and some instant messengers. I repeat, the possibility of blocking the transfer of data on the basis of checking their contents in, for example, instant messengers, no - only SMTP and HTTP. This is not bad, but not very consistent with the description in the brochures, and this is not enough to fully cover the leakage channels. The agent module is actually implemented as a mix of different agents.
Summary: In general, the solution looks (especially looks) very well. Device control at a basic level is good, for network channels monitoring is good, and blocking is satisfactory. In terminal sessions, allows you to deny access to the forwarded disks, or provide read access only, shadow copying works (for both flash drives and forwarded disks). The lack of content verification for most of the monitored channels, especially devices, is distressing, despite the fact that logic is stated in marketing documents. Let's hope that this is a kind of roadmap, and sooner or later, developers will catch up with marketers. In the meantime - PR five, the developers of the troika with a plus. Or vice versa. How to look.
DeviceLock DLP
The tests were taken version 8.3 (last updated, released in December 2018), downloaded by the developer site.
A fairly highly specialized system, only protection against leaks and nothing more - no screenshots, application controls ... However, if you believe information from webinars from the developer, user control functions should appear through screenshots in the foreseeable future. Installation is easy. A lot of management options, old-school consoles, to work with them you need at least some experience of a sysadmin - then everything becomes obvious and simple. In general, the impression is very simple to operate the system.
It was pleasant: detailed elaboration in settings of controls. Not just conditionally control, for example, Skype — but separate control, events, shadow copies, alerts, content checking — and for separate Skype components — chat, files, calls ... The list of monitored devices and network channels is reasonably built, and quite large. Built-in OCR module. Content locks do work, albeit with some workload on workstations. Alerts can come almost instantly. Agents are completely independent with respect to the server part, they can live their own lives, as required. An automatic switching of modes has been done - you can safely let an employee go with a laptop, the politicians will switch themselves to other settings. Blocks and monitoring in the system are still divorced at the console level - there is no difficulty for some channels to turn on the ban for individual comrades, and for other comrades to set the settings only for monitoring. Also, the content analysis rules look independent and work both on a ban and vice versa on the resolution of transmission with the channel closed in principle.
Did not like: no wizards. To set up a policy, you must immediately understand what you need to get, go to the appropriate section of the console and poke ticks, select users, etc. Пошаговый вариант создания политики напрашивается. С другой стороны — можно проверить, что реально задано в плане контроля. Поиск по архиву ограничен полнотекстовым поиском по содержимому теневых копий, поискать по шаблону документа или с помощью словарей возможности нет. Более-менее выручает развитая система фильтров, но это далеко не контентные фильтры. Неизбежная нагрузка на рабочие станции при работе контентно-зависимых правил (терминология разработчика).
Резюме:The system is easy to operate, clearly working, with a rich arsenal of features to protect against information leakage. According to the apt remark of one of the colleagues, it was made according to the principle “set up and forget” Given that all policies are set per user, to change the available operations for a user, it is enough to simply transfer him to another domain User group for which different control rules are configured, from simple controls to rules with content analysis. In terminal sessions, it allows you to set access rights for the forwarded disks (blocking or read-only), for the clipboard (everything is quite flexible depending on the direction of copying, on the type of data being transferred), shadow copying works, blocking by content when writing to the forwarded drives and when transferring data through the clipboard.
Information Security Contour SearchInform
We looked at our colleagues, so the dates were very tight. At first I wanted to write “I got the XXXX version for tests”, but I could not. Just because KIB Searchinform is not a system, but a
I liked it: the power of working with the archive is well developed. There is everything. A lot of criteria, dictionary search tools, regular expressions, fingerprints, corporate “similar search” ... There are tags for different incidents - you can mark already viewed, for example. There is a transparent encryption flash drives.
I did not like it: chaos in the logic of system control, which goes beyond the number of control consoles. No blocking for network channels. The absence of locks on the content for the entire set of "intercepted" channels.
Summary: Device locking is implemented at a decent level, for network channels - at a rudimentary level. In terminal sessions, you can set permissions for the forwarded disks (blocking, read only), shadow copying for the forwarded disks works. In general, the system is quite difficult to operate, strongly focused on investigating incidents - that is, monitoring and working with the archive. For this there is, perhaps, all that is needed. Protecting an organization from data leaks is clearly not here, unless you close devices you don’t need.
Falcongaze SecureTower
The tests got version 6.2. Two key words describing this system, if you do not go into the nuances - it is easy, convenient. Easy to install, conveniently managed, convenient to watch reports, convenient to work with the archive. Documentation is practically not required. Then the focus begins again with the word "interception", as in the CIB. Interception here is just for monitoring, that is, a shadow copy is being created, there is practically no blocking (except for HTTP, SMTP and MAPI). There are screenshots from workstations and some other functions for monitoring user activity.
Liked:friendly user interface. Everything is done for convenience. A good tool for viewing and analyzing the archive, successfully implemented a graph of links. Almost from any report you can go to the event (incident) specified there. Incidents can be assigned categories (investigated, unexplored, deferred). Monitoring Telegram and Viber'a.
Did not like: the lack of locks for network channels. The inability to lock printers and disks thrown into a terminal session. The absence of locks on the content for the entire set of "intercepted" channels. Low stability of the agent - unpredictable hangs and the appearance of dumps were noted. Unexpected console hangs even when working with the archive.
Summary: The system is very easy and convenient to install and operate, but sharpened to monitor and work with the archive. There is a feeling that the system is somewhat damp, OTC is not working.
Test results
As mentioned above, the results of the basic tests were tabulated. Parameters that can be assessed subjectively were estimated conditionally, according to the “traffic light scale” - in color.
Actually the table looks like this (clickable):
Stress tests were performed only for McAfee and DeviceLock DLP. In other cases, there was simply no point (see the table below).
At McAfee correctly worked ban archive with Excel file.
The test with the interception of the scan in McAfee did not go - there is no built-in OCR.
With checking on templates - it works only with full compliance, if the document is changed - the DLP system skips it.
At DeviceLock DLP all tests worked completely. Amended agreement, interception in Skype:
Writing to the flash drive archive with a littered Excel file:
Block printing of an inverted scan of documents:
The summary results of the tests are as follows (clickable):
findings
Anticipating the readers' question - “what was chosen in the end, because the title is“ experience of choice ”? Unfortunately, at the time of this writing, the guide with the choice has not yet been determined. We tried to fulfill our task - drove tests on a number of systems, provided test results to the management, and in the process decided to share with the Habra community.
Our opinion, I repeat, is subjective, built on personal impressions and determined by the task set, therefore our own choice will remain unpublished.
По большому счёту, поставленные задачи всегда первичны, поэтому всем, кто выбирает для решения своих задач DLP-систему, рекомендуем пройти по нашему пути и самостоятельно, отталкиваясь от поставленных задач, разобраться с возможностями предлагаемых систем. Надеемся, наши таблички будут вам полезной шпаргалкой.
Всем спасибо за внимание!
Source: https://habr.com/ru/post/440838/