Security Week 08: Hacking VFEMail Live
 News about serious vulnerabilities in software and hardware appear every week. Only in the last seven days, it was reported that XSS was used in the Vkontakte social network, Zero-Day was eliminated in Windows, and a little earlier, the bug in Android allowed for hacking the phone with a prepared PNG image. But we rarely see the consequences of exploiting these vulnerabilities: for obvious reasons, affected companies are in no hurry to share such information. Even less often, one can observe the consequences of the attack almost on the air, which happened last week with the VFEMail mail service.
News about serious vulnerabilities in software and hardware appear every week. Only in the last seven days, it was reported that XSS was used in the Vkontakte social network, Zero-Day was eliminated in Windows, and a little earlier, the bug in Android allowed for hacking the phone with a prepared PNG image. But we rarely see the consequences of exploiting these vulnerabilities: for obvious reasons, affected companies are in no hurry to share such information. Even less often, one can observe the consequences of the attack almost on the air, which happened last week with the VFEMail mail service.This service was founded in 2001 by a resident of the United States, and since then has served private clients (offered only 50 megabytes of free space for letters for free) and organizations on their own domains. In 2015, he was mentioned along with the ProtonMail protected mail service as a victim of extortionists - the owner of the service quoted the demand of the organizers of the DDoS-attack to pay five bitcoins. On February 11, without preliminary threats, the attackers erased the information on all the main and backup VFEMail servers, literally in a few hours, destroying the company's business almost completely.
In the list of mail service rates, the most expensive option offers 15 gigabytes (elsewhere on the site 20, readings differ) for $ 50 a year - as much as Google Mail gives for free. Or a one-time payment of $ 25 per 1 gigabyte of mail forever. Accepted payment in cryptocurrency. VFEMail does not position itself as protected mail, offering fairly standard options such as spam filtering, checking for virus attachments and access from mail programs. And: "We do not read your letters to sell you advertising."
In general, it was such a post for those who started a mailbox a hundred years ago and have been lazy since then to move somewhere else. It is a working scheme, if not the events of February 11. It all started with this message on Twitter email service: the owner noticed that he had serious problems.
After another two hours on one of the servers, the owner saw live, as the attacker erases the data:
The mail service was attacked from a Bulgarian IP, most likely from a rented virtual machine. After a few more minutes, it became clear that this was not the only server attacked:
An hour later, the founder of the service probably diagnoses a total loss of all user data:
Several servers were attacked at different sites in different countries. According to the owner of VFEMail, different methods and authorization keys were used on the servers, and yet they were hacked, followed by the destruction of data, almost simultaneously. After a week of downtime, the owner of the service managed to restore one of the servers with data for 2016:
In the comments to the website Bleeping Computer, the founder and sole owner of the email service, Rick Romero, said that he had not received any threats from anyone, unlike the situation with the DDoS attack in 2015. Most likely, the service will not be restored, although the clients were still able to receive and send mail without access to archived messages for the past two years or more. Journalist Brian Krebs on his blog cites testimony from VFEMail's corporate client: ten years of postal correspondence and more than 60 thousand messages have been lost.

Interestingly, on the VFEMail website, there was an argument in favor of a third-party mail service compared to its own mail: this is more reliable, all the security settings have already been taken care of, and you do not need to accept incoming connections on your own network.
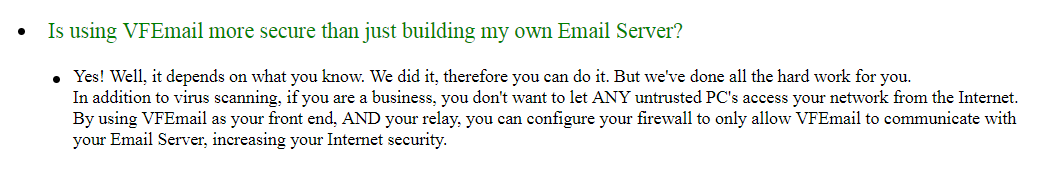
All the arguments are correct, although in the end the “professional” service experienced a completely user-generated catastrophe — when all the infrastructure included in the network was destroyed and, most likely, there were no offline backups. In the comments above, the owner of the service cites another reason for refusing to restore: even before the hacking, the postal service was not particularly profitable. A blow to reputation, the cost of restoring infrastructure, and most importantly - the cost of subsequent data backup and additional protection will make the business completely unprofitable.
In a sense - sorry. VFEMail appeared at the sunset of the romantic era of the Internet, when the current giants were garage start-ups with a similar security level. Further development of cyber attacks made the costs of protection unaffordable for all who did not have time to become large enough. Although we do not yet know exactly how we managed to crack the postal service (and perhaps never know), this story is a sad example when a company is not ready either to repel a cyber attack or to overcome its consequences. And if there are problems with the first companies with the largest companies, the inability to recover from the cyber-attacker is just the situation that should be avoided by all means.
Disclaimer: The opinions expressed in this digest may not always coincide with the official position of Kaspersky Lab. Dear editors generally recommend to treat any opinions with healthy skepticism.
Source: https://habr.com/ru/post/440918/