Benefits of analyzing level 7 applications in firewalls. Part 2. Security
The new generation of firewalls is more convenient and safer, thanks to the new architecture of the engine and the new ideology of managing network flows.
Why did this article appear?
Repeatedly I came to security colleagues who use the firewall of a new generation and saw that they continue to write rules for port numbers. On my proposal to write by the name of the application, I heard, “What if it doesn’t work?”. If you are also “scared” or do not understand why writing rules on applications, from this article is for you.Begin the article by link Part 1. Firewall Basics
Part 2. The impact of L7 FIREWALL on security
Content
L7 firewall checks the contents of the data field, L4 firewall does not
Applications have changed - has your firewall changed
How application detection works in traffic
L7 Firewall is more convenient
L7 Firewall is safer
What new problems creates a new approach to writing rules on L7
Limitations of technology analysis level 7
Conclusion
Voting
L7 firewall checks the contents of the data field, L4 firewall does not
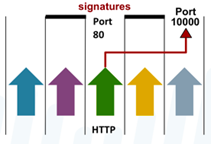
The main problem with which we struggle is that now the programs are immediately written so that they bypass the L4 firewall protection.If a person puts Skype, then he does not want to call a sysadmin and urge him to open the port on the firewall he needs - he wants Skype to immediately light up "green." Programmers know that the network often has an HTTP proxy or port 80 is open for HTTP, port 53 is for DNS, port 123 is for NTP, and it can be open to employees from the outside to the Internet, and accordingly these allowed connections can be used.
The developers have the term User Experience - after the installation, the client caught on Skype with a greenback = the client is happy. And the fact that Skype went through the company’s perimeter illegally over a connection that was open to work only with a browser on TCP / 80 and 443 ports — the L4 firewall ignores because it’s not his task to look into the contents of the packets — all that matters is their header.
Problem L4 firewall: port-hopping (tunneling)
 Tunneling of unauthorized applications within allowed connections is a standard picture in modern networks. Naturally, hackers use the same technique: they create tunnels in allowed connections. And bezopasnik even not in the know.
Tunneling of unauthorized applications within allowed connections is a standard picture in modern networks. Naturally, hackers use the same technique: they create tunnels in allowed connections. And bezopasnik even not in the know.TCP-Over-DNS Tunnel Example

By the collected packets of traffic in the picture you can see that connections are going on TCP port 53, which is usually considered as the DNS protocol operation. However, if you look closely, you can see that in the Text field of the DNS protocol there is some kind of encrypted text. This is the implementation of the TCP-Over-DNS tunnel, which I often see in corporate networks. On the left is a list of other tunnels that your users or hackers can use. Does this information give L4 firewall? Not. Therefore, if you need to protect the company from unauthorized tunnels, then you need to analyze the contents of the transmitted data and analyze which application is currently using this TCP connection.
Applications have changed - has your firewall changed

The world has changed and today it is not enough to define an application by port number. Yes, 20 years ago we agreed that if 80 is registered in the Port field, then this is HTTP, if 53, then this is DNS, but now this is no longer the case!
It is necessary to analyze the contents of the transmitted data, and it is for them to analyze which application is currently using this TCP connection.
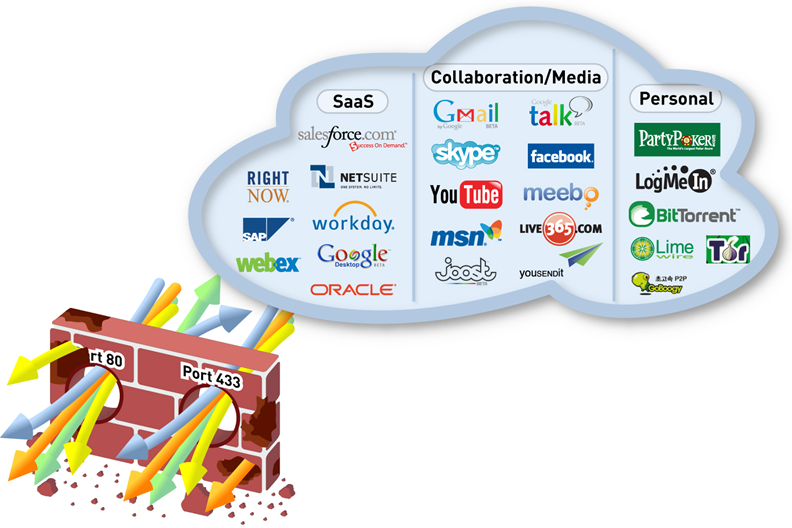
Go to the application database applipedia.paloaltonetworks.com . See how many applications port 80 and 443 are using.
Example.
Applications using port 80
The problem of many security tools - ignoring applications on non-standard ports
Moving a standard application to a nonstandard port also allows an attacker to get out of control. This control restores only the device that analyzes the contents of all traffic, and not just the headers.
How application detection works in traffic
One of the tasks of analyzing applications is to detect the traffic of applications that are specifically designed so that their connections are not seen. Take for example Skype. People who have learned to distinguish Skype encrypted UDP packets from other encrypted UDP packets are great guys.
There is also a class of devices that can do this: Deep Packet Inspection (hereinafter referred to as DPI). Such devices now stand with large providers and allow you to manipulate the traffic of applications: use QoS or redirect in the right direction. Sometimes NGFW and DPI are compared. Difference: DPI is designed to control the quality of traffic, and NGFW security, although NGFW also has QoS features.
Application detection methods in traffic are different.
- If you need to find an application that does not hide itself in traffic, such as HTTP, then it is enough to use the usual search for the corresponding patterns or signatures. And it is actively used by manufacturers. This is the easiest.
- If you need to find an application that intentionally hides itself , for example, TOR, then you need a set of methods for analyzing packet statistics and packet behavior. It is difficult, it requires a research laboratory, which also has to track changes in the protocol in time and implement new search algorithms. My attempts to force at least one developer to tell how these algorithms work, come across the answer that this is all intellectual property.
It happens that the application has already changed the algorithm of work, and the DPI or NGFW engine has not yet had time to change. For example, Telegram sometimes changes, because they are being hunted for. False positives occur. It is important to check. Accordingly, the devices and NGFW and DPI differ primarily in the number and quality of detection applications. Here is the only method: put NGFW on your traffic and see. If we talk about the perimeter, the most complex traffic that I saw contained 715 different applications in a month. On average, 200-300 applications of various kinds run through the perimeter. In this visualization of application traffic, you can see this: move your mouse over each circle:
http://researchcenter.paloaltonetworks.com/app-usage-risk-report-visualization/

There are thousands of applications in the application database, so in fact the analysis of the formats and algorithms of each application is a long and painstaking work of analysts. After they understand how the application works, programmers start working who implement application detection by traffic. And these few thousand applications are constantly changing. Accordingly, the product should be constantly maintained, study new applications and monitor changes in old ones and add modified detectors to the database. The base of all possible applications that generate traffic can be found here .
Sometimes L7 firewall vendors try to measure the number of applications they have in the database, but this is more like a profanity. By turning on critical thinking, you understand that you really only need to detect applications on the perimeter (on average, around 300 different applications), in the data center (10-15 pieces), in ICS / SCADA networks (2-3 applications), between internal segments (maybe it's just a few dozen). And if you are offered to detect thousands of applications - this is just marketing and detecting some unknown applications that nobody uses.
Sample applications in the company's network:
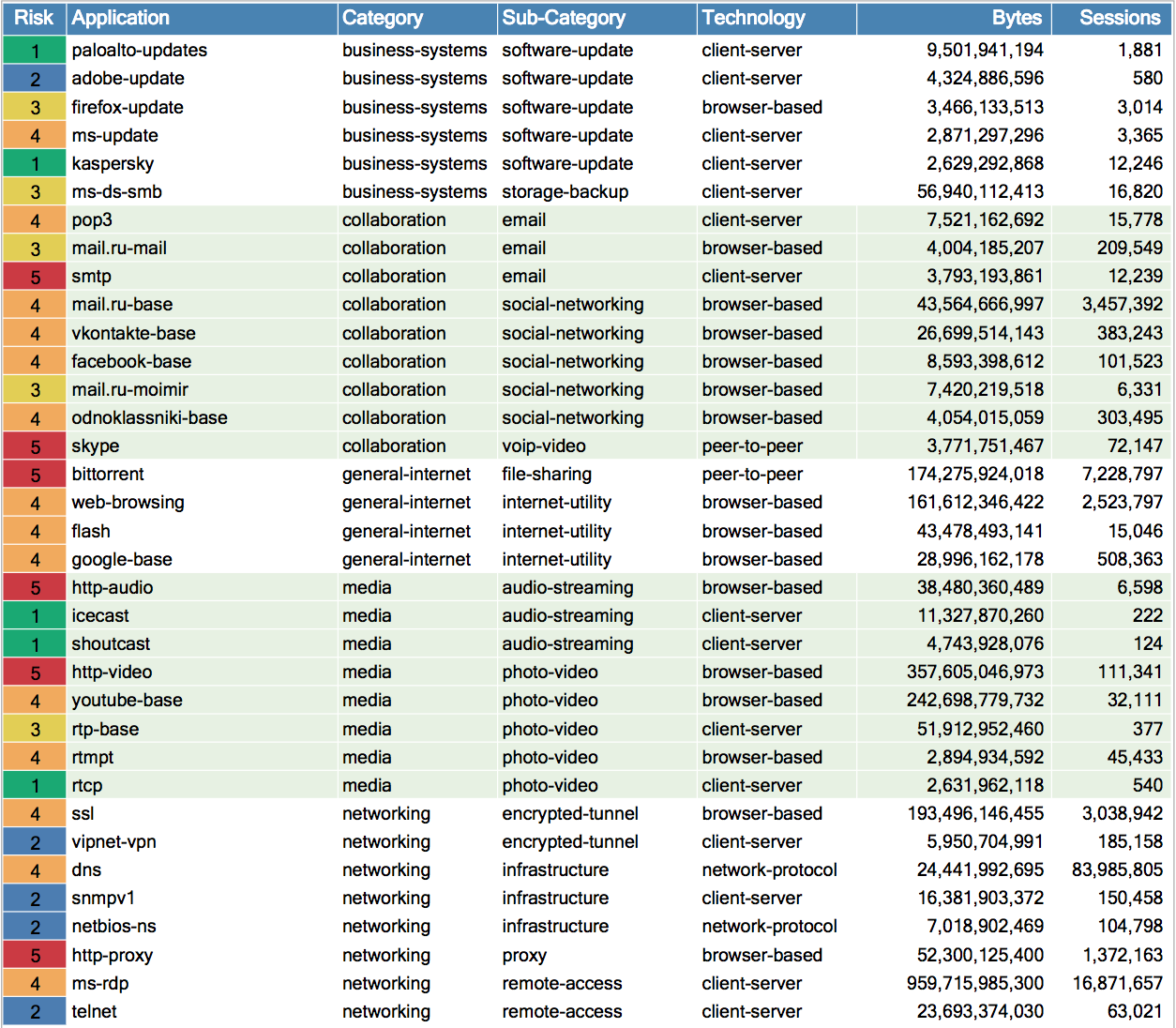
Internal segmentation within the company is a constant requirement of information security standards that almost no one performs. Between the segments where programmers are sitting, financiers, HR and accounting are also applications. At a minimum, you need to control the Windows network (SMB protocol), this became especially clear after the outbreak of the crypto-fiber WannaCry, which was distributed via SMB. That is, in the internal networks, there is also a need for analysis of applications of the 7th level and associated methods of searching for malicious code by the sandbox and IPS, and at least control of the transmitted file types.
The most common problem that is noticeable in networks: a firewall supposedly level 7, but in reality detects applications by ports. How to check it?In Russia, it is still important that firewalls know the traffic of Russian applications: 1C, Odnoklassniki, Yandex.Disk, mail.ru, how the updates of Kaspersky antivirus look, and so on. This is also an important component of application discovery that is needed to safely allow these applications to its employees.
- For the test, hang the FTP server on port 25. If the device is wrong and says that it is the SMTP protocol, then this is definitely not a L7 firewall.
- Or just try to write rules for two different applications that use the same port. Make different rules for them: block exe files in one, allow them in the other. If it turns out to be done, then it means the truth is first parsing the application (and not the port number), and then working with its content: locking files, checking virus signatures, checking IPS signatures, and so on.
- Another interesting test for NGFW is when you need to make two custom L7 applications with different properties on the same IP address. This can not L4 firewall, but can L7 firewall. Full description and the test itself here: http://basic.ngfw-test.com/
L7 Firewall is more convenient
If you look at the process of training network engineers, then most often people take courses from a well-known network equipment manufacturer and this gives a good knowledge of network technology.

The author of these lines finished a decent amount of Cisco courses in 2003 and therefore presents the features of training network engineers: as a rule, after studying the seven-level OSI ISO model, only the first 4 levels are studied in detail. That is, network engineers know all the subtleties of information security only to the TCP / UDP / ICMP level. From the application level, only a few basic ones are considered: HTTP, DNS, SSH, Telnet, NTP, FTP. What result? And the network administrator has the feeling that managing the application layer is easy from the transport level!
It may seem to the newly baked network specialist that everything can be done by the rules at the transport level, where you just need to allow the necessary protocol and port. Need to allow a browser to the Internet? Open TCP / 80. Need to open DNS? Open TCP / 53 or UDP / 53. Need to open RDP? Open TCP / 3389. And writing rules on the L4 firewall is becoming the standard in the company.
I must say that many IT specialists are aware of the concept of statefull inspection. But at the same time for many it is a revelation that different firewall supports satefull inspection for a different set of applications. I have certain statistics, because I worked as a Firewall course instructor at the Informzaschita training center. What do I see? Someone thinks that statefull inspection is only about permission to receive back the responses of TCP / UDP / ICMP protocols. And what about more complex applications? For example, how to track the two TCP connections that the FTP protocol does on ports 21 and 20 - do they depend on each other? There you need to not only accept the answer, but also allow the second connection depending on the PORT command inside the control connection on port 21. And how many more teams to open new connections within themselves give the application? Summarizing, networks now use regular access lists that do not understand the PORT command inside the FTP protocol, and there is an L4 firewall that parses the PORT command and automatically opens the correct port, is there anyone who went ahead and looks into more complex commands of the MS RPC or ICS protocols / Scada protocols. But all possible L4 firewall applications do not look, and these firewalls also differ in the number of applications implemented inside the Application Layer Gateway (ALG).
What am I getting at? The conviction that it is enough to remember the main TCP / UDP ports does not work.
There are already several thousand applications in the world and they all use computer networks. And no network engineer is able to remember all these ports.
Revelation for network engineers is the task of opening ports for an application more complicated, for example, VNC. No one remembers what ports there are and you have to use google.
When I published the first part, I conducted a survey and I see that people are still ready to memorize port numbers - opinions were divided 50 by 50: someone replied that he was ready to remember all 4 ports of the VNC application.If you take a look at Microsoft TechNet, which describes which ports you need to open, you want to write a rule to permit any to any, because there are about 40 ports and some of them must open dynamically. And it is disastrously inconvenient to register in the L4 firewall.
Perhaps the record for the number of ports is Lync (aka Skype for Business). About 40 ports. Is it possible to remember them?
It turns out that it is more convenient for the network engineer to write in the rules of the L7 application and it is necessary that the firewall itself automatically open the necessary ports.
Need to open a VNC? You write the word VNC in the rule and already the firewall understands which underlying protocols you need to open. This is convenient.
Example. NGFW report for specific traffic categories.
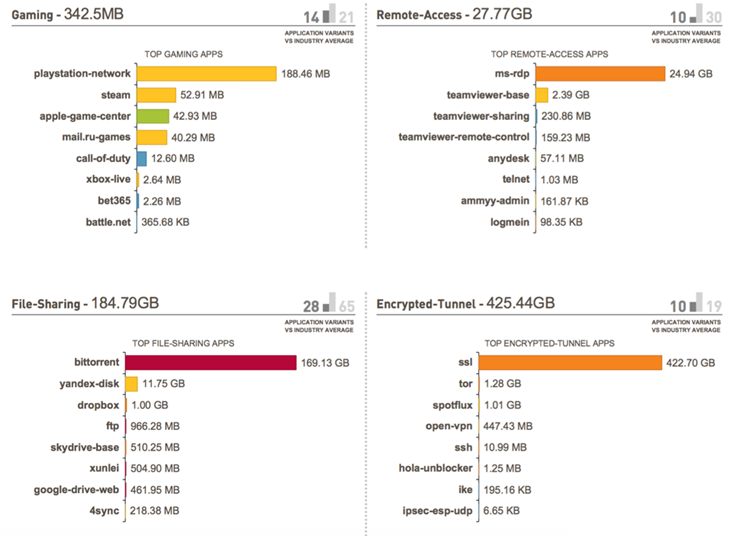
On average, 200-300 applications use the Internet access from the corporate network. Application-level firewall shows which applications it is and can filter these applications for all or for specific users and filter files by types or content that run in allowed applications for all users of the corporate network. Also, do not forget that in NGFW, security functions work in parallel: IPS, antivirus, anti-spyware, URL filter, DNS filter, Threat Intelligence, and so on. That is, we do not just allow applications, but do it safely.
L7 Firewall is safer
I have Palo Alto Networks NGFW on hand. I wrote three different rules on it. Let's see how they differ.
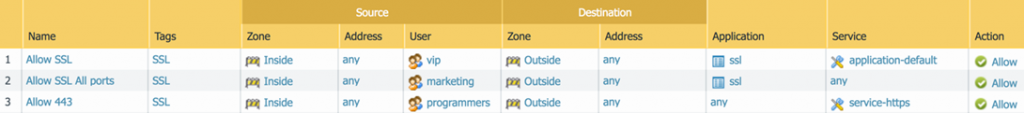
If you have ever set up a firewall, then you can see that for different groups of users: vip, marketing and programmers, I allowed SSL in three different ways.
- vip users will be able to walk on port 443 and will be able to use SSL inside it , since it is the default port for SSL. If they try to go through port 443, for example, using regular telnet, then they will fail - the firewall will check that it is not SSL and will block it. And this is what you need!
- marketing can go on any port with an SSL application , because any port is allowed in the Service field, where ports are specified. The question is, did I want marketing to use SSL over non-standard ports? Not. This is a common setup error. It is logical to specify the port as any if the rule prohibits - that is, if we want to disable SSL on any port.
- programmers can walk on port 443 with any application , which is actually a hole, because I initially wanted to open only SSL. And this is exactly how the L4 firewall works - it opens the port and after that, it’s like what the application is and what port it is. Any programmer from the programmers group can use any tunnel.
Setting up the application-default is very important and allows you to reduce the number of rules: you can specify the desired applications in one rule in the Application column and the firewall opens the necessary ports for the necessary applications and skips only those applications that need to go through these ports. Accordingly, you need one rule to open several applications.
For example, for the rule below, where all employees are allowed to go to the Internet only by default ports, NGFW will constantly check that they only want the DNS client on port 53, and not TCP-over-DNS. And of course, this increases security, because you do not just allow applications, but control that only the applications that you allow go through open channels.

What new problems creates a new approach to writing rules on L7
It is necessary to understand that the definition of an application based on the content of the package is very load on the L7 firewall processor. If a regular L4 firewall checked only a few bytes of the TCP packet header and then skipped the remaining megabytes of the flash movie without checking, then the L7 firewall should read everything that is stored in the TCP / IP data field and constantly check what content is inside the TCP / IP connection, all of a sudden it has changed or is a threat to the company. Therefore, when such functionality as content analysis appeared, all devices began to slow down. Therefore, to analyze the content, we need more powerful devices.
Limitations of technology analysis level 7
L7 firewall requires more memory to store the state of one connection, so the parameter “number of simultaneous connections” for L7 firewall is always lower than that of L4 Firewall with the same amount of RAM in both devices, and significantly, every 10. This has already been explained above in the Statefull section Inspection. And this is the price for the security of your applications. Therefore, if you compare the L4 and L7 inspections, then ask the manufacturer how he measured the parameter “number of simultaneous sessions”: with security turned on at level 7 or off.
The same is true with performance: the L4 firewall processor checks only a few bytes of the packet header and then sends the data itself at routing speeds without checking, and the L7 firewall checks both the header and all those megabytes of data that are contained in subsequent connection packets. And this is a completely different job. Therefore, such work needs to be done on specialized for this hardware platforms, where application analysis is accelerated, streaming antivirus is accelerated, IPS and other security functions are accelerated. Best of all in the creation of chips to speed up security succeeded Cavium, the chips of which, for example, is used by Palo Alto Networks. In addition, the use of specialized FPGA chips (FPGAs) allows you to flash the antivirus signatures and IPS into the chip itself and the signature verification goes at the hardware speed of the FPGA chip. Now even personal computers have accelerated graphics functions on dedicated graphics processors, so using chips to speed up security is a logical development of technology.
Conclusion
First , it is easier to manage security on the L7 firewall. Previously, you read the application manufacturer’s documentation for a long time and opened the ports listed there. Now it's simple: you specify the name of the application in the NGFW rule and the necessary ports will be automatically resolved depending on the connection status of this application.
Secondly , you will be able to detect and block tunneling, since the L7 firewall safely allows only an explicitly specified application and if someone tries to tunnel another application through an open port, it will immediately be detected and blocked.
Thirdly , you can allow the necessary application on any necessary port and only the necessary application will go on this port, but not all at once. For example, only a web browser will use port 80.
Part 3. SSL decryption in NGFW. (to be continued)
Good luck!
Denis Batrankov
denis@batrankov.ru
Source: https://habr.com/ru/post/436836/