Adams State University. How to hack websites. Part 2
Adams State University. How to hack websites. Part 1
Let's talk about our next attack. Let me tell you how the servers identify you. To do this, the stateless HTTP protocol is used between the browser and the server, when communication with the server is performed by independent “request-response” pairs. Therefore, the server forgets you as soon as the connection is established, and during the next session it no longer remembers who you are.
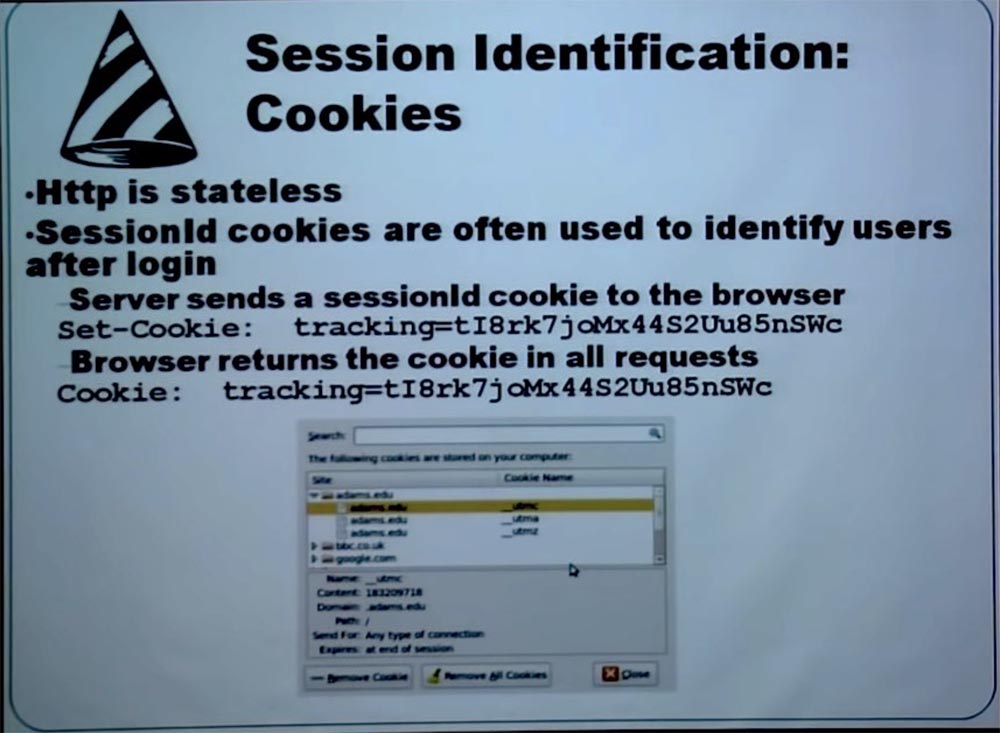
However, he remembers you while you are using the web application, because when you put into the basket the things you are going to buy, you can continue shopping and return again to view the contents of your basket. The implementation of the "memorization" occurs with the help of session identification cookies. As soon as you log in to the server, it generates a cookie, which is a unique sequence of letters and numbers, and sends it to your browser, which stores this cookie locally on your computer. After that, the browser returns the cookie to the server with each of your requests for one session. Receiving these cookies, the server understands that the user accesses him with this request. This is the most common way to identify a user who uses a web application.
The next type of attack is called cross-site scripting, XSS. The idea behind this attack is that the attacker forces the website to display malicious code, usually in the form of JavaScript, which is then executed in the user's browser. Such an attack can pursue any target, but is most often used to obtain the victim's session identifier. The value of the Session ID is that it can be viewed as a password, as it identifies you. By capturing a session identifier, an attacker can disguise itself by using a proxy server to communicate with the target server. The objectives of such an attack may be the desire to speak on your behalf, to automate some actions, such as spamming, on your behalf, or to inject a virus.
When searching for XSS cross-site scripting vulnerabilities in a web application, you are looking for an input field in which you can put some information, send it to the server and see what result is displayed in the browser window.

I enter the wrong location of the building, indicating Plachy Hall, the address of the hall of the basketball team of our university. The web server receives this information and realizes that a computer science professor is a “bot” who cannot live in the location of a sports team, and gives an error message: “Plachy Hall is wrong”!
The search boxes are most vulnerable in this respect, where you can type in some rather vague terms, and then see what you get in return. Most often, you are given a hint with a list of possible correct options that an attacker can use.
The next thing you need to do is check whether you can inject your malicious code and then execute it. We will try to organize XSS attack using JavaScript.

JavaScript code is always highlighted by opening and closing the script tag, as well as the OR operator. Application developers are not completely stupid, so they installed a filtering mechanism called "disinfection." It is embedded inside the code, checks for dangerous characters, and deletes them if possible. The simplest JavaScript "disinfection" test looks like this:
But hackers are a bit smarter, so they have the website ha.ckers.org/xss.html . I don’t have time to show you this site, but there you can find the most sophisticated ways to circumvent the controls that application developers have tried to insert into their programs to remove dangerous characters. So there are quite ingenious ways to allow a hacker to get inside the application.
So let's talk about how the XSS attack will take place. We have a web server "Faculty pages" where we are going to enter a malicious code. We have Eve, who is going to make a hack, but we missed something on this slide - we forgot about the victim. What is good about a XSS attack is that you don’t need to hire anyone. I mean, this time I'm not going to be a victim, because Eva has my password and she can do anything she wants with my account. Therefore, Eve comes out of the big game and no longer chases the little boys. Let's take our victim to the scene (audience laughter, because a picture of one of the faculty’s professors appears on the slide).
Now that the victim has taken his place, let's see how the attack develops. Suppose that Eva was able to place the malicious JavaScript code on the server where our victim is going to log in using her account.
This is important, because as soon as the victim logs into the server, she will receive a session ID, which Eva will try to intercept, this is a very important part of the attack. So, the victim requests a web page that contains malicious JavaScript code, this code will run in the victim's browser and send the session ID to Eve.

After receiving the session ID, Eva can use her proxy server and do whatever she wants, disguised as a victim. The only missing piece of the puzzle is malicious JavaScript itself, which a hacker must insert into the page and which must capture our victim's session ID and transfer it to the attacker.
It is very simple. We have a javascript code that begins and ends with the opening and closing of the tag:
The first line of code creates a drawing in the same way that a picture is dynamically created in JavaScript for any page. You know that at the heart of any image is the file that contains the image, so we need to tell the browser where to go to get this image. This is indicated in the second line, where the link to the hacker's website is located, but the browser thinks that this is exactly the place where the desired image is located. He will go to the Eva website and ask for document.cookie, because he believes that this is the image file he needs.
But this is not a picture file at all, but a session identifier that we are trying to capture using JavaScript. As you can see, getting a Session ID is pretty easy. The third line, which is not used in the code for the XSS attack, is the alarm that triggers a pop-up window in the browser with a message about the attack. This was done specifically for our example, because the real XSS attack takes place completely unnoticed by the victim.

So let's invite Eve and see how she will perform a cross-site scripting attack.
Eve Hacker: thank you, Dr. Loveland! The first thing I have to do is close a few things that we don’t need. We no longer need the Burp Suit proxy server, so I close it. Secondly, I need to reconfigure the web browser and switch it to use the default system proxy settings.
Now let's go to the login page of Dr. Loveland, because if you remember, I have her password and I can enter the site at any time instead. As I mentioned, Dr. Loveland is rather lazy, she uses an expired SSL certificate, so I have to confirm the security exceptions to go to the login page. Since I know the password, I can edit its web page. As we already know, on the personal information editing page there is a vulnerability in the Building Location line, "Building Location", and it is here that I am going to enter my malicious JavaScript.

I have simplified this attack, so in reality I will not send the code to the server, but instead I’m calling a pop-up window with the message that someone is trying to attack me. Now that I have set the stage for the attack, I will return to the login page and log out. Now you just need to wait for the victim to appear who wants to use this application.

(Eva puts on a baseball cap, depicting faculty professor Stephen Eldridge)
I just returned from a fascinating meeting, where we discussed after hours what car should take priority in the parking lot - Subaru or Jeep, and then the thought occurred to us that the difference could be in the presence of the sunroof. So now I need to log in and check my contact details, because I would not want to miss the next out-of-class meeting because my data was not available. So, I log in to my web application under the login saldrich and my password.

So, everything looks as usual, I do not see anything bad on my page of a professor of mathematics, all contact information is in order.
Oh, my God, my watch shows that until the next meeting there are only 2 minutes left! Now I'm going to meet Dr. Loveland, so I need to go to her page and see if I can dig up some compromising information on her to mention him at the meeting. So, I click on the link Susan Loveland, get on her page and ... Dr. Eldridge, your page is hacked!

(Professor Eldridge removes the baseball cap, turning into Eve)
Now that I have your Session ID, I can use my proxy server and disguise yourself, Dr. Eldridge, doing whatever I want on your behalf. I give you my word, Dr. Loveland!
Susan Loveland: thank you, Eve! I wanted to mention that our Faculty Pages application was developed based on one of the newest web frameworks - the Python Django Web Framework, which has an excellent input “disinfection” system that removes dangerous symbols from JavaScript code. Therefore, in order for Eve to carry out her attack, I excluded checking the value of the Building Location field for the presence of such characters.

How successful are cross-site scripting attacks? Approximately 80-90% of websites have a client-side vulnerability control mechanism. Failure to withstand XSS attacks is the most common vulnerability of Web 2.0 applications that interact more with end users.
Probably, you heard about one of the most famous “worms” of Samy cross-site scripting, the author of which Sami Kamkar invented in 2005 how to bypass the input filtering of the MySpase social network. He placed javascript on his page, just like Eve did on my page. This script did 2 things: I added Sami as a friend to the victim and copied myself to the profile page of the victim. At first, this attack proceeded very slowly, because only a few people visited the Sami page and were added as friends, but gradually the virus spread more and more and the infection began to grow like an avalanche. This example was indicative in terms of XSS attack capabilities, as more than a million friend requests “collapsed” MySpase site in a few hours. Thus, the consequences of these attacks can be quite serious.
The last type of attack I want to talk about today is access control attacks, or access attacks. With such an attack, the hacker wants to get information that he does not have access to. There are several vulnerabilities that are targeted by the access attack vector.
Often, application developers forget that they left files in the document root directory on a web server, and if you can detect their existence, you will be able to view these files, which often contain confidential information.
Another way to find a vulnerability is to carefully examine the URL. For example, if you see an address of this type app.com/ViewDoc.php?docid=1280149120 , you can easily get a document that is not intended for your eyes by simply searching the numbers at the end of the link.
Many applications are designed for different user levels and have an appropriate access mechanism built in them, which is often based on requests with such parameters app.com/login/home.jsp?admin=false , so you can try to enter the site using the address change in the line on admin = true.
In fact, the most common access control vulnerability is an incorrect implementation of the authorization function. Now Eve will demonstrate it.
Eve Hacker: Thank you, Dr. Loveland. To implement the latest attack, you just need to look very carefully at the URL of our web application. Now I will expand the application window so that the line with the address on Dr. Loveland’s page fits completely on the screen. I have to get rid of this annoying javascript that I installed.
We see that Dr. Loveland’s page address is localhost / SampleSite / Faculty / index-1.html , and if we switch to Dr. Eldridge’s page, the address will become localhost / SampleSite / Faculty / index-2.html .
Do not you think that the same template is used here? However, I am not interested in these address lines, because they do not have the ability to enter information. So I want to get to the Dr. Loveland authorization form. If I login under her name, I can edit her personal information. But let's look at the URL of the page at the end of which there is an IndexForm-1, and you can guess that it is possible, there is an opportunity to get to the data form of Dr. Eldridge.

So the question is whether we can get to his form without logging in on his behalf. Let's try. I change the unit to a deuce so that the address takes the form of localhost / SampleSite / Faculty / indexForm-2.html , press “Enter”, and a page with Dr. Eldridge's personal information appears in front of us.

We have before us a bug that the students of Dr. Loveland forgot to fix - the application has a vulnerability that allows to penetrate someone else's page without entering the victim's login.
Dr. Eldridge is a very pleasant person, I would not like to annoy him, I have nothing against him, but for the sake of laughter I will leave something on his page. Let me distort his name and surname, and at the same time correct the position from “Professor” to “Junior Lecturer”.

Now I will send the corrected personal information to the server, and if you now enter the Eldridge page, you can see the corrections I made on it.

So, Dr. Loveland, if you have problems with Dr. Eldridge, when he thinks of holding you back after the lectures, just tell me, and I’ll even delete all his information!
Susan Loveland: Thanks for the support, Eve! I want to talk about access control vulnerabilities in just one second. For people who, like me, love to dig into the code, I will explain what happened during this attack.

This slide shows how to fill out a form with personal information. The last line is exactly what interested Eve. This class protects form_index from the fast @ login-required and @authUser functions and checks that everyone who wants to change the values in the form fields must log in to the system. However, the developers forgot about this and did not add the mandatory mention of these quick functions in the context of filling out the form.
The code shown checks whether the requested form matches the person who has logged into the system, but since it was not used correctly, Eva was able to detect this vulnerability in the application.
I note that 78% of all sites have access vulnerabilities. In April last year, some hackers discovered a vulnerability on the Berkeley campus — these were hidden files that developers left behind on the document server of the web server. Hackers were able to view these files and obtain social security numbers and confidential medical information for more than 160 thousand people. So you see how serious the consequences of an access control attack can be.
I would like to mention a few more interesting facts in the context of the topic of our conversation today. Recently, the state’s attention to cybersecurity has increased dramatically. Thus, in 2008 alone, the Ministry of Defense recorded more than 360 million hacking attempts. It is planned to spend about $ 75.8 billion on improving the cyber security system in the field of information technologies in 2010, which is 7.2% more than was spent on these goals in 2009. According to CNN Money Magazine, in 2009 in the US, Internet security specialists were among the top most sought-after professions. The average annual income of consultants in the field of computer security was 99.7 thousand dollars, the maximum - 152 thousand dollars. According to forecasts, the need for such specialists from 2006 to 2016 will increase by 27%.
I want to say that the Faculty of Computer Science recently had the opportunity to get an associate degree in Internet Computing & Network Security, so this is a great starting point to start a career in this field.
(puts on the Black Hat)
Eve Hacker: I want to interrupt you for a minute, Dr. Loveland! For future teachers present in this audience, I note that if you master this specialty and someday find yourself in a situation where you do not receive the promised salary increase, then you can always turn to the mafia and perform contract hacking for them. This will be an excellent addition to the salary of a computer science teacher.
(takes off his hat)
Susan Loveland: I want to thank the people who have made a significant contribution to the creation of today's presentation, the developers of the “Faculty Pages”. I think that because of their hard work, I can leave this audience without handcuffs and campus police escort. The only “surviving” member of this group is Ryan Goldsworthy, who played an important role in the development of these pages. I want to thank Dr. Stephen Eldridge for his sense of humor and personal page presentation to demonstrate the attacks, to thank the department heads who made a generous contribution to my Faculty Pages project, and also to thank the Campus Computer Computing Service for protecting us from such people like eve.
Thank you for attention.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Let's talk about our next attack. Let me tell you how the servers identify you. To do this, the stateless HTTP protocol is used between the browser and the server, when communication with the server is performed by independent “request-response” pairs. Therefore, the server forgets you as soon as the connection is established, and during the next session it no longer remembers who you are.

However, he remembers you while you are using the web application, because when you put into the basket the things you are going to buy, you can continue shopping and return again to view the contents of your basket. The implementation of the "memorization" occurs with the help of session identification cookies. As soon as you log in to the server, it generates a cookie, which is a unique sequence of letters and numbers, and sends it to your browser, which stores this cookie locally on your computer. After that, the browser returns the cookie to the server with each of your requests for one session. Receiving these cookies, the server understands that the user accesses him with this request. This is the most common way to identify a user who uses a web application.
The next type of attack is called cross-site scripting, XSS. The idea behind this attack is that the attacker forces the website to display malicious code, usually in the form of JavaScript, which is then executed in the user's browser. Such an attack can pursue any target, but is most often used to obtain the victim's session identifier. The value of the Session ID is that it can be viewed as a password, as it identifies you. By capturing a session identifier, an attacker can disguise itself by using a proxy server to communicate with the target server. The objectives of such an attack may be the desire to speak on your behalf, to automate some actions, such as spamming, on your behalf, or to inject a virus.
When searching for XSS cross-site scripting vulnerabilities in a web application, you are looking for an input field in which you can put some information, send it to the server and see what result is displayed in the browser window.

I enter the wrong location of the building, indicating Plachy Hall, the address of the hall of the basketball team of our university. The web server receives this information and realizes that a computer science professor is a “bot” who cannot live in the location of a sports team, and gives an error message: “Plachy Hall is wrong”!
The search boxes are most vulnerable in this respect, where you can type in some rather vague terms, and then see what you get in return. Most often, you are given a hint with a list of possible correct options that an attacker can use.
The next thing you need to do is check whether you can inject your malicious code and then execute it. We will try to organize XSS attack using JavaScript.

JavaScript code is always highlighted by opening and closing the script tag, as well as the OR operator. Application developers are not completely stupid, so they installed a filtering mechanism called "disinfection." It is embedded inside the code, checks for dangerous characters, and deletes them if possible. The simplest JavaScript "disinfection" test looks like this:
<script>alert(“Testing”)</script> But hackers are a bit smarter, so they have the website ha.ckers.org/xss.html . I don’t have time to show you this site, but there you can find the most sophisticated ways to circumvent the controls that application developers have tried to insert into their programs to remove dangerous characters. So there are quite ingenious ways to allow a hacker to get inside the application.
So let's talk about how the XSS attack will take place. We have a web server "Faculty pages" where we are going to enter a malicious code. We have Eve, who is going to make a hack, but we missed something on this slide - we forgot about the victim. What is good about a XSS attack is that you don’t need to hire anyone. I mean, this time I'm not going to be a victim, because Eva has my password and she can do anything she wants with my account. Therefore, Eve comes out of the big game and no longer chases the little boys. Let's take our victim to the scene (audience laughter, because a picture of one of the faculty’s professors appears on the slide).
Now that the victim has taken his place, let's see how the attack develops. Suppose that Eva was able to place the malicious JavaScript code on the server where our victim is going to log in using her account.
This is important, because as soon as the victim logs into the server, she will receive a session ID, which Eva will try to intercept, this is a very important part of the attack. So, the victim requests a web page that contains malicious JavaScript code, this code will run in the victim's browser and send the session ID to Eve.

After receiving the session ID, Eva can use her proxy server and do whatever she wants, disguised as a victim. The only missing piece of the puzzle is malicious JavaScript itself, which a hacker must insert into the page and which must capture our victim's session ID and transfer it to the attacker.
It is very simple. We have a javascript code that begins and ends with the opening and closing of the tag:
<script> The first line of code creates a drawing in the same way that a picture is dynamically created in JavaScript for any page. You know that at the heart of any image is the file that contains the image, so we need to tell the browser where to go to get this image. This is indicated in the second line, where the link to the hacker's website is located, but the browser thinks that this is exactly the place where the desired image is located. He will go to the Eva website and ask for document.cookie, because he believes that this is the image file he needs.
But this is not a picture file at all, but a session identifier that we are trying to capture using JavaScript. As you can see, getting a Session ID is pretty easy. The third line, which is not used in the code for the XSS attack, is the alarm that triggers a pop-up window in the browser with a message about the attack. This was done specifically for our example, because the real XSS attack takes place completely unnoticed by the victim.

So let's invite Eve and see how she will perform a cross-site scripting attack.
Eve Hacker: thank you, Dr. Loveland! The first thing I have to do is close a few things that we don’t need. We no longer need the Burp Suit proxy server, so I close it. Secondly, I need to reconfigure the web browser and switch it to use the default system proxy settings.
Now let's go to the login page of Dr. Loveland, because if you remember, I have her password and I can enter the site at any time instead. As I mentioned, Dr. Loveland is rather lazy, she uses an expired SSL certificate, so I have to confirm the security exceptions to go to the login page. Since I know the password, I can edit its web page. As we already know, on the personal information editing page there is a vulnerability in the Building Location line, "Building Location", and it is here that I am going to enter my malicious JavaScript.

I have simplified this attack, so in reality I will not send the code to the server, but instead I’m calling a pop-up window with the message that someone is trying to attack me. Now that I have set the stage for the attack, I will return to the login page and log out. Now you just need to wait for the victim to appear who wants to use this application.

(Eva puts on a baseball cap, depicting faculty professor Stephen Eldridge)
I just returned from a fascinating meeting, where we discussed after hours what car should take priority in the parking lot - Subaru or Jeep, and then the thought occurred to us that the difference could be in the presence of the sunroof. So now I need to log in and check my contact details, because I would not want to miss the next out-of-class meeting because my data was not available. So, I log in to my web application under the login saldrich and my password.

So, everything looks as usual, I do not see anything bad on my page of a professor of mathematics, all contact information is in order.
Oh, my God, my watch shows that until the next meeting there are only 2 minutes left! Now I'm going to meet Dr. Loveland, so I need to go to her page and see if I can dig up some compromising information on her to mention him at the meeting. So, I click on the link Susan Loveland, get on her page and ... Dr. Eldridge, your page is hacked!

(Professor Eldridge removes the baseball cap, turning into Eve)
Now that I have your Session ID, I can use my proxy server and disguise yourself, Dr. Eldridge, doing whatever I want on your behalf. I give you my word, Dr. Loveland!
Susan Loveland: thank you, Eve! I wanted to mention that our Faculty Pages application was developed based on one of the newest web frameworks - the Python Django Web Framework, which has an excellent input “disinfection” system that removes dangerous symbols from JavaScript code. Therefore, in order for Eve to carry out her attack, I excluded checking the value of the Building Location field for the presence of such characters.

How successful are cross-site scripting attacks? Approximately 80-90% of websites have a client-side vulnerability control mechanism. Failure to withstand XSS attacks is the most common vulnerability of Web 2.0 applications that interact more with end users.
Probably, you heard about one of the most famous “worms” of Samy cross-site scripting, the author of which Sami Kamkar invented in 2005 how to bypass the input filtering of the MySpase social network. He placed javascript on his page, just like Eve did on my page. This script did 2 things: I added Sami as a friend to the victim and copied myself to the profile page of the victim. At first, this attack proceeded very slowly, because only a few people visited the Sami page and were added as friends, but gradually the virus spread more and more and the infection began to grow like an avalanche. This example was indicative in terms of XSS attack capabilities, as more than a million friend requests “collapsed” MySpase site in a few hours. Thus, the consequences of these attacks can be quite serious.
The last type of attack I want to talk about today is access control attacks, or access attacks. With such an attack, the hacker wants to get information that he does not have access to. There are several vulnerabilities that are targeted by the access attack vector.
Often, application developers forget that they left files in the document root directory on a web server, and if you can detect their existence, you will be able to view these files, which often contain confidential information.
Another way to find a vulnerability is to carefully examine the URL. For example, if you see an address of this type app.com/ViewDoc.php?docid=1280149120 , you can easily get a document that is not intended for your eyes by simply searching the numbers at the end of the link.
Many applications are designed for different user levels and have an appropriate access mechanism built in them, which is often based on requests with such parameters app.com/login/home.jsp?admin=false , so you can try to enter the site using the address change in the line on admin = true.
In fact, the most common access control vulnerability is an incorrect implementation of the authorization function. Now Eve will demonstrate it.
Eve Hacker: Thank you, Dr. Loveland. To implement the latest attack, you just need to look very carefully at the URL of our web application. Now I will expand the application window so that the line with the address on Dr. Loveland’s page fits completely on the screen. I have to get rid of this annoying javascript that I installed.
We see that Dr. Loveland’s page address is localhost / SampleSite / Faculty / index-1.html , and if we switch to Dr. Eldridge’s page, the address will become localhost / SampleSite / Faculty / index-2.html .
Do not you think that the same template is used here? However, I am not interested in these address lines, because they do not have the ability to enter information. So I want to get to the Dr. Loveland authorization form. If I login under her name, I can edit her personal information. But let's look at the URL of the page at the end of which there is an IndexForm-1, and you can guess that it is possible, there is an opportunity to get to the data form of Dr. Eldridge.

So the question is whether we can get to his form without logging in on his behalf. Let's try. I change the unit to a deuce so that the address takes the form of localhost / SampleSite / Faculty / indexForm-2.html , press “Enter”, and a page with Dr. Eldridge's personal information appears in front of us.

We have before us a bug that the students of Dr. Loveland forgot to fix - the application has a vulnerability that allows to penetrate someone else's page without entering the victim's login.
Dr. Eldridge is a very pleasant person, I would not like to annoy him, I have nothing against him, but for the sake of laughter I will leave something on his page. Let me distort his name and surname, and at the same time correct the position from “Professor” to “Junior Lecturer”.

Now I will send the corrected personal information to the server, and if you now enter the Eldridge page, you can see the corrections I made on it.

So, Dr. Loveland, if you have problems with Dr. Eldridge, when he thinks of holding you back after the lectures, just tell me, and I’ll even delete all his information!
Susan Loveland: Thanks for the support, Eve! I want to talk about access control vulnerabilities in just one second. For people who, like me, love to dig into the code, I will explain what happened during this attack.

This slide shows how to fill out a form with personal information. The last line is exactly what interested Eve. This class protects form_index from the fast @ login-required and @authUser functions and checks that everyone who wants to change the values in the form fields must log in to the system. However, the developers forgot about this and did not add the mandatory mention of these quick functions in the context of filling out the form.
The code shown checks whether the requested form matches the person who has logged into the system, but since it was not used correctly, Eva was able to detect this vulnerability in the application.
I note that 78% of all sites have access vulnerabilities. In April last year, some hackers discovered a vulnerability on the Berkeley campus — these were hidden files that developers left behind on the document server of the web server. Hackers were able to view these files and obtain social security numbers and confidential medical information for more than 160 thousand people. So you see how serious the consequences of an access control attack can be.
I would like to mention a few more interesting facts in the context of the topic of our conversation today. Recently, the state’s attention to cybersecurity has increased dramatically. Thus, in 2008 alone, the Ministry of Defense recorded more than 360 million hacking attempts. It is planned to spend about $ 75.8 billion on improving the cyber security system in the field of information technologies in 2010, which is 7.2% more than was spent on these goals in 2009. According to CNN Money Magazine, in 2009 in the US, Internet security specialists were among the top most sought-after professions. The average annual income of consultants in the field of computer security was 99.7 thousand dollars, the maximum - 152 thousand dollars. According to forecasts, the need for such specialists from 2006 to 2016 will increase by 27%.
I want to say that the Faculty of Computer Science recently had the opportunity to get an associate degree in Internet Computing & Network Security, so this is a great starting point to start a career in this field.
(puts on the Black Hat)
Eve Hacker: I want to interrupt you for a minute, Dr. Loveland! For future teachers present in this audience, I note that if you master this specialty and someday find yourself in a situation where you do not receive the promised salary increase, then you can always turn to the mafia and perform contract hacking for them. This will be an excellent addition to the salary of a computer science teacher.
(takes off his hat)
Susan Loveland: I want to thank the people who have made a significant contribution to the creation of today's presentation, the developers of the “Faculty Pages”. I think that because of their hard work, I can leave this audience without handcuffs and campus police escort. The only “surviving” member of this group is Ryan Goldsworthy, who played an important role in the development of these pages. I want to thank Dr. Stephen Eldridge for his sense of humor and personal page presentation to demonstrate the attacks, to thank the department heads who made a generous contribution to my Faculty Pages project, and also to thank the Campus Computer Computing Service for protecting us from such people like eve.
Thank you for attention.
Thank you for staying with us. Do you like our articles? Want to see more interesting materials? Support us by placing an order or recommending to friends, 30% discount for Habr users on a unique analogue of the entry-level servers that we invented for you: The whole truth about VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps from $ 20 or how to share the server? (Options are available with RAID1 and RAID10, up to 24 cores and up to 40GB DDR4).
VPS (KVM) E5-2650 v4 (6 Cores) 10GB DDR4 240GB SSD 1Gbps until spring for free if you pay for a period of six months, you can order here .
Dell R730xd 2 times cheaper? Only we have 2 x Intel Dodeca-Core Xeon E5-2650v4 128GB DDR4 6x480GB SSD 1Gbps 100 TV from $ 249 in the Netherlands and the USA! Read about How to build an infrastructure building. class c using servers Dell R730xd E5-2650 v4 worth 9000 euros for a penny?
Source: https://habr.com/ru/post/438332/